Pass Your Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate Certification Easy!
Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate Certification Exams Questions & Answers, Accurate & Verified By IT Experts
Instant Download, Free Fast Updates, 99.6% Pass Rate.

Microsoft Dynamics 365 Customer Service Functional Consultant
Includes 430 Questions & Answers
$44.99
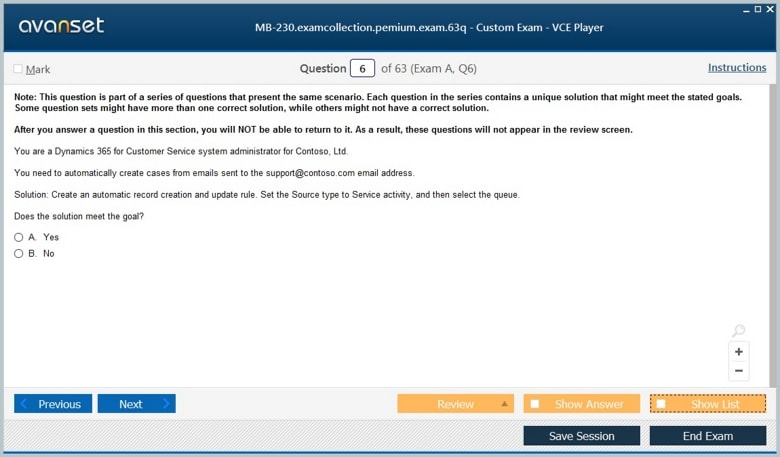
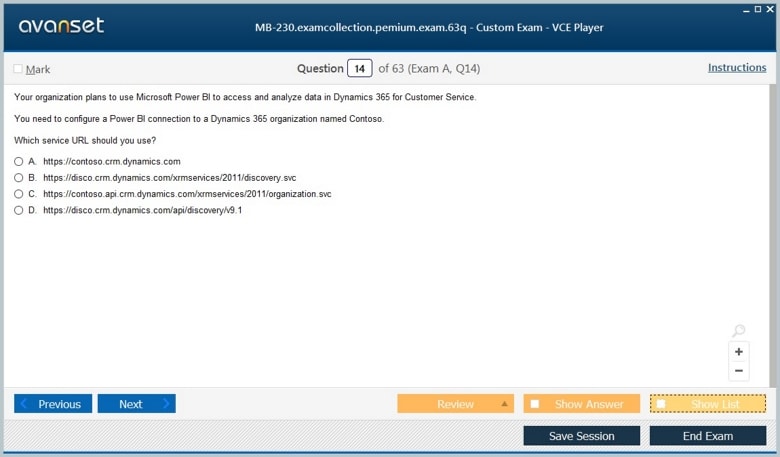
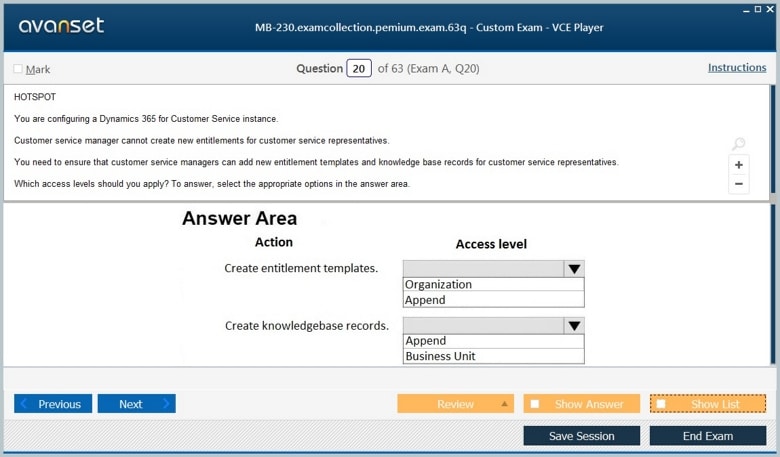
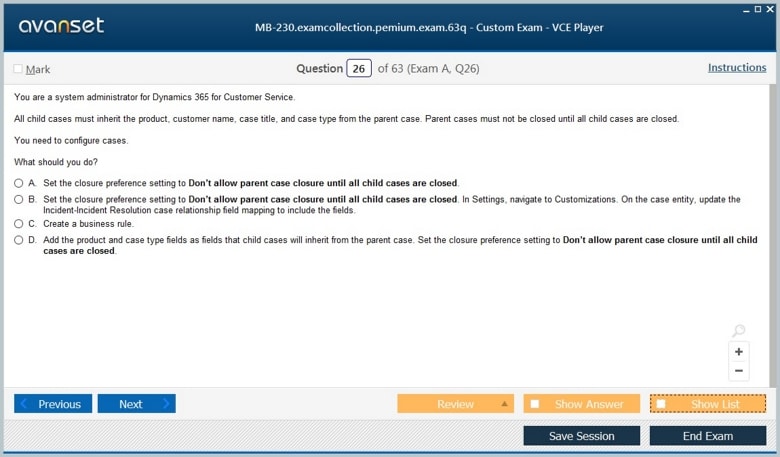
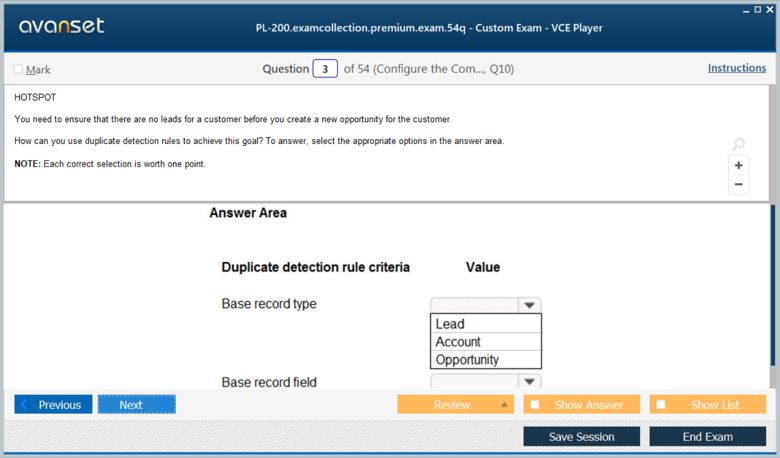
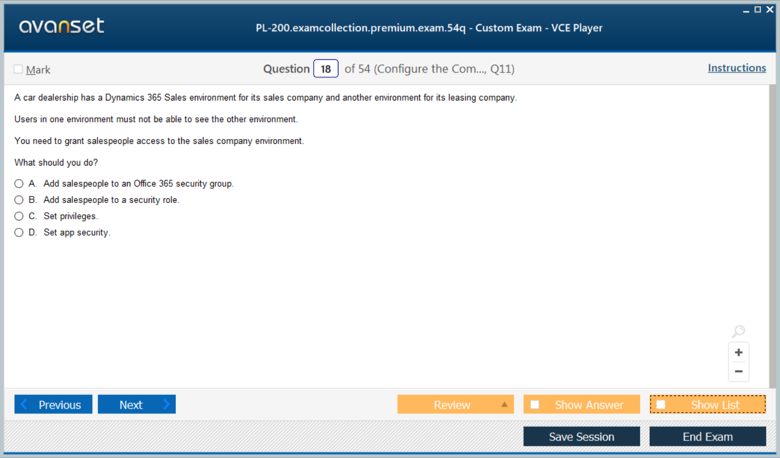
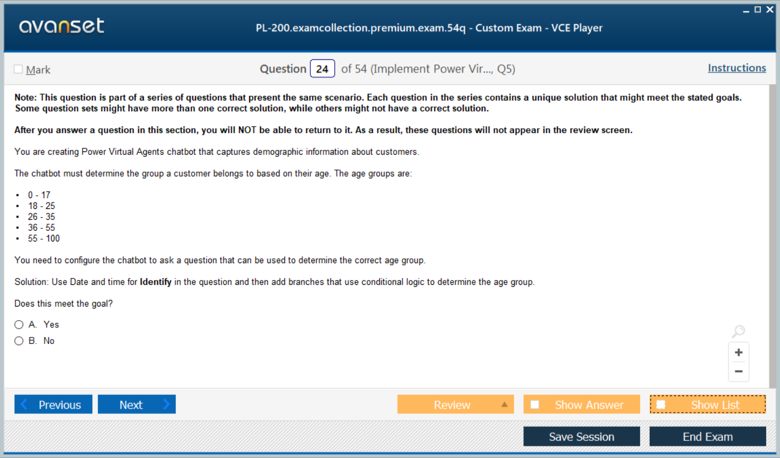
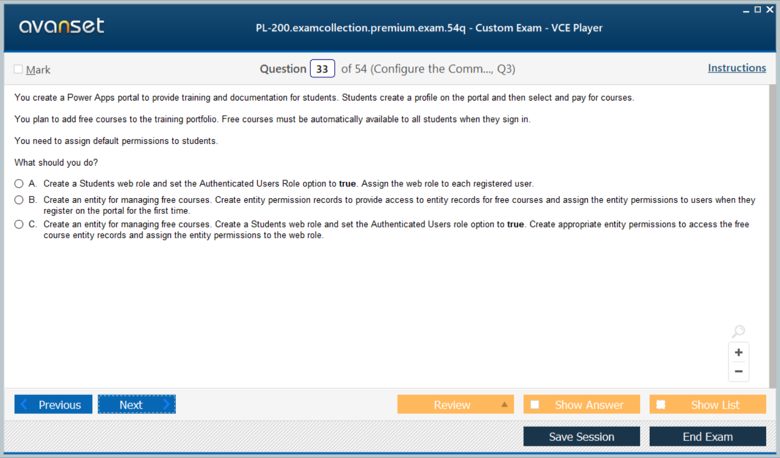
Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate Certification Exams Screenshots
Download Free Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate Practice Test Questions VCE Files
| Exam | Title | Files |
|---|---|---|
Exam MB-230 |
Title Microsoft Dynamics 365 Customer Service Functional Consultant |
Files 8 |
Exam PL-200 |
Title Microsoft Power Platform Functional Consultant |
Files 5 |
Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate Certification Exam Dumps & Practice Test Questions
Prepare with top-notch Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate certification practice test questions and answers, vce exam dumps, study guide, video training course from ExamCollection. All Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate certification exam dumps & practice test questions and answers are uploaded by users who have passed the exam themselves and formatted them into vce file format.
Microsoft Dynamics 365 Customer Service: Expert Strategies for Functional Consultants
In today’s competitive business environment, delivering exceptional customer service has become a strategic priority. Organizations are constantly seeking tools and platforms that allow them to streamline operations, respond quickly to customer inquiries, and enhance overall satisfaction. Microsoft Dynamics 365 Customer Service stands out as a leading solution for businesses looking to achieve these goals. For professionals aiming to excel in this space, becoming a Microsoft Certified Dynamics 365 Customer Service Functional Consultant Associate offers a clear path to mastering the platform and demonstrating expertise in customer service management.
Dynamics 365 Customer Service is more than a CRM system; it is a comprehensive platform that integrates customer data, AI-driven insights, and automation to deliver seamless service experiences. Functional consultants play a pivotal role in configuring, implementing, and optimizing this platform to meet business needs. Their expertise helps organizations reduce response times, improve resolution rates, and create a more personalized customer experience.
This article provides a deep dive into the certification, the skills required, and the practical applications of Dynamics 365 Customer Service. It also explores how this certification can advance your career, enhance business outcomes, and position you as a valued consultant in the rapidly growing CRM market.
Understanding the Role of a Functional Consultant
A functional consultant acts as a bridge between business requirements and technical implementation. In the context of Dynamics 365 Customer Service, the functional consultant focuses on understanding an organization’s service operations and translating these needs into actionable configurations within the platform. This involves collaborating with stakeholders, analyzing business processes, and designing solutions that enhance efficiency and customer satisfaction.
Functional consultants are expected to:
Configure case management and service scheduling tools to align with organizational workflows
Integrate Dynamics 365 with other business systems and applications
Implement knowledge management strategies to provide support teams with easy access to relevant information
Monitor performance metrics and suggest improvements to optimize service delivery
By mastering these areas, functional consultants ensure that the Dynamics 365 Customer Service platform is not only technically sound but also strategically aligned with business objectives.
Core Features of Dynamics 365 Customer Service
To effectively implement Dynamics 365 Customer Service, functional consultants need a comprehensive understanding of the platform’s core features. These features are designed to facilitate seamless customer interactions and streamline service operations.
Case Management
Case management is the cornerstone of Dynamics 365 Customer Service. It allows organizations to track customer issues from initial contact to resolution. Functional consultants configure case queues, routing rules, and escalation procedures to ensure that cases are handled efficiently. By setting up automated workflows, consultants can reduce response times and improve customer satisfaction.
Knowledge Management
Knowledge management is essential for providing consistent and accurate information to both customers and service agents. Dynamics 365 allows organizations to create a centralized knowledge base that agents can access in real time. Functional consultants design strategies for content creation, approval processes, and knowledge article maintenance, enabling teams to resolve cases faster and reduce dependency on senior staff.
Service Scheduling
Efficient service scheduling ensures that customer appointments, field service visits, and support calls are coordinated effectively. Dynamics 365 Customer Service includes tools for resource scheduling, capacity planning, and calendar management. Functional consultants configure these tools to optimize resource utilization and minimize service delays, which directly contributes to customer satisfaction.
Omnichannel Engagement
Modern customers expect support across multiple channels, including email, chat, social media, and phone. Dynamics 365 supports omnichannel engagement, allowing organizations to interact with customers seamlessly across all touchpoints. Functional consultants set up channel integrations, routing rules, and response templates to ensure that customers receive consistent and timely support, regardless of how they reach out.
AI and Analytics
Artificial intelligence and analytics play a crucial role in enhancing customer service. Dynamics 365 leverages AI to provide insights, predict trends, and suggest actions that improve service quality. Functional consultants configure dashboards, reports, and AI-driven recommendations to help organizations make data-driven decisions and proactively address customer needs.
Preparing for the Certification Exam
The Microsoft Certified Dynamics 365 Customer Service Functional Consultant Associate certification validates a professional’s ability to implement and optimize Dynamics 365 Customer Service solutions. Preparation for this exam requires both theoretical knowledge and practical experience with the platform.
Exam Objectives
The certification exam focuses on key areas, including:
Configuring and managing core service management features
Designing and implementing case management solutions
Enabling and configuring knowledge management
Implementing service level agreements, entitlements, and routing rules
Leveraging analytics, dashboards, and AI insights to optimize performance
Understanding these objectives allows candidates to focus their study efforts on the most relevant topics and develop the skills necessary for real-world application.
Study Resources
Microsoft provides a range of resources to support exam preparation, including learning paths, documentation, and hands-on labs. Candidates are encouraged to explore:
Microsoft Learn modules specific to Dynamics 365 Customer Service
Online training courses and video tutorials
Community forums and user groups for practical insights
Practice exams to familiarize themselves with question formats and time management
Combining these resources with hands-on experience in a test environment ensures that candidates are well-prepared for the certification exam.
Practical Experience
While theoretical knowledge is important, practical experience is critical for success. Functional consultants should engage in activities such as configuring case workflows, creating knowledge articles, and setting up dashboards. Real-world projects, even in a simulated environment, help reinforce concepts and provide confidence in applying skills during the exam.
Career Benefits of Certification
Achieving the Microsoft Certified Dynamics 365 Customer Service Functional Consultant Associate credential offers significant career advantages. It signals to employers that you possess specialized skills in Dynamics 365 and can contribute to enhancing customer service operations.
Professional Credibility
Certification demonstrates a validated level of expertise that distinguishes you from other professionals. Organizations recognize certified consultants as capable of implementing solutions that improve efficiency and customer satisfaction. This credibility can open doors to advanced consulting roles, project leadership positions, and higher-level responsibilities.
Career Advancement
The demand for skilled Dynamics 365 consultants is growing as more organizations adopt Microsoft’s cloud-based solutions. Certified professionals are well-positioned for career advancement in areas such as CRM consulting, customer experience management, and business process optimization. This certification can also serve as a stepping stone to advanced Microsoft certifications, expanding career opportunities further.
Increased Earning Potential
Certification often correlates with higher earning potential. Employers are willing to invest in professionals who bring proven skills to their teams. By demonstrating your ability to optimize customer service operations and leverage Dynamics 365 effectively, you position yourself as a high-value contributor capable of impacting business performance.
Networking Opportunities
Becoming certified connects you with a global community of Dynamics 365 professionals. Engaging with peers, participating in forums, and attending Microsoft events provides access to best practices, industry insights, and potential career opportunities. Networking within this community can accelerate learning and professional growth.
Implementing Dynamics 365 Customer Service in Organizations
Successfully implementing Dynamics 365 Customer Service requires a strategic approach. Functional consultants must consider organizational goals, customer needs, and technical capabilities to design solutions that deliver measurable outcomes.
Needs Assessment
The first step in any implementation project is conducting a thorough needs assessment. This involves gathering input from stakeholders, analyzing existing processes, and identifying pain points. Functional consultants use this information to design a solution that aligns with business objectives and addresses customer service challenges.
Solution Design
Based on the needs assessment, functional consultants create a detailed solution design. This includes configuring case management workflows, defining knowledge management strategies, setting up service level agreements, and designing dashboards for performance monitoring. The design phase ensures that all system components work together to achieve the desired outcomes.
Configuration and Testing
Once the solution design is finalized, consultants configure the Dynamics 365 environment. This involves creating entities, fields, forms, and workflows tailored to organizational needs. Rigorous testing is conducted to ensure that the system functions as intended and meets performance expectations. User acceptance testing is critical to validate that the solution supports real-world business processes effectively.
Training and Adoption
Successful adoption of Dynamics 365 Customer Service depends on training and support for end-users. Functional consultants develop training materials, conduct workshops, and provide guidance to ensure that service teams are confident in using the platform. Change management strategies are employed to minimize resistance and promote a smooth transition.
Continuous Improvement
Dynamics 365 Customer Service is not a static system; it evolves as organizational needs change. Functional consultants monitor system performance, gather user feedback, and implement improvements to optimize service delivery continually. This ongoing process ensures that the organization maximizes the value of its Dynamics 365 investment.
The Microsoft Certified Dynamics 365 Customer Service Functional Consultant Associate certification equips professionals with the skills and knowledge needed to implement and optimize customer service solutions. By mastering core features such as case management, knowledge management, service scheduling, and AI-driven analytics, consultants can drive efficiency, enhance customer experiences, and support organizational growth.
Earning this certification not only validates your expertise but also opens doors to advanced career opportunities, higher earning potential, and professional recognition. For organizations, having certified consultants ensures that Dynamics 365 Customer Service is deployed effectively, delivering measurable benefits and positioning the company for success in a customer-centric market.
Investing time in understanding the platform, gaining hands-on experience, and preparing thoroughly for the certification exam is essential for aspiring consultants. By doing so, you position yourself as a valuable asset capable of transforming customer service operations and making a tangible impact on business performance.
Advanced Features of Dynamics 365 Customer Service
Dynamics 365 Customer Service is a versatile platform that goes beyond basic customer support. While basic features like case management and knowledge articles are foundational, advanced capabilities empower organizations to deliver highly personalized and efficient service. Functional consultants must understand these advanced features to implement solutions that drive measurable outcomes and create a competitive advantage.
These advanced capabilities include AI-driven insights, omnichannel engagement, automation workflows, service level agreements, and integration with the broader Microsoft ecosystem. Mastery of these tools allows consultants to design solutions that streamline processes, reduce resolution times, and improve overall customer satisfaction.
AI and Automation in Customer Service
Artificial intelligence (AI) and automation are transforming the way organizations interact with customers. Dynamics 365 Customer Service leverages AI to enhance decision-making, predict customer needs, and provide proactive service. Functional consultants play a key role in configuring AI-driven features to optimize service operations.
Predictive Analytics
Predictive analytics uses historical data and machine learning algorithms to anticipate customer behavior. In Dynamics 365, predictive analytics can forecast case volumes, identify potential escalations, and suggest next best actions for support agents. Functional consultants configure these analytics tools to generate actionable insights, helping teams prioritize cases and allocate resources effectively.
Virtual Agents and Chatbots
Virtual agents and chatbots are AI-powered tools that provide instant responses to common customer inquiries. Dynamics 365 enables organizations to deploy intelligent chatbots across multiple channels, including websites, mobile apps, and social media. Consultants configure chatbots to recognize customer intent, escalate complex issues to human agents, and collect data for continuous improvement.
Automated Workflows
Automation in Dynamics 365 Customer Service reduces repetitive tasks and ensures consistent processes. Consultants set up workflows to automate case routing, send notifications, update records, and trigger escalation rules. Automated workflows enhance efficiency, minimize human error, and allow service teams to focus on high-value interactions.
Omnichannel Engagement
Modern customers expect support across various channels, including email, chat, social media, and phone. Dynamics 365 Customer Service offers omnichannel capabilities that enable organizations to provide seamless, consistent service regardless of the communication channel. Functional consultants are responsible for configuring these channels to ensure a smooth and integrated customer experience.
Email and Social Media Integration
By integrating email and social media platforms, organizations can track customer interactions in a single interface. Functional consultants configure inbound and outbound routing, assign cases to the right agents, and ensure that responses are timely and accurate. Integration also allows businesses to monitor sentiment, detect trends, and respond proactively to customer needs.
Real-Time Chat Support
Real-time chat enables immediate assistance for customers navigating websites or mobile apps. Dynamics 365 allows consultants to configure chat queues, assign agents based on skill sets, and track chat performance metrics. This ensures that customers receive prompt and knowledgeable support, improving satisfaction and loyalty.
Voice Support and Telephony
Voice support remains a critical channel for many organizations. Dynamics 365 integrates with telephony systems to enable click-to-call functionality, call routing, and automated logging of interactions. Functional consultants configure these systems to streamline voice support and maintain a complete record of customer interactions.
Service Level Agreements and Performance Management
Service level agreements (SLAs) define the expected level of service and response times for customer interactions. Dynamics 365 Customer Service enables organizations to monitor compliance with SLAs and track performance metrics. Functional consultants are responsible for configuring SLA rules, escalation policies, and reporting dashboards.
Configuring SLAs
Consultants define SLA conditions, such as response times for high-priority cases or resolution targets for specific issue types. The system automatically monitors case progress and triggers notifications when SLA thresholds are approaching. Proper SLA configuration ensures accountability and helps organizations maintain high service standards.
Performance Metrics and Dashboards
Dynamics 365 offers a robust set of reporting tools and dashboards to track key performance indicators (KPIs). Consultants configure dashboards to visualize case resolution times, agent productivity, customer satisfaction scores, and SLA compliance. These insights allow managers to make data-driven decisions and identify areas for improvement.
Continuous Improvement
By analyzing SLA and performance data, functional consultants can recommend process enhancements, reassign resources, and implement best practices. Continuous improvement ensures that the organization adapts to changing customer needs and consistently delivers high-quality service.
Integration with Microsoft Ecosystem
One of the strengths of Dynamics 365 Customer Service is its integration with the broader Microsoft ecosystem. Functional consultants leverage these integrations to enhance functionality, streamline operations, and provide a unified experience across platforms.
Power Platform Integration
The Power Platform, which includes Power Apps, Power Automate, and Power BI, complements Dynamics 365 by enabling custom applications, automation, and advanced analytics. Functional consultants create custom apps to address specific business needs, automate complex workflows, and generate visual insights for decision-makers.
Microsoft Teams Collaboration
Collaboration is essential for effective customer service. Dynamics 365 integrates with Microsoft Teams to enable real-time communication, case collaboration, and knowledge sharing. Consultants configure Teams integration to facilitate seamless collaboration between agents, managers, and subject matter experts, enhancing problem resolution efficiency.
Azure and Cloud Services
Azure provides scalable cloud infrastructure, AI capabilities, and data services that enhance Dynamics 365 Customer Service. Functional consultants can leverage Azure services to implement advanced analytics, sentiment analysis, and predictive maintenance solutions. This integration empowers organizations to leverage cloud computing and AI for superior customer service experiences.
Best Practices for Implementation
Successful implementation of Dynamics 365 Customer Service requires careful planning, strategy, and execution. Functional consultants must follow best practices to ensure that solutions deliver maximum value and adoption across the organization.
Define Clear Objectives
Before implementing the system, it is essential to define clear business objectives. Consultants work with stakeholders to identify goals, such as reducing response times, improving customer satisfaction, or increasing agent productivity. Clear objectives guide the configuration process and provide benchmarks for measuring success.
Engage Stakeholders Early
Involving stakeholders early in the implementation process ensures that the solution meets business needs. Functional consultants conduct workshops, gather requirements, and validate processes with key stakeholders. This engagement minimizes resistance and promotes user adoption.
Focus on User Experience
The success of a customer service solution depends on the user experience. Consultants design intuitive interfaces, streamline workflows, and ensure that agents can access relevant information quickly. A user-friendly system enhances productivity and reduces training time.
Regular Training and Support
Ongoing training is critical for maintaining competency and adoption. Functional consultants develop training programs, provide documentation, and offer hands-on support to ensure that service teams are confident in using Dynamics 365. Continuous support helps address challenges and encourages best practice adherence.
Monitor, Analyze, and Improve
Implementation is not a one-time activity. Functional consultants monitor system performance, analyze metrics, and recommend process improvements. By adopting a culture of continuous improvement, organizations can adapt to changing customer expectations and maintain high service quality.
Real-World Use Cases
Understanding real-world applications of Dynamics 365 Customer Service helps illustrate its value. Many organizations across industries leverage the platform to enhance customer service, optimize workflows, and drive business growth.
Retail and E-Commerce
Retail organizations use Dynamics 365 to manage customer inquiries, returns, and complaints efficiently. Automated workflows, AI-driven recommendations, and omnichannel engagement enable retailers to provide timely support, increase customer loyalty, and streamline operations.
Financial Services
Banks and financial institutions leverage Dynamics 365 to manage client interactions, track service requests, and comply with regulatory requirements. Functional consultants configure the platform to ensure data security, improve response times, and enhance the overall client experience.
Healthcare
Healthcare providers utilize Dynamics 365 to coordinate patient inquiries, appointment scheduling, and follow-up communications. Functional consultants help design workflows that prioritize critical cases, manage patient data securely, and enable seamless collaboration between care teams.
Technology and IT Services
IT service providers use Dynamics 365 to manage technical support tickets, monitor SLAs, and deliver proactive maintenance. Consultants configure AI-driven insights and automation to reduce downtime, improve response times, and enhance service reliability.
Career Opportunities and Growth
Becoming proficient in advanced Dynamics 365 Customer Service features opens numerous career opportunities. Professionals with expertise in configuration, automation, AI integration, and omnichannel support are in high demand. Career paths include:
Senior Dynamics 365 Consultant
Customer Service Solutions Architect
CRM Project Manager
Business Process Analyst
AI and Automation Specialist
Certification validates skills and positions professionals for leadership roles, higher salaries, and opportunities to work on complex, high-impact projects.
Advanced knowledge of Dynamics 365 Customer Service empowers functional consultants to design solutions that transform customer service operations. By leveraging AI, automation, omnichannel engagement, and integration with the Microsoft ecosystem, consultants can create highly efficient and personalized service experiences.
Implementing best practices, monitoring performance, and continuously improving processes ensure that organizations maximize the value of Dynamics 365 investments. Real-world use cases demonstrate the platform’s versatility across industries, and mastering these capabilities significantly enhances career growth and earning potential.
Functional consultants who excel in these areas become trusted advisors, capable of driving digital transformation initiatives and delivering measurable business outcomes. By focusing on advanced features, strategic implementation, and continuous improvement, professionals position themselves as leaders in the evolving landscape of customer service technology.
Practical Implementation of Dynamics 365 Customer Service
While understanding the features and capabilities of Dynamics 365 Customer Service is critical, translating that knowledge into practical implementation is what truly drives business value. Functional consultants are responsible for bridging the gap between theoretical design and real-world execution, ensuring that the platform meets organizational goals and enhances customer experiences.
This article delves into practical strategies for implementing Dynamics 365 Customer Service, covering configuration, workflows, knowledge management, dashboards, testing, and user adoption. It also highlights challenges, solutions, and best practices that functional consultants should follow to ensure successful deployments.
Planning a Successful Implementation
A structured planning phase is the foundation of a successful Dynamics 365 Customer Service deployment. Without careful planning, projects risk delays, misalignment with business needs, and low user adoption.
Requirements Gathering
Functional consultants begin by gathering detailed requirements from stakeholders across the organization. This includes understanding current processes, identifying pain points, and defining desired outcomes. Techniques such as workshops, interviews, and process mapping are commonly used to ensure that all perspectives are captured.
Key areas to focus on include:
Case management processes and routing rules
Knowledge management practices
Customer interaction channels
Reporting and performance monitoring requirements
Thorough requirements gathering ensures that the solution addresses real business challenges rather than hypothetical scenarios.
Solution Design
Once requirements are gathered, the functional consultant creates a solution design that outlines how Dynamics 365 Customer Service will be configured and integrated. The design should include entity definitions, workflow diagrams, data mapping, and integration points with other systems.
Solution design should also consider scalability, flexibility, and future growth. By anticipating potential changes, consultants can create a robust implementation that remains effective as the organization evolves.
Risk Assessment and Mitigation
Every implementation comes with risks. Common risks include data migration challenges, resistance to change, and integration complexities. Functional consultants perform risk assessments to identify potential issues and develop mitigation strategies, such as phased rollouts, pilot testing, and user training programs.
Configuring Core Features
Configuration is where the theoretical design meets practical application. Functional consultants tailor Dynamics 365 Customer Service to match organizational needs, ensuring that workflows are optimized and tools are intuitive for users.
Case Management Configuration
Case management is at the heart of customer service operations. Consultants configure case entities, forms, queues, and routing rules to ensure that each customer inquiry is handled efficiently. Advanced configurations may include automated case creation, escalation procedures, and assignment based on agent skills or availability.
Proper configuration minimizes delays, ensures accountability, and provides agents with the information they need to resolve issues effectively.
Knowledge Management Setup
A centralized knowledge base is crucial for consistent and accurate service delivery. Functional consultants create knowledge articles, set up approval workflows, and configure search and tagging functionalities. This allows agents to access relevant content quickly, reducing resolution times and enhancing the customer experience.
Service Scheduling and Resource Allocation
Efficient scheduling of resources, appointments, and field service activities is vital for organizations with extensive service operations. Consultants configure resource calendars, availability rules, and booking policies to optimize utilization and minimize conflicts. Automated scheduling tools ensure that the right personnel are assigned to the right tasks at the right time.
Workflow Automation and Customization
Workflows are a key component of efficient service operations. Dynamics 365 allows consultants to automate repetitive tasks, enforce business rules, and trigger notifications based on specific conditions.
Automated Notifications
Automated notifications ensure that stakeholders are informed when actions are required. Consultants configure notifications for SLA breaches, case escalations, and approvals, ensuring timely interventions and accountability.
Custom Workflows
Custom workflows can address unique business requirements that standard configurations do not cover. Functional consultants use the built-in workflow designer to create processes that align with organizational goals, such as multi-step approvals, cross-departmental coordination, and automated reporting.
Integration with Power Automate
Power Automate extends the automation capabilities of Dynamics 365. Consultants can create flows that connect Dynamics 365 with other applications, automate data entry, synchronize records, and trigger actions across multiple systems, reducing manual work and enhancing efficiency.
Dashboards and Analytics
Data-driven decision-making is a key advantage of Dynamics 365 Customer Service. Consultants configure dashboards and reports that provide visibility into key metrics, enabling managers to monitor performance, identify trends, and make informed decisions.
Configuring Dashboards
Dashboards display real-time information on case volumes, SLA compliance, agent productivity, and customer satisfaction. Consultants design dashboards that are tailored to different user roles, ensuring that managers, supervisors, and agents have the insights they need to perform effectively.
Advanced Analytics
Beyond basic reporting, advanced analytics uses historical data, trends, and AI-driven insights to predict future outcomes. Consultants can configure predictive models to anticipate case surges, detect recurring issues, and recommend proactive actions to prevent service bottlenecks.
Data Migration and Integration
Many organizations transitioning to Dynamics 365 Customer Service must migrate data from legacy systems. Functional consultants oversee data migration, ensuring that records are accurate, complete, and properly mapped to new entities.
Data Cleaning and Preparation
Prior to migration, consultants perform data cleaning to remove duplicates, correct errors, and standardize formats. Clean data ensures that the new system operates efficiently and reduces the risk of inaccuracies affecting service delivery.
System Integration
Integration with other enterprise systems, such as ERP, marketing automation, and communication platforms, allows for a unified customer experience. Consultants configure integration points to synchronize data, automate workflows, and ensure seamless communication across the organization.
User Training and Adoption
Even the most technically sound implementation can fail without proper user adoption. Functional consultants play a crucial role in training and change management to ensure that service teams embrace the new system.
Training Programs
Consultants develop training programs tailored to different roles, providing hands-on exercises, guides, and reference materials. Training focuses on system navigation, case handling, knowledge base usage, and workflow management, ensuring that users can operate effectively from day one.
Change Management
Change management strategies address resistance and encourage adoption. Functional consultants communicate the benefits of the system, highlight improvements over legacy processes, and involve users in testing and feedback sessions. Engaging stakeholders early fosters a sense of ownership and promotes successful adoption.
Testing and Quality Assurance
Testing is critical to verify that the implementation meets design specifications and operates as intended. Consultants conduct multiple testing phases to identify issues and ensure smooth operation.
Unit and System Testing
Unit testing ensures that individual components, such as workflows, forms, and dashboards, function correctly. System testing verifies that all components work together seamlessly and that business processes are supported end-to-end.
User Acceptance Testing
User acceptance testing involves real users performing tasks within the system to validate functionality and usability. Feedback from UAT sessions helps consultants fine-tune configurations and address any gaps before full deployment.
Performance Monitoring
After deployment, consultants monitor system performance to identify bottlenecks, errors, or inefficiencies. Regular monitoring ensures that the system continues to meet business objectives and provides a reliable service platform.
Common Challenges and Solutions
Implementing Dynamics 365 Customer Service comes with challenges that consultants must anticipate and address.
Resistance to Change
Employees may be hesitant to adopt a new system. Consultants overcome resistance by demonstrating the system’s benefits, providing comprehensive training, and involving users in configuration decisions.
Data Quality Issues
Poor data quality can hinder system performance. Data cleansing, validation, and ongoing monitoring are essential to maintain accuracy and reliability.
Complex Integrations
Integrating Dynamics 365 with other enterprise systems can be challenging. Consultants address this by mapping data flows carefully, testing integrations thoroughly, and using tools like Power Automate for seamless connections.
Managing Expectations
Stakeholders may have unrealistic expectations about the system’s capabilities. Clear communication, realistic timelines, and iterative implementation help manage expectations and ensure satisfaction.
Measuring Success
The success of a Dynamics 365 Customer Service implementation is measured by tangible improvements in efficiency, customer satisfaction, and business outcomes.
Key Metrics
Functional consultants track metrics such as:
Case resolution time
SLA compliance
Agent productivity
Customer satisfaction scores
Knowledge base utilization
These metrics provide insights into system performance and areas for continuous improvement.
Continuous Improvement
Successful organizations adopt a culture of continuous improvement. Consultants regularly review metrics, gather user feedback, and implement updates to workflows, dashboards, and knowledge management practices. This ongoing optimization ensures that the system evolves with business needs.
Career Impact of Practical Expertise
Practical expertise in implementing Dynamics 365 Customer Service enhances career prospects. Professionals with hands-on experience are highly valued for their ability to deliver functional solutions that drive measurable outcomes. Career opportunities include:
Senior Functional Consultant
CRM Solution Architect
Customer Experience Manager
Dynamics 365 Trainer or Coach
Business Process Consultant
Hands-on implementation experience differentiates professionals in the competitive CRM consulting landscape and positions them for leadership roles.
Practical implementation of Dynamics 365 Customer Service is where theoretical knowledge transforms into measurable business value. Functional consultants are at the center of this process, designing configurations, automating workflows, integrating systems, and ensuring user adoption.
By focusing on requirements gathering, solution design, configuration, testing, and continuous improvement, consultants enable organizations to deliver exceptional customer service experiences. Overcoming challenges and leveraging advanced features ensures that the platform drives efficiency, enhances satisfaction, and supports organizational growth.
Hands-on implementation skills are essential for career advancement, positioning functional consultants as trusted experts capable of delivering tangible results and guiding organizations through digital transformation initiatives.
Leveraging AI and Analytics in Dynamics 365 Customer Service
Modern customer service is increasingly data-driven, requiring insights that allow organizations to anticipate needs, optimize operations, and deliver personalized experiences. Dynamics 365 Customer Service integrates AI and advanced analytics to help organizations transform raw data into actionable intelligence. Functional consultants play a key role in implementing these capabilities, ensuring that AI tools are configured correctly and analytics dashboards provide meaningful insights.
This article explores AI-driven features, predictive analytics, sentiment analysis, real-time dashboards, and best practices for leveraging data to improve customer service outcomes.
Understanding AI in Customer Service
Artificial intelligence enhances Dynamics 365 by automating routine tasks, predicting outcomes, and providing recommendations for customer interactions. AI reduces manual effort, improves decision-making, and empowers service teams to focus on complex or high-value customer issues.
AI-Powered Case Management
AI in Dynamics 365 can automatically categorize and prioritize cases based on historical patterns and customer context. Functional consultants configure AI models to recognize case types, suggest resolution steps, and route cases to the appropriate agents. This reduces resolution times and ensures that customers receive timely support.
Virtual Agents and Chatbots
Virtual agents are AI-driven bots that handle routine customer queries through chat or voice. Dynamics 365 allows consultants to design bots that interact naturally with customers, escalate complex issues, and capture data for reporting and process improvement. These bots improve availability, provide instant responses, and reduce the workload on human agents.
Predictive Analytics
Predictive analytics uses machine learning models to forecast customer behavior, service demand, and potential escalations. Consultants configure these models to identify trends, anticipate issues, and recommend proactive measures. For example, if a spike in support cases is predicted, resources can be allocated in advance to maintain service levels.
Sentiment Analysis and Customer Insights
Understanding customer sentiment is critical for delivering personalized service. Dynamics 365 includes tools that analyze customer communications, such as emails, chats, and social media posts, to detect sentiment and mood.
Configuring Sentiment Analysis
Functional consultants configure sentiment analysis models to monitor interactions and flag negative feedback or potential escalations. Insights from sentiment analysis allow agents to tailor responses, prioritize urgent issues, and improve customer satisfaction.
Integration with Customer Insights
Customer Insights in Dynamics 365 aggregates data from multiple sources to create unified customer profiles. Consultants configure these profiles to include preferences, interaction history, purchase behavior, and feedback. A complete view of the customer enables more informed decisions and personalized engagement strategies.
Real-Time Dashboards and Reporting
Data visualization is a critical aspect of leveraging analytics. Real-time dashboards provide instant visibility into performance metrics, operational efficiency, and customer trends.
Designing Dashboards
Consultants design dashboards tailored to different user roles. Managers can track team productivity, case resolution rates, SLA compliance, and customer satisfaction scores. Agents see their current workloads, pending cases, and recommended actions. Dashboards help ensure that decision-makers have actionable insights at their fingertips.
Advanced Analytics with Power BI
Power BI integration allows for deeper analysis and interactive reporting. Consultants can create detailed visualizations, trend analysis, and predictive models. These tools enable organizations to identify inefficiencies, monitor KPIs, and optimize resource allocation for maximum impact.
Monitoring Key Metrics
Effective customer service relies on tracking metrics such as average resolution time, first-contact resolution rate, and knowledge base usage. Functional consultants configure reports to highlight these metrics and provide actionable recommendations for improvement. Continuous monitoring ensures that service standards remain high and performance gaps are addressed promptly.
Automation and AI-Driven Workflows
Automation and AI together enhance efficiency, consistency, and service quality. Dynamics 365 allows functional consultants to implement workflows that combine business rules with AI recommendations.
Case Routing and Escalation
AI can analyze case complexity and automatically route it to the most suitable agent. Consultants configure rules and escalation paths to ensure timely resolution, maintain SLA compliance, and prevent service delays.
AI-Recommended Actions
AI-driven recommendations suggest the next best actions for agents, including relevant knowledge articles, potential solutions, and follow-up steps. These suggestions reduce decision-making time and increase resolution accuracy.
Predictive SLA Management
AI can monitor case progression and predict SLA breaches before they occur. Functional consultants configure alerts, notifications, and automatic escalations to proactively manage cases, ensuring customer expectations are met consistently.
Enhancing Omnichannel Engagement with AI
Omnichannel service is greatly enhanced by AI capabilities. Customers interact through multiple channels, and AI ensures that their experience is seamless across all touchpoints.
Intelligent Chat Routing
AI analyzes customer interactions across channels and routes inquiries based on agent skills, availability, and past interactions. This reduces wait times and improves first-contact resolution rates.
Voice and Call Analysis
AI-driven voice analysis evaluates calls for tone, sentiment, and urgency. Consultants configure these tools to alert supervisors about high-risk interactions, identify training needs, and optimize call handling strategies.
Personalized Customer Journeys
By analyzing interaction history and customer data, AI enables personalized engagement. Recommendations can include tailored product suggestions, proactive issue resolution, and targeted follow-ups. Functional consultants ensure that these journeys are seamlessly integrated into daily service operations.
Best Practices for Implementing AI and Analytics
While AI and analytics offer significant advantages, proper planning and configuration are essential for success.
Start with Clear Objectives
Define what business outcomes you want to achieve with AI. This could include reducing resolution times, increasing customer satisfaction, or improving agent productivity. Clear objectives guide model configuration, dashboard design, and workflow automation.
Use Clean and Complete Data
AI models and analytics rely on accurate and comprehensive data. Consultants must ensure that customer records, interaction history, and service data are consistent, complete, and free from duplicates.
Engage Stakeholders
Involve stakeholders in defining key metrics, dashboard designs, and AI recommendations. Early engagement ensures that tools align with business needs and are adopted by end-users.
Pilot and Iterate
Implement AI and analytics features in a pilot phase to gather feedback, measure performance, and refine configurations. Iterative improvements help optimize accuracy, usability, and impact before full deployment.
Continuous Monitoring and Optimization
AI models and analytics dashboards require ongoing monitoring. Consultants should track model performance, validate recommendations, and adjust configurations to reflect changing business needs and customer expectations.
Emerging Trends in Dynamics 365 Customer Service
The customer service landscape continues to evolve, and functional consultants must stay updated on emerging trends to maintain competitive advantage.
Hyper-Personalization
Using AI and analytics, organizations are moving toward hyper-personalized customer experiences. By leveraging behavioral data and predictive insights, consultants can design solutions that anticipate needs and tailor interactions for individual customers.
Proactive Support
Predictive analytics enables organizations to address issues before they impact customers. Functional consultants can implement proactive alerts, maintenance reminders, and personalized outreach, reducing negative experiences and enhancing loyalty.
Integration with IoT
IoT devices provide real-time operational data that can trigger service actions automatically. For example, a connected device can alert support teams to a malfunction, allowing consultants to configure workflows that open cases and schedule interventions automatically.
AI-Augmented Decision Making
AI is increasingly supporting agent decisions rather than replacing them. Functional consultants configure AI tools to provide actionable recommendations, context-aware insights, and process guidance, enabling agents to resolve cases faster and with greater accuracy.
Career Advantages of AI and Analytics Expertise
Expertise in AI and analytics within Dynamics 365 Customer Service significantly enhances career prospects. Professionals skilled in predictive modeling, sentiment analysis, and advanced reporting are highly sought after. Career opportunities include:
AI Solutions Consultant
Customer Experience Analyst
Dynamics 365 Data Analyst
CRM Strategy Manager
Customer Service Operations Lead
Certification combined with practical AI and analytics skills positions professionals as thought leaders in the rapidly evolving customer service technology space.
AI and analytics are transforming Dynamics 365 Customer Service, enabling organizations to provide faster, more personalized, and more effective support. Functional consultants play a critical role in implementing these capabilities, configuring models, dashboards, workflows, and insights to deliver measurable business outcomes.
By leveraging predictive analytics, sentiment analysis, AI-driven recommendations, and advanced reporting, consultants ensure that organizations can anticipate customer needs, streamline operations, and optimize resource utilization. Staying ahead of emerging trends like hyper-personalization, proactive support, and IoT integration ensures that solutions remain innovative and impactful.
Mastering AI and analytics in Dynamics 365 Customer Service not only enhances organizational performance but also accelerates career growth, establishing functional consultants as indispensable experts in the customer service technology landscape.
Career Pathways with Dynamics 365 Customer Service
Earning the Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate credential opens doors to numerous career opportunities in customer service, CRM consulting, and business process optimization. Organizations increasingly rely on Dynamics 365 experts to implement, manage, and optimize their customer service operations, making this certification highly valuable for professionals seeking growth and advancement.
This article explores career pathways, professional development strategies, certification roadmaps, real-world consulting practices, and tips for maximizing value in the Dynamics 365 ecosystem.
Understanding the Career Landscape
Customer service is a critical component of organizational success, and Dynamics 365 provides the tools to enhance every aspect of service delivery. Certified functional consultants are in high demand because they combine technical expertise with business acumen, enabling organizations to improve efficiency, customer satisfaction, and revenue.
Roles for certified professionals often include responsibilities such as:
Designing and configuring customer service solutions
Integrating Dynamics 365 with other enterprise systems
Automating workflows and processes
Analyzing performance metrics and providing insights
Training users and ensuring adoption
These responsibilities make functional consultants indispensable for organizations implementing Dynamics 365 Customer Service.
Common Roles and Responsibilities
Dynamics 365 expertise allows professionals to pursue various roles, depending on their skills, experience, and career goals.
Functional Consultant
Functional consultants configure and optimize Dynamics 365 Customer Service to meet business requirements. Responsibilities include gathering requirements, designing workflows, implementing case management, configuring SLAs, and providing end-user training. They ensure that the system is aligned with organizational goals and delivers measurable results.
Senior Consultant or Solution Architect
With experience, consultants may advance to senior consultant or solution architect roles. These positions involve designing end-to-end solutions, integrating multiple Microsoft applications, advising on best practices, and leading implementation projects. Architects also play a strategic role, ensuring that solutions support business objectives and long-term growth.
Customer Experience Manager
Certified professionals may transition into customer experience management roles. Here, they oversee customer service operations, analyze metrics, implement improvements, and align service strategies with business goals. Knowledge of Dynamics 365 enables managers to leverage technology effectively to enhance customer satisfaction.
CRM Project Manager
CRM project managers lead Dynamics 365 implementation projects, coordinating teams, managing timelines, and ensuring that project objectives are met. Functional consultants with project experience are well-positioned to step into these leadership roles, combining technical knowledge with project management skills.
Business Process Analyst
Business process analysts focus on evaluating and improving organizational processes using Dynamics 365. They identify inefficiencies, design optimized workflows, and ensure that the platform supports operational excellence. Functional consultants with analytical skills can excel in this role, bridging the gap between technology and business strategy.
Certification Roadmap and Professional Growth
Achieving the Functional Consultant Associate certification is an important milestone, but it can also serve as a foundation for further professional growth. Microsoft offers additional certifications and learning paths that help professionals expand their expertise and advance their careers.
Advanced Dynamics 365 Certifications
After earning the associate-level certification, professionals can pursue advanced certifications, such as:
Dynamics 365 Customer Service Expert
Dynamics 365 Solution Architect Expert
Dynamics 365 Field Service Functional Consultant
These certifications deepen expertise in specific areas, enhance credibility, and open up higher-level consulting or management opportunities.
Complementary Certifications
Complementary certifications in related areas can further strengthen a professional profile. Examples include:
Microsoft Power Platform certifications, which enable automation, app development, and advanced analytics
Azure certifications, which provide cloud expertise for scalable, integrated solutions
Project management certifications like PMP, which support leadership roles in implementation projects
Combining Dynamics 365 expertise with complementary skills creates a well-rounded professional capable of handling complex business challenges.
Continuous Learning
The technology landscape evolves rapidly, and continuous learning is essential. Functional consultants should stay updated on platform updates, new features, AI capabilities, and best practices. Engaging in webinars, community forums, Microsoft Learn modules, and conferences ensures that professionals remain competitive and informed.
Real-World Consulting Strategies
Practical experience and consulting skills are crucial for success in Dynamics 365 roles. Certified professionals need to understand not only the technical features but also the business context in which solutions are deployed.
Stakeholder Engagement
Engaging stakeholders effectively is key to successful implementation. Consultants should understand the priorities, challenges, and goals of various stakeholders, communicate clearly, and involve them in requirements gathering, testing, and adoption activities.
Solution Customization
Every organization has unique processes, and consultants must tailor Dynamics 365 configurations accordingly. Customization includes designing workflows, case routing rules, knowledge management strategies, dashboards, and integrations that align with business objectives.
Problem-Solving and Troubleshooting
Consultants frequently encounter challenges such as complex integrations, workflow conflicts, or data inconsistencies. Strong problem-solving skills enable them to diagnose issues, implement solutions, and maintain system reliability.
Training and Change Management
Ensuring user adoption requires training and change management strategies. Consultants develop role-specific training materials, conduct workshops, and provide ongoing support to users. Communicating the benefits of the platform and guiding employees through the transition are critical for long-term success.
Metrics and Performance Monitoring
Effective consultants measure outcomes to demonstrate value. Monitoring key metrics like case resolution times, SLA compliance, knowledge base utilization, and customer satisfaction helps identify opportunities for improvement and validates the impact of the implementation.
Industry Applications
Dynamics 365 Customer Service is applicable across a wide range of industries. Understanding industry-specific requirements enhances a consultant’s ability to deliver impactful solutions.
Retail and E-Commerce
In retail, consultants design solutions to manage customer inquiries, returns, and loyalty programs. AI-driven insights and omnichannel engagement help improve response times, increase customer retention, and optimize operational efficiency.
Financial Services
Banks and financial institutions use Dynamics 365 for case management, compliance tracking, and client engagement. Consultants ensure secure data handling, automate routine processes, and enhance client satisfaction with timely, accurate support.
Healthcare
Healthcare providers rely on Dynamics 365 to manage patient communications, scheduling, and care coordination. Consultants implement workflows that prioritize critical cases, integrate with patient management systems, and ensure compliance with regulations.
Technology and IT Services
IT service organizations use Dynamics 365 to manage technical support tickets, track service levels, and deliver proactive maintenance. Functional consultants configure AI tools and automation to optimize workflows and improve service reliability.
Building a Strong Professional Profile
In addition to technical expertise, building a strong professional profile enhances career opportunities. Key strategies include:
Networking
Engage with Microsoft communities, user groups, forums, and conferences to build connections. Networking provides access to best practices, job opportunities, and mentorship.
Showcasing Projects
Documenting real-world projects and successful implementations demonstrates practical experience. Consultants can highlight achievements such as improved SLA compliance, automated workflows, or AI-driven insights that delivered measurable business outcomes.
Thought Leadership
Sharing insights through blogs, webinars, or community contributions positions professionals as experts. Thought leadership enhances credibility, increases visibility in the industry, and can attract consulting opportunities.
Continuous Skill Development
Stay current with platform updates, AI capabilities, analytics features, and emerging customer service trends. Continuous skill development ensures that professionals remain competitive and prepared for advanced roles.
Maximizing Value in the Dynamics 365 Ecosystem
To maximize professional value, consultants should adopt a holistic approach that combines technical proficiency, business insight, and strategic thinking. Key considerations include:
Understanding the end-to-end customer journey and designing solutions that enhance each touchpoint
Leveraging AI and analytics to drive proactive, data-driven service strategies
Integrating Dynamics 365 with complementary Microsoft solutions like Power Platform, Azure, and Teams
Continuously monitoring system performance, optimizing workflows, and improving user adoption
By taking this approach, functional consultants deliver high-impact solutions, support digital transformation initiatives, and position themselves as trusted advisors within their organizations.
Future Opportunities and Emerging Trends
The Dynamics 365 ecosystem continues to evolve, presenting new opportunities for certified professionals. Emerging trends include:
Greater adoption of AI for predictive support and decision-making
Integration with Internet of Things (IoT) devices for real-time service interventions
Hyper-personalization of customer experiences based on behavioral data
Expansion of omnichannel engagement across new digital platforms
Consultants who stay ahead of these trends can guide organizations in leveraging technology to meet evolving customer expectations, maintaining relevance and competitive advantage in the marketplace.
Conclusion
The Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate certification serves as a gateway to a dynamic and rewarding career. Professionals who earn this credential gain the skills needed to implement, optimize, and manage customer service solutions that drive efficiency, improve customer satisfaction, and deliver measurable business outcomes.
By pursuing advanced certifications, gaining hands-on experience, and mastering AI, analytics, and automation, consultants can expand their expertise and unlock leadership opportunities. Real-world consulting skills, stakeholder engagement, and continuous professional development further enhance career growth and visibility in the Dynamics 365 ecosystem.
Whether your goal is to become a senior consultant, solution architect, customer experience manager, or CRM strategist, expertise in Dynamics 365 Customer Service provides a solid foundation. By combining technical proficiency with business insight and strategic thinking, professionals can make a lasting impact on organizations and establish themselves as trusted experts in customer service technology.
ExamCollection provides the complete prep materials in vce files format which include Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate certification exam dumps, practice test questions and answers, video training course and study guide which help the exam candidates to pass the exams quickly. Fast updates to Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate certification exam dumps, practice test questions and accurate answers vce verified by industry experts are taken from the latest pool of questions.
Microsoft Microsoft Certified: Dynamics 365 Customer Service Functional Consultant Associate Video Courses



Top Microsoft Certification Exams
- AZ-104
- AI-102
- DP-700
- AI-900
- AZ-305
- PL-300
- MD-102
- AZ-900
- AZ-500
- SC-200
- SC-300
- MS-102
- AZ-204
- SC-401
- DP-600
- SC-100
- AZ-700
- PL-200
- AZ-400
- AZ-800
- AZ-140
- SC-900
- PL-400
- PL-600
- MS-900
- AZ-801
- DP-300
- MS-700
- MB-280
- GH-300
- PL-900
- MB-800
- MB-330
- MB-310
- DP-100
- DP-900
- MB-820
- MB-230
- MB-700
- GH-200
- MS-721
- GH-900
- MB-920
- MB-910
- PL-500
- MB-500
- MB-335
- GH-500
- DP-420
- GH-100
- MB-240
- AZ-120
- SC-400
- DP-203
- AZ-303
- MO-100
- MB-210
- 98-388
- MB-900
- 62-193
- 98-383
Site Search: