Pass Your Juniper JN0-362 Exam Easy!
Juniper JN0-362 Exam Questions & Answers, Accurate & Verified By IT Experts
Instant Download, Free Fast Updates, 99.6% Pass Rate
Juniper JN0-362 Practice Test Questions, Exam Dumps
Juniper JN0-362 (Service Provider Routing and Switching, Specialist) exam dumps vce, practice test questions, study guide & video training course to study and pass quickly and easily. Juniper JN0-362 Service Provider Routing and Switching, Specialist exam dumps & practice test questions and answers. You need avanset vce exam simulator in order to study the Juniper JN0-362 certification exam dumps & Juniper JN0-362 practice test questions in vce format.
A Comprehensive Introduction to the Juniper JN0-362 Service Provider Certification
The JN0-362 exam, officially known as the Service Provider Routing and Switching, Specialist (JNCIS-SP), represents a significant milestone for any networking professional working with Juniper Networks technologies. It is designed to validate the skills and knowledge of individuals with an intermediate understanding of routing and switching implementations within a service provider environment. Passing this exam demonstrates a thorough grasp of the Junos operating system, core routing protocols, and the fundamental technologies that power modern service provider networks. This certification is not an entry-level credential; it assumes foundational knowledge, typically demonstrated by holding the JNCIA-Junos certification.
The journey towards achieving the JN0-362 certification involves moving beyond basic device configuration and into the realm of network design and troubleshooting. Candidates are expected to understand not just the 'how' but also the 'why' behind various protocol operations and feature implementations. The exam blueprint covers a wide range of topics, including Interior Gateway Protocols (IGPs) like OSPF and IS-IS, the Border Gateway Protocol (BGP), Multiprotocol Label Switching (MPLS), and even foundational concepts of Layer 2 and Layer 3 Virtual Private Networks (VPNs). It is a robust test of a candidate's ability to operate in a real-world service provider context.
The Significance of JNCIS-SP in the Service Provider World
In the competitive landscape of network engineering, certifications serve as a standardized measure of expertise. The JNCIS-SP credential, earned by passing the JN0-362 exam, is highly respected within the industry. It signals to employers and peers that an individual possesses the requisite skills to configure, manage, and troubleshoot complex service provider infrastructures built on Juniper Networks platforms. This certification is often a key differentiator for career advancement, opening doors to more senior roles in network operations, engineering, and architecture within telecommunications companies, internet service providers, and large enterprises with extensive network backbones.
Holding this certification validates a deep understanding of the technologies that are essential for service delivery. Service providers rely on robust, scalable, and resilient networks to deliver services like internet access, business VPNs, and mobile data. The topics covered in the JN0-362 exam directly align with these requirements. An engineer certified at the JNCIS-SP level is trusted to work on the core infrastructure that underpins these critical services, making them a valuable asset to any organization. The knowledge gained while preparing for this exam provides a solid foundation for further specialization in more advanced topics.
Foundational Junos OS Concepts for JN0-362
Before diving into complex routing protocols, a solid understanding of the Junos operating system is paramount for success in the JN0-362 exam. The Junos OS architecture is distinct, featuring a clear separation between its control plane and forwarding plane. The control plane, which runs on the Routing Engine (RE), is responsible for all protocol operations, management, and system control. The forwarding plane, handled by the Packet Forwarding Engine (PFE), is responsible for the high-speed transit of traffic based on the forwarding table it receives from the RE. This separation enhances stability and performance.
A key feature of Junos is its configuration hierarchy. The configuration is structured in a tree-like format, which is both logical and easy to navigate. This hierarchical structure allows for organized and granular control over every aspect of the device. Another critical concept is the candidate versus active configuration model. Engineers make changes to a copy of the active configuration, known as the candidate configuration. These changes are not applied to the running system until they are explicitly verified and committed. This transactional commit model allows for atomic changes and provides a robust mechanism to prevent configuration errors from immediately impacting the network.
Mastering Junos Operational Commands
While configuration is a major part of the JN0-362 curriculum, proficiency in operational mode commands is equally vital for verification and troubleshooting. The ability to quickly and accurately assess the state of a device and its protocols is a core skill for any network engineer. The show command is the most frequently used tool for this purpose. For example, show interfaces terse provides a concise summary of all interfaces and their status, while show route displays the contents of the routing table, which is essential for verifying reachability and path selection.
Beyond basic verification, Junos offers powerful tools for deeper analysis. The monitor command allows for real-time observation of system logs or traffic on an interface, which is invaluable for troubleshooting live issues. For more in-depth debugging, traceoptions is the go-to feature. It can be configured under various protocol hierarchies to log detailed information about protocol events, packet exchanges, and state transitions. Understanding how to properly configure, enable, and interpret the output from traceoptions is a critical skill tested in the JN0-362 and is indispensable in real-world troubleshooting scenarios.
Core Routing Principles Revisited
The JN0-362 exam builds upon fundamental routing concepts. A clear understanding of the difference between the Routing Information Base (RIB) and the Forwarding Information Base (FIB) is essential. The RIB, also known as the routing table, is maintained by the Routing Engine and contains all the routing information learned from various sources, including static routes, directly connected interfaces, and dynamic routing protocols. The control plane uses the information in the RIB to calculate the best path to each destination network. This decision-making process is a central theme throughout the exam syllabus.
Once the best routes are selected, they are installed into the FIB, or forwarding table, which resides in the Packet Forwarding Engine. The PFE uses the FIB for high-speed packet forwarding, as it is optimized for fast lookups. The distinction between these two tables highlights the separation of the control and forwarding planes in Junos. Another foundational topic is administrative distance, known in Junos as route preference. This value is used to determine which route should be chosen when the same prefix is learned from multiple different routing protocols. A lower preference value is always preferred over a higher one.
Understanding Protocol-Independent Routing
Junos provides a flexible framework for managing routing information through its protocol-independent properties. One of the most important features in this category is the concept of routing instances. By default, all routing information resides in the primary routing instance, often referred to as the global routing table. However, Junos allows for the creation of multiple, separate routing instances on a single device. Each instance maintains its own set of interfaces, routing tables, and protocols, effectively creating a virtual router. This capability is the cornerstone of implementing services like Layer 3 VPNs, a key topic in the JN0-362.
Another powerful protocol-independent feature is the use of RIB groups. RIB groups allow you to share routing information between different routing tables on the same device. For instance, you can use a RIB group to import routes from a specific routing instance's table into the main global routing table, or vice versa. This provides granular control over how routing information is propagated within a router. Mastering the configuration and application of routing instances and RIB groups is crucial for building the sophisticated network designs expected of a JNCIS-SP certified professional. These features provide immense flexibility beyond basic protocol configuration.
Laying the Groundwork with Interfaces and Static Routes
The configuration of any network begins with its interfaces. In Junos, all interface configurations are handled under the [edit interfaces] hierarchy. This includes assigning logical units, which are akin to subinterfaces, and configuring protocol families such as inet for IPv4 and inet6 for IPv6. For each logical unit and family, an IP address is assigned, which enables the interface to participate in IP routing. Understanding the syntax for configuring different interface types, from high-speed Ethernet to logical loopback interfaces, is a fundamental prerequisite for the JN0-362 exam. Loopback interfaces are particularly important as they provide a stable router identifier for routing protocols.
Static routing represents the most basic form of directing traffic. While dynamic routing protocols are the focus of the JN0-362, static routes are still used in many scenarios, such as defining a default route to the internet or directing traffic to a specific destination that is not part of a dynamic routing domain. In Junos, static routes are configured under the [edit routing-options] hierarchy. A key feature is the concept of the next-hop. This specifies the IP address of the adjacent router to which packets for the destination prefix should be forwarded. It is also possible to configure more advanced static route options, like qualified next-hops for backup routes.
Preparing Your Study Plan for the JN0-362
Successfully passing the JN0-362 exam requires a structured and disciplined approach to studying. The first step should be to thoroughly review the official exam objectives. These objectives provide a detailed breakdown of all the topics that may appear on the exam, allowing you to identify areas where you are strong and areas that require more attention. A balanced study plan should allocate time for both theoretical learning and practical, hands-on lab exercises. Simply reading about protocols is not sufficient; you must configure and troubleshoot them to truly understand their behavior.
Building a home lab using virtualized Juniper devices is an excellent and cost-effective way to gain practical experience. This allows you to experiment with different configurations, break things, and learn how to fix them in a safe environment. Supplement your hands-on practice with reputable study materials, such as official courseware, books, and online technical documentation. Participating in online forums and study groups can also be beneficial, as it allows you to ask questions and learn from the experiences of others who are also on their JN0-362 journey. Consistency is key; dedicating a certain amount of time each day or week to studying will be more effective than cramming at the last minute.
The Role of IGPs in the JN0-362 Blueprint
Interior Gateway Protocols, or IGPs, form the foundational layer of routing within a single autonomous system (AS). For any service provider network, a robust and scalable IGP is essential. It provides the reachability information that is required for all other services to function. Protocols like Border Gateway Protocol (BGP) rely on an underlying IGP to resolve the next-hop addresses of BGP peers. Similarly, traffic engineering protocols like RSVP, a key component of MPLS, use the IGP's link-state database to calculate paths through the network. The JN0-362 exam places significant emphasis on both OSPF and IS-IS, the two most common IGPs in service provider environments.
A candidate preparing for the JN0-362 must have a deep understanding of how these protocols work, not just how to configure them. This includes knowledge of their underlying algorithms, packet types, neighbor adjacency formation processes, and scalability mechanisms. The exam will test your ability to configure these protocols in a multi-area or multi-level design, as well as your skills in verifying their correct operation and troubleshooting common issues that may arise. A solid grasp of IGPs is not just a prerequisite for the exam, but a fundamental skill for any engineer working in a service provider network.
A Deep Dive into Open Shortest Path First (OSPF)
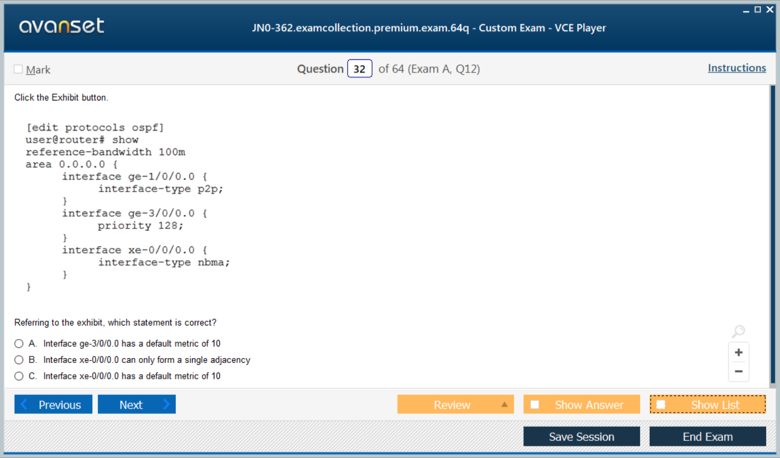
Open Shortest Path First (OSPF) is a link-state routing protocol that is widely deployed in both enterprise and service provider networks. Its operation is based on the Dijkstra shortest-path first algorithm. Each router running OSPF maintains a complete map of the network topology in its Link-State Database (LSDB). This map is built from Link-State Advertisements (LSAs) that are flooded throughout a given area. When a change in the network occurs, such as a link going down, the affected router generates a new LSA, which is then flooded to all other routers in the area, allowing them to update their LSDB and recalculate the shortest path to all destinations.
For scalability, OSPF uses a hierarchical design based on the concept of areas. Area 0, also known as the backbone area, is central to this design, and all other areas must connect directly to it. This segmentation helps to limit the scope of LSA flooding and reduces the size of the LSDB on routers, which in turn conserves CPU and memory resources. On multi-access network segments like Ethernet, OSPF elects a Designated Router (DR) and a Backup Designated Router (BDR) to manage the adjacency formation process and reduce the amount of protocol traffic. A deep understanding of OSPF areas and DR/BDR election is critical for the JN0-362.
Configuring and Verifying OSPF in Junos
Configuring OSPF on a Junos device is a straightforward process performed under the [edit protocols ospf] hierarchy. The fundamental step is to define an area and then assign interfaces to that area. For example, to enable OSPF on an interface, you would add it under [edit protocols ospf area 0.0.0.0]. The loopback interface is particularly important in an OSPF deployment. It is typically configured with a /32 address and serves as the router ID, which is a unique 32-bit number that identifies the router within the OSPF domain. A stable router ID is essential for network stability.
Verification is a key skill tested on the JN0-362 exam. Once OSPF is configured, you must verify that adjacencies have formed and that routes are being exchanged correctly. The show ospf neighbor command is the primary tool for checking the status of OSPF adjacencies. It displays information about each neighbor, including its address, state, and the interface on which it was learned. To inspect the routes learned via OSPF, the show route protocol ospf command is used. For a deeper look into the protocol's operation, show ospf database allows you to view the contents of the LSDB, which is invaluable for troubleshooting routing issues.
Exploring OSPF Area Types and LSA Summarization
To enhance scalability, OSPF supports several special area types that control the propagation of LSAs. A standard area accepts all types of LSAs, including internal routes, summary routes from other areas, and external routes redistributed from other protocols. A stub area, however, blocks external LSAs (Type 5 LSAs) from entering. Instead, the Area Border Router (ABR) injects a default route into the stub area, simplifying the routing table for routers within that area. This is useful for areas with limited resources or simple connectivity requirements. The JN0-362 requires a clear understanding of these concepts.
A Totally Stubby Area takes this concept further by blocking not only external LSAs but also inter-area summary LSAs (Type 3 LSAs). Only the default route is allowed. Another important area type is the Not-So-Stubby Area (NSSA). An NSSA behaves like a stub area but with a special exception: it allows an Autonomous System Boundary Router (ASBR) to exist within the area and redistribute external routes. These external routes are advertised using a special Type 7 LSA, which is then translated into a Type 5 LSA by the ABR. Mastering these area types and the concept of route summarization at the ABR is crucial for designing and managing large-scale OSPF networks.
An Introduction to Intermediate System to Intermediate System (IS-IS)
Intermediate System to Intermediate System (IS-IS) is another link-state IGP that is extremely popular in large service provider backbones. Originally designed for the CLNS protocol suite, it was later extended to support IP routing, a version often referred to as Integrated IS-IS. Like OSPF, it uses the Dijkstra algorithm to compute best paths. However, its design philosophy and terminology are quite different. Instead of routers and areas, IS-IS talks about Intermediate Systems (IS) and levels. A network is divided into Level 2 (the backbone) and Level 1 areas, which are analogous to OSPF's backbone and non-backbone areas.
One of the most distinct features of IS-IS is its use of Network Entity Titles (NETs) for addressing. A NET address is assigned to the router itself, typically on the loopback interface, rather than to individual links. This address identifies the area the router belongs to and the system ID of the router. Another key difference is that IS-IS runs directly over the data link layer, encapsulating its packets in Layer 2 frames, whereas OSPF is encapsulated in IP packets. This design makes IS-IS protocol-agnostic, and its use of Type-Length-Value (TLV) fields makes it highly extensible, a key reason for its popularity in service provider networks that need to support new features like traffic engineering and IPv6.
Practical IS-IS Configuration and Troubleshooting on Junos
Configuring Integrated IS-IS on a Junos device is done under the [edit protocols isis] hierarchy. The configuration involves assigning interfaces to the protocol. For each interface, you specify the level it should participate in, either Level 1, Level 2, or both. A router can be a Level 1 router (staying within an area), a Level 2 router (participating only in the backbone), or a Level 1-2 router (acting as a border router between a Level 1 area and the Level 2 backbone). A crucial part of the configuration is setting the NET address on the loopback interface under [edit interfaces lo0 unit 0 family iso].
Verification and troubleshooting commands for IS-IS are similar in purpose to their OSPF counterparts. The show isis adjacency command is used to check if the router has formed adjacencies with its neighbors. To view the contents of the link-state database, you use the show isis database command. This will display the Link-State PDUs (LSPs), which are the IS-IS equivalent of OSPF's LSAs. For troubleshooting connectivity, show route protocol isis will display all the routes learned through the protocol. For more complex issues, traceoptions can be enabled under the IS-IS hierarchy to capture detailed protocol messages, a necessary skill for the JN0-362.
Comparing OSPF and IS-IS for Service Provider Networks
While both OSPF and IS-IS are robust link-state IGPs, service providers often choose one over the other based on specific design goals and scalability requirements. A key consideration for the JN0-362 is understanding the trade-offs between them. IS-IS is often favored in very large-scale networks due to its perceived scalability advantages. Because it uses a more flexible TLV-based packet format, it is easier to extend the protocol to carry new types of information, which is a significant benefit for MPLS traffic engineering and other advanced features. IS-IS also tends to be less chatty and can support a larger number of routers in a single area.
OSPF, on the other hand, is generally more widely known and understood by network engineers, especially those coming from an enterprise background. Its IP-based encapsulation can make it easier to filter and manage using standard IP access control lists. The concept of areas and the DR/BDR election process are well-defined and familiar. However, its design can be seen as slightly more rigid compared to the flexible nature of IS-IS TLVs. For the JN0-362 exam, you should be prepared to not only configure and verify both protocols but also to discuss their comparative strengths and weaknesses in different network scenarios.
IGP Route Manipulation and Policy
Even within an IGP, there are often requirements to influence path selection or control the advertisement of routes. Junos provides a powerful and flexible policy framework that can be applied to IGPs. Policies can be used to manipulate metrics, filter routes, or set specific attributes. For example, you can create a policy that increases the metric for routes learned from a specific neighbor, making that path less preferred. This is accomplished using an export policy applied to the IGP. The policy would match certain routes and then modify their metric before they are advertised to other routers.
Similarly, an import policy can be used to filter which routes are accepted into the routing table from an IGP neighbor. While less common within an IGP (as you typically want full reachability), it can be useful in specific scenarios. A more common use of policy with IGPs is for controlling redistribution between different routing protocols. When redistributing routes from, for example, BGP into OSPF, a policy is essential to filter which prefixes are injected and to set their initial OSPF metric and route type. Understanding how to write and apply these routing policies is a core competency for the JN0-362.
Why BGP is Critical for the JN0-362 Exam
The Border Gateway Protocol (BGP) is the protocol that powers the global internet. It is the only exterior gateway protocol (EGP) in widespread use today, and it is responsible for exchanging routing information between different autonomous systems (AS). For a service provider, BGP is not just a protocol for connecting to the internet; it is the foundation for delivering many of its most important services, including internet transit and Layer 3 VPNs. A deep and practical understanding of BGP is therefore a non-negotiable requirement for any engineer aspiring to achieve the JNCIS-SP certification, and the JN0-362 exam reflects this importance.
The exam blueprint for JN0-362 dedicates a significant portion to BGP, covering its fundamental operations, attributes, path selection process, scaling mechanisms, and the application of routing policies. Candidates are expected to be able to configure both internal BGP (iBGP) and external BGP (eBGP) sessions, manipulate traffic flow using various BGP attributes, and implement policies to control the advertisement and reception of routes. Mastering BGP is not just about passing an exam; it is about acquiring the skills necessary to manage and engineer the flow of traffic across large and complex networks.
Understanding BGP Fundamentals: Path Vector and AS Numbers
Unlike IGPs like OSPF or IS-IS, which use metrics based on link speed to find the shortest path, BGP is a path vector protocol. It makes routing decisions based on a list of attributes associated with each route, the most important of which is the AS_PATH. The AS_PATH attribute is a list of all the autonomous system numbers that a route has traversed to reach the local router. This path information is fundamental to BGP's primary function: loop prevention. A BGP router will not accept a route if it sees its own AS number already present in the AS_PATH, as this would indicate a routing loop.
BGP sessions, or peerings, are established between routers using TCP port 179. There are two main types of BGP peerings. External BGP (eBGP) is used to establish a session between routers in different autonomous systems. This is the type of peering used between a service provider and its customers or between two different service providers. Internal BGP (iBGP) is used to establish sessions between routers within the same autonomous system. iBGP is used to ensure that all routers within an AS have a consistent view of the external routes learned via eBGP, which is essential for proper forwarding. The JN0-362 requires proficiency in both.
Establishing BGP Peering Sessions in Junos
Configuring BGP in the Junos OS is done under the [edit protocols bgp] hierarchy. The first step is to define the local autonomous system number under [edit routing-options]. After that, you create a BGP group. Groups are a convenient way to apply common configuration parameters to a set of BGP neighbors. You can create different groups for iBGP peers and eBGP peers. Within a group, you define each neighbor by its IP address and specify its peer AS number. For an eBGP session, the peer AS will be different from the local AS. For an iBGP session, the peer AS will be the same.
A critical aspect of establishing BGP sessions, particularly iBGP sessions, is ensuring that the peering addresses are reachable. Since iBGP peers are often not directly connected, they typically peer using their loopback interface addresses. This requires that the underlying IGP (OSPF or IS-IS) provides a route to the loopback addresses of all iBGP speakers within the AS. Once configured, the state of BGP sessions can be verified using the show bgp summary command. This command provides a concise overview of all configured neighbors, their AS number, and the current state of their session. A state of "Established" indicates a successful peering.
The BGP Path Selection Algorithm Explained
BGP's power lies in its complex path selection process, which allows for granular control over routing. When a BGP router learns multiple paths to the same destination prefix, it must decide which path is the best. It does this by stepping through a well-defined sequence of checks based on BGP attributes. A key focus of the JN0-362 is understanding this algorithm. The process begins by checking for a valid next-hop. Then, it prefers the path with the highest LOCAL_PREFERENCE value. This attribute is only exchanged between iBGP peers and is a primary tool for influencing outbound traffic flow from an AS.
If the LOCAL_PREFERENCE is equal, the router prefers paths that it originated locally. Following that, it prefers the path with the shortest AS_PATH length. This is often a primary factor in eBGP path selection. If the AS_PATH lengths are also equal, the router checks the ORIGIN code, preferring routes with an origin of IGP over EGP, and EGP over INCOMPLETE. The next major attribute checked is the Multi-Exit Discriminator (MED), where a lower value is preferred. The algorithm continues with several more steps, such as preferring eBGP over iBGP paths, until a single best path is identified and installed into the routing table.
Common BGP Path Attributes and Their Functions
To effectively use the BGP path selection algorithm, a network engineer must understand the purpose of each major attribute. As mentioned, LOCAL_PREFERENCE is a locally significant attribute used within an AS to express a preference for a particular exit point. It is typically set on inbound routes from eBGP peers to guide the traffic of the entire AS. The AS_PATH attribute, besides being a loop prevention mechanism, is a key metric for path length. Engineers can influence inbound traffic from other networks by using AS_PATH prepending, which involves artificially lengthening the AS_PATH of advertised routes to make them appear less desirable.
The Multi-Exit Discriminator (MED) attribute is another tool for influencing inbound traffic. It is sent from one AS to a neighboring AS to suggest which of several entry points the neighboring AS should prefer. A lower MED value is more preferred. The ORIGIN attribute indicates how the route was first injected into BGP; IGP means it was injected using a network statement, while INCOMPLETE typically means it was redistributed from another protocol. Finally, COMMUNITIES are optional transitive attributes that act as tags, allowing for policies to be applied to groups of routes across multiple routers or even multiple autonomous systems. The JN0-362 will test your knowledge of all these attributes.
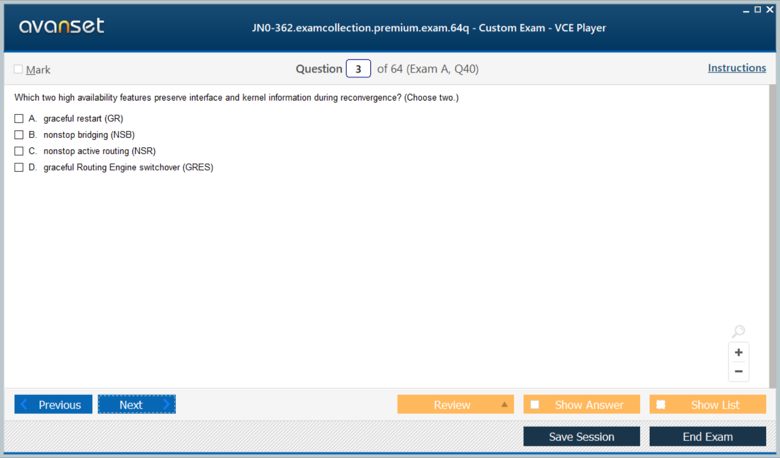
Scaling iBGP with Route Reflectors and Confederations
A fundamental rule of iBGP is that a route learned from one iBGP peer cannot be advertised to another iBGP peer. This rule is in place to prevent routing loops within the AS. To ensure all iBGP speakers have complete routing information, a full mesh of iBGP sessions must be configured between all of them. While this works for small networks, it does not scale. The number of required sessions grows quadratically with the number of routers, creating significant configuration and processing overhead. The JN0-362 exam covers two primary solutions to this scalability problem: route reflectors and confederations.
A route reflector (RR) is a router that is allowed to break the standard iBGP split-horizon rule. It can reflect routes learned from one iBGP peer (its client) to other iBGP peers (other clients). This allows for a much more scalable design where iBGP clients only need to peer with the route reflector, rather than with every other client. Confederations are another approach where a large AS is divided into smaller sub-autonomous systems. Normal iBGP is run within each sub-AS, and a special form of eBGP is run between the sub-autonomous systems, but the entire configuration appears as a single AS to the outside world. Route reflectors are the more commonly deployed solution today.
Implementing BGP Routing Policies
The true power of BGP is unlocked through the application of routing policies. Junos has a highly flexible and powerful policy engine that is used extensively with BGP to control routing information. Policies are constructed using a from-then logic. The from part specifies the matching conditions, such as a specific prefix list, AS path, or community value. The then part specifies the actions to be taken if the conditions are met, such as accepting the route, rejecting it, or modifying one of its attributes. For example, a policy can be written to match routes from a specific customer and then set a higher LOCAL_PREFERENCE on them.
These policies are applied to BGP sessions using the import and export directives. An import policy is applied to routes being received from a BGP neighbor, before they are placed in the routing table. This is where you would filter unwanted routes or set attributes like LOCAL_PREFERENCE. An export policy is applied to routes being advertised to a BGP neighbor. This is where you would control which of your routes are announced to the outside world and perform actions like AS_PATH prepending or setting the MED value. A significant portion of the JN0-362 exam involves creating and applying BGP policies to achieve specific routing outcomes.
Verifying and Troubleshooting BGP for the JN0-362
Effective verification and troubleshooting are essential skills for any BGP administrator. The show bgp summary command, as previously noted, is the first step to check the status of peering sessions. If a session is not established, you should check for IP reachability between the peers, verify that the AS numbers are configured correctly, and check for any firewall filters that might be blocking TCP port 179. Once the session is up, you need to verify route exchange. The show route receive-protocol bgp [neighbor-address] command shows all the routes received from a neighbor before any import policies have been applied.
To see the routes that have been accepted and installed in the routing table, you use show route protocol bgp. To see what you are advertising to a neighbor, the command is show route advertising-protocol bgp [neighbor-address]. This shows the routes after any export policy has been applied. When a route is not being learned or advertised as expected, the issue often lies with the routing policy. Carefully analyzing the configured policies and using these verification commands to check the routing information at each step of the process is a critical troubleshooting methodology that you must master for the JN0-362 exam.
Introduction to Multiprotocol Label Switching (MPLS)
Multiprotocol Label Switching (MPLS) is a core technology in virtually every modern service provider network. It was initially developed to improve the speed of packet forwarding by making decisions based on short, fixed-length labels instead of performing complex IP lookups. While modern hardware has largely negated this original speed advantage, MPLS has become indispensable for the services it enables, such as Virtual Private Networks (VPNs) and Traffic Engineering (TE). The JN0-362 exam requires a solid understanding of MPLS theory, operation, and its role as a foundational platform for delivering advanced services.
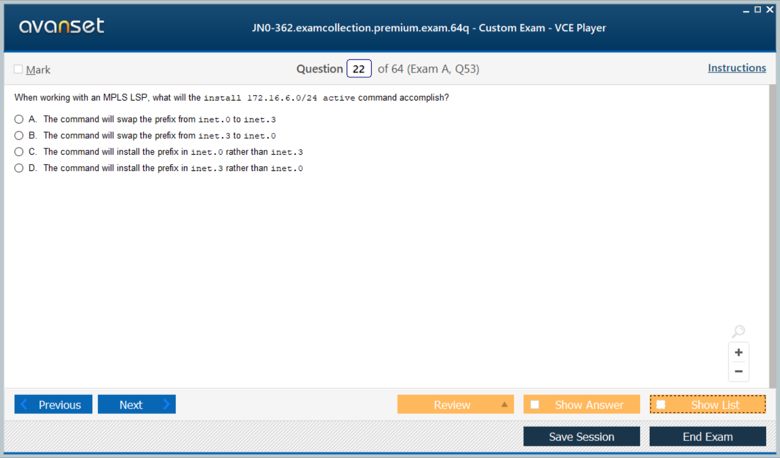
At its core, MPLS works by prepending a label to a packet at the ingress edge of the network and then forwarding the packet based solely on this label within the MPLS core. Routers in the core, known as Label Switching Routers (LSRs), perform a simple label swap operation: they look at the incoming label, find the corresponding outgoing label in a table, and forward the packet out the correct interface. This process continues until the packet reaches the egress edge router, which removes the label and forwards the original IP packet towards its final destination. This path that a labeled packet takes is called a Label Switched Path (LSP).
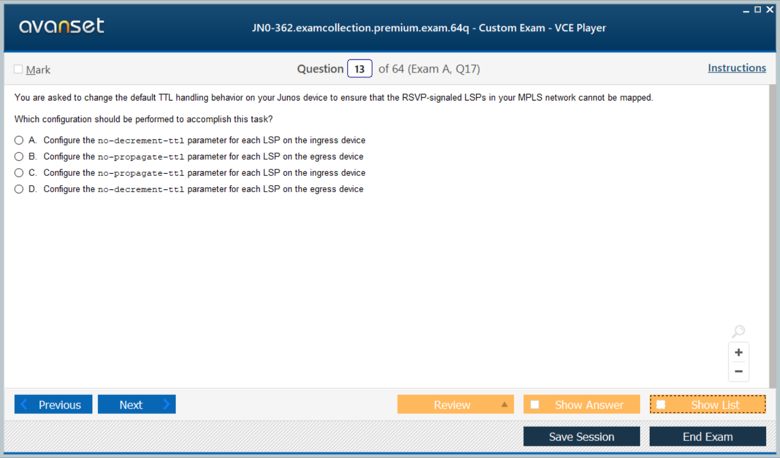
The MPLS Architecture: LDP, RSVP, and LSPs
For MPLS to function, the routers in the network need a way to distribute and agree upon the labels that will be used. This is accomplished using a label distribution protocol. The two main protocols covered in the JN0-362 are the Label Distribution Protocol (LDP) and the Resource Reservation Protocol with Traffic Engineering extensions (RSVP-TE). LDP is the simpler of the two. It works in conjunction with the existing IGP. As routers learn IP prefixes from the IGP, LDP automatically assigns a label for each prefix and advertises these label bindings to its LDP neighbors. This dynamically builds LSPs that follow the IGP's shortest path.
RSVP-TE, on the other hand, is used to build explicitly routed LSPs for traffic engineering purposes. With RSVP, an administrator can define a specific path that traffic should take through the network, which may not be the IGP's shortest path. This is useful for load balancing or for directing traffic away from congested links. RSVP can also reserve bandwidth along the path, ensuring a certain quality of service for the traffic carried over the LSP. The JN0-362 expects candidates to understand the operational differences between LDP and RSVP and the scenarios in which each would be used.
Configuring and Verifying Basic MPLS Operations in Junos
Enabling MPLS on a Junos network is a relatively straightforward process. The first step is to enable MPLS on the core-facing interfaces of the routers that will participate in label switching. This is done under the [edit interfaces] hierarchy by adding family mpls. Next, you must configure a label distribution protocol. To enable LDP, you simply add the relevant interfaces under the [edit protocols ldp] hierarchy. LDP will then automatically form adjacencies with its neighbors on those links and begin exchanging labels. To enable RSVP, the interfaces are configured under [edit protocols rsvp].
Verification is crucial. To check that MPLS is operational on your interfaces, you can use the show mpls interface command. The status of LDP neighbor sessions can be checked with show ldp neighbor, and the label bindings learned via LDP can be viewed with show ldp database. For RSVP, the show rsvp neighbor and show rsvp session commands provide similar information. The most important verification step is to check the forwarding table for MPLS. The show route table mpls.0 command displays the MPLS label forwarding table, showing the incoming label, the outgoing label, and the next-hop for each LSP. This is a key skill for the JN0-362.
The Foundation of Layer 3 VPNs
One of the most powerful services built on top of an MPLS backbone is the Layer 3 Virtual Private Network (L3VPN). L3VPNs allow a service provider to offer private IP routing services to multiple customers over a shared public infrastructure, while keeping each customer's traffic completely isolated. This is achieved through a combination of several technologies. The first is the use of Virtual Routing and Forwarding (VRF) instances on the Provider Edge (PE) routers. A VRF is essentially a separate routing table for each customer, which ensures that one customer's routes are not leaked to another.
To keep the routes unique across different customers, especially when they use overlapping private IP address space, a Route Distinguisher (RD) is added to each prefix. The RD is an 8-byte value that prepends the customer's IPv4 prefix, creating a globally unique 12-byte address known as a VPN-IPv4 prefix. To control the import and export of these VPN routes into and out of the VRFs, Route Targets (RTs) are used. An RT is a BGP extended community that acts like a tag. Routes are exported from a VRF with a specific RT, and other VRFs are configured to import routes that have that same RT. Understanding RD and RT is fundamental for the JN0-362.
Configuring a BGP Layer 3 VPN Service
The exchange of VPN-IPv4 routes between PE routers is handled by Multiprotocol BGP (MP-BGP). MP-BGP is an extension to BGP that allows it to carry routing information for multiple address families, not just standard IPv4. In the context of an L3VPN, the PE routers establish an iBGP session between them and enable the vpn-ipv4 address family. When a PE router learns a route from a customer's Customer Edge (CE) device, it adds the appropriate Route Distinguisher and Route Target, and then advertises this VPN-IPv4 route to the other PE routers via MP-BGP.
On the receiving PE router, the MP-BGP process receives the VPN-IPv4 route. It checks the Route Target community attached to the route. If that RT matches one of the import RTs configured on a local customer VRF, the route is stripped of its RD and installed into that customer's VRF routing table. The PE then advertises the standard IPv4 route to the local CE device. The configuration involves setting up the VRF routing instance, defining the RD and RTs, configuring the PE-CE routing protocol (often BGP or a static route), and establishing the MP-BGP peering between the PE routers. This entire workflow is a core topic of the JN0-362.
Exploring Layer 2 VPN Technologies
In addition to L3VPNs, service providers also offer Layer 2 VPN services, which extend a Layer 2 domain (like an Ethernet VLAN) between customer sites over the MPLS backbone. The JN0-362 exam introduces two main types of L2VPNs: virtual private wire service (VPWS), also known as L2Circuit in Junos, and virtual private LAN service (VPLS). A L2Circuit provides a point-to-point Layer 2 connection between two customer sites. It behaves like a virtual leased line or a crossover cable, transparently carrying Layer 2 frames between the two locations.
VPLS, on the other hand, provides a multipoint-to-multipoint Layer 2 service. It creates a virtual Ethernet switch in the provider's cloud, allowing multiple customer sites to connect and behave as if they were all on the same local area network (LAN) segment. This is extremely useful for customers who want to manage their own IP routing but need Layer 2 adjacency between their geographically dispersed locations. Both L2Circuit and VPLS rely on the MPLS backbone for transport, using a two-label stack: an outer transport label to get across the core and an inner service label to identify the specific customer circuit or VPLS instance.
Configuring VPLS for Transparent LAN Services
Configuring a basic VPLS service in Junos involves several steps on the PE routers. First, a routing instance of type vpls is created. Within this instance, you must configure the interfaces that will connect to the customer CE devices. You also define a VPLS instance identifier (VPLS ID) which must be the same on all PE routers participating in that specific VPLS domain. Similar to L3VPNs, VPLS uses a Route Distinguisher for uniqueness and a Route Target to control membership in the VPLS instance.
The PE routers need a way to discover each other and signal the service labels. This is typically done using BGP. The PE routers advertise their VPLS membership information using BGP, and this allows for auto-discovery of all PEs that are part of the same VPLS instance. Once the signaling is complete, a full mesh of pseudowires (signaled via LDP) is established between all the PE routers in the VPLS instance. The PE routers can then perform MAC address learning on the customer-facing ports and forward Layer 2 frames to the correct remote PE router over the appropriate pseudowire. A foundational understanding of this setup is expected for the JN0-362.
Troubleshooting MPLS and VPNs for the JN0-362
Troubleshooting MPLS-based services requires a systematic approach. If a VPN service is down, you must check each layer of the technology stack. First, verify the underlying IGP. Is there IP reachability between the PE routers' loopback addresses? Next, check the label distribution protocol. Are the LDP or RSVP sessions established? Is there a valid LSP between the PE routers? The ping mpls command is an excellent tool for this. For example, ping mpls l3vpn
For L3VPN issues, verify the MP-BGP session between the PE routers. Use show bgp summary to check its state. Then, examine the VRF routing table (show route table
Mastering Class of Service (CoS) for the JN0-362
In a service provider network, not all traffic is created equal. Voice, video, and critical business data require preferential treatment over best-effort traffic like web browsing or file transfers. Class of Service (CoS) is the set of mechanisms used to provide this differentiated treatment. The JN0-362 exam requires a fundamental understanding of the Junos CoS architecture. This architecture can be broken down into several key components. First is classification, the process of identifying different types of traffic and assigning them to a specific Forwarding Class. This can be based on various fields in the packet header, such as DSCP values or MPLS EXP bits.
Once traffic is classified, it is assigned to a specific queue for transmission. Schedulers are then used to manage these queues, determining how much bandwidth each queue gets and in what order packets are serviced. This ensures that high-priority traffic is not delayed by lower-priority traffic. Finally, as packets leave the router, rewrite rules can be applied. Rewrites modify the CoS bits in the packet header (e.g., DSCP or EXP) to signal the desired per-hop behavior to the next router in the path. Understanding this flow of classification, scheduling, and rewriting is essential for the CoS portion of the JN0-362.
A Practical Look at Junos CoS Configuration
Configuring CoS in Junos is done under the [edit class-of-service] hierarchy. The process logically follows the packet flow. First, you define classifiers. A behavior aggregate (BA) classifier is commonly used, which maps incoming DSCP or EXP values to a specific forwarding class and loss priority. For example, you might map the voice-related DSCP value of EF (Expedited Forwarding) to a forwarding class named voice-traffic. Next, you configure schedulers and scheduler maps. Schedulers define the properties of a queue, such as its transmit rate, priority, and buffer size. A scheduler map then links each forwarding class to a specific scheduler.
Finally, you apply these components to the interfaces. The BA classifier is applied on the ingress interface to classify incoming traffic, and the scheduler map is applied on the egress interface to control how traffic is queued and sent out. Rewrite rules are also applied on the egress interface to mark the packets for the next hop. While the JN0-362 exam doesn't require expert-level CoS configuration skills, it does expect you to understand these components and be able to configure a basic policy to prioritize a specific type of traffic over another. Verification commands like show class-of-service interface are important for checking your configuration.
Understanding IP Multicast Fundamentals
IP multicast is an efficient method for delivering a single stream of traffic to multiple receivers simultaneously. Instead of the source sending a separate unicast packet to each recipient, it sends a single packet to a special multicast group address. The network infrastructure is then responsible for replicating the packet only where necessary to reach all the interested receivers. This is critical for services like IPTV and live video streaming. The JN0-362 covers the foundational protocols that enable IP multicast, primarily the Internet Group Management Protocol (IGMP) and Protocol Independent Multicast (PIM).
IGMP is used between a host (a receiver) and its first-hop router. It allows the host to signal to the router that it is interested in receiving traffic for a particular multicast group. The router then keeps track of which multicast groups have active listeners on its interfaces. PIM is the routing protocol used between routers to build the distribution tree for multicast traffic. It uses the unicast routing table to determine the reverse path back to the source of the multicast stream, which prevents loops and ensures efficient delivery. PIM has several modes, but PIM Sparse-Mode (PIM-SM) is the most common and the focus of the JN0-362.
Go to testing centre with ease on our mind when you use Juniper JN0-362 vce exam dumps, practice test questions and answers. Juniper JN0-362 Service Provider Routing and Switching, Specialist certification practice test questions and answers, study guide, exam dumps and video training course in vce format to help you study with ease. Prepare with confidence and study using Juniper JN0-362 exam dumps & practice test questions and answers vce from ExamCollection.
Top Juniper Certification Exams
Site Search: