- Home
- Checkpoint
- 156-215.77 Check Point Certified Security Administrator Dumps
Pass Your Checkpoint CCSA 156-215.77 Exam Easy!
Checkpoint CCSA 156-215.77 Exam Questions & Answers, Accurate & Verified By IT Experts
Instant Download, Free Fast Updates, 99.6% Pass Rate
Checkpoint CCSA 156-215.77 Practice Test Questions in VCE Format
| File | Votes | Size | Date |
|---|---|---|---|
File Checkpoint.Braindumps.156-215.77.vv2014-10-22.by.MARISELA.350q.vce |
Votes 327 |
Size 4.2 MB |
Date Oct 25, 2014 |
Checkpoint CCSA 156-215.77 Practice Test Questions, Exam Dumps
Checkpoint 156-215.77 (Check Point Certified Security Administrator) exam dumps vce, practice test questions, study guide & video training course to study and pass quickly and easily. Checkpoint 156-215.77 Check Point Certified Security Administrator exam dumps & practice test questions and answers. You need avanset vce exam simulator in order to study the Checkpoint CCSA 156-215.77 certification exam dumps & Checkpoint CCSA 156-215.77 practice test questions in vce format.
Decoding the Checkpoint 156-215.77 Exam: An Overview
The 156-215.77 exam is the official test associated with the Check Point Certified Security Administrator (CCSA) R77 certification. It serves as a foundational benchmark for IT professionals, validating their ability to install, configure, and manage Check Point Security Gateway and Management Software Blade systems on the Gaia operating system. Passing this exam demonstrates a comprehensive understanding of fundamental cybersecurity concepts, from creating security policies to monitoring network traffic. It is a critical first step for anyone aspiring to build a career in network security using Check Point's robust and widely deployed technologies.
Successfully navigating the 156-215.77 exam requires more than just theoretical knowledge; it demands hands-on familiarity with the Check Point environment. The certification confirms that an individual can effectively defend against network threats, manage user access, and ensure the secure operation of corporate networks. It covers the essential skills needed for the day-to-day administration of Check Point security solutions. For organizations, hiring professionals with this certification provides confidence that their security infrastructure is in capable hands, ensuring the integrity and availability of their critical digital assets. This makes the certification highly valuable in the competitive IT job market.
The Evolution of Check Point Certifications
Check Point has a long history of providing industry-leading security solutions, and its certification path has evolved alongside its technology. The R77 version, which the 156-215.77 exam is based on, represents a mature and stable iteration of their architecture. While newer versions like R80 and R81 have introduced significant changes, such as a unified console and a new policy management paradigm, the core principles learned in the CCSA R77 track remain incredibly relevant. Understanding the fundamentals of the three-tier architecture, stateful inspection, and the object-oriented approach of R77 provides a solid foundation for mastering any subsequent version.
Many organizations still operate on R77 or have environments that integrate with it, making knowledge of this version a practical and sought-after skill. The 156-215.77 exam specifically tests these foundational elements that are crucial for understanding how Check Point’s security philosophy is implemented. For professionals new to the ecosystem, starting with the R77 curriculum offers a structured learning path that builds concepts logically. It allows one to grasp the essentials of firewall policy, NAT, and VPN before moving on to the more advanced features and consolidated architecture of later releases.
Key Objectives of the 156-215.77 Exam
The 156-215.77 exam is meticulously designed to cover several critical domains of Check Point security administration. A primary objective is to test a candidate's understanding of Check Point's technology overview, including its unified security architecture and the function of different Software Blades. A major focus is on Security Policy Management, which involves creating and managing firewall rules, network objects, and security zones. Candidates must demonstrate proficiency in controlling network traffic and enforcing organizational security policies. This section is often considered the heart of the exam, as a well-configured policy is the backbone of any secure network.
Another key objective revolves around monitoring traffic and connections. The exam assesses your ability to use tools like SmartView Tracker and SmartView Monitor to analyze logs, identify security events, and troubleshoot connectivity issues. Furthermore, the 156-215.77 exam covers Network Address Translations (NAT), requiring you to understand and configure both hide NAT and static NAT to manage IP address allocation and secure internal resources. Finally, User Management and Authentication are tested, ensuring you can create user accounts, integrate with directory services, and implement identity-based security policies for granular access control.
Who Should Take the 156-215.77 Exam?
The 156-215.77 exam is tailored for a specific audience of IT professionals whose roles involve securing network environments. System administrators responsible for the daily operation of servers and network services will find the CCSA certification invaluable for understanding how to protect their infrastructure. Network engineers who design and maintain network topologies will benefit by learning how to integrate robust security controls directly into their designs. The primary audience, however, is security engineers and analysts who are directly tasked with managing, monitoring, and responding to threats using Check Point solutions. This exam provides them with the validated skills needed for their roles.
Beyond these core roles, IT managers who oversee security teams can also benefit from understanding the concepts covered in the 156-215.77 exam. This knowledge enables them to better communicate with their technical staff, understand resource requirements, and make informed decisions about security strategy. Essentially, any professional who installs, configures, or manages Check Point firewalls as part of their job function is an ideal candidate. It is the definitive starting point for anyone seeking to specialize in one of the most respected security platforms in the industry.
Understanding the Exam Format and Structure
To succeed on the 156-215.77 exam, it is crucial to understand its format. The exam typically consists of 90 multiple-choice questions that must be answered within a 90-minute timeframe. This structure requires both accurate knowledge and efficient time management. The questions are designed to test a wide range of skills, from recalling specific configuration steps to applying concepts to solve practical, scenario-based problems. The passing score is generally 70%, meaning a candidate must answer at least 63 questions correctly. There is no partial credit for answers, so each question demands careful consideration.
The questions are delivered through a secure testing platform at a designated proctored testing center. The interface allows you to navigate between questions and flag those you are unsure about, enabling you to return to them later if time permits. This feature is particularly useful for managing your time effectively; you can answer the questions you are confident about first and then dedicate the remaining time to more challenging ones. Familiarizing yourself with this format through practice exams is a key strategy for reducing anxiety and improving performance on the actual 156-215.77 exam day.
Foundational Concepts in Check Point Architecture
At the core of the 156-215.77 exam curriculum is Check Point's three-tier architecture, a fundamental concept that separates management, enforcement, and presentation functions. The first tier is the Security Management Server, which acts as the central brain of the operation. It is where security policies are created, objects are defined, and logs are stored and correlated. This centralized approach allows administrators to manage multiple security gateways from a single point, ensuring consistency and simplifying administration. The exam will test your understanding of the Security Management Server's role and its database.
The second tier is the Security Gateway, which is the enforcement point of the architecture. This is the actual firewall appliance or software that sits on the network, inspecting traffic and enforcing the security policy downloaded from the Security Management Server. It makes real-time decisions on whether to allow or block traffic based on the established rule base. The third tier is the SmartConsole, a suite of graphical user interface tools, including SmartDashboard and SmartView Tracker, used by administrators to interact with the Security Management Server. Understanding how these three components communicate and work together is essential for passing the 156-215.77 exam.
Navigating the SmartDashboard Interface
SmartDashboard is the primary graphical tool used for policy management in the R77 environment, and proficiency with it is a major focus of the 156-215.77 exam. This application is part of the SmartConsole suite and provides the interface for creating and managing all aspects of the security policy. When you first open SmartDashboard, you are presented with a layout that includes panes for network objects, services, resources, and the central rule base. A significant portion of your exam preparation should involve becoming intimately familiar with navigating this interface to perform various administrative tasks.
The core of SmartDashboard is the rule base, which is a top-down list of rules that dictate how traffic is handled. Each rule is composed of several elements, including source, destination, service, and action. A key concept tested in the 156-215.77 exam is object-oriented management. Instead of using raw IP addresses in rules, you create reusable objects representing hosts, networks, or services. This approach makes the policy more readable, manageable, and less prone to errors. Understanding how to create, group, and effectively use these objects is a critical skill for any Check Point administrator.
The Importance of a Strong Security Policy
The philosophy behind a Check Point security policy is to deny all traffic by default and only permit what is explicitly required for business operations. This "default deny" stance is a cornerstone of robust network security. The 156-215.77 exam heavily emphasizes your ability to translate business requirements into a secure and efficient security policy. This involves not only creating rules to allow necessary traffic but also structuring the rule base logically to ensure it is easy to manage and troubleshoot. A well-designed policy is both secure and efficient, minimizing its impact on network performance.
A critical aspect of policy design tested in the exam is the use of a "Stealth Rule" and a "Cleanup Rule." The Stealth Rule is typically placed at the top of the policy to explicitly block any direct traffic to the firewall, protecting the gateway itself from attack. The Cleanup Rule is placed at the very bottom of the rule base to explicitly deny and log any traffic that has not been matched by any of the preceding rules. This ensures that no unintended traffic is allowed through the firewall and that all denied traffic is logged for analysis, providing visibility into potential threats.
Setting Up a Lab Environment for 156-215.77 Exam Practice
Theoretical knowledge alone is insufficient to pass the 156-215.77 exam; practical, hands-on experience is essential. Setting up a home lab environment is the most effective way to gain this experience. Using virtualization software like VMware Workstation, Player, or Oracle VirtualBox, you can create a virtual network that simulates a real-world corporate environment. Your lab should consist of at least three virtual machines: one for the Security Management Server, one for the Security Gateway, and one or two "client" machines to generate traffic and test your policies. This setup allows you to practice every concept covered in the exam.
Check Point provides evaluation licenses for their software, allowing you to install and use the full suite of tools for a limited time, which is perfect for study purposes. The ISO files for the Gaia operating system can be found on their support site. You will need a computer with sufficient RAM and CPU resources to run multiple virtual machines simultaneously. Building this lab, configuring the initial setup, and then using it to work through study guide exercises will solidify your understanding and build the muscle memory needed to confidently answer practical questions on the 156-215.77 exam.
Initial Steps to Prepare for Success
Embarking on the journey to pass the 156-215.77 exam requires a structured approach. The first step is to acquire the official study materials. Check Point offers its own official courseware, which is the most authoritative source of information. Augment this with reputable third-party study guides and video courses that align with the CCSA R77 curriculum. Once you have your materials, create a realistic study schedule. Allocate specific times each week to read the material, watch videos, and, most importantly, work in your lab environment. Consistency is more effective than cramming.
As you begin your studies, focus on understanding the "why" behind the concepts, not just memorizing the "how." For example, understand why a Stealth Rule is important, not just how to create one. Join online forums and study groups to connect with others who are also preparing for the 156-215.77 exam. Discussing challenging topics can provide new perspectives and clarify your understanding. Finally, from the very beginning, plan to use practice exams as a tool to gauge your progress. These tests will help you identify your weak areas, allowing you to focus your study efforts more effectively and build your confidence for the final test.
Deep Dive into Security Policy Management
Security Policy Management is the most critical skill set tested on the 156-215.77 exam. It forms the core of a security administrator's daily responsibilities and is the primary mechanism for controlling traffic flow through a Check Point Security Gateway. The policy itself is a collection of rules, organized in a Rule Base, that dictates how the gateway inspects and handles network packets. Mastering this domain requires a thorough understanding of how rules are structured, evaluated, and installed. A candidate must demonstrate not only how to create rules but also how to design a policy that is secure, efficient, and scalable.
The exam will present various scenarios requiring you to build or troubleshoot a security policy. This involves more than just selecting the right source, destination, and service. It requires an understanding of the implicit rules that are active by default, the importance of rule order, and the function of different actions like "Accept," "Drop," and "Reject." A deep dive into this topic means moving beyond the basics and learning how to leverage features like policy layers and application control to create granular and sophisticated security postures, all of which are key to success in the 156-215.77 exam.
Creating and Managing Network Objects
The object-oriented nature of Check Point's policy management is a fundamental concept that simplifies administration and is heavily featured in the 156-215.77 exam. Instead of using static IP addresses, MAC addresses, or port numbers directly within the Rule Base, you create reusable objects to represent them. These objects can be a single host, a network, a range of IP addresses, or a group containing other objects. This approach makes the security policy far more readable and intuitive. For example, instead of a rule showing "Source: 192.168.1.10," it can show "Source: Web-Server-01."
Effective object management is crucial for maintaining a clean and efficient Rule Base. The exam will test your ability to create different types of objects, such as network objects, service objects, and time objects. You will need to know how to group objects together, for instance, creating a group for all servers in the finance department. This allows you to apply a single rule to the entire group rather than creating multiple individual rules. This not only saves time but also significantly reduces the chance of error when updating the policy, a key best practice for any security administrator.
Constructing an Effective Firewall Rule Base
An effective firewall Rule Base is the heart of your network's defense, and constructing one is a primary skill evaluated by the 156-215.77 exam. Each rule in the base is a statement that tells the Security Gateway what to do with specific traffic. A rule is defined by its core components: Source, Destination, VPN, Service/Application, Action, Track, and Install On. The Source and Destination define the origin and target of the traffic, while the Service defines the protocol or port being used. The Action field determines whether the traffic is accepted, dropped, or rejected.
Best practices in Rule Base construction are essential knowledge for the exam. This includes the implementation of a Stealth Rule at the top of the policy to protect the gateway itself from direct connections. Another critical component is the Cleanup Rule at the bottom, which should be set to "Drop" and "Log" any traffic not explicitly permitted by the rules above it. This enforces a "default deny" security posture. Understanding how to structure rules for different network zones, such as a Demilitarized Zone (DMZ), and how to comment and document your rules for clarity are also important aspects of a professional approach.
Understanding the Logic of Policy Evaluation
A key part of the 156-215.77 exam is understanding precisely how a Check Point Security Gateway processes traffic against the installed policy. The gateway evaluates the Rule Base sequentially from top to bottom. When a packet arrives, the gateway compares its attributes (source IP, destination IP, protocol, etc.) against the first rule. If the packet matches all the criteria of the first rule, the gateway applies the specified action (e.g., Accept or Drop) and stops processing. This is known as the "first match" principle. If there is no match, it moves to the second rule, and so on.
This top-down processing logic has critical implications for policy design. A broad "allow" rule placed at the top of the policy could inadvertently permit malicious traffic, effectively overriding more specific "deny" rules placed below it. Therefore, the general best practice is to place the most specific rules at the top of the Rule Base and the more general rules towards the bottom. The exam will often present scenario-based questions with a sample Rule Base and ask you to predict how a certain type of traffic will be handled, testing your understanding of this fundamental processing logic.
Implementing Application Control and URL Filtering
Modern network security goes beyond simple port and protocol filtering. The 156-215.77 exam requires knowledge of Check Point's Software Blade architecture, specifically the Application Control and URL Filtering blades. These blades provide more granular control over network traffic by identifying and managing specific applications and web categories, regardless of the port they use. For example, you can create a rule that allows general web browsing on port 80 but specifically blocks peer-to-peer file-sharing applications that also use that port. This capability is crucial for enforcing acceptable use policies and mitigating threats.
To prepare for the exam, you must be familiar with how to enable these Software Blades on a Security Gateway and integrate them into the security policy. This involves using the Applications and URL Filtering tab within a rule to select specific applications, categories of applications, or website categories. You might be asked how to create a policy that allows access to business-related social media sites while blocking access to gaming sites. This demonstrates a deeper level of security administration, moving from network-level control to application-level awareness, a key evolution in firewall technology.
Managing Policy Layers and Inline Layers
As a security policy grows in complexity, managing a single, long Rule Base can become cumbersome. The 156-215.77 exam touches upon the concept of policy layers as a method for better organization and delegation. In R77, you can create ordered layers, where each layer is a sub-policy with its own set of rules. The gateway processes the rules in the first layer, then the second, and so on. This allows administrators to group rules by function, such as creating one layer for corporate access rules and another for rules governing internet traffic from the guest network.
A more advanced concept is the use of inline layers. An inline layer is essentially a sub-policy that is referenced within a single rule in the parent policy. When traffic matches the parent rule, it is then evaluated against the set of rules within the inline layer. This is particularly useful for delegating administrative tasks. For example, a senior network administrator can create the main policy structure, while a junior administrator is given permission to manage only the rules within a specific inline layer for their department. Understanding this hierarchical approach to policy management is important for advanced topics on the 156-215.77 exam.
The Policy Installation Process Explained
Creating or modifying a security policy in SmartDashboard is only the first step. For the changes to take effect, the policy must be installed on the Security Gateways. The 156-215.77 exam requires you to understand the steps involved in this critical process. When an administrator clicks the "Install Policy" button, the Security Management Server initiates a multi-stage procedure. First, it performs a verification process, checking the policy for any logical errors or conflicting rules that could cause security issues or network outages. This helps prevent administrators from inadvertently locking themselves out of the system.
If the verification is successful, the Security Management Server compiles the policy. This involves converting the high-level rules and objects from the graphical interface into a low-level, machine-readable inspection code that the Security Gateway can execute with maximum efficiency. Finally, the compiled policy is securely transferred and loaded onto the designated Security Gateways. The exam may test your knowledge of how to troubleshoot common policy installation failures, such as communication errors between the management server and the gateway, or license-related issues that prevent a blade's policy from being installed.
Leveraging Time Objects and Dynamic Objects
A static security policy may not always meet the dynamic needs of a business. The 156-215.77 exam expects candidates to know how to create rules that are time-sensitive. This is achieved using Time Objects. A Time Object defines specific hours of the day or days of the week. This object can then be placed in the "Service" column of a rule. For example, you could create a rule that allows employees to access certain recreational websites only during their lunch break. This adds a layer of flexibility to policy enforcement, allowing for different access levels at different times.
Another powerful feature is the use of Dynamic Objects. These are special objects that act as placeholders in the security policy. Their IP addresses are not defined on the Security Management Server but are fed to the Security Gateway from an external source or through an API. This is useful for environments where IP addresses change frequently, such as in a cloud environment or when dealing with threat intelligence feeds that provide lists of malicious IP addresses. While a deep technical implementation is more of an advanced topic, being aware of their purpose and function is beneficial for the 156-215.77 exam.
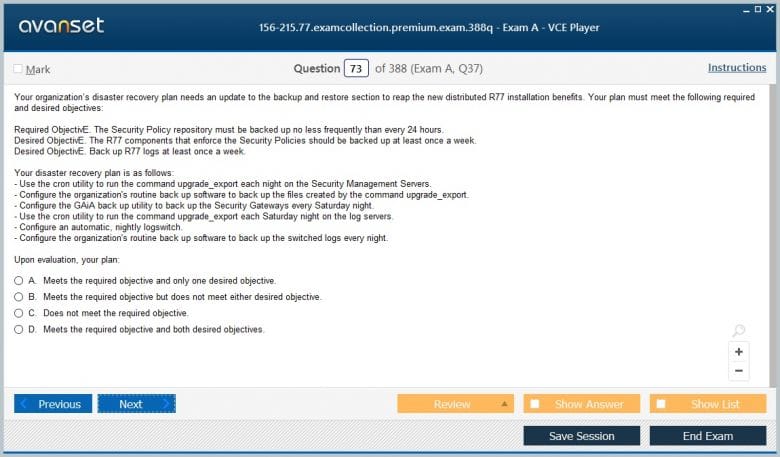
Backup, Restore, and Revision Control of Security Policies
Mistakes happen, and hardware fails. Therefore, having a robust backup and recovery strategy is a critical administrative function tested in the 156-215.77 exam. Check Point provides tools to back up the entire configuration of the Security Management Server, including the security policy, all network objects, and user databases. You need to know how to initiate a backup and, just as importantly, how to restore from one in case of a server failure. This ensures business continuity and minimizes downtime. Backups can be performed from the command line or through the Gaia web interface.
In addition to full backups, SmartDashboard has a built-in feature for database revision control. Every time an administrator saves changes to the policy, the Security Management Server saves a new version. The "Policy Versions" view allows you to see a history of all changes, view differences between versions, and revert the entire policy to a previous known-good state. This is an invaluable tool for troubleshooting issues that arise after a policy change. For the 156-215.77 exam, understanding how to use this feature to roll back a problematic policy change is a key skill.
Practical Scenarios for the 156-215.77 Exam
To tie all these concepts together, the 156-215.77 exam will present practical scenarios. You might be given a network diagram and a set of requirements and asked to design a portion of a Rule Base. For example, a company wants to host a web server in a DMZ. You would need to create the necessary network objects for the server and the DMZ network. Then, you would construct a rule that allows inbound HTTP and HTTPS traffic from "Any" source to the web server. You would also need a rule allowing the web server to access a database server in the internal network, but only on the specific SQL port.
Another common scenario involves troubleshooting. You might be shown a Rule Base and a log entry showing that legitimate traffic is being dropped. Your task would be to analyze the rules and their order to identify the misconfiguration. Perhaps a broad "deny" rule is placed above a more specific "allow" rule, or the service object used in the rule is incorrect. Working through these types of exercises in your lab environment is the best way to prepare for the problem-solving questions you will face on the 156-215.77 exam.
Understanding Network Address Translation (NAT)
Network Address Translation, or NAT, is a fundamental networking technology and a crucial topic for the 156-215.77 exam. Its primary purpose is to modify IP address information in packet headers while they are in transit across a routing device. The most common use of NAT is to conserve the limited number of public IPv4 addresses. A company can use a large range of private, non-routable IP addresses (like 192.168.x.x) for its internal network and use NAT on its gateway to translate all outbound traffic to appear as if it is coming from a single public IP address.
The 156-215.77 exam requires a clear understanding of the two main types of NAT. The first is Source NAT (SNAT), where the source IP address of a packet is rewritten. This is typically used for internal clients accessing the internet. The second is Destination NAT (DNAT), where the destination IP address is rewritten. This is commonly used to make an internal server, which has a private IP address, accessible from the external internet via a public IP address. Grasping the distinction and the specific use cases for each is essential for correctly answering NAT-related questions.
Configuring Hide NAT in the 156-215.77 Exam Context
Hide NAT is Check Point's terminology for a specific type of Source NAT, also known as Port Address Translation (PAT) or NAT Overload. This is the most common form of NAT used to allow multiple internal clients to access the internet using a single public IP address. The gateway "hides" the private source IP addresses of the internal clients behind its own external IP address. To keep track of the different sessions, it also translates the source port number, ensuring that return traffic is correctly sent back to the original client. This one-to-many translation is a key concept for the 156-215.77 exam.
Configuration of Hide NAT within SmartDashboard can be done automatically or manually. The automatic method is simpler and often configured directly within the network object for the gateway itself. However, manual NAT rules provide more granular control and are necessary for more complex scenarios. You will need to know how to create a manual NAT rule specifying the original source, destination, and service, and then defining the translated source. Understanding the processing order—specifically, that NAT rules are checked before the security policy firewall rules—is a critical piece of knowledge.
Implementing Static NAT for Internal Servers
While Hide NAT is for outbound connections, Static NAT is used for inbound connections. It creates a permanent, one-to-one mapping between a public IP address and a private IP address. This is essential for hosting services like web servers, email servers, or application servers on your internal network and making them accessible to the outside world. For the 156-215.77 exam, you must be able to configure Static NAT to forward incoming requests from a public IP address to the correct internal server. This is a common requirement for any organization with a public-facing presence.
Implementing Static NAT involves creating a manual NAT rule. The rule will state that for any traffic destined for a specific public IP address (the translated destination), the destination should be rewritten to the private IP address of the internal server. Crucially, configuring the NAT rule is only half the battle. You must also create a corresponding firewall rule in the security policy that allows the traffic to pass through to the newly translated destination. The exam will often test your understanding of this two-part process, as forgetting the firewall rule is a common administrative mistake.
Troubleshooting Common NAT Issues
Because NAT modifies packet headers, it can sometimes be a source of complex connectivity problems. The 156-215.77 exam will likely test your ability to troubleshoot these issues. A common problem is an incorrectly ordered or poorly defined NAT rule. For example, a broad Hide NAT rule placed above a more specific Static NAT rule might incorrectly translate traffic intended for an internal server, causing the connection to fail. Understanding how to analyze the NAT rule base to find such conflicts is a key skill. You should be familiar with the logical flow of NAT rule processing.
Another frequent issue arises from the interaction between NAT and the security policy. An administrator might correctly configure the NAT rule but create an incorrect firewall rule. For instance, the firewall rule might use the pre-NAT (public) IP address in the destination field instead of the post-NAT (private) IP address, causing the gateway to drop the traffic after it has been translated. Using SmartView Tracker to analyze logs is the primary method for diagnosing these problems. You need to be able to identify log entries that show a successful NAT translation but a subsequent drop by the firewall policy.
Introduction to User Management and Authentication
Securing a network based solely on IP addresses is no longer sufficient in a modern, mobile-centric world where users and devices are dynamic. The 156-215.77 exam covers the important topic of identity-based security, which begins with user management and authentication. This involves creating policies that are based on user identity rather than just a machine's IP address. This allows for much more granular control. For example, you can grant members of the "Finance" group access to financial servers, regardless of the computer they are using to log in.
The first step in this process is creating user definitions within the Check Point environment. In SmartDashboard, you can create user objects, define user groups, and manage authentication credentials. The exam will expect you to know how to perform these basic user management tasks. You should be familiar with creating a user template to enforce password complexity and other security settings. This foundational knowledge is the precursor to implementing more advanced features like Identity Awareness and creating identity-based firewall rules.
Configuring Different User Authentication Methods
Once users are defined, the gateway needs a way to authenticate them to verify their identity. The 156-215.77 exam covers several authentication methods. The simplest form is User Authentication (UserAuth), where a user trying to access a resource through the firewall is redirected to a web portal to enter a username and password. Another method is Client Authentication (ClientAuth), which prompts the user for credentials via a pop-up window. This method is more transparent but requires a small agent to be pushed to the client machine.
A third key method is Agent-based authentication, where a dedicated agent is installed on the user's workstation. This agent securely communicates the user's identity to the gateway when they log into their computer, providing a seamless single sign-on experience. Knowing the differences between these methods, their respective user experiences, and the scenarios where each is most appropriate is crucial. For example, UserAuth might be suitable for a guest network, while agent-based authentication is better for corporate employees.
Integrating with Identity Sources like Active Directory
Manually creating and managing user accounts in Check Point is not scalable for large organizations. A more efficient and secure approach is to integrate with an existing identity source, such as a Microsoft Active Directory server. The 156-215.77 exam requires you to understand the concept of the Identity Awareness Software Blade, which enables this integration. By connecting the Check Point management server to an Active Directory domain controller, you can pull user and group information directly from the directory.
This integration allows you to create firewall rules using the same user groups that are already defined in Active Directory. When a user logs into the domain, the gateway can identify them through various methods and apply the appropriate security policy. This simplifies administration immensely, as user management is centralized in Active Directory. For the exam, you need to understand the benefits of this integration and the basic steps required to configure the connection to an LDAP or Active Directory server, a common task in enterprise environments.
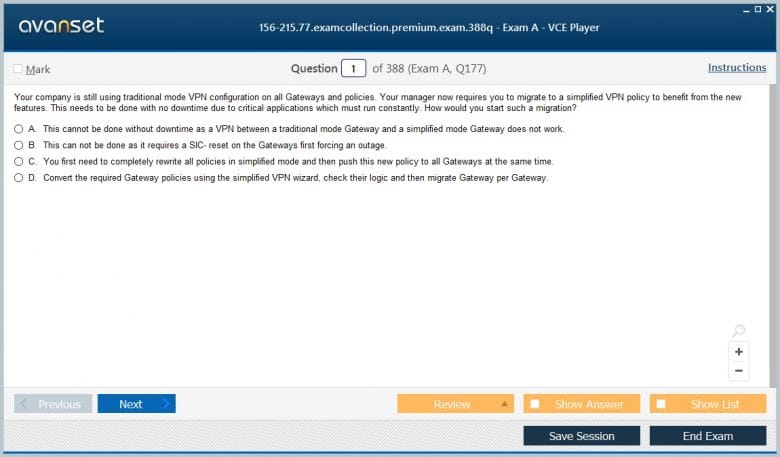
Fundamentals of Virtual Private Networks (VPN)
A Virtual Private Network (VPN) is a technology used to create a secure, encrypted connection over a less secure network, such as the public internet. VPNs are essential for two primary use cases: securely connecting remote offices (Site-to-Site VPN) and allowing remote users to securely access corporate resources (Remote Access VPN). The 156-215.77 exam focuses on the fundamentals of Site-to-Site VPNs, which are built using the IPsec protocol suite. You need to understand the core concepts that provide security for the VPN tunnel.
These core concepts are often referred to as the pillars of a VPN. The first is Confidentiality, which is provided by encryption algorithms (like AES) to ensure that the data cannot be read by unauthorized parties. The second is Integrity, which uses hashing algorithms (like SHA-256) to ensure that the data has not been altered in transit. The third is Authentication, which verifies that the two gateways establishing the tunnel are who they claim to be, often using pre-shared keys or digital certificates. Understanding these three pillars and the protocols that provide them is fundamental.
Building a Site-to-Site VPN with Check Point Gateways
A major practical skill tested on the 156-215.77 exam is the configuration of a Site-to-Site VPN between two Check Point gateways. Check Point simplifies this process through the use of VPN Communities. The most common type is the Meshed Community, where every gateway in the community can form a VPN tunnel with every other gateway. Another type is the Star Community, where smaller satellite gateways can only form tunnels to a central hub gateway, but not to each other. You will need to know which community type is appropriate for a given network topology.
The configuration involves several steps. First, you must ensure the gateways are created as interoperable Check Point objects. Next, you define the VPN community and add the gateways to it. A critical step is defining the encryption domain for each gateway. The encryption domain is the set of internal networks behind the gateway that should be accessible through the VPN. Finally, you must create firewall rules that specify which traffic is allowed to pass through the VPN tunnel. The exam will test your knowledge of this entire workflow.
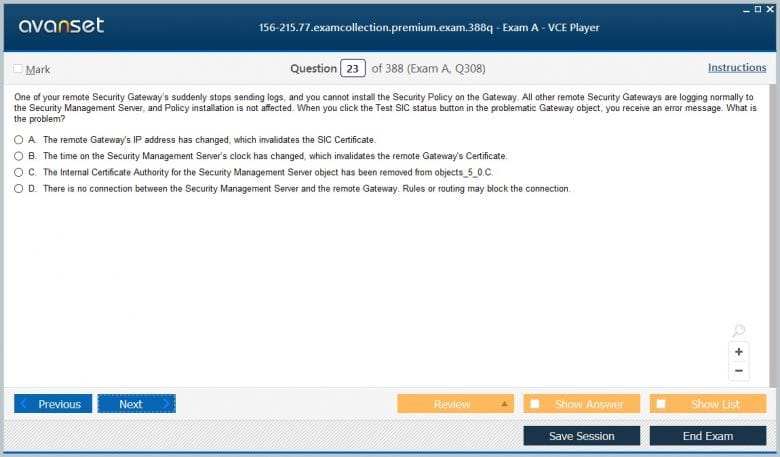
Monitoring and Troubleshooting VPN Tunnels
Once a VPN is configured, administrators must be able to monitor its status and troubleshoot any connectivity issues. The 156-215.77 exam expects you to be familiar with the tools available for this purpose. The primary graphical tool is SmartView Monitor, which provides a real-time view of tunnel status, showing which tunnels are active and which are down. For more detailed analysis, SmartView Tracker is used to view the logs related to the IKE (Internet Key Exchange) negotiation process, which establishes the secure tunnel. These logs can reveal why a tunnel is failing to come up.
From the command line, the vpn tu (TunnelUtil) utility is an essential troubleshooting tool. This interactive program allows you to list active tunnels, delete security associations (SAs) to reset a problematic tunnel, and perform other diagnostic tasks. The VPN negotiation process occurs in two phases: Phase 1 establishes a secure management channel, and Phase 2 negotiates the security parameters for the actual data tunnel. Being able to identify whether a failure is happening in Phase 1 or Phase 2 is a key troubleshooting skill that the 156-215.77 exam may evaluate through scenario-based questions.
The Role of SmartView Monitor
SmartView Monitor is Check Point's dedicated tool for real-time status monitoring, and understanding its capabilities is a key component of the 156-215.77 exam curriculum. This tool provides a live dashboard of the health and performance of the security environment. Administrators use it to view the status of Security Gateways, check CPU and memory utilization, and see the number of current connections. It offers a quick, at-a-glance perspective on whether the security infrastructure is operating within normal parameters. This is the first place an administrator would look to investigate reports of a network slowdown or outage.
The exam requires you to be familiar with the different views available within SmartView Monitor. You can set up custom views to display the specific metrics that are most important to your organization. One of its most powerful features is the ability to see traffic counters on firewall rules in real time, which helps in identifying which rules are being hit most frequently. It is also the primary tool for monitoring the status of VPN tunnels and other critical system components. Proficiency in navigating SmartView Monitor demonstrates your ability to proactively manage the health of the security system.
Analyzing Traffic with SmartView Tracker
While SmartView Monitor provides real-time status, SmartView Tracker is the primary tool for historical log analysis. Every connection that passes through or is blocked by the Security Gateway can be logged, and SmartView Tracker is the interface used to query and view these logs. Mastering this tool is absolutely essential for passing the 156-215.77 exam. It is used for a wide range of critical tasks, from troubleshooting a user's connectivity issue to performing forensic analysis after a security incident. The exam will test your ability to interpret log entries and use the query tools effectively.
A log entry in SmartView Tracker contains a wealth of information, including the source and destination IP addresses, the service or port number, the rule number that matched the traffic, and the action taken (Accept, Drop, etc.). You must be able to read a log entry and understand precisely what happened to a specific packet. The tool's strength lies in its powerful filtering capabilities. You can build complex queries to find specific log entries, such as all traffic from a particular IP address that was dropped by the firewall in the last hour.
Differentiating Between Log Types: Firewall, Audit, and System
The 156-215.77 exam will expect you to know that Check Point generates several different types of logs, each serving a distinct purpose. The most common and frequently analyzed logs are the firewall logs. These are generated by the Security Gateway and provide a record of network traffic and the security policy decisions made about it. These are the logs you will spend most of your time with in SmartView Tracker, used for troubleshooting connectivity and investigating potential security events. They provide the "who, what, where, and when" of network traffic.
Beyond firewall logs, there are Audit logs. These are generated by the Security Management Server and track all administrative actions. Every time an administrator logs in, creates an object, modifies a rule, or installs a policy, an audit log is created. This provides a crucial trail for accountability and for understanding what changes were made to the system and by whom. Finally, System logs record events related to the health of the Check Point devices themselves, such as hardware issues, software process failures, or system reboots. Knowing where to look for different types of information is a key administrative skill.
Creating and Customizing Log Queries
The sheer volume of logs generated by a busy Security Gateway can be overwhelming. The ability to create precise queries to find the exact information you need is a skill tested by the 156-215.77 exam. SmartView Tracker features a query pane that allows you to build filters based on any field in the log entry. For example, you can filter for a specific source IP, a destination port, a particular action like "Drop," or traffic handled by a specific rule. You can also combine multiple criteria to create highly specific queries.
For instance, if you are troubleshooting why a user at IP address 10.1.1.5 cannot access a web server at 203.0.113.10, you could build a query where "Source" is "10.1.1.5" and "Destination" is "203.0.113.10". This would instantly show you all connection attempts between those two hosts and whether they were accepted or dropped. The exam may present a scenario and ask you which query you would use to find the relevant information, testing your practical application of the tool's features. Saving frequently used queries is also a useful feature for efficient administration.
The Logging and Status Software Blade
The foundation of all monitoring and analysis is the proper configuration of logging itself. The 156-215.77 exam requires an understanding of the Logging and Status Software Blade. This blade must be enabled on the Security Management Server to allow it to function as a Log Server, receiving and storing logs from the Security Gateways. It also needs to be enabled on the Security Gateways to instruct them to generate and forward their logs. You need to know how this communication is established and how to ensure logs are being sent correctly.
The configuration of logging also includes setting up log forwarding. In large environments, you might have a dedicated Log Server or integrate with a third-party SIEM (Security Information and Event Management) system. You must know how to configure the gateway to forward its logs to these external systems. Additionally, the tracking options within the firewall rules themselves are important. You can configure each rule to generate no log, a basic log, or a detailed log. Understanding how to set these tracking options to balance visibility with performance and storage considerations is a key administrative decision.
Generating Reports with SmartReporter
While SmartView Tracker is ideal for interactive log analysis, SmartReporter is the tool used for creating historical, summarized reports. This is an important function for management oversight and compliance purposes. The 156-215.77 exam will likely touch upon the capabilities of this tool. SmartReporter uses the log data collected by the Log Server to generate a wide variety of predefined reports, such as "Top 10 Blocked Websites," "Top Bandwidth Consuming Applications," or "Security Events Over Time." These reports provide valuable insights into network usage and the threat landscape.
In addition to the out-of-the-box reports, administrators can create custom reports tailored to their specific needs. You can define the report layout, choose the data to include, and schedule the report to be generated and emailed automatically on a daily, weekly, or monthly basis. For the exam, you should understand the purpose of SmartReporter, the types of information it can provide, and how it differs from the real-time, interactive analysis performed in SmartView Tracker. It serves a different audience and a different administrative purpose.
Understanding Check Point Licensing
Licensing is a practical aspect of Check Point administration that is often covered in the 156-215.77 exam. Every Check Point product and Software Blade requires a valid license to function correctly. The exam will test your understanding of the basic licensing model. Licenses are tied to the IP address of the management interface of the device they are for, whether it's a Security Management Server or a Security Gateway. You need to know how to generate a license on the Check Point support portal and how to apply it to the device.
There are two main licensing models: Central and Local. In a Central licensing scheme, all licenses are managed on the Security Management Server and are then attached to the appropriate gateway objects. This is the most common and recommended method. Local licensing involves applying a license file directly to the Security Gateway itself. SmartUpdate is the tool within the SmartConsole suite used to manage licenses, as well as software packages and hotfixes. You should be familiar with the SmartUpdate interface for adding, deleting, and viewing license information.
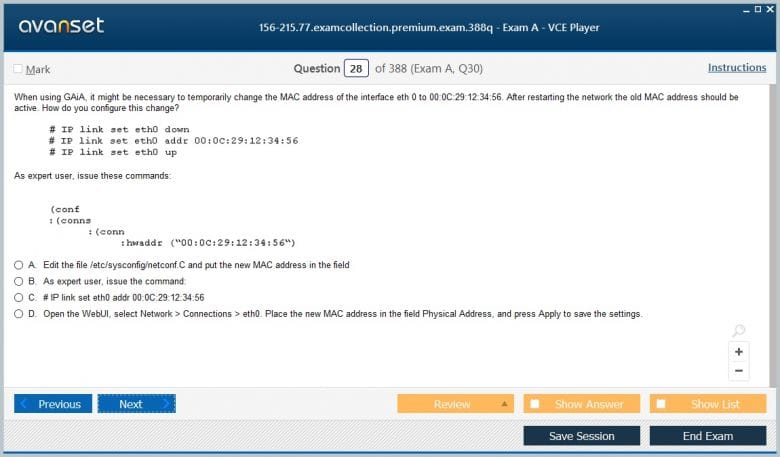
Using Command Line Tools for Monitoring
While the graphical tools are powerful, the 156-215.77 exam also expects some familiarity with the command line interface (CLI) for monitoring and basic troubleshooting. The CLI can be faster for experienced administrators and is essential when the graphical interface is unavailable. One of the most important commands is cpstat. This command provides a quick overview of the status of various Check Point applications and processes. For example, cpstat fw will show the status of the firewall module, including the policy name and installation time.
Other critical commands include fw ctl and vpn. The fw ctl command is a low-level tool used to view detailed statistics about the firewall kernel, such as the connections table. The vpn command, as discussed previously, is used to manage and troubleshoot VPN tunnels. While you are not expected to be a CLI expert for the CCSA level, you should be able to execute these basic commands and interpret their output to determine the health and status of a gateway, as this may be required to answer certain exam questions.
Interpreting Log Entries for Troubleshooting
The ability to look at a log entry in SmartView Tracker and immediately understand its meaning is perhaps the most important troubleshooting skill for a Check Point administrator. The 156-215.77 exam will test this skill repeatedly. For example, you might see a log entry with an action of "Drop" and the "Information" field stating "Rule 0 - Implied Rule." This tells you that the traffic was not dropped by any rule you created, but by the implicit cleanup rule, meaning no explicit rule existed to allow it.
Another example is seeing a log entry for traffic that you believe should be encrypted in a VPN. If the log shows the "Encryption" field as "Clear," it means the traffic did not match the VPN's encryption domain and was sent unencrypted over the internet. These small details in the log files are the clues you need to solve complex problems. Practicing log analysis in your lab is crucial. You should intentionally create misconfigurations and then use the logs to figure out what went wrong.
Preparing for Monitoring-Based 156-215.77 Exam Questions
To succeed on the monitoring and logging portion of the 156-215.77 exam, you should focus your preparation on practical application. Memorizing the names of the tools is not enough; you must know what each tool is used for and how to use it to solve a problem. The exam will present you with scenarios like "A user cannot access a website. Which tool would you use first to investigate, and what would you look for?" The correct answer involves using SmartView Tracker to filter for the user's IP and check for dropped packets.
Create a checklist of key monitoring tasks and practice them in your lab. This should include checking gateway status in SmartView Monitor, querying logs in SmartView Tracker, identifying administrator changes in the audit log, checking VPN tunnel status, and using basic CLI commands like cpstat. Being comfortable and efficient with these tasks will ensure you can quickly analyze the scenario-based questions on the exam and select the correct answer with confidence. This hands-on practice is the bridge between theoretical knowledge and exam success.
Go to testing centre with ease on our mind when you use Checkpoint CCSA 156-215.77 vce exam dumps, practice test questions and answers. Checkpoint 156-215.77 Check Point Certified Security Administrator certification practice test questions and answers, study guide, exam dumps and video training course in vce format to help you study with ease. Prepare with confidence and study using Checkpoint CCSA 156-215.77 exam dumps & practice test questions and answers vce from ExamCollection.
Checkpoint 156-215.77 Video Course

Top Checkpoint Certification Exams
Site Search:











is there any latest dumps for ccsa