- Home
- Popular IT Certifications
- Switch Administration & Layer 2 Protocols
How to troubleshoot switch administration & Layer 2 protocols
Switch 2 transitioning employs this mass media gain access to control address (MAC address) from host's multi level interface cards to make the decision to forward support. Layer 2 transitioning can be computer hardware centered, meaning knob use application-specific routine to make filtration system (also often known as MAC address tables as well as camera tables) effective. A good way to imagine the level 2 transition is as the multiport connect.
Layer 2 transitioning affords the following:
Hardware based bridging for MAC
Cable velocity
Excessive velocity
Minimal latency
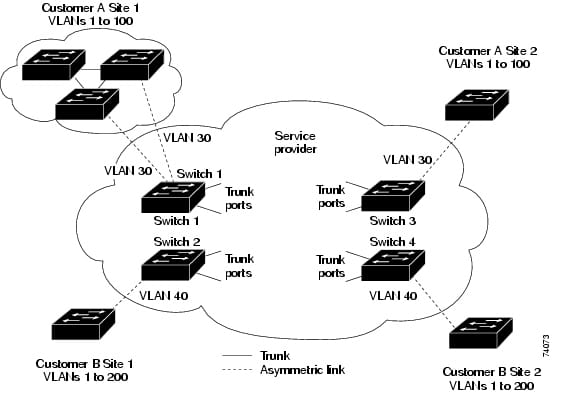
Layer 2 transitioning can be very effective mainly because there isn't a adjustment for the info supply, and then this frame encapsulation from the supply, and only in the event of the info supply, can be move through different mass media (such because by Ethernet to be able to FDDI). Layer 2 transitioning is utilized intended for workgroup on the web connectivity and multilevel segmentation (breaking upwards). This will give the slimmer multilevel layout with increased multilevel portions than regular 10BaseT contributed communities. Layer 2 transitioning offers helped produce fresh components from the multilevel facilities.
SDM Templates
You need to use SDM templates to configure system which means change to improve service intended for particular features, according to how a change is used inside circle. You possibly can decide on a theme to deliver maximum system consumption for a lot of characteristics as well as utilize the default theme for you to efective means.
In order to spend ternary content addressable memory space, it is intended for various usages, this change in SDM templates prioritize system means for you to improve service for sure features. You possibly can choose SDM templates for you to improve these kinds of features:
- Access-the gain access to theme boosts system means intended for gain access to command directories to match quite a few ACLs.
- Default-the default theme gives harmony to every characteristics.
- Routing-the direction finding theme boosts system intended for IPv4 unicast direction-finding, generally important for some sort of router as well as aggregator in the center of circle.
- VLANs-The VLAN theme hinders direction-finding as well as helps the ideal number of unicast MAC PC address. It would generally become decided on for any Layer 2 change.
Moreover, this combined IPv4 as well as IPv6 templates help some sort of combined heap setting. Begin to see the "Dual IPv4 as well as IPv6 SDM Templates" segment.
You'll find a couple of variations of every theme: some sort of desktop computer theme as well as an aggregator theme. Your Driver 3750-12S change will incorporate the use of the larger TCAM dimension accessible in aggregator templates as well as incorporate the use of the standard desktop computer templates. All Driver 3750 switches service merely use these desktop templates. If you do not enter this desktop computer key phrase on an aggregator change, this aggregator templates are decided on.
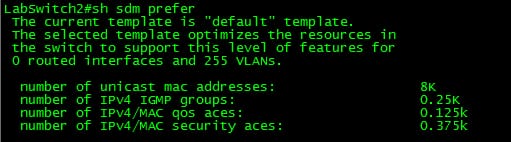
Since Catalyst 3750 can be employed in a number of different purposes, mobility inside TCAM subsystems resource portion is necessary. To this particular conclude, you will find 3 predefined SDM web themes which you can use to divide the TCAM to match the use of the Catalyst 3750. The initial the first is the redirecting theme which boosts the device assets regarding unicast redirecting. The actual redirecting theme would likely typically supply if the box can be used seeing that like a router or maybe course aggregator in the heart of the community. The actual VLAN theme would be the subsequent just one and with that theme, unicast redirecting is usually inept, enabling the most quantity of supported MAC PC address. The actual VLAN theme could be utilized if the swap has been utilized like a solely L2 device. Lastly there's the default theme a blend involving the redirecting and also VLAN web themes. That theme provides very good equilibrium involving L2 and also L3 features. The actual SDM favor course theme directions must be utilized when policy-based redirecting (PBR) is used for the swap. Or even then, directions for PBR will go away.
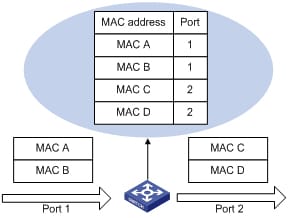
Managing MA C address table
This MAC target stand consists of target facts which the change uses to frontward traffic involving slots. Most MAC addresses in the target stand tend to be associated with a number of slots. This target stand contains these types of addresses:
- Energetic target: the source MAC target which the change discovers and then age ranges when it is not being used.
- Static target: the personally entered unicast target it does not age group and that is not lost when the change resets.
This target stand directories the particular location MAC target, the particular related VLAN NO, and interface number linked to the target and also the kind (static or dynamic).
Configuring the MAC address table
By default, MAC target learning is usually empowered about many interfaces and VLANs for the router. You can manage MAC target learning by using the software or VLAN to deal with the particular accessible MAC target stand area through handling which usually interfaces or VLANs can understand. Before you disable MAC target learning, be sure that you are familiar with the particular system topology and also the router method settings. Disabling MAC target learning by using software or VLAN could cause inundating in the system.
Stick to these kind of suggestions as soon as disabling MAC target learning by using an software or VLAN:
- Use caution before disabling MAC target learning by using an software or VLAN with a constructed change exclusive software (SVI). This change after that massive amounts many IP packets in the Coating two sector.
- You can disable MAC target learning about the same VLAN number via 1 to 4094 (for case, not any MAC pc address-table learning VLAN 223) or an array of VLAN IDs, segregated by way of a hyphen or comma (for case, not any MAC pc address-table learning VLAN 1-10, 15).
- We advice that you disable MAC target learning merely with VLANs with a couple of slots. When you disable MAC target learning over a VLAN with an increase of in comparison with a couple of slots, each supply going into the particular change is usually overloaded as VLAN sector.
You can't disable MAC target learning over a VLAN that is certainly employed in house with the router. When the VLAN number which you enter is definitely an inner VLAN, the particular change yields a mistake communication and rejects the particular command. To watch inner VLANs being used, enter the particular demonstrate VLAN inner use blessed EXEC command. - When you disable MAC target learning over a VLAN that also includes the safe interface, MAC target learning isn't handicapped about that will interface.
Troubleshoot Err - disable recovery
This document describes the errdisabled state, talks about how to endure it, and supplies degrees of errdisable retrieval. This document works by using this phrases errdisable as well as miscalculation disable interchangeably. Clients frequently contact Cisco Tech support team when they discover that one or more with their swap slots are getting to be miscalculation abled, so that this slots employ a status connected with errdisabled. These kinds of customers would like to know the reason why this miscalculation disablement occurred as well as how they may regain these slots to normal.
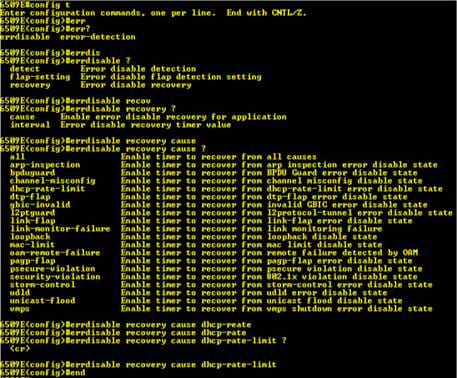
Causes of Errdisable:
This attribute was initially executed to address exclusive crash situations when the swap found excessive as well as later crashes over a dock. Abnormal crashes occur whenever a shape is decreased for the reason that swaps activities of sixteen crashes in a line. Later crashes occur right after each and every device within the line needs to have regarded that the line was at work with. Achievable factors that cause a lot of these errors include:
Some sort of cable tv which is out of options (either too much time, the incorrect sort, as well as defective).
An undesirable community user interface credit card (NIC) credit card (with actual problems as well as motorist problems).
Some sort of dock duplex mis-configuration.
Some sort of dock duplex mis-configuration is a frequent cause of this errors because of breakdowns to negotiate this velocity as well as duplex adequately among a pair of directly hooked up products (for case in point, any NIC that will links to your switch). Only half-duplex cable connections ought to ever before have crashes in a LAN. With the company sense many entry (CSMA) characteristics connected with Ethernet, crashes are usual intended for 50 percent duplex, so long as this crashes do not meet or exceed a percentage connected with site visitors.
CDP
CDP directs just about all packets on the L2 multicast handle regarding 01: 00: 0C: CLOSED CIRCUIT: CLOSED CIRCUIT: CLOSED CIRCUIT. For that reason, our filtration may be:
Ether number 01: 00: 0c: cc: cc: cc
Nonetheless, VTP (VLAN Trunking Protocol) furthermore directs packets to the handle. Because the default timer intended for VTP can be more than 200 a few moments, as well as the default timer intended for CDP can be 59 a few moments, this kind of shouldn't end up being a worry. Furthermore, considering that VTP packets are just posted out to you start ports, when you notice VTP packets over a vent which a person needs to be connected to, possibly you have simply just observed your short lived problem.
This Cisco Development Protocol (CDP) is usually a system finding project which goes over Layer 3 (the files website link layer) upon most Cisco-manufactured units (routers, bridges, accessibility machines, and switches). CDP will allow circle administration purposes to instantly find out and discover some other Cisco units associated with the particular circle.
LLDP
Link Level Breakthrough discovery Project, ALSO KNOWN AS 802. 1AB, is an IEEE typical. While Cisco doesn't support LLDP out of the field, it could be permitted with your Cisco equipment. HEWLETT PACKARD, Juniper, Dell, in addition to everyone else which i include ever before caused helps LLDP automatically. The actual L2 multicast handle intended for LLDP can be: 01: 60: C2: 00: 00: 0E. Nonetheless, LLDP possesses the benefit of an exceptional Ether Type. That will form can be: 0x88cc. Determined by of which information, we can easily filtration using possibly:
Ether number 01: 60: C2: 00: 00: 0E
The actual default timer intended for LLDP generally seems to change throughout suppliers, even though thirty a few moments will be the default intended for Cisco in addition to a number of other folks.
To aid non-Cisco units and also to accommodate interoperability involving some other units, the particular switch sustains the particular IEEE 802.1 AB LLDP. LLDP is usually a neighbor finding project that may be employed for circle units advertising specifics of independently to some other units for the circle. That project goes within the data-link level that allows a pair of techniques managing different circle level protocols to understand concerning 1 another.
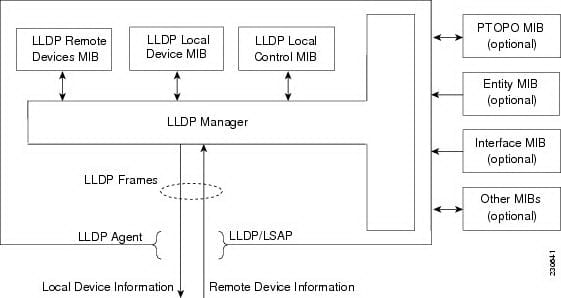
LLDP sustains a collection of attributes which it uses to find out neighbor units. These attributes incorporate sort, duration, and worth descriptions and they are called TLVs. LLDP reinforced units will use TLVs to receive and send out information on their neighbors. Particulars for example construction information, system features, and system personality is usually marketed by using this project.
UDLD
UDLD (Unidirectional Url Detection) is usually Cisco little-known off shoot pertaining to uncovering any mis-configured hyperlink. The concept at the rear of it really is very straight forward - let 2 changes to validate whenever they may both equally send out along with receive facts on the point-to-point relationship. Think about a circle together with 2 changes, A along with T hooked up by simply 2 hyperlinks: "A=B". Naturally, in the event that "A" could be the reason behind occupying tree, on the list of plug-ins on "B" is going to be blocking, continually getting BPDUs coming from "A". If this particular hyperlink might flip uni-directional along with "B" might begin missing these BPDUs, the particular port may ultimately unblock, being created any trap between "A" along with "B". Be aware that the problem together with unidirectional hyperlinks generally takes place on fiber-optical contacts and is particularly not popular on UTP (wired) contacts, where by hyperlink pulses utilized to keep an eye on the connection strength.
Approaches to Detect Unidirectional Back links
UDLD works by utilizing 2 things:
- Neighbor data source upkeep
UDLD discovers regarding other UDLD-capable neighbors by simply routinely transmitting any hi there packet (also called the advertising campaign or even probe) on just about every productive user interface to maintain every gadget advised regarding neighbors.
If the move receives any hi there information that caches the info before era time (hold time or even time-to-live) expires. In the event the move receives a fresh information previous to old cache access age groups, the particular move replaces the particular old access while using the brand-new a single.
Anytime the user interface is usually impaired along with UDLD is usually jogging, anytime UDLD is usually impaired by using an user interface, or even anytime the particular move is usually totally reset, UDLD clears most recent cache synonyms for that interfaces impacted by the particular configuration alter. UDLD communicates at least one information to see the particular neighbors to cleanse the particular component of the caches impacted by the particular reputation alter. Your information is supposed to maintain the particular caches synchronized.
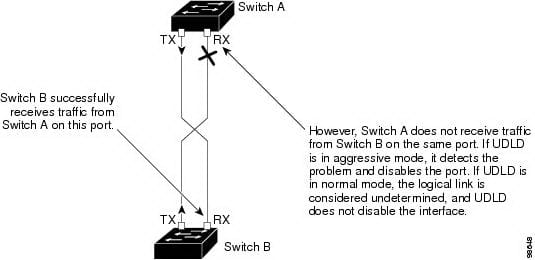
- Event-driven prognosis along with echoing
UDLD depends on echoing because it's prognosis device. If a UDLD gadget discovers about a brand-new friend or even receives any resynchronization obtain coming from the out-of-sync friend, that restarts the particular prognosis windowpane on its aspect in the relationship along with communicates reveal emails with reply. Due to the fact this particular habits could be the same on most UDLD neighbors, the particular sender in the echoes desires to obtain the reveal with reply.
Site Search:






