Pass Your CWNP CWSP-205 Exam Easy!
CWNP CWSP-205 Exam Questions & Answers, Accurate & Verified By IT Experts
Instant Download, Free Fast Updates, 99.6% Pass Rate
CWNP CWSP-205 Practice Test Questions in VCE Format
| File | Votes | Size | Date |
|---|---|---|---|
File CWNP.Testking.CWSP-205.v2015-07-28.by.Dumps.92q.vce |
Votes 20 |
Size 137.12 KB |
Date Jul 28, 2015 |
CWNP CWSP-205 Practice Test Questions, Exam Dumps
CWNP CWSP-205 (Certified Wireless Security Professional (CWSP)) exam dumps vce, practice test questions, study guide & video training course to study and pass quickly and easily. CWNP CWSP-205 Certified Wireless Security Professional (CWSP) exam dumps & practice test questions and answers. You need avanset vce exam simulator in order to study the CWNP CWSP-205 certification exam dumps & CWNP CWSP-205 practice test questions in vce format.
Mastering the CWNP CWSP-205 Exam: A Comprehensive Introduction
The CWSP-205 exam, which leads to the Certified Wireless Security Professional certification, is a highly respected credential in the IT industry. It is designed for professionals who want to demonstrate their expertise in securing enterprise wireless networks. This certification validates an individual's ability to identify, implement, and manage robust security solutions for Wi-Fi networks. Passing the CWSP-205 exam signifies a deep understanding of wireless security principles, from legacy protocols to modern, sophisticated defense mechanisms. It is a critical step for anyone aspiring to become a leader in the field of wireless network security. The exam curriculum is comprehensive, covering a wide array of topics essential for a security professional. It delves into the intricacies of WLAN discovery techniques, intrusion and attack methods, and the design of secure network architectures.
The CWSP-205 exam also tests knowledge of security policies, procedures, and monitoring tools. This breadth of knowledge ensures that certified individuals are not just theoreticians but are also capable of hands-on implementation and troubleshooting. It prepares them to tackle real-world security challenges in diverse enterprise environments, making them valuable assets to any organization concerned about its wireless security posture. To succeed in the CWSP-205 exam, candidates must possess a solid foundation in general networking concepts and a particular focus on the IEEE 802.11 standard. The certification builds upon the knowledge gained from the foundational CWNA (Certified Wireless Network Administrator) certification. Therefore, it is highly recommended that candidates either hold a valid CWNA certification or have equivalent knowledge and experience. This prerequisite ensures that individuals have the necessary groundwork to grasp the advanced security concepts presented in the CWSP curriculum. The journey to becoming a CWSP is challenging, but the rewards in terms of career advancement are significant.
Who Should Pursue the CWSP Certification?
The CWSP certification is ideal for a range of IT professionals whose roles involve the security of wireless networks. Network administrators and engineers who are responsible for the day-to-day management and security of their organization's WLAN will find this certification invaluable. It equips them with the skills needed to design, deploy, and maintain secure wireless infrastructures. By achieving this certification, they can transition from general network administration to a specialized role in wireless security, which is often accompanied by increased responsibility and better career prospects. The CWSP-205 exam is their gateway to this specialization. Security professionals, including security analysts, consultants, and architects, are also prime candidates for the CWSP certification. For these individuals, understanding the unique vulnerabilities of wireless networks is crucial. The CWSP-205 exam provides a vendor-neutral perspective on wireless security, which is essential for consultants and architects who work with a variety of technologies and products.
This certification allows them to offer expert advice and design security solutions that are both effective and compliant with industry best practices. It enhances their credibility and demonstrates a commitment to staying current with evolving security threats. IT managers and decision-makers can also benefit greatly from the knowledge covered in the CWSP-205 exam. While they may not be involved in the hands-on implementation, a deep understanding of wireless security principles enables them to make informed decisions about technology investments, security policies, and risk management strategies. This knowledge helps them to effectively communicate with their technical teams and to ensure that the organization's security posture is aligned with its business objectives. A manager with a CWSP background is better equipped to lead a team of security professionals and to champion security initiatives within the organization.
Core Domains of the CWSP-205 Exam
One of the fundamental domains covered in the CWSP-205 exam is WLAN Discovery and Monitoring. This area focuses on the techniques and tools used to identify and analyze wireless networks. Candidates are expected to understand how to use various discovery tools to detect both authorized and rogue access points. The curriculum covers passive and active scanning methods, as well as the analysis of 802.11 frames to gather information about a network's configuration and security settings. A thorough grasp of these techniques is essential for maintaining situational awareness and for identifying potential security threats. Another critical domain is Intrusion and Attack Analysis. This section of the CWSP-205 exam tests a candidate's ability to recognize and understand different types of wireless attacks. Topics include denial-of-service (DoS) attacks, man-in-the-middle (MITM) attacks, and various methods of cracking wireless encryption.
The exam requires candidates to not only identify these attacks but also to understand their underlying mechanisms and potential impact. This knowledge is crucial for developing effective defense strategies and for responding to security incidents in a timely and efficient manner. Security Policy and Compliance is also a key area of focus. The CWSP-205 exam emphasizes the importance of establishing and enforcing comprehensive security policies for wireless networks. This includes defining acceptable use policies, guest access policies, and procedures for incident response. Candidates must also be familiar with relevant industry standards and regulations, such as PCI DSS and HIPAA, and understand how to design and implement a wireless network that meets these compliance requirements.
This domain highlights the administrative and governance aspects of wireless security, which are just as important as the technical controls. Finally, the CWSP-205 exam extensively covers Authentication and Encryption Mechanisms. This domain delves into the details of various security protocols, including legacy standards like WEP and WPA, as well as the modern, robust standards of WPA2 and WPA3. Candidates need to understand the differences between these protocols, their respective vulnerabilities, and the best practices for their implementation. The exam also covers enterprise-level authentication using IEEE 802.1X and RADIUS, including the various EAP types and their specific use cases. Mastery of this domain is essential for implementing strong access control and for protecting the confidentiality of wireless communications.
The Importance of 802.11 Frame Analysis
A deep understanding of 802.11 frame analysis is a cornerstone of the CWSP-205 exam. The ability to capture and dissect wireless frames is a critical skill for any wireless security professional. It allows for a granular view of the network's operations, revealing details that are not visible through higher-level management interfaces. By examining management, control, and data frames, a security expert can identify misconfigurations, detect anomalies, and uncover covert activities that might indicate a security breach. This skill is indispensable for both proactive security assessments and reactive incident response. The CWSP-205 exam requires candidates to be proficient in using protocol analysis tools, such as Wireshark, to interpret 802.11 frames. This includes understanding the structure of different frame types, from beacon and probe response frames to authentication and association frames. Candidates must be able to identify key information within these frames, such as SSIDs, BSSIDs, channel information, and supported data rates.
This level of detail is crucial for diagnosing network problems, verifying security settings, and conducting forensic investigations following a security incident. Practical, hands-on experience with a protocol analyzer is therefore highly recommended. Frame analysis is particularly important for understanding and troubleshooting authentication and encryption processes. By capturing and analyzing the 802.1X/EAP exchange, a security professional can verify that the authentication process is working correctly and identify potential points of failure. Similarly, analyzing the 4-way handshake frames is essential for understanding how encryption keys are generated and distributed in WPA2/WPA3 networks. The CWSP-205 exam will test a candidate's ability to interpret these specific frame exchanges and to diagnose any issues that may arise during the establishment of a secure connection.
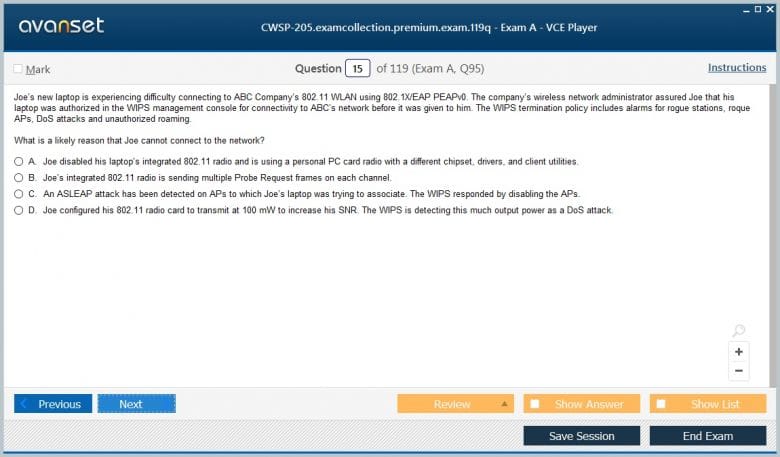
Wireless Intrusion Prevention Systems (WIPS)
The topic of Wireless Intrusion Prevention Systems, or WIPS, is a significant component of the CWSP-205 exam. A WIPS is a dedicated security solution designed to monitor the radio frequency spectrum for unauthorized or malicious activity and to take automated actions to mitigate threats. The exam covers the architecture and operation of WIPS, including the roles of sensors, servers, and management consoles. Candidates are expected to understand how a WIPS can be deployed to provide comprehensive security coverage for an enterprise wireless network, often as an overlay to the existing WLAN infrastructure. A key function of a WIPS that is tested on the CWSP-205 exam is its ability to detect and classify a wide range of wireless threats. This includes identifying rogue access points, which are unauthorized APs connected to the corporate network, and evil twins, which are malicious APs that impersonate legitimate ones to trick users into connecting.
The curriculum also covers the detection of other attacks, such as ad-hoc networks, client misassociations, and denial-of-service attacks. Understanding the signatures and behaviors associated with these threats is crucial for both the exam and real-world application. Beyond detection, the CWSP-205 exam emphasizes the prevention and mitigation capabilities of a WIPS. This involves understanding the different methods a WIPS can use to neutralize threats, such as sending de-authentication frames to disconnect clients from a rogue AP or using RF jamming techniques to disrupt a malicious device. Candidates must also be aware of the potential legal and operational implications of these countermeasures. A well-configured WIPS can be a powerful tool for automating wireless security, but it requires careful planning and management to be effective and to avoid disrupting legitimate network operations.
Preparing for the CWSP-205 Exam
Successful preparation for the CWSP-205 exam requires a multi-faceted approach. Simply reading the official study guide is often not enough. Candidates should supplement their reading with hands-on lab exercises that reinforce the theoretical concepts. Setting up a small lab environment with a few access points, a wireless LAN controller, and a RADIUS server can provide invaluable practical experience. This allows candidates to experiment with different security configurations, practice using protocol analysis tools, and simulate various types of wireless attacks in a controlled environment. This practical application of knowledge is key to passing the exam. Joining study groups and online forums can also be a highly effective preparation strategy. Collaborating with other candidates provides an opportunity to discuss challenging topics, share insights, and ask questions.
It can also help to maintain motivation and to stay on track with a study plan. Many online communities are dedicated to CWNP certifications, and these can be a great resource for finding study materials, practice questions, and expert advice. Engaging with a community of peers can make the challenging journey of preparing for the CWSP-205 exam a more interactive and supportive experience. Finally, taking practice exams is a crucial step in the final stages of preparation. Practice exams help to identify areas of weakness that require further study and to become familiar with the format and style of the actual exam questions. They also help to develop effective time management skills, which are essential for completing the exam within the allotted time. By simulating the exam experience, candidates can build confidence and reduce anxiety on the test day. A combination of thorough study, hands-on practice, and rigorous self-assessment is the formula for success on the CWSP-205 exam.
Advanced WLAN Discovery Techniques
The CWSP-205 exam requires a profound understanding of WLAN discovery, which extends beyond simply finding available networks. It involves the meticulous process of identifying and profiling every wireless device operating within an organization's airspace. This includes not only access points but also client devices, ad-hoc networks, and any other sources of radio frequency interference. Advanced discovery techniques employ specialized tools that go beyond the capabilities of standard operating system utilities. These tools can identify hidden SSIDs, map out the physical location of devices, and provide detailed information about a device's configuration and capabilities. Passive scanning is a key discovery technique covered in the CWSP-205 exam.
This method involves listening to the wireless medium for frames being transmitted by other devices, such as beacon frames from access points and probe requests from clients. Because it is a passive process, it is stealthy and does not generate any network traffic. This makes it ideal for covert reconnaissance and for monitoring a network without affecting its performance. A security professional must be able to interpret the information contained within these captured frames to build a comprehensive picture of the wireless environment. In contrast, active scanning involves sending out probe request frames to solicit responses from access points in the vicinity. While this method is faster and can discover networks that do not broadcast their SSID, it also creates network traffic and reveals the presence of the scanning device. The CWSP-205 exam tests a candidate's knowledge of both methods, including their respective advantages and disadvantages. A skilled professional knows when to use each technique and how to combine them to achieve a complete and accurate understanding of the wireless landscape. This skill is foundational for security auditing and threat hunting.
Analyzing 802.11 Protocol Vulnerabilities
A core component of the CWSP-205 exam is the analysis of vulnerabilities inherent in the IEEE 802.11 protocol itself. While the standard has evolved significantly over the years, certain fundamental aspects of its operation can be exploited by attackers. For example, the management frames used to control the wireless medium, such as authentication, de-authentication, and association frames, are typically sent unencrypted. This makes them susceptible to spoofing, which can be used to launch various denial-of-service attacks or to facilitate man-in-the-middle attacks. The exam delves into the specifics of these vulnerabilities. Candidates must understand how an attacker can forge a de-authentication frame to disconnect a legitimate user from the network, a simple yet highly effective DoS attack. Similarly, knowledge of how association floods or authentication floods can overwhelm an access point's resources is essential.
The CWSP-205 exam requires not just the identification of these attacks but also an understanding of the countermeasures, such as the implementation of 802.11w, also known as Management Frame Protection (MFP), which provides a mechanism for protecting management frames from being spoofed. Furthermore, the exam covers vulnerabilities related to the discovery process. For instance, the use of probe requests by client devices can reveal information about the networks they have previously connected to, which can be a privacy risk. An attacker can use this information to create a malicious access point with a matching SSID, tricking the client into connecting automatically. Understanding these nuances of the 802.11 protocol is crucial for designing a secure wireless network and for developing strategies to mitigate these inherent risks. A CWSP certified professional is expected to have a deep, technical grasp of these issues.
Intrusion Detection Methodologies
The CWSP-205 exam places a strong emphasis on intrusion detection methodologies as they apply to wireless networks. This involves more than just deploying a WIPS; it requires a deep understanding of how to detect malicious activity by analyzing network traffic and device behavior. Signature-based detection is one common method, which involves looking for specific patterns or "signatures" that are known to be associated with particular attacks. For example, a WIPS might have a signature for a de-authentication flood, which would be triggered if a large number of de-authentication frames are detected in a short period. Another important methodology covered is anomaly-based detection. This approach involves first establishing a baseline of normal network behavior and then monitoring for any deviations from that baseline.
For instance, if a client device suddenly starts communicating with a new, unknown access point, this could be flagged as a potential anomaly. Anomaly-based detection is often more effective at detecting new or unknown attacks that do not have a pre-defined signature. However, it can also be more prone to false positives if the baseline is not accurately defined. The CWSP-205 exam expects candidates to understand the trade-offs between these two approaches. A third methodology is stateful protocol analysis. This involves tracking the state of network connections and looking for any behavior that violates the expected protocol sequence. For example, in a WPA2 handshake, there is a specific sequence of four frames that must be exchanged. If a device sends a frame that is out of sequence, it could indicate a potential attack. This method requires a detailed understanding of the protocols being analyzed, which is why a strong foundation in 802.11 frame analysis is so critical for the CWSP-205 exam. A proficient security professional uses a combination of these methods for robust threat detection.
Wireless Denial-of-Service Attacks
Denial-of-Service (DoS) attacks are a major threat to wireless networks, and this topic is covered extensively in the CWSP-205 exam. These attacks aim to disrupt the availability of the network, preventing legitimate users from accessing it. Due to the shared nature of the wireless medium, WLANs are particularly vulnerable to DoS attacks. The exam covers both Layer 1 (physical layer) and Layer 2 (data link layer) attacks. Layer 1 attacks typically involve generating radio frequency interference or jamming, which can drown out the legitimate Wi-Fi signal and render the network unusable. Layer 2 DoS attacks are more sophisticated and exploit the workings of the 802.11 protocol. As mentioned earlier, spoofing de-authentication or disassociation frames is a common technique. Another method is to manipulate the Network Allocation Vector (NAV) timer.
By sending frames with a long duration value, an attacker can trick other devices into thinking the medium is busy, forcing them to defer their own transmissions. This can effectively halt all communication on a channel. The CWSP-205 exam requires candidates to understand the mechanics of these attacks and how to detect them using protocol analysis. Mitigating wireless DoS attacks is a complex challenge. For Layer 1 attacks, identifying the source of the interference is the first step, which can be done using spectrum analysis tools. For Layer 2 attacks, implementing Management Frame Protection (802.11w) is a key defense, as it provides integrity checking for management frames. A well-designed WIPS can also help to detect and locate the source of a DoS attack. The CWSP-205 exam will test a candidate's knowledge of these mitigation techniques and their ability to apply them in different scenarios to ensure network resiliency.
Man-in-the-Middle (MITM) Attacks
Man-in-the-Middle (MITM) attacks are a serious threat in the wireless world, and they are a key topic on the CWSP-205 exam. In a MITM attack, an adversary secretly positions themselves between two communicating parties, intercepting, and potentially altering, their communications. In a wireless context, this is often achieved by setting up a rogue or evil twin access point. The attacker tricks a user into connecting to their malicious AP, which then acts as a relay, forwarding traffic between the user and the legitimate network. The attacker is then able to eavesdrop on all the traffic. The CWSP-205 exam requires candidates to understand the various techniques used to execute MITM attacks. This includes the use of Karma attacks, where a malicious AP listens for probe requests from clients and then spoofs the requested SSID to lure them in. Another technique is the use of captive portals on an evil twin AP to harvest user credentials.
Candidates must also be familiar with tools like KARMA and Jasager that can be used to automate these types of attacks. This knowledge is essential for understanding the threat landscape and for developing effective countermeasures. Preventing MITM attacks requires a multi-layered security approach. The most effective defense is the use of strong, mutual authentication, such as that provided by 802.1X/EAP. This ensures that both the client and the network can verify each other's identity before establishing a connection, making it much more difficult for an attacker to insert themselves into the communication path. User education is also critical, as users need to be trained to be cautious about connecting to unknown or untrusted networks. A CWSP professional must be able to design and implement these layered defenses to protect against MITM threats.
Wireless Penetration Testing Methodologies
While the CWSP-205 exam is focused on defense, understanding offensive techniques is crucial for building a strong security posture. The exam therefore touches upon the methodologies used in wireless penetration testing. A penetration test is a simulated attack that is performed to evaluate the security of a network. The process typically begins with a reconnaissance phase, where the tester uses discovery techniques to gather as much information as possible about the target wireless network. This is followed by a vulnerability analysis phase, where the tester attempts to identify weaknesses in the network's security controls. The next phase is exploitation, where the tester attempts to gain unauthorized access to the network by exploiting the identified vulnerabilities. This could involve cracking weak encryption keys, exploiting a misconfigured RADIUS server, or tricking a user into revealing their credentials. The goal is to demonstrate the potential impact of a successful attack.
The CWSP-205 exam expects candidates to be familiar with the tools and techniques used in each of these phases, such as Aircrack-ng for WEP/WPA cracking and Kismet for network discovery. The final phase of a penetration test is reporting. The tester must document their findings, including the vulnerabilities that were discovered, the methods used to exploit them, and the potential business impact. The report should also include recommendations for remediation to help the organization improve its security posture. Understanding this entire process from a defender's perspective allows a CWSP professional to better anticipate the actions of an attacker and to proactively identify and fix security weaknesses before they can be exploited. This proactive mindset is a key attribute tested by the CWSP-205 exam.
The Evolution of Wireless Security Protocols
The CWSP-205 exam curriculum places a strong emphasis on understanding the history and evolution of wireless security protocols. This journey begins with Wired Equivalent Privacy (WEP), the original security standard for 802.11 networks. Candidates must understand the fundamental flaws in WEP, such as its use of a static, shared key and the weak RC4 stream cipher, which make it trivial to crack with modern tools. Although obsolete, knowledge of WEP is still relevant for identifying legacy systems and understanding the motivations behind the development of more secure protocols. The next major step in this evolution was Wi-Fi Protected Access (WPA). WPA was introduced as an interim solution to address the serious security holes in WEP. The CWSP-205 exam requires a detailed understanding of WPA's improvements, including the Temporal Key Integrity Protocol (TKIP), which introduced per-packet key mixing to prevent the key-reuse attacks that plagued WEP. However, WPA still relied on the RC4 cipher and was eventually found to have its own set of vulnerabilities.
A certified professional must be able to articulate why WPA is no longer considered secure for enterprise environments. The current industry standard, and a major focus of the CWSP-205 exam, is WPA2. It mandated the use of the Advanced Encryption Standard (AES) with Counter Mode CBC-MAC Protocol (CCMP), a much stronger encryption mechanism than TKIP. WPA2 has been the bedrock of wireless security for over a decade and provides a robust level of protection when implemented correctly. Candidates must master the details of WPA2-Personal (using a pre-shared key) and WPA2-Enterprise (using 802.1X/EAP authentication), including their respective use cases and configuration best practices. Most recently, WPA3 was introduced to further enhance wireless security. The CWSP-205 exam is updated to include this latest standard. WPA3 offers several key improvements over WPA2, including protection against offline dictionary attacks through the Simultaneous Authentication of Equals (SAE) handshake, also known as Dragonfly. It also offers stronger encryption for open networks through Wi-Fi Enhanced Open. Understanding the new features of WPA3 and the migration path from WPA2 is now a critical knowledge area for any aspiring CWSP.
Deep Dive into 802.1X and EAP
For enterprise-level security, the CWSP-205 exam requires an expert-level understanding of the IEEE 802.1X framework. This standard provides a mechanism for port-based network access control, ensuring that a device is authenticated before it is granted access to the network. The exam covers the three main components of the 802.1X architecture: the supplicant (the client device), the authenticator (the access point or switch), and the authentication server (typically a RADIUS server). Candidates must understand the roles and interactions of each of these components in the authentication process. The Extensible Authentication Protocol (EAP) is at the heart of the 802.1X framework, and it is a vast and complex topic on the CWSP-205 exam.
EAP is not a specific authentication mechanism itself but rather a framework that allows for various authentication methods, known as EAP types, to be used. The exam covers a wide range of EAP types, and candidates must know their differences, strengths, and weaknesses. This knowledge is crucial for selecting the appropriate EAP type for a given security requirement and environment. Common EAP types tested include EAP-TLS, which provides the strongest security through certificate-based mutual authentication, and PEAP (Protected EAP), which creates a TLS tunnel to protect the authentication of a weaker, inner EAP method like MS-CHAPv2. Other important types are EAP-TTLS (Tunneled TLS) and EAP-FAST (Flexible Authentication via Secure Tunneling). The CWSP-205 exam requires candidates to understand the message flow for these different EAP types and to be able to troubleshoot common issues that can arise during the authentication process, making this a critical area of study.
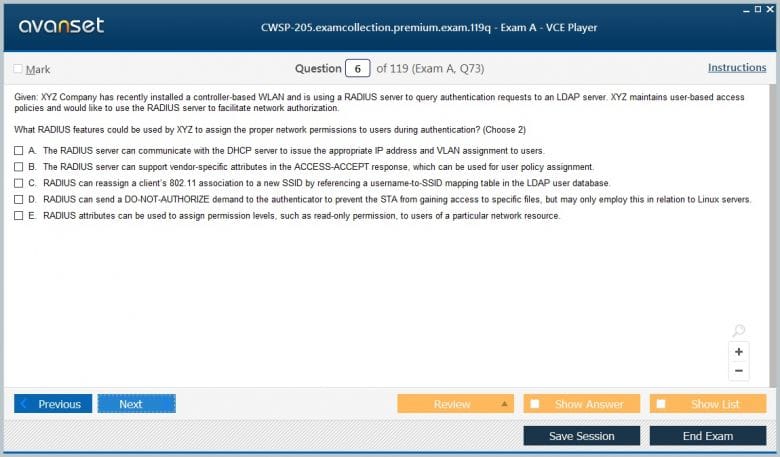
The Role of RADIUS in Wireless Security
The Remote Authentication Dial-In User Service (RADIUS) protocol is a fundamental building block of enterprise wireless security and a key topic in the CWSP-205 exam. While 802.1X and EAP define the framework for authentication, RADIUS is the protocol that is typically used to carry the authentication messages between the authenticator (the access point) and the authentication server. The authentication server, which is the RADIUS server, is responsible for validating the user's credentials against a database, such as Active Directory. The CWSP-205 exam delves into the operational details of the RADIUS protocol. This includes understanding the format of RADIUS packets and the different types of attributes that can be used to convey information between the access point and the server.
Candidates must know about key attributes such as User-Name, User-Password, and various vendor-specific attributes (VSAs) that are used to implement advanced features. The concept of a shared secret, which is used to secure communication between the access point and the RADIUS server, is also a critical point of study. Beyond simple authentication, RADIUS plays a vital role in authorization and accounting (AAA). Once a user is authenticated, the RADIUS server can send back authorization information to the access point, such as which VLAN the user should be assigned to or what quality of service (QoS) policies should be applied. The CWSP-205 exam covers these advanced capabilities, including the concept of dynamic VLAN assignment. Understanding how to leverage RADIUS for granular access control is a hallmark of a skilled wireless security professional and is therefore thoroughly tested.
Designing Robust Wireless Security Policies
Technical controls are only one part of a comprehensive security strategy; policies and procedures are equally important. The CWSP-205 exam recognizes this by dedicating a significant portion of its content to the topic of wireless security policies. A well-defined security policy provides the foundation for a secure network by clearly outlining the rules and requirements for wireless access. The exam requires candidates to understand the key elements that should be included in a wireless security policy, such as an acceptable use statement, data privacy guidelines, and incident response procedures. One critical aspect of policy design covered in the CWSP-205 exam is the definition of different security levels for different types of users and devices.
For example, a policy might specify that corporate-owned laptops must use 802.1X authentication to connect to a specific SSID, while guest users are directed to a separate guest network with a captive portal and limited network access. This practice of network segmentation is a fundamental security principle. The exam tests a candidate's ability to design a policy that effectively balances security requirements with the need for usability and business agility. The policy should also address the security of the WLAN infrastructure itself. This includes guidelines for the physical security of access points, strong password policies for management interfaces, and procedures for regularly updating firmware to patch security vulnerabilities. Furthermore, the CWSP-205 exam covers the importance of policies related to monitoring and logging. A comprehensive policy will define what events should be logged, how long logs should be retained, and who should be responsible for reviewing them. This ensures that the organization has the necessary visibility to detect and respond to security incidents.
Fast Secure Roaming Technologies
In many enterprise environments, such as hospitals or warehouses, users with mobile devices need to be able to move seamlessly between different access points without losing their connection. This process is known as roaming. The CWSP-205 exam covers the security implications of roaming and the technologies that have been developed to make it both fast and secure. When a client roams using standard 802.1X authentication, it must perform a full re-authentication with the RADIUS server every time it moves to a new AP, which can cause noticeable delays and disrupt real-time applications like voice calls. To address this issue, various fast secure roaming technologies have been developed. The CWSP-205 exam requires knowledge of these methods.
One common approach is key caching, where the client and the initial AP establish a master key, which can then be securely distributed to other APs on the same network. When the client roams to a new AP, it can use this cached key to perform an abbreviated handshake, bypassing the need for a full RADIUS authentication. This significantly speeds up the roaming process. The exam covers specific standards that facilitate fast secure roaming, such as the 802.11r amendment, also known as Fast BSS Transition (FT). FT defines a standardized method for clients to establish their security context with a new AP before they even roam to it, resulting in a nearly seamless transition. Candidates must understand the different FT modes, such as over-the-air and over-the-DS, and how they work. A thorough understanding of these technologies is essential for designing and securing wireless networks that support mobility-critical applications, a common requirement in modern enterprises.
Implementing a Wireless Security Monitoring Strategy
A critical aspect of maintaining a secure wireless network, and a key domain in the CWSP-205 exam, is the implementation of a continuous security monitoring strategy. It is not enough to simply deploy security controls; an organization must also have the visibility to ensure that those controls are working effectively and to detect any threats that may have bypassed them. This requires a combination of tools and processes designed to provide ongoing insight into the state of the wireless environment. The exam tests a candidate's ability to design and implement such a strategy. The foundation of a good monitoring strategy is the collection of relevant data from various sources. The CWSP-205 exam covers the importance of gathering logs from wireless LAN controllers, access points, and RADIUS servers.
These logs can provide a wealth of information about authentication attempts, device associations, and system events. Additionally, data from a Wireless Intrusion Prevention System (WIPS) is invaluable for detecting security-specific events, such as rogue APs or denial-of-service attacks. The ability to correlate data from these different sources is crucial for gaining a holistic view of wireless security. Once the data is collected, it must be analyzed. The CWSP-205 exam emphasizes the use of Security Information and Event Management (SIEM) systems to aggregate and analyze security data. A SIEM can be configured with correlation rules to automatically detect suspicious patterns of activity that might indicate a security incident. For example, a rule could be created to generate an alert if a large number of failed authentication attempts are detected from a single device. A CWSP professional should be able to define the requirements for a wireless security monitoring program and select the appropriate tools for its implementation.
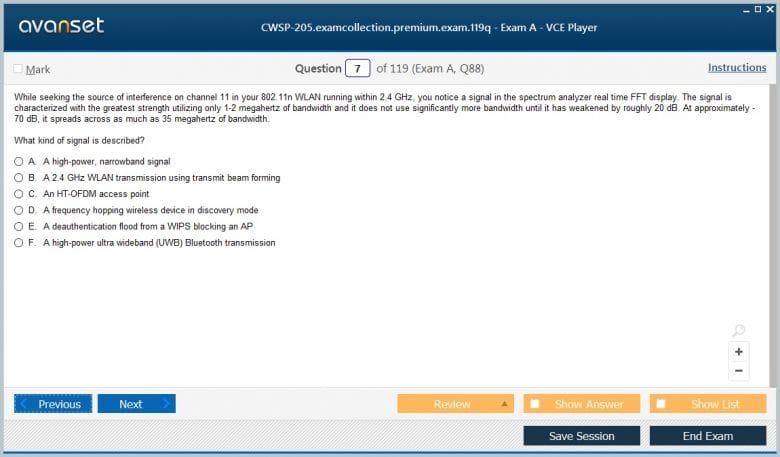
Spectrum Analysis for Security Professionals
While protocol analysis focuses on the data being transmitted over the air, spectrum analysis is concerned with the underlying radio frequency (RF) energy itself. This is a specialized but important topic within the CWSP-205 exam. A spectrum analyzer is a tool that can visualize the RF environment, showing the amplitude of signals at different frequencies. For a security professional, this is essential for detecting certain types of attacks and for troubleshooting network performance issues that may have a security implication. One of the primary security use cases for spectrum analysis is the detection of physical layer denial-of-service attacks. A jamming device, for example, will show up on a spectrum analyzer as a source of high-power, broadband noise that is disrupting the Wi-Fi channels.
By using a spectrum analyzer with a directional antenna, a security professional can often pinpoint the physical location of such a device. The CWSP-205 exam expects candidates to be able to interpret the output of a spectrum analyzer and to recognize the signatures of common RF jammers and other sources of interference. Spectrum analysis can also be used to identify covert or non-standard wireless devices that may not be detectable with a traditional protocol analyzer. Some advanced threats may use custom or proprietary wireless protocols that do not conform to the 802.11 standard. These devices would be invisible to a Wi-Fi scanner, but their RF transmissions would be clearly visible on a spectrum analyzer. This capability makes spectrum analysis a critical tool for comprehensive threat hunting in high-security environments. A CWSP must understand when and how to employ this advanced tool.
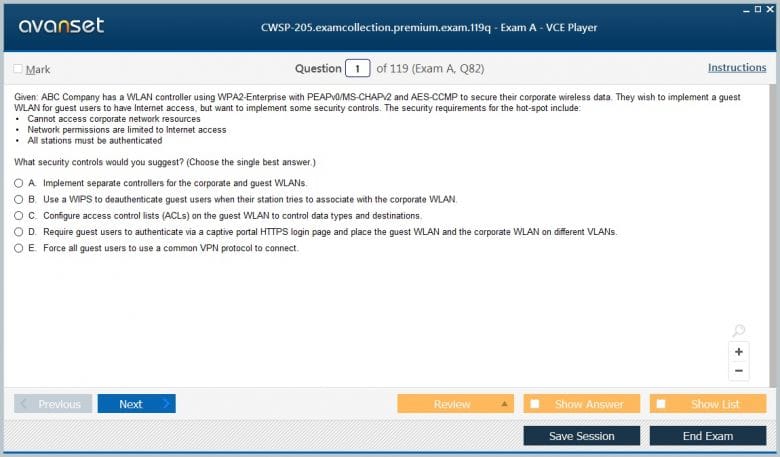
Wireless Guest Access and BYOD Security
Providing secure wireless access for guests and for employees' personal devices (Bring Your Own Device or BYOD) is a common requirement in modern enterprises and a significant topic on the CWSP-205 exam. These scenarios introduce unique security challenges, as the organization has little or no control over the security posture of the devices connecting to its network. Therefore, a robust security architecture is needed to provide network access while protecting corporate resources. The exam tests a candidate's ability to design and implement secure solutions for these use cases. For guest access, the most common solution is a captive portal. When a guest connects to the guest SSID, they are redirected to a web page where they must accept a terms of use policy or enter some basic information before being granted internet access.
The CWSP-205 exam covers the importance of ensuring that the guest network is completely isolated from the internal corporate network, typically through the use of VLANs and firewall rules. This network segmentation is crucial to prevent a compromised guest device from being used as a pivot point to attack internal systems. BYOD security is more complex. While a captive portal might be used for initial device registration, a more robust solution is often required. The CWSP-205 exam covers the use of device onboarding systems, which can automate the process of provisioning a personal device for secure network access. This might involve pushing a configuration profile to the device that sets up a secure WPA2-Enterprise connection and installs a client certificate for authentication. These systems can also perform posture assessments to ensure that the device meets certain security requirements, such as having up-to-date antivirus software, before it is allowed on the network.
VPNs and Secure Remote Access
While not strictly a wireless technology, Virtual Private Networks (VPNs) play a crucial role in securing wireless communications, and their application is a relevant topic for the CWSP-205 exam. A VPN creates an encrypted tunnel over an untrusted network, such as a public Wi-Fi hotspot, to a trusted network, such as the corporate LAN. This ensures the confidentiality and integrity of all data transmitted by the client, even if the underlying wireless network is insecure. A CWSP professional should understand how VPNs can be used as a compensatory control in high-risk environments. The exam may touch upon the different types of VPN technologies, such as IPsec and SSL/TLS-based VPNs. Candidates should have a high-level understanding of how these protocols work and the security services they provide.
For example, they should know that a VPN can provide end-to-end encryption from the client device all the way to the VPN concentrator on the corporate network, which is a stronger guarantee of confidentiality than that provided by WPA2/WPA3 alone, as the latter only encrypts the traffic over the air to the access point. The use of VPNs is particularly important for remote workers and employees who travel frequently. When these users connect to public Wi-Fi networks in airports, hotels, and coffee shops, they are exposed to a significant risk of eavesdropping and man-in-the-middle attacks. The CWSP-205 exam emphasizes the importance of a corporate policy that mandates the use of a VPN whenever an employee connects to an untrusted network. This simple measure can dramatically reduce the risk of a data breach resulting from the use of insecure wireless networks.
Managing Wireless Security Incidents
Despite the best efforts to implement strong security controls, security incidents can still occur. The CWSP-205 exam, therefore, covers the topic of incident response as it applies to wireless networks. This involves having a predefined plan for how to detect, analyze, contain, and recover from a security breach. A CWSP professional should be familiar with the standard incident response lifecycle and be able to apply it to wireless-specific incidents. This proactive planning is essential for minimizing the damage and disruption caused by an attack. The first step in responding to a wireless incident is detection. This relies on the security monitoring tools and processes that have been put in place. Once a potential incident has been detected, the next step is analysis.
This involves gathering as much information as possible about the incident to determine its scope and impact. For a wireless incident, this would likely involve analyzing logs from the WIPS, WLAN controller, and RADIUS server, as well as performing packet captures of the suspicious activity. The CWSP-205 exam tests the ability to use these tools for forensic analysis. Once the incident has been analyzed, the focus shifts to containment. For a wireless incident, this might involve blacklisting the MAC address of a malicious device, shutting down a rogue access point, or disabling a compromised user account. The goal is to stop the attack and prevent it from spreading. After the incident has been contained, the organization must move to the eradication and recovery phase, which involves removing the threat and restoring normal operations. Finally, a post-incident review should be conducted to identify lessons learned and to improve the security posture to prevent similar incidents in the future.
Go to testing centre with ease on our mind when you use CWNP CWSP-205 vce exam dumps, practice test questions and answers. CWNP CWSP-205 Certified Wireless Security Professional (CWSP) certification practice test questions and answers, study guide, exam dumps and video training course in vce format to help you study with ease. Prepare with confidence and study using CWNP CWSP-205 exam dumps & practice test questions and answers vce from ExamCollection.
CWNP CWSP-205 Video Course

Site Search: