Pass Your Isaca CISA Certification Easy!
Isaca CISA Certification Exams Questions & Answers, Accurate & Verified By IT Experts
Instant Download, Free Fast Updates, 99.6% Pass Rate.

$69.99
Download Free CISA Practice Test Questions VCE Files
| Exam | Title | Files |
|---|---|---|
Exam CISA |
Title Certified Information Systems Auditor |
Files 29 |
Isaca CISA Certification Exam Dumps & Practice Test Questions
Prepare with top-notch Isaca CISA certification practice test questions and answers, vce exam dumps, study guide, video training course from ExamCollection. All Isaca CISA certification exam dumps & practice test questions and answers are uploaded by users who have passed the exam themselves and formatted them into vce file format.
ISACA CISA Certification: Your Complete Guide to Auditing, Security, and Career Advancement
In today’s rapidly evolving technological landscape, organizations are increasingly reliant on robust information systems. With this reliance comes the critical need for auditing, monitoring, and securing these systems. The CISA certification, offered by ISACA, is widely recognized as a benchmark of excellence for professionals in information systems auditing, control, and security. Earning a CISA credential demonstrates a high level of expertise, credibility, and commitment to maintaining the integrity of an organization’s information infrastructure.
Information systems auditors play a pivotal role in ensuring that IT processes, controls, and policies align with business objectives while mitigating risks. Professionals with CISA certification are equipped not only to identify vulnerabilities but also to offer strategic recommendations that enhance organizational performance and security.
Who Should Pursue the CISA Certification
The CISA credential is tailored for professionals who want to solidify their expertise in IT auditing and security management. This includes IT auditors, security professionals, risk management specialists, and consultants responsible for evaluating and improving information systems.
Professionals in governance and compliance roles also benefit greatly, as the certification emphasizes understanding of control frameworks and regulatory standards. Individuals who aspire to take on leadership roles in IT risk and assurance functions often find the CISA certification invaluable, as it highlights both technical competence and strategic insight.
Even experienced IT professionals without a formal auditing background can benefit. The certification equips them with auditing principles and practices, allowing them to assess systems effectively and understand organizational risk from a governance perspective.
Core Domains of the CISA Certification
The CISA exam focuses on five essential domains, each reflecting a critical aspect of an information systems auditor’s responsibilities. Understanding these domains provides a clear roadmap for preparation and highlights the professional skills needed to succeed in the field.
Information Systems Auditing Process
Auditing is at the heart of the CISA certification. This domain covers the entire auditing process, including planning, execution, and reporting. Professionals are trained to evaluate the effectiveness of information systems and ensure they meet organizational standards.
Key responsibilities include assessing internal controls, identifying risks, and making recommendations for improvement. This domain emphasizes a structured approach to audits, encouraging consistency, thoroughness, and alignment with best practices. It equips auditors with the skills to examine systems critically while maintaining objectivity and compliance with professional standards.
Governance and Management of IT
Effective IT governance ensures that technology strategies align with business objectives, optimize resources, and manage risks. This domain emphasizes the importance of oversight, strategic planning, and policy development in IT management.
Professionals certified in CISA learn to evaluate IT governance structures, assess organizational objectives, and ensure that technology initiatives contribute positively to business performance. This domain highlights the intersection of technical expertise and business acumen, demonstrating how IT decisions impact overall organizational success.
Information Systems Acquisition, Development, and Implementation
Organizations rely on new systems to improve efficiency and support growth. This domain focuses on evaluating the acquisition, development, and implementation of information systems.
CISA professionals are trained to assess project management practices, review system designs, and ensure that controls are integrated throughout the system lifecycle. This includes verifying that systems meet business needs, comply with security standards, and are implemented effectively. The knowledge gained in this domain enables auditors to identify potential issues before they become critical risks, ensuring that projects deliver value and maintain integrity.
Information Systems Operations and Business Resilience
Operational effectiveness and resilience are key priorities for any organization. This domain covers the processes that maintain information systems, including monitoring, incident management, and disaster recovery planning.
Professionals learn to assess operational controls, evaluate system performance, and ensure business continuity. By focusing on operational reliability, auditors can identify weaknesses that could disrupt services or compromise data. This domain also emphasizes the importance of resilience planning, helping organizations prepare for and respond to unexpected events such as system failures, cyberattacks, or natural disasters.
Protection of Information Assets
Safeguarding information is a core responsibility of IT professionals. This domain emphasizes the identification and management of risks related to data and information systems.
CISA-certified professionals develop expertise in implementing security controls, conducting risk assessments, and establishing policies to protect organizational assets. This includes ensuring compliance with regulations, monitoring threats, and recommending strategies to mitigate vulnerabilities. This domain highlights the evolving nature of cybersecurity and the importance of staying current with threats and best practices.
Benefits of the CISA Certification
Earning a CISA certification offers numerous professional advantages, positioning individuals for growth and recognition in the field of information systems auditing.
Global Recognition and Credibility
The CISA certification is internationally recognized, making it a valuable credential for professionals seeking global opportunities. Organizations worldwide trust CISA-certified auditors to assess, monitor, and protect their information systems effectively. This recognition enhances professional credibility, signaling a commitment to high standards of practice and ethical conduct.
Career Advancement Opportunities
CISA-certified professionals often enjoy accelerated career growth. The credential opens doors to senior-level positions in IT auditing, consulting, risk management, and information security. Professionals with CISA certification are frequently considered for leadership roles, where they can influence strategy, governance, and compliance within their organizations.
Increased Earning Potential
Certification often correlates with higher salaries. Employers value the specialized knowledge and practical skills that CISA-certified professionals bring to the table, which can translate into significant financial benefits. Professionals with CISA certification typically earn more than their non-certified peers, reflecting their expertise and the strategic value they provide.
Comprehensive Skill Development
CISA certification equips professionals with a broad skill set that encompasses technical auditing, risk assessment, governance, and cybersecurity. This multidisciplinary knowledge allows auditors to evaluate complex systems, identify vulnerabilities, and recommend improvements effectively.
Professional Networking and Resources
ISACA provides a robust professional community for CISA-certified individuals. Membership offers access to conferences, training, publications, and networking opportunities. Engaging with this community allows professionals to stay updated on industry trends, share best practices, and learn from peers and experts worldwide.
Eligibility and Experience Requirements
Obtaining a CISA certification requires a combination of education and professional experience. Candidates must have at least five years of work experience in information systems auditing, control, or security. Certain educational achievements or relevant certifications can substitute for a portion of this experience, providing flexibility for professionals from diverse backgrounds.
For example, a four-year degree in a related field may reduce the required experience by one year. Additionally, certain other certifications or prior work experience in IT or auditing roles can partially fulfill the requirements. This approach ensures that the certification remains accessible while maintaining its high standards.
Exam Structure and Preparation
The CISA exam is a rigorous assessment designed to test knowledge across all five domains. It consists of multiple-choice questions that evaluate both technical understanding and the ability to apply auditing principles in real-world scenarios.
Effective Study Strategies
Preparing for the CISA exam requires a structured approach. Candidates should start by reviewing the official study materials and reference manuals provided by ISACA. These resources offer detailed coverage of all domains and practical examples that help reinforce key concepts.
Joining study groups or attending formal training programs can enhance preparation by providing structured guidance and opportunities for discussion. Practice exams and sample questions are also essential, helping candidates become familiar with the format and improve time management skills during the test.
Real-world application is critical. Professionals are encouraged to connect theoretical knowledge with their practical experience, understanding how auditing principles, risk management practices, and security controls are implemented in organizational settings.
Maintaining Certification
CISA certification is a mark of ongoing professional competence. To maintain the credential, certified professionals must complete continuing professional education (CPE) hours annually. This requirement ensures that auditors remain current with technological developments, evolving security threats, and changing regulatory environments.
CPE activities may include attending conferences, participating in training programs, publishing articles, or contributing to industry initiatives. By fulfilling these requirements, professionals demonstrate their commitment to lifelong learning and continuous improvement in their field.
The CISA certification represents a significant milestone for professionals seeking to advance in the field of information systems auditing and security. It validates technical expertise, strategic insight, and a dedication to maintaining the highest professional standards.
Professionals who pursue CISA certification benefit from enhanced career opportunities, global recognition, increased earning potential, and a comprehensive skill set that spans auditing, risk management, governance, and cybersecurity. By understanding the core domains, fulfilling eligibility requirements, preparing diligently for the exam, and engaging in ongoing professional development, individuals can position themselves for long-term success and growth.
In an era where information systems underpin nearly every business function, the role of a CISA-certified professional is more critical than ever. Organizations rely on these experts to ensure operational integrity, mitigate risks, and protect valuable information assets. For ambitious IT and auditing professionals, earning the CISA credential is not just a goal—it is a pathway to expertise, influence, and meaningful career advancement.
Preparing for the CISA Exam
Successfully earning the CISA certification begins with a clear understanding of the exam structure, content, and preparation strategies. The CISA exam is designed to assess both technical expertise and the practical application of auditing principles. It evaluates knowledge across the five core domains: auditing process, governance, system acquisition, operations, and information security.
Candidates should approach preparation strategically, combining study materials, practice exams, and real-world experience. A structured plan helps ensure comprehensive coverage of all domains while building confidence for test day.
Understanding the Exam Structure
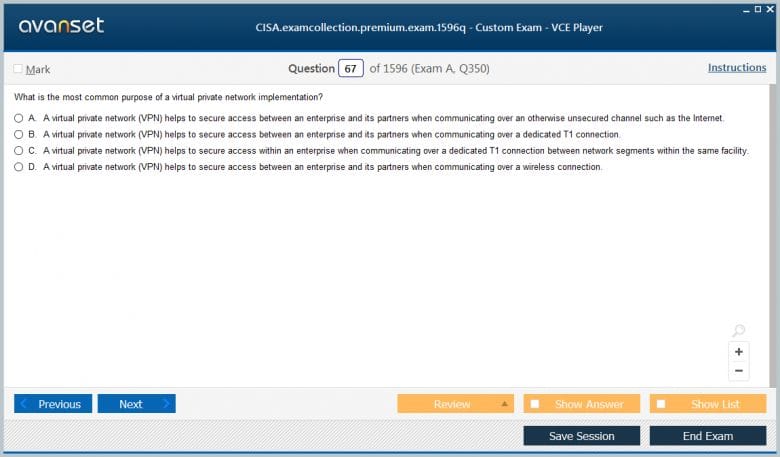
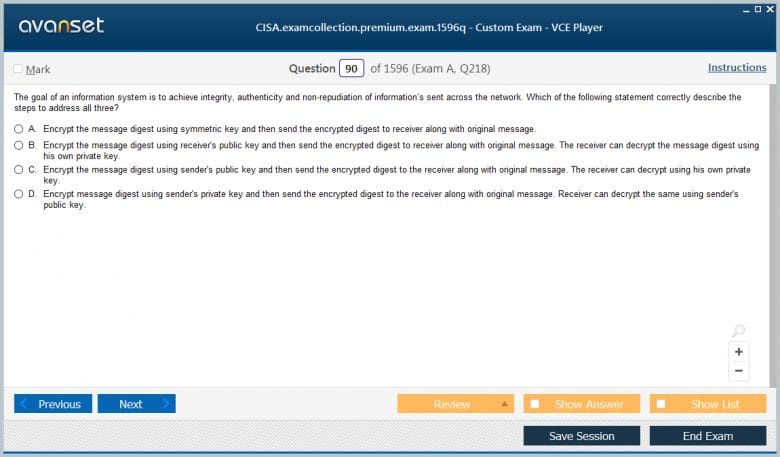
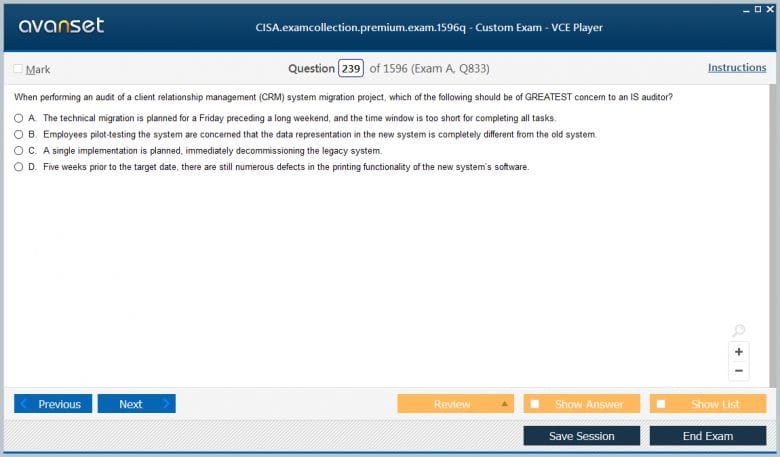
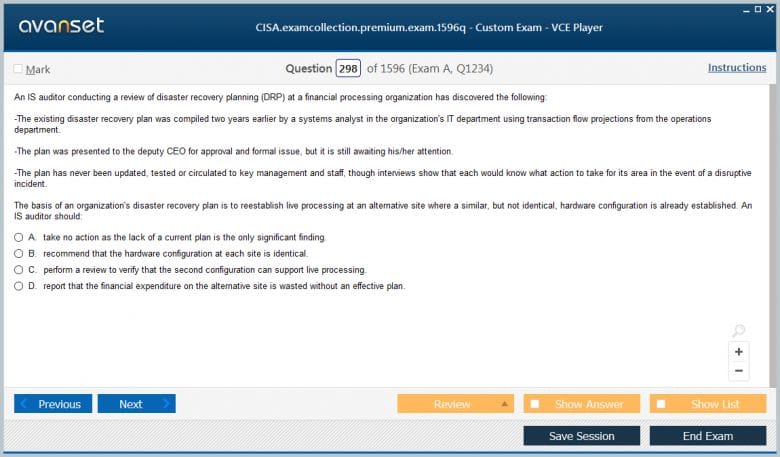
The CISA exam is a four-hour test consisting of 150 multiple-choice questions. Questions are designed to assess knowledge, comprehension, and application skills in realistic business scenarios. The distribution of questions across the five domains is generally as follows:
Information Systems Auditing Process: approximately 21%
Governance and Management of IT: approximately 17%
Information Systems Acquisition, Development, and Implementation: approximately 12%
Information Systems Operations, Maintenance, and Business Resilience: approximately 23%
Protection of Information Assets: approximately 27%
This distribution emphasizes the importance of security and operational resilience, reflecting the critical responsibilities of a CISA-certified professional.
Effective Study Materials
A combination of official ISACA resources and supplementary study materials is recommended for exam preparation.
ISACA Review Manuals
The official CISA review manual provides in-depth coverage of each domain, including frameworks, standards, and practical examples. It is essential for understanding the scope of the exam and serves as a primary reference.
Practice Questions and Mock Exams
Practice questions help candidates familiarize themselves with the exam format and identify areas requiring additional study. Mock exams simulate real testing conditions, improving time management and boosting confidence.
Online Courses and Training Programs
Structured online courses, workshops, and boot camps provide guided instruction, tips, and interaction with instructors or peers. These programs often include interactive exercises, case studies, and scenario-based questions that mimic real-world audit challenges.
Study Groups and Peer Collaboration
Joining study groups or discussion forums can enhance learning by offering alternative perspectives, sharing strategies, and addressing complex concepts collaboratively. Peer engagement reinforces understanding and provides motivation throughout the preparation period.
Building a Study Plan
A well-structured study plan is crucial for success. Candidates should allocate time based on the weight of each domain and their personal strengths and weaknesses. Key elements of an effective plan include:
Assessment of knowledge gaps: Identify areas requiring more attention based on prior experience and initial practice tests.
Domain-focused study sessions: Dedicate focused time to each domain, reviewing key concepts, controls, and real-world applications.
Regular practice tests: Schedule practice exams periodically to evaluate progress and adjust study strategies accordingly.
Revision and reinforcement: Allocate time for review sessions to consolidate learning, clarify doubts, and memorize key standards and processes.
Consistency is more important than intensity. Short, daily study sessions tend to be more effective than occasional long sessions, as they reinforce retention and reduce stress.
Understanding Core Exam Concepts
The CISA exam emphasizes not just technical knowledge but also the application of auditing and security principles in practical situations. Candidates should focus on key concepts within each domain:
Information Systems Auditing Process
Auditors must understand the full audit lifecycle, including planning, execution, reporting, and follow-up. Familiarity with professional standards, frameworks, and risk-based approaches is essential. Candidates should be able to evaluate controls, identify vulnerabilities, and make practical recommendations for improvement.
Governance and Management of IT
Candidates must understand the alignment between IT strategy and business objectives. This includes assessing IT governance frameworks, risk management processes, resource allocation, and performance measurement. Knowledge of organizational policies, compliance requirements, and ethical standards is also crucial.
Information Systems Acquisition, Development, and Implementation
This domain focuses on evaluating IT projects from planning through implementation. Candidates should be able to assess system development methodologies, project management practices, and control integration. Emphasis is placed on ensuring that systems meet business requirements, are secure, and comply with regulatory standards.
Information Systems Operations and Business Resilience
Understanding operational processes, maintenance practices, and disaster recovery planning is critical. Candidates should be able to evaluate system reliability, performance metrics, and business continuity strategies. Knowledge of incident management and response protocols is also essential for ensuring organizational resilience.
Protection of Information Assets
Securing information systems requires knowledge of risk management, security controls, and compliance requirements. Candidates must understand access controls, encryption, network security measures, and vulnerability management. Emphasis is placed on identifying threats, implementing controls, and monitoring effectiveness over time.
Practical Tips for Exam Success
While knowledge is critical, exam success also depends on strategy, preparation habits, and mental readiness.
Time Management
Effective time management during the exam is crucial. Candidates should aim to allocate roughly 1.5 minutes per question, leaving time at the end for review. Avoid spending excessive time on challenging questions; mark them for review and return later.
Scenario-Based Thinking
Many questions present real-world scenarios rather than straightforward facts. Candidates should practice analyzing scenarios, identifying risks, and determining the most appropriate course of action based on auditing principles and best practices.
Focus on High-Impact Areas
Prioritize areas weighted more heavily in the exam, particularly protection of information assets and operational resilience. Understanding these areas thoroughly increases the likelihood of answering a significant portion of questions correctly.
Stress Management and Mindset
Exam preparation can be stressful, but maintaining a positive mindset is critical. Regular breaks, consistent study habits, and relaxation techniques help manage stress and improve focus. Confidence grows as preparation progresses and knowledge deepens.
Utilize Real-World Experience
Professional experience is one of the most valuable tools for exam preparation. Applying auditing concepts to past projects, analyzing real incidents, and considering the practical implications of controls and governance strengthen understanding and make exam questions easier to navigate.
Common Mistakes to Avoid
Many candidates make avoidable mistakes that can impact performance. Awareness of these pitfalls helps improve results:
Neglecting weaker domains in favor of stronger areas.
Relying solely on memorization without understanding concepts.
Failing to practice scenario-based questions.
Ignoring time management during practice tests.
Underestimating the importance of continuing education and staying updated on standards.
Avoiding these mistakes ensures a more balanced and effective preparation strategy.
Leveraging Technology and Tools
Several tools can enhance preparation:
Flashcards: Useful for memorizing key terms, standards, and controls.
Online quizzes: Offer immediate feedback and help reinforce learning.
Simulation software: Mimics real audit scenarios for practical experience.
Study apps and trackers: Help monitor progress and maintain a consistent study schedule.
Integrating technology into the study process improves efficiency and retention while making preparation more engaging.
Post-Exam Considerations
Passing the CISA exam is a significant achievement, but candidates should also plan for professional application.
Certification Maintenance: CISA requires ongoing continuing professional education to stay current with evolving IT standards and practices.
Career Planning: Identify roles where CISA certification adds value, such as IT auditor, risk consultant, or information security manager.
Networking: Engage with the ISACA community to stay updated on trends, best practices, and professional opportunities.
Preparing thoroughly ensures not just exam success but long-term professional growth and the ability to apply CISA principles effectively in real-world settings.
Preparing for the CISA exam is a journey that combines knowledge, strategy, and practical experience. By understanding the exam structure, leveraging study materials, developing a structured study plan, and focusing on real-world application, candidates can increase their chances of success.
Effective preparation also involves avoiding common pitfalls, managing time and stress, and staying engaged with professional communities. Beyond passing the exam, preparation equips professionals with the skills, confidence, and perspective to excel in IT auditing, governance, and security roles.
The CISA certification opens doors to a rewarding career, but achieving it requires dedication, discipline, and a clear understanding of what the exam demands. Those who commit to thorough preparation gain not only a credential but also the knowledge and practical expertise necessary to make meaningful contributions to their organizations and advance in the dynamic field of information systems auditing.
Career Opportunities with CISA Certification
The CISA certification is highly respected in the IT and auditing fields, opening doors to a variety of career paths. Organizations worldwide seek professionals who can evaluate, monitor, and secure information systems. As businesses increasingly rely on digital infrastructure, the demand for skilled auditors and security experts continues to grow.
Professionals with CISA certification are well-positioned for roles in auditing, governance, risk management, and information security. Their expertise ensures that organizations comply with regulatory requirements, mitigate risks, and optimize IT performance.
Key Roles for CISA-Certified Professionals
IT Auditor
IT auditors are responsible for evaluating the integrity, confidentiality, and availability of information systems. They conduct audits to identify weaknesses, assess controls, and recommend improvements.
Core responsibilities include:
Reviewing system logs and controls
Evaluating internal policies and procedures
Assessing compliance with industry standards and regulations
Reporting findings to management and stakeholders
This role requires a combination of technical knowledge, analytical skills, and strong communication to convey complex findings to non-technical audiences.
Information Security Analyst
CISA-certified professionals can also work as information security analysts, focusing on protecting organizational assets from cyber threats. Their responsibilities include:
Conducting risk assessments and vulnerability analyses
Implementing security measures and monitoring systems
Investigating security breaches and recommending mitigation strategies
Ensuring compliance with security policies and regulations
Information security analysts play a crucial role in preventing data breaches, maintaining business continuity, and ensuring the overall security posture of an organization.
Risk Management Specialist
Risk management specialists identify, analyze, and mitigate risks related to information systems and IT operations. CISA certification equips professionals with the knowledge to:
Develop and implement risk management frameworks
Evaluate potential threats to systems and data
Recommend controls to minimize operational and strategic risks
Monitor risk mitigation efforts for effectiveness
Organizations rely on these specialists to make informed decisions about technology investments, policy development, and strategic planning.
IT Governance and Compliance Professional
IT governance and compliance roles focus on aligning IT strategy with business objectives and ensuring adherence to regulatory standards. Professionals in these positions:
Evaluate IT policies, procedures, and organizational structures
Ensure compliance with legal and industry requirements
Implement frameworks that support efficient IT management
Advise senior management on governance and control matters
These positions often involve working closely with executives, highlighting the need for both technical proficiency and business acumen.
Consulting and Advisory Roles
CISA certification also prepares professionals for consulting or advisory roles. In these positions, individuals provide expertise to organizations on audits, risk management, and information security strategies. Key responsibilities include:
Performing independent IT audits and assessments
Advising on security and control improvements
Developing customized policies and frameworks for clients
Delivering recommendations to enhance operational efficiency and compliance
Consulting roles can offer variety, exposure to multiple industries, and the opportunity to shape strategic IT initiatives.
Industries That Value CISA Certification
CISA-certified professionals are in demand across multiple sectors. Industries that particularly value the certification include:
Financial Services: Banks, insurance companies, and investment firms rely on auditors and security professionals to safeguard sensitive data and comply with strict regulations.
Healthcare: Hospitals, clinics, and healthcare providers need auditors to ensure patient data security and regulatory compliance, particularly with standards like HIPAA.
Government and Public Sector: Agencies require professionals to evaluate IT systems, manage risks, and enforce transparency and compliance.
Consulting Firms: Advisory firms hire CISA-certified experts to provide auditing and security services to clients across industries.
Technology and IT Services: Software companies, data centers, and cloud providers value CISA professionals for assessing systems, managing security, and implementing controls.
The certification’s versatility allows professionals to transition between industries, applying their expertise wherever information systems play a critical role.
Salary Insights for CISA-Certified Professionals
CISA certification often results in higher earning potential compared to non-certified peers. Salaries vary depending on factors such as experience, role, industry, and geographic location.
Entry-Level Professionals
Entry-level positions, such as junior IT auditors or security analysts, typically earn competitive salaries, reflecting both the demand for skilled professionals and the specialized knowledge required for CISA roles. Early-career CISA-certified professionals can expect to earn significantly more than peers without certification, often ranging from $60,000 to $85,000 annually, depending on region and organization size.
Mid-Level Professionals
With several years of experience, CISA-certified professionals may advance to mid-level roles such as senior IT auditor, risk manager, or information security analyst. Salaries for these positions generally range from $90,000 to $120,000 per year. The combination of certification and hands-on experience positions individuals to take on more complex projects, manage teams, and influence strategic decisions.
Senior-Level Professionals
Senior-level positions include IT audit managers, security managers, and governance leaders. These roles command salaries typically ranging from $120,000 to $160,000 or higher, reflecting both expertise and responsibility. Professionals in these positions oversee audit programs, manage compliance initiatives, and provide guidance to executive leadership.
Executive and Specialized Roles
For individuals who progress into executive-level or specialized advisory roles, compensation can exceed $180,000 annually. These roles may include Chief Information Security Officer (CISO), IT risk director, or senior consultant for global organizations. Beyond salary, such positions often include performance bonuses, stock options, and other incentives, reflecting the strategic value of their expertise.
Geographic Considerations
Salaries are influenced by location, with metropolitan areas and regions with a high concentration of financial or technology companies offering higher compensation. Professionals in major cities or tech hubs often receive additional benefits and incentives to attract top talent.
Career Growth and Advancement
CISA certification not only enhances current career prospects but also facilitates long-term professional growth. Professionals can pursue specialization in areas such as cybersecurity, risk management, or IT governance, positioning themselves for leadership roles.
Networking, ongoing education, and engagement with the ISACA community also support career advancement. By staying updated on industry trends, best practices, and emerging technologies, CISA-certified professionals maintain relevance and continue to grow their expertise.
Mentorship and leadership opportunities further enhance career growth. Experienced CISA-certified professionals can guide junior colleagues, lead audit teams, and shape organizational policies, solidifying their influence and professional reputation.
Professional Credibility and Recognition
CISA certification provides a significant boost to professional credibility. Employers recognize certified professionals as highly skilled, knowledgeable, and committed to ethical standards. The credential signals proficiency in auditing, risk management, and information security, increasing trust among stakeholders and clients.
Recognition extends beyond immediate employers. Industry peers, regulatory bodies, and clients value the certification, making CISA holders more competitive for consulting engagements, advisory roles, and leadership opportunities.
Leveraging CISA Certification for Career Transition
CISA certification is particularly useful for professionals seeking to transition from general IT roles to auditing, governance, or security positions. The certification demonstrates a formal understanding of auditing principles, risk assessment, and information security, making it easier to move into specialized roles.
Transitioning into IT auditing or governance roles can be challenging without formal credentials. CISA bridges this gap, providing both knowledge and industry recognition that employers require. Professionals can combine certification with hands-on experience to accelerate their career transition and gain credibility quickly.
CISA certification significantly enhances career opportunities and earning potential in the IT and auditing fields. It opens doors to diverse roles, including IT auditor, information security analyst, risk management specialist, governance professional, and consultant.
The certification is valued across industries, including financial services, healthcare, government, technology, and consulting. CISA-certified professionals command competitive salaries at all levels, from entry-level positions to executive roles, reflecting their specialized skills and strategic value.
Beyond compensation, the certification facilitates long-term professional growth, providing opportunities for specialization, leadership, and global recognition. Networking, ongoing education, and real-world experience ensure that certified professionals remain relevant and influential in the rapidly evolving landscape of IT governance, auditing, and security.
For professionals seeking to advance their careers, increase their impact, and secure a respected global credential, CISA offers a pathway to meaningful achievement and long-term success.
Maintaining Your CISA Certification
Earning the CISA certification is a major achievement, but maintaining it is equally important. The credential demonstrates expertise in auditing, risk management, and information security, but to remain relevant, certified professionals must actively engage in continuing professional education (CPE) and adhere to ISACA’s code of professional ethics.
Maintaining the certification ensures that professionals stay current with evolving technologies, regulatory changes, and industry best practices. It also reinforces credibility with employers, peers, and clients, emphasizing a commitment to ongoing learning and professional excellence.
Continuing Professional Education (CPE) Requirements
ISACA requires CISA-certified professionals to complete 20 CPE hours annually and a total of 120 CPE hours over three years. These hours must be relevant to information systems auditing, control, security, or governance.
Types of CPE Activities
CPE activities are diverse and allow flexibility in how professionals maintain their certification:
Formal Education: Attending university courses, professional development classes, or certification training programs related to IT auditing, governance, or security.
Workshops and Seminars: Participating in conferences, workshops, or seminars that cover emerging trends, new technologies, or best practices in auditing and information security.
Online Courses and Webinars: Enrolling in online training programs, webinars, and virtual workshops that provide CPE credits.
Professional Reading and Research: Engaging in research, reading industry publications, or writing articles related to auditing, governance, or information security.
Volunteer Work and Mentorship: Serving as a mentor, participating in ISACA chapter activities, or contributing to community projects within the IT audit and security field.
CPE activities not only fulfill certification requirements but also enhance professional knowledge and skills, keeping auditors equipped to handle evolving challenges.
Reporting and Documentation
CISA-certified professionals are responsible for tracking and reporting their CPE hours to ISACA. Accurate documentation of all activities, including dates, duration, and relevance, is essential. Maintaining detailed records helps avoid compliance issues and demonstrates commitment to professional development.
Adhering to ISACA’s Code of Professional Ethics
CISA-certified professionals must comply with ISACA’s Code of Professional Ethics, which emphasizes integrity, objectivity, confidentiality, and professional competence. Adhering to these ethical standards ensures trust and credibility in the workplace and with clients.
Key principles include:
Integrity: Acting with honesty and transparency in all professional activities.
Objectivity: Making impartial decisions based on evidence and professional judgment.
Confidentiality: Protecting sensitive information obtained during audits or assessments.
Professional Competence: Continuously developing skills and maintaining knowledge to perform responsibilities effectively.
Ethical conduct is a cornerstone of professional auditing and governance, and compliance with these principles reinforces the value of the CISA certification.
Advancing Your Professional Development
Beyond maintaining certification, CISA professionals are encouraged to engage in ongoing professional development. Continuous growth ensures adaptability to emerging technologies, regulatory changes, and evolving business needs.
Specialization and Advanced Skills
CISA-certified professionals can pursue specialization in areas such as cybersecurity, IT risk management, cloud computing, or advanced auditing techniques. Specialization enhances career opportunities and allows professionals to address specific organizational challenges more effectively.
Leadership and Management Skills
Developing leadership skills is essential for those aspiring to managerial or executive roles. CISA professionals may lead audit teams, oversee security initiatives, or participate in strategic planning. Effective communication, team management, and decision-making skills complement technical expertise and increase career advancement potential.
Networking and Industry Engagement
Active engagement with the professional community provides access to industry insights, peer learning, and new opportunities. Participating in ISACA chapters, attending conferences, and connecting with other certified professionals helps build a robust network and facilitates knowledge sharing.
Staying Current with Emerging Trends
Information systems and cybersecurity are dynamic fields. Professionals must stay informed about new threats, technological innovations, and regulatory updates. This includes understanding cloud technologies, artificial intelligence, data privacy regulations, and emerging auditing standards. Remaining proactive ensures that CISA-certified professionals maintain relevance and effectiveness in their roles.
Leveraging CISA Certification for Career Growth
Maintaining CISA certification and actively pursuing professional development opens doors to advanced career opportunities. Professionals can leverage the credential to pursue roles such as:
IT Audit Manager: Overseeing audit teams, developing audit strategies, and ensuring organizational compliance.
Information Security Manager: Managing security operations, assessing risks, and implementing security policies.
Risk Management Director: Designing and leading enterprise risk management initiatives to safeguard information systems.
Governance Specialist: Aligning IT strategy with business objectives and implementing effective governance frameworks.
Consultant or Advisor: Providing expert guidance on audits, compliance, and security strategies for diverse organizations.
Each of these roles benefits from the credibility, expertise, and ethical standards that CISA certification represents. Professionals who maintain their certification and develop complementary skills position themselves for leadership opportunities, higher compensation, and global recognition.
Practical Strategies for Continuous Growth
To maximize the benefits of CISA certification, professionals should adopt practical strategies for continuous growth:
Set Annual Goals
Define clear objectives for professional development each year. This may include completing specific CPE hours, attending workshops, or pursuing new skills in cybersecurity, cloud computing, or advanced auditing methodologies.
Track and Reflect
Maintain a detailed record of accomplishments, training, and professional activities. Reflecting on progress helps identify gaps, measure growth, and adjust development plans for the future.
Seek Mentorship
Engage with experienced professionals for guidance and advice. Mentors can provide insights into industry trends, career strategies, and practical challenges, helping mentees navigate their professional paths more effectively.
Participate in Industry Forums
Join online forums, discussion groups, or local ISACA chapter events. Engaging with the community fosters knowledge exchange, highlights emerging challenges, and helps build a professional reputation.
Embrace Technology
Stay current with emerging technologies and tools used in auditing, governance, and security. Familiarity with new software, automation tools, and analytics platforms enhances effectiveness and ensures relevance in modern IT environments.
The Long-Term Value of Maintaining CISA Certification
Maintaining the CISA certification is not just a requirement—it is an investment in long-term career growth. Professionals who actively engage in continuous learning:
Strengthen their technical expertise and analytical skills
Enhance credibility and trust with employers, clients, and peers
Expand career opportunities and potential for higher-level positions
Stay adaptable to evolving industry trends, risks, and regulations
Contribute meaningfully to organizational success and IT governance
The ongoing commitment to education and professional ethics ensures that CISA-certified professionals remain leaders in auditing, governance, and security fields.
CISA certification represents expertise, integrity, and leadership in information systems auditing. Maintaining the credential through continuing professional education, adherence to ethical standards, and active professional development is essential for long-term success.
By completing CPE requirements, engaging in specialized training, developing leadership skills, and staying informed about emerging trends, CISA-certified professionals remain competitive and valuable to organizations. These efforts not only ensure compliance with ISACA requirements but also foster growth, credibility, and recognition in the industry.
Investing in continuous development transforms the certification from a milestone into a lifelong career asset. Professionals who maintain their CISA certification are equipped to adapt to new challenges, lead audit and security initiatives, and contribute meaningfully to organizational success. The path of continuous learning and professional engagement ensures that CISA-certified individuals remain influential, respected, and effective leaders in the dynamic field of IT auditing and information security.
Applying CISA Knowledge in the Real World
Earning the CISA certification equips professionals with a deep understanding of auditing, governance, risk management, and information security. However, the true value of the credential comes from applying this knowledge effectively in real-world organizational settings. CISA-certified professionals bridge the gap between technical expertise and strategic decision-making, ensuring that information systems operate securely, efficiently, and in alignment with business goals.
Practical application goes beyond theoretical knowledge. It involves using auditing principles to identify risks, evaluating controls, advising stakeholders, and supporting organizational growth. Professionals must translate their certification learning into actionable strategies that deliver tangible benefits.
Integrating CISA Principles into Daily Work
CISA-certified professionals operate across a wide range of roles, from auditing to governance to cybersecurity. Integrating CISA principles into daily work involves several key practices:
Risk-Based Auditing
Risk-based auditing is central to the CISA approach. Professionals focus on areas with the greatest potential impact on organizational objectives. This requires:
Identifying critical assets and processes
Assessing potential threats and vulnerabilities
Evaluating existing controls for effectiveness
Prioritizing audit efforts based on risk exposure
This approach ensures that auditing resources are allocated efficiently and that high-risk areas receive appropriate attention.
Governance Alignment
CISA principles emphasize the alignment of IT strategy with business objectives. Professionals ensure that IT initiatives support organizational goals by:
Reviewing policies and governance frameworks
Evaluating decision-making processes
Assessing resource allocation and performance metrics
Advising leadership on strategic improvements
Governance alignment strengthens organizational efficiency and ensures that IT investments contribute positively to long-term objectives.
Strengthening Security Controls
Protecting information assets is a core responsibility of CISA-certified professionals. This involves:
Implementing security controls based on risk assessments
Monitoring systems for potential threats or breaches
Ensuring compliance with regulatory requirements
Recommending corrective actions to strengthen defenses
By focusing on security, auditors and analysts help prevent data loss, financial damage, and reputational harm.
Enhancing Operational Resilience
Operational resilience ensures that organizations continue to function effectively during disruptions. CISA-certified professionals contribute by:
Reviewing disaster recovery and business continuity plans
Evaluating operational processes for efficiency and risk mitigation
Testing response protocols to ensure readiness
Advising on improvements to minimize downtime or data loss
Operational resilience is increasingly critical in the face of cyberattacks, natural disasters, and system failures, making this skillset highly valuable.
Practical Insights for CISA Professionals
Beyond technical knowledge, success in real-world roles requires a combination of strategic thinking, interpersonal skills, and continuous learning.
Effective Communication
CISA professionals often need to communicate audit findings, risks, and recommendations to non-technical stakeholders. Clear, concise, and persuasive communication is essential. This includes:
Presenting complex technical information in understandable terms
Highlighting the business impact of risks and controls
Offering actionable recommendations rather than abstract observations
Building consensus and supporting informed decision-making
Strong communication ensures that audits and assessments influence meaningful change within the organization.
Problem-Solving and Analytical Thinking
CISA professionals must analyze complex systems, identify root causes of issues, and develop effective solutions. This requires:
Evaluating data and evidence critically
Considering multiple perspectives and potential outcomes
Applying professional judgment to resolve challenges
Leveraging both technical knowledge and practical experience
Analytical thinking allows professionals to address systemic problems and improve organizational processes.
Staying Current with Emerging Trends
Technology and cyber threats evolve rapidly. CISA-certified professionals must remain informed about emerging risks, new tools, and evolving standards. Areas of focus include:
Cloud computing and virtualization
Cybersecurity threats and incident response strategies
Data privacy regulations and compliance requirements
Advanced auditing tools and automation
Proactive learning ensures that professionals remain effective and relevant, ready to address modern challenges.
Real-World Success Strategies
To maximize the benefits of CISA certification, professionals should adopt strategies that combine preparation, application, and ongoing growth.
Hands-On Experience
Practical experience is invaluable. Professionals should seek opportunities to:
Participate in audits or assessments of varying complexity
Lead projects that enhance risk management or governance
Collaborate with cross-functional teams to implement security measures
Analyze incidents and apply lessons learned to prevent future occurrences
Hands-on experience reinforces theoretical knowledge and builds confidence in decision-making.
Mentorship and Collaboration
Learning from experienced professionals accelerates growth. Mentorship and collaboration allow individuals to:
Gain insights into real-world challenges
Learn best practices for audit planning and execution
Develop leadership and interpersonal skills
Expand professional networks and career opportunities
Active engagement with mentors and peers enhances both competence and credibility.
Continuous Improvement
CISA-certified professionals should embrace a mindset of continuous improvement, seeking opportunities to enhance skills and refine processes. This includes:
Regularly reviewing audit methodologies and frameworks
Incorporating feedback from stakeholders into future audits
Exploring new tools, technologies, and best practices
Adapting strategies to address evolving organizational and technological needs
Continuous improvement ensures that professionals remain valuable contributors and thought leaders within their organizations.
Ethical Leadership
Ethics is a cornerstone of CISA certification. Professionals should uphold integrity, objectivity, and confidentiality in all activities. Ethical leadership involves:
Making decisions that prioritize organizational and stakeholder interests
Addressing conflicts of interest transparently
Modeling professional behavior for peers and junior staff
Promoting a culture of accountability and compliance
Ethical conduct reinforces trust and credibility, critical for success in auditing, governance, and security roles.
Leveraging CISA for Strategic Impact
CISA-certified professionals can move beyond technical execution to strategic influence. By aligning audit, risk, and security functions with business objectives, they contribute to long-term organizational success.
Driving Policy and Procedure Improvements
Auditors and governance professionals identify areas where policies or procedures may be inadequate or outdated. By recommending improvements, they help organizations:
Enhance operational efficiency
Strengthen risk management practices
Ensure regulatory compliance
Reduce exposure to cyber threats and operational failures
Influencing Decision-Making
CISA professionals provide insights that inform executive decision-making. By analyzing risks, controls, and IT performance, they:
Advise on technology investments and strategic initiatives
Recommend risk mitigation strategies
Highlight potential consequences of operational decisions
Support alignment between IT and business strategy
Contributing to Organizational Culture
Professionals with CISA certification influence organizational culture by promoting accountability, transparency, and security awareness. Their actions can:
Encourage employees to follow best practices for data protection
Foster collaboration between IT, security, and business teams
Reinforce the importance of compliance and ethical conduct
Cultivate a culture of continuous improvement
Measuring Success and Impact
CISA-certified professionals should track the impact of their work to demonstrate value to the organization. Metrics may include:
Reduction in audit findings or compliance violations
Improved risk management and mitigation outcomes
Enhanced operational resilience and system reliability
Increased efficiency and effectiveness of IT controls
Stakeholder satisfaction and confidence in audit processes
By quantifying achievements, professionals can highlight the tangible benefits of their expertise and justify further investments in auditing and security initiatives.
Conclusion
The CISA certification equips professionals with the knowledge, skills, and credibility needed to excel in auditing, governance, and information security roles. Its value extends far beyond passing the exam; it lies in the practical application of principles to real-world challenges.
CISA-certified professionals contribute to organizational success by:
Assessing risks and implementing effective controls
Aligning IT initiatives with strategic business objectives
Strengthening security measures and operational resilience
Influencing decision-making and policy development
Promoting ethical leadership and a culture of accountability
Practical application, continuous learning, and strategic thinking ensure that the certification translates into meaningful career growth and organizational impact. Professionals who embrace these principles position themselves as trusted advisors, influential leaders, and highly sought-after experts in the dynamic field of information systems auditing and security.
By integrating CISA knowledge into daily work, pursuing continuous development, and demonstrating ethical leadership, professionals can maximize the benefits of their certification and achieve long-term success.
ExamCollection provides the complete prep materials in vce files format which include Isaca CISA certification exam dumps, practice test questions and answers, video training course and study guide which help the exam candidates to pass the exams quickly. Fast updates to Isaca CISA certification exam dumps, practice test questions and accurate answers vce verified by industry experts are taken from the latest pool of questions.
Isaca CISA Video Courses

Top Isaca Certification Exams
Site Search: