- Home
- Checkpoint
- 156-315.77 Check Point Certified Security Expert Dumps
Pass Your Checkpoint CCSE 156-315.77 Exam Easy!
Checkpoint CCSE 156-315.77 Exam Questions & Answers, Accurate & Verified By IT Experts
Instant Download, Free Fast Updates, 99.6% Pass Rate
Checkpoint CCSE 156-315.77 Practice Test Questions in VCE Format
| File | Votes | Size | Date |
|---|---|---|---|
File Checkpoint.Pass4sure.156-315.77.v2015-03-09.by.Angelo.519q.vce |
Votes 36 |
Size 3.3 MB |
Date Mar 09, 2015 |
File Checkpoint.Testking.156-315.77.v2015-02-27.by.Mike.363q.vce |
Votes 9 |
Size 3.16 MB |
Date Feb 27, 2015 |
Archived VCE files
| File | Votes | Size | Date |
|---|---|---|---|
File Checkpoint.Passit4sure.156-315.77.v2015-03-28.by.Sadie.344q.vce |
Votes 108 |
Size 1.21 MB |
Date Mar 28, 2015 |
Checkpoint CCSE 156-315.77 Practice Test Questions, Exam Dumps
Checkpoint 156-315.77 (Check Point Certified Security Expert) exam dumps vce, practice test questions, study guide & video training course to study and pass quickly and easily. Checkpoint 156-315.77 Check Point Certified Security Expert exam dumps & practice test questions and answers. You need avanset vce exam simulator in order to study the Checkpoint CCSE 156-315.77 certification exam dumps & Checkpoint CCSE 156-315.77 practice test questions in vce format.
Mastering the Checkpoint 156-315.77 Exam: A Comprehensive Introduction
The 156-315.77 Exam is the official test leading to the Check Point Certified Security Expert R77 certification. This examination is designed for security professionals who need to manage and support Check Point security solutions at an expert level. It goes far beyond the foundational knowledge tested in the associate-level certification, focusing instead on advanced configuration, management, and troubleshooting of the Security Gateway and Management Server architecture. Passing this exam demonstrates a candidate's ability to handle complex security implementations, including redundant deployments, advanced VPN configurations, and in-depth troubleshooting of network traffic. Success in the 156-315.77 Exam requires a deep understanding of the underlying technologies that power Check Point’s security platform. This includes a thorough grasp of the Gaia operating system, ClusterXL for high availability, advanced firewall features, and the various Software Blades responsible for threat prevention. The exam is structured to test not just theoretical knowledge but also the practical skills needed to deploy, maintain, and resolve issues in real-world enterprise environments. Candidates should be prepared for scenario-based questions that require them to apply their knowledge to solve specific problems.
Understanding the CCSE R77 Certification Path
The path to achieving the Check Point Certified Security Expert (CCSE) R77 designation typically begins with the Check Point Certified Security Administrator (CCSA) certification. The CCSA provides the foundational knowledge required to work with Check Point products, covering essential tasks like creating security policies, managing user access, and monitoring network activity. The 156-315.77 Exam is the next logical step, building directly upon the skills learned at the administrator level. It is designed for professionals who have already mastered the basics and are ready to tackle more complex and demanding security challenges. While CCSA is a formal prerequisite, practical experience is equally crucial. The 156-315.77 Exam assumes candidates have hands-on experience deploying and managing Check Point solutions. The questions are designed to test skills that are developed through day-to-day administration and problem-solving. Therefore, a study plan should incorporate not only theoretical learning through official courseware and documentation but also extensive practice in a lab environment. This combination of knowledge and experience is the key to successfully navigating the advanced topics covered in the expert-level examination.
The Relevance of R77 in Modern Networks
While newer versions of Check Point's software, such as R80 and beyond, have been released, the R77 version remains relevant in many organizations. A large number of enterprises continue to run on this stable and well-understood platform due to long-term support cycles, infrastructure compatibility, or phased upgrade schedules. For security engineers and consultants working in these environments, a deep knowledge of R77, as validated by the 156-315.77 Exam, is not just beneficial but often essential. It ensures they can effectively manage, troubleshoot, and secure the existing infrastructure without immediate pressure to upgrade. Furthermore, the core principles tested in the 156-315.77 Exam are foundational to all subsequent versions of Check Point’s architecture. Concepts like stateful inspection, ClusterXL, IPsec VPNs, and policy management remain central to the product line. Mastering these topics in the context of R77 provides a strong and transferable skill set. This knowledge facilitates a smoother transition to newer versions, as the underlying logic and troubleshooting methodologies are largely consistent. Therefore, pursuing this certification is a valuable investment for understanding both legacy systems and the evolution of the security platform.
Core Components of the Gaia Architecture
The 156-315.77 Exam requires a comprehensive understanding of the Gaia operating system, which is the foundation for Check Point Security Gateways and Management Servers. Gaia unifies the legacy SecurePlatform and IPSO operating systems into a single, robust platform. It provides a feature-rich and secure environment for all Check Point software components. Key features that candidates must master include the web-based user interface for simplified management and the powerful command-line interface (clish) for advanced configuration and scripting. Understanding the integration of these two interfaces is crucial for efficient system administration. Gaia’s architecture is designed for security and performance. It supports both IPv4 and IPv6 and offers advanced routing capabilities, including dynamic routing protocols like OSPF and BGP. This allows Check Point gateways to integrate seamlessly into complex corporate networks. Another critical aspect is role-based administration, which allows for granular control over user permissions, ensuring that administrators only have access to the functions necessary for their roles. A solid grasp of Gaia's system management, backup procedures, and snapshot capabilities is essential for maintaining a stable and recoverable security environment, a topic frequently tested in the exam.
Navigating SmartDashboard and Key Management Blades
SmartDashboard is the primary legacy client for managing security policies and configuring objects in the R77 environment. For the 156-315.77 Exam, candidates must possess expert-level proficiency in its use. This includes creating complex rulebases, defining intricate network objects, and managing application control and URL filtering policies. A deep understanding of the policy installation process, including verification and troubleshooting failed installations, is a critical skill. Candidates should be comfortable navigating the various tabs and menus to configure every aspect of the security policy, from firewall rules to NAT and VPN settings. Beyond the firewall blade, the exam covers the configuration and management of several other key Software Blades through SmartDashboard. The Identity Awareness blade, for instance, allows for the creation of policies based on user and machine identities, rather than just IP addresses. The Application Control and URL Filtering blades provide granular control over web traffic and applications. Mastery involves understanding how these blades work together to create a multi-layered security posture. Candidates must be able to configure their settings, analyze their logs, and optimize their performance for a given network environment.
Fundamentals of Check Point Firewall Policy
At the heart of any Check Point deployment is the firewall policy, and the 156-315.77 Exam tests this area extensively. A core concept is the rulebase processing order. Rules are evaluated from top to bottom, and the first rule that matches the traffic is applied. This principle dictates that more specific rules must be placed above more general ones to function correctly. Understanding this logic is fundamental to designing a secure and efficient policy. The exam will likely present scenarios where candidates must analyze a rulebase to predict traffic behavior or identify misconfigurations. Another critical aspect is the implicit cleanup rule, which by default drops any traffic that does not match a preceding explicit rule. Candidates must understand its function and how to modify it if necessary. The concept of stealth and anti-spoofing rules is also vital. Stealth rules prevent direct connections to the firewall, protecting it from attack, while anti-spoofing is configured on interfaces to prevent attackers from using forged source IP addresses. A thorough knowledge of how to create, manage, and optimize these foundational policy elements is non-negotiable for anyone attempting the 156-315.77 Exam.
Introduction to Network Address Translation (NAT)
Network Address Translation (NAT) is a fundamental networking concept that is heavily featured in the 156-315.77 Exam. Check Point implements NAT within the firewall policy, allowing for flexible and granular control over address translation. The two primary types of NAT are Hide NAT and Static NAT. Hide NAT is used to translate the IP addresses of multiple internal clients into a single public IP address, typically the external IP of the gateway. This is common for providing internet access to internal networks while conserving public IP addresses. Static NAT, on the other hand, creates a one-to-one mapping between a private IP address and a public IP address. This is typically used to make an internal server, such as a web server, accessible from the internet. The 156-315.77 Exam requires candidates to know how to configure both types of NAT, understand the NAT rule processing order relative to the security policy, and troubleshoot common NAT issues. Advanced scenarios may involve complex translations, such as port mapping or server load balancing, which require a deeper understanding of the underlying mechanisms.
Preparing a Study Plan for the 156-315.77 Exam
Creating a structured study plan is essential for success on the 156-315.77 Exam. The first step should be to download the official exam objectives from the vendor. These objectives provide a detailed outline of all the topics that may be covered, from Gaia administration to advanced troubleshooting. This document should serve as a checklist to guide your learning and ensure that no critical areas are overlooked. Allocate study time based on your familiarity with each topic, dedicating more time to areas where you feel less confident. Your study materials should be diverse. While official Check Point courseware is highly recommended, it should be supplemented with official administration guides and technical whitepapers. These documents often provide a deeper level of detail than the training courses. Most importantly, your plan must include significant time for hands-on practice. Building a lab environment using virtual machines is an effective way to gain practical experience. Practice configuring ClusterXL, setting up complex VPNs, and using command-line tools to diagnose problems. This practical application solidifies theoretical knowledge and prepares you for the scenario-based questions on the exam.
Key Differences Between CCSA and CCSE
The transition from the CCSA to the CCSE level represents a significant leap in complexity and depth. The CCSA certification focuses on the day-to-day administrative tasks required to manage a single Check Point security gateway. This includes building a basic security policy, managing users, and monitoring traffic. The 156-315.77 Exam, however, targets expert-level skills needed for large-scale and redundant enterprise deployments. It moves beyond single gateway management to focus on multi-gateway environments, high availability, and advanced security features. For example, where a CCSA candidate needs to know how to create a NAT rule, a CCSE candidate must understand how to troubleshoot complex NAT scenarios that overlap with VPN traffic. While a CCSA learns to enable Software Blades, a CCSE must know how to optimize their performance and troubleshoot their operation at a deep level. The CCSE curriculum also introduces advanced topics not covered in the CCSA, such as command-line troubleshooting with tools like fw monitor and cphaprob, kernel debug procedures, and advanced clustering configurations. The emphasis shifts from "how to configure" to "why it works and how to fix it when it breaks."
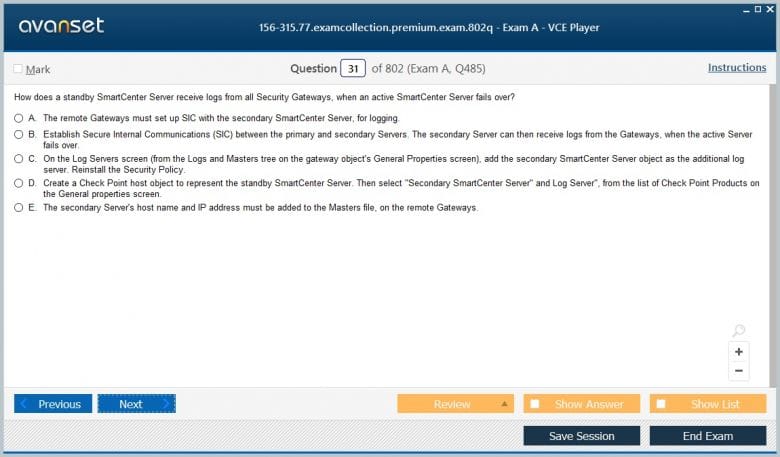
Deep Dive into ClusterXL Technology
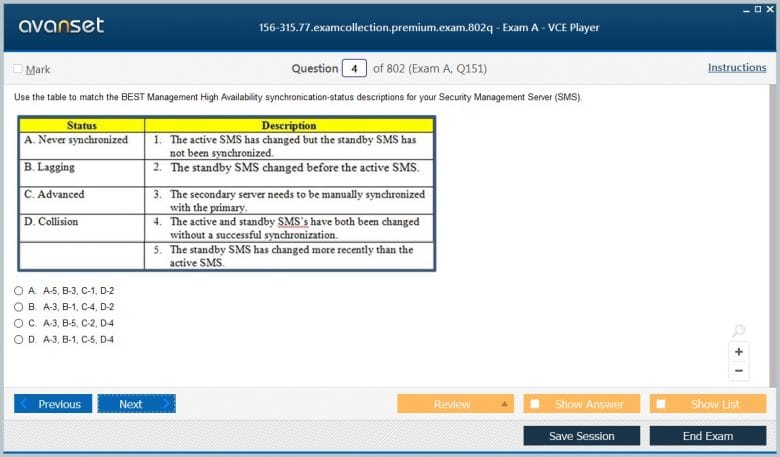
ClusterXL is Check Point's proprietary high availability and load sharing solution, and it is a cornerstone of the 156-315.77 Exam. This technology allows multiple Security Gateways to be grouped into a single, logical entity known as a cluster. The primary goal of ClusterXL is to provide uninterrupted network connectivity and security by ensuring that if one cluster member fails, another member takes over its responsibilities seamlessly. A deep understanding of the Cluster Control Protocol (CCP), which is used for state synchronization and health checks between cluster members, is absolutely essential for the exam. Candidates must be familiar with the different components that make up a ClusterXL deployment. This includes the synchronization network, which is a dedicated interface used to pass state and synchronization information between members. The concept of a pivot member in Load Sharing mode and the roles of master and standby in High Availability mode are also critical. The 156-315.77 Exam will test your ability to not only configure a cluster from scratch but also to troubleshoot common issues related to synchronization, failover events, and network connectivity problems specific to a clustered environment.
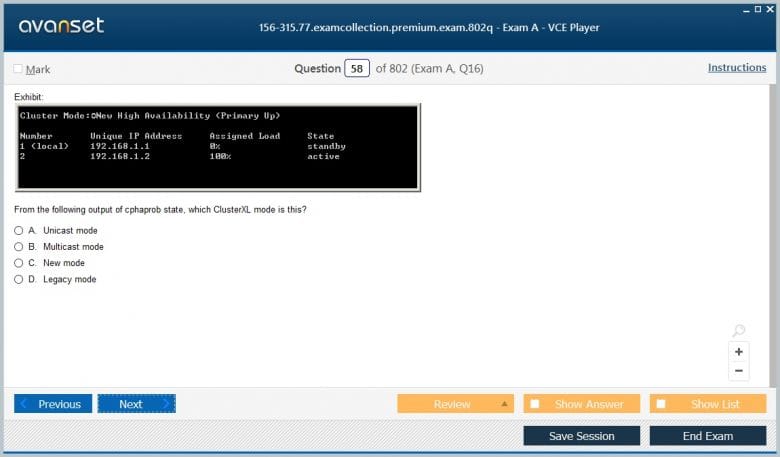
Understanding High Availability and Load Sharing Modes
ClusterXL operates in two primary modes: High Availability and Load Sharing. The High Availability mode is designed for redundancy. In this configuration, one gateway acts as the active member, processing all network traffic, while the other members remain in a standby state. The standby members are continuously updated with state information from the active member via the synchronization network. If the active member fails, a standby member is promoted to active status and begins processing traffic, a process known as failover. This ensures minimal disruption to network services. The Load Sharing mode, on the other hand, is designed to distribute the traffic load across multiple active cluster members, providing both redundancy and performance enhancement. This mode is available in Unicast and Multicast configurations, and the 156-315.77 Exam requires knowledge of both. In Load Sharing, a designated member called the pivot is responsible for assigning connections to different members of the cluster. Understanding how the pivot makes these decisions and how to troubleshoot load distribution problems is a key skill for any CCSE candidate. The exam will likely present scenarios requiring you to choose the appropriate mode for a given business requirement.
Advanced Network Address Translation Scenarios
The 156-315.77 Exam moves beyond basic Hide and Static NAT to cover more complex and nuanced scenarios. One such scenario is NAT on a clustered deployment. Candidates must understand how NAT is handled during a failover event and how to ensure that translated connections persist without interruption. This involves a deep understanding of how the NAT translation tables are synchronized between cluster members. Misconfigurations in a clustered NAT environment can lead to significant connectivity issues, making it a prime topic for troubleshooting questions. Another advanced area is the interaction between NAT and VPNs. When traffic is destined for a VPN tunnel, the timing of the NAT process is critical. The exam will test your knowledge of whether to apply NAT before or after encryption and how to configure the system to achieve the desired outcome. This often involves working with manual NAT rules and understanding their placement within the rulebase relative to automatic NAT rules. Scenarios involving overlapping IP addresses between two sites connected by a VPN, which requires NAT to resolve, are also common expert-level challenges.
Mastering the Command Line Interface (CLI)
While the Gaia web interface is useful for many administrative tasks, the Command Line Interface (CLI) provides more powerful and granular control over the system. For the 156-315.77 Exam, proficiency in the CLI is not optional. Candidates are expected to be comfortable with both the standard expert mode shell and the configuration shell, known as clish. The clish environment provides a structured way to configure system settings like interfaces, routing, and clustering, often with built-in validation to prevent errors. Knowing how to perform key configuration tasks from clish is a required skill. The expert mode provides a standard Linux shell environment, giving administrators access to the full range of system commands and diagnostic tools. This is where advanced troubleshooting takes place. Expert-level engineers must know how to navigate the file system, view and edit configuration files, and use powerful utilities to analyze system behavior. The 156-315.77 Exam will expect you to know the purpose and syntax of various CLI commands related to firewall processes, kernel parameters, and cluster status, as these are indispensable for resolving complex issues.
Working with fw monitor for Packet Analysis
fw monitor is arguably the most powerful built-in tool for troubleshooting traffic flow through a Check Point Security Gateway. It allows an administrator to view the packet's journey as it is processed by the firewall's inspection chain. The 156-315.77 Exam requires a thorough understanding of how to use fw monitor to diagnose a wide range of problems, from policy misconfigurations to NAT issues. Candidates must know the proper syntax for capturing specific traffic based on source, destination, and port, as well as how to interpret the detailed output it produces. The output of fw monitor provides a step-by-step description of how the firewall is handling a packet, indicating which rule it matched, whether NAT was applied, and if it was ultimately accepted or dropped. The tool uses a specific notation to represent the different inspection points within the kernel. Understanding what each of these points signifies (pre-inbound, post-inbound, pre-outbound, post-outbound) is critical for accurately diagnosing the root cause of a problem. The ability to use fw monitor effectively separates junior administrators from expert-level troubleshooters.
Identity Awareness and User-Based Policies
The Identity Awareness Software Blade provides the ability to create firewall policies based on user or group identity rather than just on source IP addresses. This is a critical feature for modern networks where users may access resources from multiple devices or locations. The 156-315.77 Exam covers the configuration and management of this blade in detail. Candidates must understand the various methods for acquiring user identity, including AD Query, Browser-Based Authentication (Captive Portal), and the Endpoint Identity Agent. Choosing the right method depends on the specific requirements of the environment. Once identities are acquired, they can be used to build a more granular and meaningful security policy. For example, you can create a rule that allows only members of the finance department to access the accounting servers, regardless of the IP address they are using. The 156-315.77 Exam will test your ability to configure these identity-based rules, troubleshoot identity acquisition issues, and manage user sessions. Understanding the flow of identity information from the source to the Security Gateway is key to mastering this topic.
Configuring and Managing Application Control
The Application Control Software Blade gives administrators visibility into and control over the specific applications and web protocols being used on their network. It goes beyond simple port-based filtering, using deep packet inspection to identify thousands of different applications, such as social media platforms, streaming services, and peer-to-peer file sharing. For the 156-315.77 Exam, you must know how to create policies that leverage this granular control. This includes allowing, blocking, or rate-limiting specific applications or categories of applications to enforce corporate usage policies and conserve bandwidth. Effective management of Application Control also involves using the visibility it provides. SmartLog and SmartView Tracker can be used to generate detailed reports on application usage across the network. This information is invaluable for understanding traffic patterns, identifying potential security risks, and refining the security policy over time. The exam may present scenarios where you need to analyze application logs to identify a problem or create a policy to address a specific business need, such as blocking all high-bandwidth entertainment applications for a particular group of users.
URL Filtering Blade for Web Security
Working in tandem with Application Control, the URL Filtering Software Blade provides granular control over access to websites based on their content categories. Check Point maintains a massive database of websites, categorized into groups such as gambling, social networking, malware, and phishing. The 156-315.77 Exam requires candidates to be proficient in creating policies that use these categories to protect users and enforce acceptable use policies. For example, a rule could be created to block access to all known malware distribution sites for all users. An important aspect of URL Filtering is the ability to create exceptions and customize policies for different user groups. You might need to allow the marketing department to access social networking sites while blocking them for all other employees. The exam will test your ability to configure these nuanced policies and to manage custom categories for uncategorized or internal websites. Understanding how URL Filtering interacts with other blades, such as Application Control and the HTTPS Inspection feature for decrypting SSL/TLS traffic, is crucial for building a comprehensive web security strategy.
Troubleshooting Common Security Gateway Issues
The 156-315.77 Exam places a heavy emphasis on troubleshooting. A common issue that security experts must diagnose is incorrect traffic routing. This can be caused by misconfigured static routes, issues with dynamic routing protocols, or problems with the gateway's interface configuration. Candidates must know how to use CLI tools like netstat and ip route to inspect the gateway's routing table and identify the source of the problem. Understanding how the gateway makes routing decisions is fundamental to resolving these types of issues. Another frequent problem is policy misconfiguration, where a rule is either too permissive or too restrictive. The primary tool for diagnosing this is the log file, viewed through SmartLog or SmartView Tracker. An expert administrator must be able to filter and analyze logs efficiently to determine which rule is matching a specific traffic flow and why it is being allowed or dropped. For more complex issues where the logs do not provide enough information, tools like fw monitor become necessary to trace the packet's path through the firewall kernel and pinpoint the exact point of failure.
Fundamentals of IPsec VPNs
Virtual Private Networks (VPNs) are a critical component of modern network security, and the 156-315.77 Exam covers them in extensive detail. The exam focuses primarily on IPsec-based VPNs, which provide a secure method for connecting remote networks or users to a central corporate network over an untrusted medium like the internet. To succeed, candidates must have a solid understanding of the underlying protocols that make up the IPsec suite. This includes the Internet Key Exchange (IKE) protocol, which handles the negotiation of security parameters and the generation of encryption keys. The IKE negotiation process itself occurs in two phases. Phase 1 establishes a secure, authenticated channel between the two VPN gateways. Phase 2 uses this secure channel to negotiate the IPsec Security Associations (SAs) that will be used to protect the actual user data. The 156-315.77 Exam requires a deep knowledge of the different modes and parameters involved in both phases, such as authentication methods (pre-shared keys or certificates), encryption algorithms (like AES), and hashing algorithms (like SHA). A clear grasp of these fundamentals is essential for both configuration and troubleshooting.
Configuring Site-to-Site VPNs with Gaia
A site-to-site VPN securely connects two entire networks, such as a branch office and a corporate headquarters. The 156-315.77 Exam requires candidates to be proficient in configuring these connections using Check Point's architecture. This process typically involves creating network objects to represent the VPN gateways and the networks that will be communicating through the tunnel. These objects are then grouped into a VPN community, which simplifies the management of the VPN topology and the underlying encryption and security settings. The configuration is managed primarily through SmartDashboard. Candidates must be able to define the encryption domains for each gateway, which specifies which networks are allowed to send traffic through the VPN tunnel. They must also be able to configure the IKE and IPsec properties for the VPN community, ensuring that both sides of the tunnel are using compatible settings. The exam will test not only the initial setup but also the ability to modify existing VPNs, add new sites to a community, and verify that the VPN tunnel is active and passing traffic correctly.
Route-Based versus Policy-Based VPNs
Check Point supports two primary methods for implementing site-to-site VPNs: policy-based and route-based. Policy-based VPNs are the traditional method, where the decision to encrypt traffic is made based on a specific rule in the firewall policy. The encryption domain is defined by network objects, and any traffic matching the source and destination in the VPN rule is encrypted. This method is straightforward but can become cumbersome to manage in complex networks with many subnets. Route-based VPNs, on the other hand, use a virtual tunnel interface (VTI). All traffic routed to the VTI is automatically encrypted and sent to the peer gateway. This approach simplifies the security policy, as you only need a simple rule allowing traffic to flow between the networks. The complexity is shifted to the network routing layer, which is often more flexible and scalable, especially when used with dynamic routing protocols. The 156-315.77 Exam requires candidates to understand the pros and cons of each method and to be able to configure, manage, and troubleshoot both types of VPN implementations.
Managing Remote Access for End Users
In addition to connecting sites, VPNs are essential for providing secure remote access to individual users, such as employees working from home or on the road. The 156-315.77 Exam covers the configuration of Check Point's remote access solutions. This typically involves deploying an endpoint security VPN client on the user's machine. The client establishes a secure tunnel to the corporate Security Gateway, giving the user access to internal network resources as if they were physically in the office. Configuration on the gateway side involves setting up the Mobile Access Software Blade and defining remote access communities. Administrators must configure authentication methods, which could range from simple usernames and passwords to more secure options like certificates or two-factor authentication. They also need to define an IP address pool to assign addresses to remote users and create security policy rules to control what resources those users can access. The exam will test your ability to manage the entire lifecycle of a remote access deployment, from initial setup to user management and troubleshooting connectivity issues.
SSL VPN and the Mobile Access Blade
For situations where installing a full VPN client is not feasible or desirable, Check Point offers an SSL VPN solution through the Mobile Access Blade. This allows users to access corporate resources securely using only a standard web browser. The 156-315.77 Exam requires candidates to understand how to configure the Mobile Access portal, which provides users with a secure entry point to internal applications. This can include web applications, file shares, and even native applications through various secure proxies. The key advantage of the SSL VPN is its clientless nature, which simplifies deployment for a wide range of devices, including mobile phones and tablets. Candidates must know how to configure the different access methods available through the Mobile Access portal, such as Web Applications, Secure Workspace, and Native Application access. They also need to be able to set up robust authentication policies and customize the portal's appearance and functionality to meet specific corporate requirements. Understanding the security implications and use cases for each access method is a critical part of the curriculum.
Visitor Mode and Clientless Access Solutions
Visitor Mode, now more commonly known as VPN over TCP, is a feature of the Check Point remote access client that encapsulates IPsec traffic within a TCP packet, typically on port 443. This is extremely useful for users who are behind restrictive firewalls or NAT devices that might block standard IKE and ESP packets. The 156-315.77 Exam expects candidates to know when and how to enable this feature to overcome common remote access connectivity problems. It is a key troubleshooting tool for ensuring that mobile users can connect from almost any location. Beyond Visitor Mode, the broader concept of clientless access is an important topic. This primarily refers to the SSL VPN portal provided by the Mobile Access blade. This solution is ideal for providing controlled access to specific applications for non-employee users, such as contractors or business partners. Instead of granting them full network access with a traditional VPN client, clientless access can restrict them to only the web-based applications they need. Understanding these different access paradigms and choosing the right one for a given scenario is a hallmark of a security expert.
Advanced VPN Authentication Methods
While pre-shared keys are simple to configure, they are not considered a secure authentication method for large-scale or high-security environments. The 156-315.77 Exam emphasizes the use of more robust authentication mechanisms, particularly digital certificates. Using a Public Key Infrastructure (PKI), certificates provide a much stronger form of authentication for both site-to-site and remote access VPNs. Candidates must understand the role of a Certificate Authority (CA), how to generate and deploy certificates on gateways and clients, and how to configure the VPN to use them for authentication. For remote access, integrating with existing user directories like Active Directory is essential. The exam covers how to use protocols like RADIUS or LDAP to authenticate remote users against a central database. This simplifies user management and allows for the enforcement of corporate password policies. Furthermore, the exam will likely cover the implementation of two-factor authentication (2FA), which adds an additional layer of security by requiring users to provide a second form of verification, such as a one-time password from a token or mobile app.
Troubleshooting VPN Connectivity with vpn debug
When a VPN tunnel fails to establish or pass traffic, a security expert needs a systematic approach to troubleshooting. The 156-315.77 Exam requires proficiency with the powerful vpn debug command-line utility. This tool provides a real-time view of the IKE negotiation process, allowing an administrator to see the exchange of packets between the two gateways. By analyzing the vpn debug output, you can pinpoint the exact reason for a negotiation failure, such as a mismatch in encryption proposals, an authentication error, or a connectivity problem. Common issues that can be diagnosed with vpn debug include incorrect pre-shared keys, invalid certificates, or mismatched encryption domains. The tool can also help identify routing problems or NAT issues that are preventing VPN traffic from being processed correctly. In addition to vpn debug, candidates should also be familiar with other related tools like fw monitor to trace the path of the encrypted packets and the logs in SmartView Tracker to get a high-level overview of VPN activity. A combination of these tools is often required to solve complex VPN problems.
Understanding VPN Communities
In the Check Point architecture, a VPN community is the central object used to manage the settings for a group of VPN gateways. Instead of configuring encryption properties individually for each tunnel, you configure them once for the community, and they are inherited by all members. The 156-315.77 Exam tests your ability to effectively manage both Meshed and Star VPN communities. In a Meshed community, every gateway can establish a VPN tunnel directly with every other gateway. This is useful for decentralized networks where any site may need to communicate directly with any other site. In a Star community, a central gateway (the hub) is defined, and all other gateways (the spokes) can only establish tunnels with the hub. Spoke-to-spoke communication must pass through the central hub. This topology is very common in hub-and-spoke network designs, as it simplifies routing and policy management. A CCSE candidate must know how to choose the appropriate community type, how to configure it correctly, and how to manage advanced settings like tunnel sharing and routing options within the community.
Introduction to Check Point Threat Prevention
The 156-315.77 Exam requires candidates to demonstrate expertise not just in firewalling, but also in advanced threat prevention. Check Point's approach to this is a unified, multi-layered solution managed through a set of Software Blades. These blades work together to provide comprehensive protection against known and unknown threats. The core components of this solution include Intrusion Prevention (IPS), Antivirus, Anti-Bot, Threat Emulation, and Threat Extraction. A key concept tested is the ability to configure these blades to work in concert, creating a defense-in-depth security posture. An expert-level administrator must understand the flow of traffic as it passes through these different inspection engines. The exam will expect you to know how to enable and configure these blades, create tailored threat prevention profiles for different parts of your network, and monitor their activity through SmartLog. The goal is to move beyond simple packet filtering and build a system that can proactively identify and block sophisticated cyberattacks. This requires a solid grasp of the technologies behind each blade and the best practices for their deployment and management.
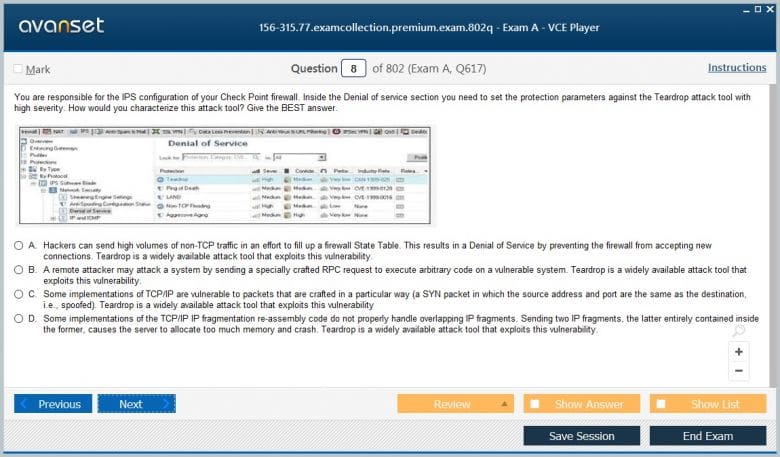
Configuring the Intrusion Prevention System (IPS) Blade
The Intrusion Prevention System (IPS) blade provides protection against network-based attacks by identifying and blocking exploits against vulnerabilities in operating systems and applications. It operates by inspecting network traffic for malicious patterns and behaviors that match its extensive database of signatures. For the 156-315.77 Exam, candidates must know how to effectively manage the IPS profile. This includes understanding the different protection activation modes, such as Prevent and Detect, and knowing when to use each. A crucial skill is the ability to tune the IPS policy to reduce false positives while maintaining a high level of security. This involves creating exceptions for specific protections, sources, or destinations when legitimate traffic is being incorrectly flagged. The exam will also cover the process of updating IPS protections to ensure the gateway is defended against the latest threats. Monitoring IPS logs is another key competency, as it allows administrators to identify active attacks, understand the nature of the threats targeting their network, and refine the IPS policy accordingly.
Understanding Antivirus and Anti-Bot Protections
The Antivirus blade is designed to prevent malware from entering the network via common protocols like HTTP, FTP, and SMTP. It scans files as they are being downloaded or transferred and blocks them if they match known malware signatures. The 156-315.77 Exam requires knowledge of how to configure the Antivirus blade, including selecting the file types to scan and defining the action to be taken when malware is detected. Understanding its role as a network-level defense complements traditional host-based antivirus solutions. The Anti-Bot blade provides protection against a different stage of the attack lifecycle. It focuses on detecting and blocking the communication of bots that have already infected machines inside the network. These bots attempt to communicate with their command and control (C&C) servers to receive instructions or exfiltrate data. The Anti-Bot blade identifies this C&C traffic based on signatures and reputation feeds, preventing the bot from carrying out its malicious activities. A CCSE candidate must be able to configure this blade, analyze its logs to identify infected hosts, and understand its importance in post-infection mitigation.
Leveraging Threat Emulation and Extraction
Threat Emulation is Check Point's advanced sandboxing solution for dealing with zero-day and unknown malware. When a file enters the network, Threat Emulation can send it to a virtual sandbox environment where it is opened and its behavior is analyzed. If the file exhibits malicious behavior, it is blocked, and a new signature is created to protect against future instances of the threat. The 156-315.77 Exam covers the different deployment options for Threat Emulation, including cloud-based and on-premise appliances, and how to configure the policy to send suspicious files for emulation. Threat Extraction complements Threat Emulation by providing immediate, threat-free content to the user. While a file is being sent for emulation, which can take a few minutes, Threat Extraction can reconstruct the file, stripping out any potentially malicious active content like macros or embedded scripts. It then delivers a clean, safe version of the file to the user instantly, minimizing business disruption. Understanding the synergy between these two blades and how to configure them to balance security with user productivity is a key expert-level skill.
Optimizing Security Policy Performance
A poorly optimized security policy can become a significant performance bottleneck on a Security Gateway. The 156-315.77 Exam tests a candidate's ability to analyze and optimize a rulebase for maximum efficiency. One of the most important tools for this is SecureXL, Check Point's patented acceleration technology. SecureXL offloads much of the traffic processing from the main CPU to dedicated hardware or software acceleration paths. Candidates must understand how SecureXL works and how to verify that traffic is being accelerated correctly using command-line tools. Another key optimization technique is proper rulebase ordering. Rules that see the most traffic should be placed as high up in the policy as possible to minimize the number of rules that need to be evaluated for each connection. The exam may present a scenario with a disorganized rulebase and ask you to identify the best way to reorder it for better performance. Additionally, understanding how to use features like inline layers and policy packages to segment and streamline the rulebase is critical for managing large and complex security policies efficiently.
Utilizing SmartLog for Event Analysis
SmartLog is the primary tool in R77 for monitoring and analyzing log data from Security Gateways and Software Blades. It provides a powerful, indexed search capability that allows administrators to quickly query vast amounts of log data. For the 156-315.77 Exam, proficiency with SmartLog is essential for troubleshooting and incident response. Candidates must be able to build effective search queries to filter logs based on any field, such as source IP, application name, or action taken. This allows for rapid identification of relevant events during a security investigation or a troubleshooting session. Beyond simple searching, SmartLog allows for the visualization of log data and the identification of trends. You can see top sources, destinations, applications, and threats at a glance. Understanding how to use these features to gain situational awareness of your network is a key skill. The exam will expect you to be able to navigate the SmartLog interface efficiently, interpret the log entries from various blades, and use the information to diagnose problems or identify security incidents.
Generating Reports with SmartReporter
While SmartLog is excellent for real-time analysis, SmartReporter is the tool for creating historical, formatted reports. The 156-315.77 Exam requires candidates to know how to use SmartReporter to generate reports on network activity, security events, and policy compliance. These reports are crucial for communicating with management, demonstrating the value of the security infrastructure, and meeting regulatory requirements. Candidates should be familiar with the wide range of pre-defined reports available and how to customize them to meet specific needs. The process involves configuring the Security Management Server to forward logs to a dedicated Log Server, which in turn feeds data to the SmartReporter server. Understanding this architecture is important for setting up the reporting system correctly. A CCSE candidate should be able to schedule reports to be generated and distributed automatically via email. They should also know how to create custom reports from scratch, selecting the specific data, charts, and tables required to convey the necessary information to the target audience.
Best Practices for Rulebase Management
As a security policy grows, it can become difficult to manage without adhering to a set of best practices. The 156-315.77 Exam will test your knowledge of these principles. One fundamental practice is to use descriptive names for all network objects, services, and rules. This makes the policy self-documenting and easier for other administrators to understand. Similarly, adding comments to complex or non-obvious rules is crucial for maintaining a clean and understandable rulebase. Another best practice is to regularly review and clean up the policy. This involves identifying and removing unused objects and redundant or shadowed rules. A shadowed rule is one that will never be matched because a rule above it in the policy will always match the same traffic. Tools within the Check Point suite can help identify these issues. Grouping related rules into sections or layers also improves readability and manageability. Following these practices not only improves performance but also reduces the risk of human error leading to a security vulnerability.
Upgrading and Patching Management Servers
Maintaining the security infrastructure involves keeping the software up to date. The 156-315.77 Exam covers the procedures for upgrading and patching Check Point components, particularly the Security Management Server. A CCSE candidate must know the correct in-place upgrade procedures as well as the migration process, which involves exporting the configuration from an old server and importing it onto a new one. Understanding the prerequisites, potential pitfalls, and rollback procedures for an upgrade is critical for minimizing downtime and risk. Patching is a more frequent task, typically done to address specific vulnerabilities or bugs. This is often accomplished by installing a hotfix. Candidates must be familiar with the process of finding, downloading, and installing hotfixes using the command line or the Gaia web interface. A key part of this process is taking a snapshot or backup of the system before applying any changes, ensuring that you have a reliable way to revert to a known good state if the patch causes unexpected issues. These maintenance skills are a core responsibility of an expert-level administrator.
Go to testing centre with ease on our mind when you use Checkpoint CCSE 156-315.77 vce exam dumps, practice test questions and answers. Checkpoint 156-315.77 Check Point Certified Security Expert certification practice test questions and answers, study guide, exam dumps and video training course in vce format to help you study with ease. Prepare with confidence and study using Checkpoint CCSE 156-315.77 exam dumps & practice test questions and answers vce from ExamCollection.
Top Checkpoint Certification Exams
Site Search: