- Home
- Popular IT Certifications
- Overview of Public Key Infrastructure, Certificate Management and Associated Components
Overview of Public Key Infrastructure, certificate management and associated components
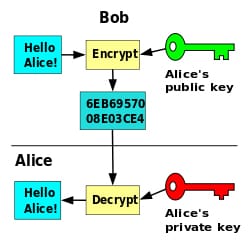
The public key infrastructure concept is one that we must be conversant with since it is a very important aspect of cryptography. It is the basis of most of the encryption techniques and therefore it is important that we have some basic knowledge about it. Certificate management is also another area we should not ignore if we are dealing with encryption of information. Here are the information about the certifications management and the components which are associated to them;
Certificate authorities and digital certificates
Here are the certifications which are commonly obtained and gained benefit from;
CA
In a public key infrastructure, a Certificate Authority is responsible for the creation and distribution of certificates to the end users and other people that will need them in the environment. These are the public and private keys and one's certificate authority is one's clearing house for this. If one is in a private organization, one may have a private certificate authority which is meant for one's own users and private servers. In such a case, one have to ensure that third party individuals to use one's certificates trust them since in most cases, people tend not to trust certificates that one have built on one's own.
One might also choose to use a public certificate authority so as to get third party individuals to use one's key. There are a number of responsibilities associated with certificate authorities. One I that they ensure the validity of certificates. It makes sure that all the people who are registering for a certificate are legitimate so as not to have some problems later.
Certificate authorities are also responsible for the management of servers that store and administer certificates. These servers are very sensitive since they are responsible for making private keys and one do not want anybody to get their hands on them.
A certificate authority is also responsible for performing key and certificate life cycle management. The certificate authority needs to make sure that if there are keys that are no longer good or if there are keys that could have been fraudulently distributed are revoked.
CRLs
The CRL which is an abbreviation for certificate revocation lists which are special types of lists that are used to carry out checks. For instance, if one wants to use a certificate, one might first want to check if the certificate has not been revoked. If it is not on the CRL list, then we can use the certificate.
OCSP
The Online Certificate Status Protocol is also another method that can be used to check for revocation of certificates. It's a little bit easier to use and more streamlined to use than a CRL. Many organizations are starting to use it to carry out checks to make sure that no certificates have been revoked.
PKI
The public key infrastructure(PKI) is a mixture of things working together such as policies, procedures, people, hardware and software all put together to create a standard way to manage, distribute these certificates, store them, revoke them. If one are going to venture into public key cryptography and one are making a PKI, it means that one will be making something that is very big which one need to plan out from the very beginning and set all the processes in place so that it can be as successful as possible. The PKI is responsible for building these certificates and binding them to people or resources.
In the public key infrastructure, there is an entire lifecycle that revolves around the keys. The first step is usually creation of the key. This is where we are developing a key with a particular cipher or key string or key size and it is one that is very specific therefore we will have to make decisions of all the exact technical details associated with generation of the keys when we first make them.
What follows next is the creation of a certificate. This is where we will allocate that key to a person who can bind us together and create that x509 certificate that includes the key and other details. What follows is the distribution of the keys to the end users, the certificates are sent out to our certificate servers. This is a process that needs to be available to our users and it should be as secure as possible.
The key life cycle also involves storing of the information. We are creating a lot of certificates and building out a lot of keys and so these are extremely valuable and private and private keys that we do not want to get into the wrong hands. This means that there has to be a proper storage mechanism so as to handle this. Ultimately, there may be a need to revoke these keys. Some of the keys may be compromised, the business may close down, people may leave the organization or there might be some certain amount of time that the key is valid and so at the end of that time from or for one of those reasons we need to have a processing place that is able to properly revoke those keys and make everyone realize that we have revoked them by perhaps having some key revocation lists or other mechanisms in place so that people understand which keys have been revoked and which ones have not.
Finally, is an expiration. Similar to other items, keys may only have a certain short life. For instance, one may have created them to only last for three months and after that time, the key is no longer valid and one will have to create new keys. It is at this point that the cycle goes back to the top and begins again.
As long as one are thinking about one's public key infrastructure and building out one's processes and procedures to take into account every single step along the way of this life cycle, one should have a very successful; public key infrastructure.
Recovery agent
The idea of key recovery basically means that we have put some processes in place to make sure that should something happen to that key, we have ways of recovering data that had been encrypted with the lost key. One of the ways it to back-up the private key. However, one need to make sure that one do not have too many backups of the private key or rather too many versions of it to avoid it getting into the hands of other people. Therefore, one need to be sure that the private key is backed up but not too much.
In every organization, there is already a key recovery process that will start up from the beginning if the key is lost. We want to have a process where an organization can recover the data or private key and therefore the recovery process is probably built into one's public key infrastructure. It may be a process that is done automatically every time one comes up with a new set of keys. One of the different approaches one can take to do this is by taking every key one create and just back them up. That way, if one loses one of the keys, one can always go back and recover them from a place one has stored them safely.
If one is using a certificate authority, some of the recovery process is already built into it making the whole recovery process very difficult to implement. The key recovery process is an extremely important process if one are building out a certificate authority, one are creating an entire public key infrastructure for one's organization and it is something that one certainly want to look at.
Public key
The public key cryptography methodology is one that was founded by asymmetric encryption. The creation of public keys really involves a lot of mathematics and randomization. A lot of mathematics and prime numbers goes into this so as to create a public key that can be given to anyone in the world. By looking at a public and private key, it is very difficult for one to differentiate between the two.
Private Key
A private key is a kind of encryption key that cannot be shared with any other person. This means that one are the only one who maintains possession of such a key and one can only use it to decrypt information that has been encrypted using a public key
Registration
Key registration in one's public key infrastructure is the role that ensures that the right people are associated with the right keys. It is this registration process that ensures that one have exactly the right people lined up with exactly the right certificate. This process ensures that there is no type of mix-up or fraud with the certificates. The public key infrastructure registration process can either be done casually where it is done over the phone or it can also involve some very many procedures.
The key registration process is one that is very important and it requires one to be very detailed so as to ensure that the specific key is matched correctly with a specific end user.
Key escrow
Basically, when we are talking about escrow we are talking about a third party that is holding something for us. In the context of cryptography, this refers to the encryption keys. In this case, it requires that a third party stores the encryption key so that we can decrypt information in case the original key gets lost. In this case, the encryption key should be kept in a very safe place so that it is not accessed by others. Key escrow also helps when it comes to the recovery of data.
Symmetric encryption in the context of key escrow means that one are keeping one's key somewhere making sure that it is put in a safe so that no one can get access to it.
Asymmetrical encryption in this case means that one need to have an additional private key that one can use to decrypt information. The process of getting to the key escrow is as important as the key since so have to be aware of what circumstances can prompt one to get the key and who can access the key. Having the right process in place and one have the right ideas behind what one are doing with the key escrow, it then becomes a valuable part of maintaining the integrity and security of one's data.
Trust models
The most important aspect of one's public key infrastructure is that of trust. One has some assurance that the certificates one are using are those that one can trust. This means that the names associated with those certificates are the names associated with people who might be receiving those and might be decrypting the information one are sending to them.
Depending on the type of infrastructure one has and the way one has built one's public key infrastructure, there may be a number of different models that one use for trust. For instance, if one have a single certificate authority, one might find out that everyone is receiving all their certificates from one place and one can now trust that the one certificate authority is managing that process for everyone.
If one is in a large organization, one might need more than one certificate authority and therefore one may end up coming up with a hierarchical trust model. One can have a single root certificate authority server that is issuing certificates to intermediate servers which then issue certificates to leaf certificate authorities and then to one's end users and resources. This depends on one's organization since there could be some geographical requirements or structural requirements that would require that level of control and have the ability to spread trust from the very top root all the way down to other certificate authorities.
There is also another model called the mesh trust model relationship. In this case, every certificate authority trusts all of the other certificate authorities which works perfectly well in a case where one have two or three certificate authorities. Bringing in additional certificate authorities makes it difficult to scale the whole trust model.
Another trust model relationship is the mutual authentication where the server authenticates to the client and the client authenticates to the server and they both trust each other in the same amount.
Basically, the public key infrastructure and other components related to encryption and certificate are very important in cryptography. These are aspects whose working is quite inter-related and thus they are concepts that we must all be familiar with. So, one should know about them all so that he can be the master in this specific field and can improve his career.
Site Search:






