- Home
- Popular IT Certifications
- Overview of Malware and Its Types
Overview of Malware and its types
Malware is the type of virus which is specifically designed to destroy the data. It can come in various forms and hence it can perform many actions within the data and on it. For example it can completely destroy data, can send the data automatically to some other place, can alter the data or can keep monitoring it till the specified time period. It can come in many forms and one should take some appropriate steps to prevent that data destruction tool. There are numbers of software's now which are available in the market and they can be sued very effectively against these attacks. Following are some of the malware types which one might face in their computing machines;
Adware
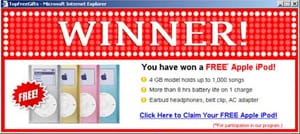
This software is basically the advertising supporting software. It is a package which comes automatically with the advertisements inside. Hence it can generate some good revenue for the owner and the author. These advertisements which are shown might be the software's user interface or they can even be the screen which would be presented to one while the installation is being done. The built in functions might be designed in some way so that they can analyse that which of the internet sites are being visits by one and this thing mostly leads to the unwanted advertisement displays and many people complaint about it. The software's which legitimated ones are, these functions of the advertising are integrated intentionally and they come with the bundle. It is usually also considered as the way in which developer can cover the cost of creating that software. These days, this term adware has been strongly associated with the malware to describe it as a form of it. It is basically something that shows the unwanted advertisements. The advertisement which are produced by the adware are sometimes also shown as the pop ups. When the term is called in such way, the severity may vary. So, one should use the pop blockers to protect himself from such malware.
Virus
The computer virus is the type of malware program which acts in interesting way. This program, which is executed, replicates itself by putting in some of the copies of itself in some other computer programs, boot sector, data files, hard disk etc. when the replication process is done, then the areas which are affected are said to be the infected ones. Normally, the viruses are built to perform some of the harmful activities on the hosts when they get infected. They can steal the CPU time or even the space at the hard disk. They can also corrupt the data and can put some funny messages on the screen of user. Their keystrokes can be recorded and even the contacts can be spammed as well. There is some miss-conception in the mind of many that viruses can only be used for destruction of data, but it is not the case. Actually everything which can replicate itself, and is designed to do so, is the cirrus. Hence one would install the anti-virus which can take care of this problem well.
Spyware
As the name implies, this software is basically used for the gathering of information about some organization or person. That information is gathered without anyone letting know that the information is being fathered from their system. This software's helps sending the information to some other entity which can gather the data about what one is doing and it is done without the consent. That's why, it is known as the spyware. It is mostly brought down in 4 types. One of them is the system monitors, other is the Trojans, tracking cookie and the fourth one is the adware. The common purpose, for which he spyware is used, is to track the movements of the internet users on the websites. They also serve some pop ups to the internet users.
Trojan
This malwares is actually the non-self-replicating one. It contains some malicious code which carries out some actions which are determined by the nature of that specific Trojan. That happens upon the execution only. The result of the action is normally the data lose. And it can also harm he system in some ways. This term, has been derived from the story of the troy. They used the wooden horse. The reason why Trojans are given this name is that they often take form of some social engineering and hence can present themselves as if they are so useful and are so interesting. Then they get themselves installed at the victim's computer by manipulating them.
Rootkits
The rootkits are typically malicious ones. They are the stealth type of the software. They are designed in some special way that they can actually hide themselves very well and it is pretty difficult to get them detected in the system. The normal methods of detection don't work on them. Hence they can have some continued access to the computer. When someone hears the word rootkit, it means that it is software which has some negative credibility and it should not be staying on the computer. The bad thing about this is that it can get installed on the computer automatically and the attacker doesn't need any permission for that. Once they have installed it into the system, they can get access to the root or the administrator access. This access is gained through the successful attack. Once it is installed, it becomes quite possible to hide this virus in the system and hence the privileged access can be maintained easily. Having the full fledge control over the system can result in the modification of software, hence, the software might also be used for the detection and that one can be altered as well. The worst thing I, that the rootkit is something difficult thing. The reason is, one might be able to change the rootkit and can get access to the software which is sued for the detection of that rootkit. Detection method which can contain the several techniques like the usage of some trusted OS, the dumping of the memory, the signature scanning etc. can be used. The removal of these rootkits can become pretty much difficult or partially possible. This specially happens in the time when the kernel is the host for those rootkits. So, if that happens, then the reinstalling of that specific OS is the only solution which can help one getting rid of the problem.
Backdoors
Backdoor, actually is the thing which enables the attacker to get passed through the authentication which is normal. Hence one can get some illegal access towards the computer. This can also result into the access to the plain texts. The backdoor may have many forms. One of them can be the form of some installed program. Hence it can also enter and can destroy the system in the form of rootkit. If the user doesn't change some of the default passwords, then it is quite possible that they can act as the function of the backdoors. Also, the debugging features which we use can also be used as the backdoors. The backdoor might take another form of the user which is hard coded. It can give some combination of it and the password which can give away some access towards the system. A famous example which has been used for this is the plot device which was used in the old movies. Another great thing is that one can create the backdoor even without getting the source code of the program changed. Also, it can get modified after it has been completed. This thing is actually done by re writing of that compiler. Hence, it can make the recognition of the code during the compiling which triggers the backdoor's inclusion in the output of compiling.
Logic bomb
This thing is basically some piece of the code which has been inserted into the software and the system intentionally. It can help setting off some malicious function. It is done when there are some specified conditions and they are met. Like, a programmer might like to hide some code piece which can start the deleting of files. Those files should never get out of the company's database. There are some of the software's which are actually malicious and it is in their genes. They can be the worms or the viruses. They get executed in this case, after some defined situations are put up there and hence they pop up. This method is actually used by some worm or the virus, which can get some maximum amount of the momentum and can spread really fast. Some attackers can make that attack on some specified date, like on the April 1st. so, the Trojans which can get activated at some dates which are already specified, are known as the time bombs. So one can install some anti-viruses which can enable one to not to get them installed and control the situation if it is going out of the hand. The best possible situation is to reformat the windows.
Botnets
The botnet is classically an internet program which is connected through internet and it can help one communicate with the other same type of programs so that some takes can be performed. They can be same as the keeping control of some IRC, which is the internet related charts. Also, it can be utilized for sending out some of the spam emails or to participate in some distribution of the denial of services attacks. Botnet is the word which is made up from the two words, the network and robot. This name is normally used with some negative or the malicious connotations.
Ransom ware
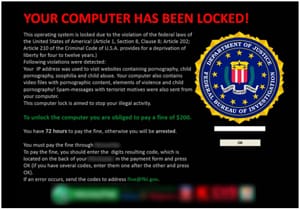
One might not like this malware. This is the malware which is used for some restricting the access to a computer system. That computer system is normally the infected one. As the name gives a hint, it requires some ransom which has to be paid to its creator so that the restriction can be removed and one can get the control of the computer back. Also, there are the forms of this programs which can encrypt the files which are on hard drive or some of them can end up with simply showing some message about payment of money to the one who has implemented this program.
Polymorphic malware
In the language of computer, the polymorphic code is the thing which uses the polymorphic engine. It helps mutating while maintaining real algorithm in intact. The code is changed itself whenever it is ran through, but, there is the thing that the function which is associated with it would not get changed. Like, the numbers 1+4 and 20-15 would be producing the same type of results but they would be using some different codes. Also, this is the technique which is used by the worms, shell codes and some viruses as well. So, protection from this is very important for a person.
Armoured virus
This is one type of the virus. There are many of the codes which are used it in and hence it becomes quite difficult to get it detected. There are many tricks that this virus has under its sleeves. One of them is that the virus can be located at some other location but it would act as if it is located at some other location. It makes it become somehow, difficult to get detected and get removed. Hence it works like some armour. That's why it is given name of the armoured virus. Protection against it can be pretty difficult so one might think about reinstallation of windows.
Hence, there are many of the malware types which can destroy the computer's system and the data. One must keep a close eye on any weird activity and should run and antivirus regularly so he can keep some check on the viruses. Also, if the worst case scenario is seen, one might consider some other alternatives too which can be the reinstallation of windows which can surely guarantee the complete removal of the all malwares and threats.
Site Search:






