- Home
- Popular IT Certifications
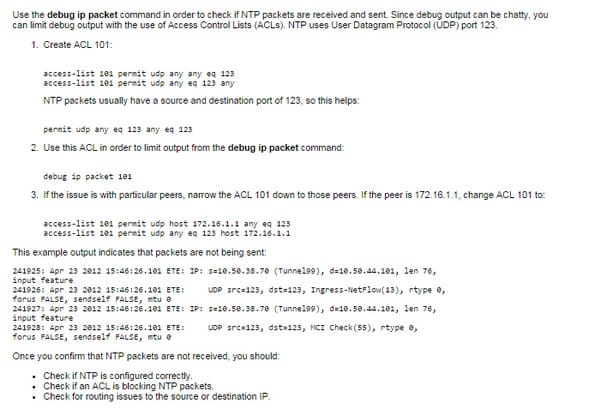
- Troubleshooting Network Time Protocol(NTP)
How to troubleshoot Network Time Protocol (NTP)
Is a systems administration convention for clock synchronization between machine frameworks over parcel exchanged, variable-idleness information systems. In operation since before 1985, NTP is one of the most seasoned Internet conventions being used. NTP was initially outlined by David L. Plants of the University of Delaware, who still creates and keeps up it with a group of volunteers.
NTP is planned to synchronize all taking an interest machines to inside a couple of milliseconds of Coordinated Universal Time (UTC). It utilizes an adjusted variant of Manzullo's calculation to choose exact time servers and is intended to relieve the impacts of variable system inertness. NTP can normally keep up time to inside several milliseconds over general society Internet, and can accomplish better than one millisecond precision in neighborhood under perfect conditions. Lopsided courses and system clogging can result in lapses of 100 mms or more.
The convention is typically portrayed regarding a customer server model, yet can as effortlessly be utilized as a part of shared connections where both companions consider the other to be a potential time source. Implementations send and get timestamps utilizing the User Datagram Protocol (UDP) on port number 123. They can likewise utilize television or multicasting, where customers latently listen to time upgrades after a beginning round-excursion aligning exchange. NTP supplies a cautioning of any looming jump second conformity, yet no data about nearby time zones or light sparing time is transmitted. NTP utilizes a various leveled, semi-layered arrangement of time sources. Each one level of this chain of command is termed a "stratum" and is allocated a number beginning with zero at the top. The number speaks to the separation from the reference clock and is utilized to avert cyclical conditions in the progression. Stratum is not generally a sign of value or unwavering quality; it is regular to discover stratum 3 time sources that are higher quality than other stratum 2 time sources. Telecom frameworks utilize an alternate definition for clock strata.
Stratum 0
These are high-exactness timekeeping gadgets, for example, nuclear (cesium, rubidium) clocks, GPS tickers or other radio timekeepers. They produce an exceptionally exact beat for every second flag that triggers a hinder and timestamp on an associated machine. Stratum 0 gadgets are otherwise called reference tickers.
Stratum 1
These are machines whose framework tickers are synchronized to inside a couple of microseconds of their joined stratum 0 gadgets. Stratum 1 servers may peer with other stratum 1 servers for rational soundness checking and backup. They are likewise alluded to as essential time servers.
Stratum 2
These are machines that are synchronized over a system to stratum 1 servers. Regularly a stratum 2 machine wills inquiry a few stratum 1 servers. Stratum 2 machines might likewise peer with other stratum 2 machines to give more steady and hearty time for all gadgets in the companion bunch.
Stratum 3
These are machines that are synchronized to stratum 2 servers. They utilize precisely the same calculations for peering and information inspecting as stratum 2, and can themselves go about as servers for stratum 4 machines, et cetera.
Just strata 0 to 15 are substantial; stratum 16 is utilized to demonstrate that a gadget is unsynchronized. The NTP calculations on every machine connect to build a Bellman-Ford most limited way spreading over tree, to minimize the aggregated round-excursion deferral to the stratum 1 servers for all the clients. The 64-bit timestamps utilized by NTP comprise of a 32-bit part for a considerable length of time and a 32-bit part for partial second, giving a period scale that moves over like clockwork (136 years) and a hypothetical determination of 2-32 seconds (233 picoseconds). NTP utilizes an age of January 1, 1900 so the first move over will be in 2036. Future forms of NTP may develop the time representation to 128 bits: 64 bits for the second and 64 bits for the fragmentary second. The current Ntpv4 design has help for Era Number and Era Offset, that when utilized appropriately ought to support altering date rollover issues. As per Mills, "the 64 bit esteem for the division is sufficient to purpose the measure of time it takes a photon to pass an electron at the velocity of light. The 64 bit second esteem is sufficient to give unambiguous time representation until the universe goes dim. The NTP reference usage, alongside the convention, has been persistently produced in excess of 20 years. Rearward similarity has been kept up as new gimmicks have been included. It contains a few touchy calculations, particularly to train the clock that can act up when synchronized to servers that utilize distinctive calculations. The product has been ported to practically every processing stage, including individual computers. It runs as a daemon called NTDP under UNIX or as an administration under Windows. Reference timekeepers are upheld and their counterbalances are separated and investigated in the same path as remote servers, despite the fact that they are normally surveyed more frequently. All Microsoft Windows renditions since Windows 2000 and Windows XP incorporate the Windows Time administration ("W32time"), which can synchronize the machine clock to a NTP server. The W32time administration was initially executed with the end goal of the Kerberos adaptation 5 validation conventions, which obliged time to be inside not more than 5 minutes of the right esteem. The rendition in Windows 2000 and Windows XP just executes Simple NTP, and disregards a few parts of the NTP form 3 standard. Beginning with Windows Server 2003 and Windows Vista, a consistent execution of full NTP is included. Microsoft says that the W32time administration can't dependably keep up sync time to the scope of 1 to 2 seconds. If higher precision is craved, Microsoft prescribes to utilize an alternate NTP implementation. On the day of a jump second occasion, NTDP gets notice from either a design record, an appended reference clock or a remote server. In spite of the fact that the clock is really ended amid the occasion, any courses of action that question the framework time
cause it to increment by a small sum, saving the request of occasions. On the off chance that it ought to ever get to be important, a jump second would be erased. NTP servers are helpless to man-in-the-center assaults unless bundles are cryptographically marked for validation. The computational overhead included can make this unrealistic on occupied servers, especially amid dissent of administration attacks. Just a couple of security issues have been recognized in the reference usage of the NTP codebase in its 25+ year history. The convention has been experiencing amendment and survey over its whole history. As of January 2011, there are no security corrections in the NTP detail and no reports at Cert. The current codebase for the reference execution has been experiencing security reviews from a few hotspots for a few years now, and there are no known high-hazard vulnerabilities in the current discharged software. A few NTP server abuse and ill-use practices exist which cause harm or corruption to a Network Time Protocol (NTP) server. NTP has been utilized as a part of disseminated disavowal of administration (DDOS) attacks. A little inquiry is sent to a NTP server with the return location parodied to be the target address. Like the DNS enhancement assault, the server reacts with a much bigger answer that permits an aggressor to considerably expand the measure of information being sent to the target. To abstain from taking an interest in an assault, servers might be arranged to disregard outside questions, or they could be moved up to form 4.2.7p26 or later.
How to troubleshoot NTP:
This is how it's done;
NTP master, client, version 3, version 4
Here is how NPT master is configured;
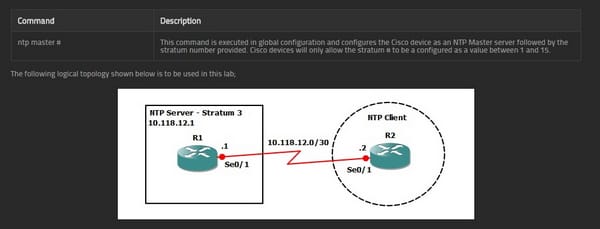
And here is how NTP client is configured;
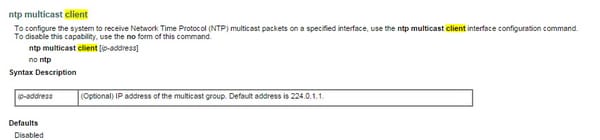
Version 3 supersedes the Version 2 of the convention portrayed in RFC-1119 dated September 1989. Then again, it not one or the other changes the convention in any noteworthy way nor obsoletes past renditions or existing usage. The fundamental inspiration for the new form is to refine the investigation and usage models for new applications at much higher system paces to the gigabit-for every second administration and to give for the upgraded steadiness, precision and accuracy needed at such speeds. Specifically, the wellsprings of time and recurrence lapses have been thoroughly analyzed and lapse limits made with a specific end goal to enhance execution, give a model to accuracy attestations and show timekeeping quality to the client. The update additionally consolidates two new discretionary peculiarities, (1) a calculation to join the balances of a number of companion time servers with a specific end goal to improve exactness and (2) enhanced nearby clock calculations which permit the survey interims on all synchronization ways to be significantly expanded with a specific end goal to decrease system overhead.in Version 3 The nearby clock calculation has been updated to progress solidness and exactness. Supplement G shows an itemized scientific model and configuration illustration which has been refined with the help of input control dissection and far reaching recreation utilizing information gathered over standard Internet ways. Segment 5 of RFC-1119 on the NTP neighborhood clock has been totally revised to portray the new calculation. Since the new calculation can bring about message rates far underneath the old ones, it's profoundly prescribed that they be utilized as a part of new usage. Note that utilization of the new calculation does not influence interoperability with past adaptations or existing usage.
The Ntpv4 outline overcomes huge deficiencies in the Ntpv3 outline, adjusts certain bugs, and consolidates new peculiarities. In specific, stretched NTP timestamp definitions empower the utilization of the skimming twofold information sort all through the execution. As a result, the time determination is superior to one nanosecond, and recurrence determination is short of what one nanosecond for every second. Extra changes incorporate another clock discipline calculation that is more receptive to framework clock fittings recurrence vacillations. Ordinary essential servers utilizing current machines are exact inside a few many microseconds. Ordinary optional servers and customers on quick LANS are inside a couple of hundred microseconds with survey interims up to 1024 seconds, which was the greatest with Ntpv3. With Ntpv4, servers and customers are exact inside a couple of many milliseconds with survey interims up to 36 hours. A NTP usage works as an essential server, auxiliary server, then again customer. An essential server is synchronized to a reference clock specifically traceable to UTC (e.g., GPS, Galileo, and so on.). A customer synchronizes to one or all the more upstream servers, yet does not give synchronization to ward customers. An optional server has one or all the more upstream servers and one or all the more downstream servers or customers. All servers and customers who are completely Ntpv4-agreeable MUST actualize the whole suite of calculations portrayed in this archive. In place to keep up dependability in substantial NTP subnets, optional servers SHOULD be completely Ntpv4-agreeable. Elective calculations MAY be utilized, yet their yield MUST be indistinguishable to the calculations portrayed in this particular. There are three NTP convention variations: symmetric, customer/server, and telecast. Each is connected with an affiliation mode (a depiction of the relationship between two NTP speakers) as appeared
NTP authentication
A typical misguided judgment about NTP validation is the bearing in which verification happens, on the other hand it bodes well on the off chance that you make this inquiry: what is the reason for utilizing NTP confirmation? One acceptable answer is that validation is utilized to avoid messing with the timestamps on the logs produced by gadgets. To execute an assault on NTP, a programmer would make their rebel host give off an impression of being a legitimate NTP server. NTP verification is accordingly used to verify the time source, not the customer.
So NTP is the very important part of the networking system. So, those people who want to establish a good career in the field of networking must ensure that they learn about NTP so they can apply this knowledge into the practical field.
Site Search:






