- Home
- Popular IT Certifications
- How to Troubleshoot Logging Issues
Describe the process of troubleshooting logging issues
You can point out to send client log data to different customers or Log Targets and define whether the log messages are put away by regional standards in content arrangement or sent to syslog servers. Naturally, a solitary predefined neighborhood Log Target called Local Store stores information in content arrangement on an ACS server and contains log messages from the nearby ACS server just. You can view records put away in the Local Store from the CLI.
Likewise, you can define that logs be sent to a syslog server. ACS utilizes syslog transport to forward logs to the Monitoring and Reports segment. You can likewise characterize extra syslog servers to get ACS log messages. For every extra syslog server you point out, you must characterize a remote log target. In a dispersed arrangement, you ought to assign one of the auxiliary ACS servers as the Monitoring and Reports server, and point out that it gets the logs from all servers in the organization. Naturally, a Log Target called the Log collector distinguishes the Monitoring and Reports server. In situations where a dispersed sending is utilized, the Log Collector alternative on the web interface assigns which server gathers the log data. It is suggested that you assign an auxiliary server inside the arrangement to go about as the Monitoring and Reports server. Each log is connected with a message code that is packaged with the logging classes as per the log message content. Logging classes help depict the substance of the messages that they contain.
A logging classification is a heap of message codes which portray a capacity of ACS, a stream, or a utilization case. The classes are masterminded in a progressive structure and utilized for logging arrangement. Every class has:
- Name: An engaging name
- Type: Audit, Accounting, or Diagnostics
- Attributes List: A rundown of qualities that may be logged with messages connected with a class, if pertinent
ACS gives these preconfigured worldwide ACS logging classifications, to which you can appoint log targets (see Local Store Target): Administrative and Operational review, which can include:
ACS setup progressions Logs all arrangement changes made to ACS. At the point when an in thing is included or altered, the setup change occasions likewise incorporate subtle elements of the traits that were changed and their new values. In the event that an alter appeal brought about no properties having new values, no setup review record is created. The log messages could be contained in the logging classifications as depicted in this theme, or they might be contained in the logging subcategories. You can arrange each one logging subcategory independently, and its setup does not influence the guardian classification. In the ACS web interface, pick System Administration > Configuration > Logging Categories > Global to view the various leveled structure of the logging classes and subcategories. In the web interface, pick Monitoring and Reports > Catalog to run reports focused around your arranged logging classifications.
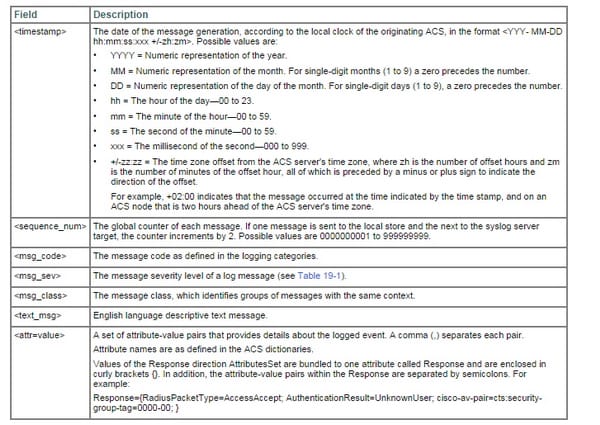
Each one log message contains the accompanying data:
- Event code-an exceptional message code.
- Logging classification identifies the class to which a log message has a place.
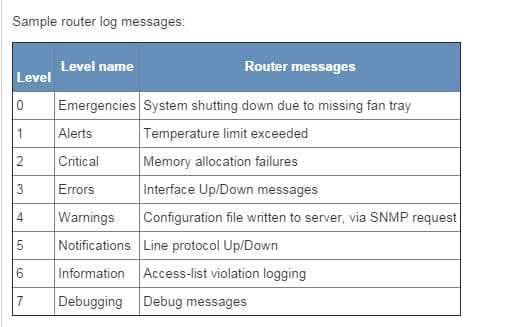
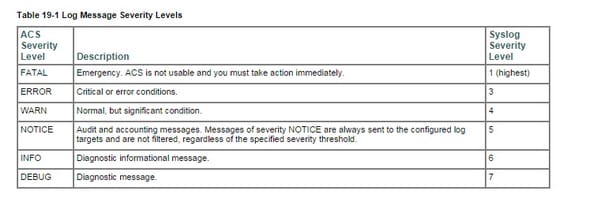
- Severity level-identifies the level of seriousness for diagnostics. See Log Message Severity Levels for more data.
- Message class-Identifies gatherings of messages of comparative connection, for instance, RADIUS, strategy, or EAP-related setting.
- Message content Brief English dialect logical content.
- Description-English dialect message that portrays log message reasons, troubleshooting data (if pertinent), and outer connections for more data.
- Failure reason (discretionary)-Indicates whether a log message is connected with a disappointment reason.by default, a solitary log classification design applies to all servers in an organization. For each one log classification, the limit seriousness of messages to be logged, whether messages are to be logged to the nearby target, and the remote syslog focuses to which the messages are to be sent to, are characterized.
The log classes are sorted out in a progressive structure so that any setup transforms you make to a guardian classification are connected to all the youngster classifications. Be that as it may, the chairman can apply distinctive arrangements to the individual servers in a sending. For instance, you can apply more serious symptomatic logging on one server in the sending. For every occurrence logging class design shows all servers in an arrangement and demonstrates whether they are designed to use the worldwide logging setup or have their custom arrangement. To characterize a custom setup for a server, you should first select the Override alternative, and after that arrange the particular log class definitions for that server. You can utilize the Log Message Catalog to show all conceivable log messages that could be created, each with its relating class and seriousness. This data might be helpful when arranging the logging class definitions. You can design logs of a certain seriousness level, and higher, to be logged for a particular logging classification and include this as an arrangement component as far as possible or extend the quantity of messages that you need to spare, view, and fare. For instance, in the event that you arrange logs of seriousness level WARNING to be logged for a particular logging classification, log messages for that logging class of seriousness level WARNING and those of a higher need levels (ERROR and FATAL) are sent to any arranged areas.
Local logging, syslog, debugs conditional debugs
Log messages in the nearby store are content documents that are sent to one log record, paying little respect to which logging classification they fit in with. The nearby store can just contain log messages from the neighborhood ACS hub; the nearby store can't acknowledge log messages from different ACS hubs.
You can arrange which logs are sent to the nearby store, yet you can't design which qualities are sent with the log messages; all characteristics are sent with sent log messages. Authoritative and operational review log messages are constantly sent to the nearby store, and you can likewise send them to remote syslog server and Monitoring and Reports server targets. You can utilize the web interface to design the quantity of days to hold neighborhood store log records; then again, the default setting is to cleanse information when it surpasses 5 MB or every day, whichever breaking point is initially accomplished. On the off chance that you do design more than one day to hold nearby store documents and the information size of the joined records achieves 95000mb, a FATAL message is sent to the framework symptomatic log, and all logging to the neighborhood store is ceased until information is cleansed. Utilize the web interface to cleanse neighborhood store log records. Cleansing activities are logged to the present, dynamic log record. The neighborhood store target can work as a discriminating log focus on the essential, or required, log focus for a logging class. For instance, regulatory and operational review messages are constantly logged to the neighborhood store; however you can likewise design them to be logged to a remote syslog server or the Monitoring and Reports server log target. Be that as it may, regulatory and operational review messages designed to be furthermore logged to a remote log target are just logged to that remote log target in the event that they are initially logged effectively to the neighborhood log target.
Syslog:
It is a standard for machine message logging. It allows partition of the product that produces messages from the framework that stores them and the product that reports and dissects them.
Syslog might be utilized for machine framework administration and security reviewing and in addition summed up instructive, examination, and debugging messages. It is upheld by a wide assortment of gadgets (like printers and switches) and recipients crosswise over various stages. As a result of this, syslog might be utilized to coordinate log information from numerous diverse sorts of frameworks into a focal vault. Messages are named with an office code demonstrating the sort of programming that produced the messages, and are appointed seriousness (one of: Emergency, Alert, Critical, Error, Warning, Notice, Info, and Debug). Executions are accessible for some working frameworks. Most executions additionally give a charge line utility, regularly called lumberjack that can send messages to the syslog. A few usages allow the separating and presentation of syslog messages. Various gatherings are chipping away at draft benchmarks specifying the utilization of syslog for more than simply system and security occasion logging, for example, its proposed application inside the health the earth.
Regulations, for example, SOX, PCI, HIPAA, and numerous others are obliging associations to actualize thorough efforts to establish safety, which regularly incorporate gathering and investigating logs from numerous distinctive sources. Syslog has turned out to be a viable configuration to merge logs, as there are numerous open source and exclusive devices for reporting and examination. Converters exist from Windows Event Log and in addition other log organizations to syslog. A developing territory of oversaw security administrations is the accumulation and investigation of syslog records for associations. Organizations calling themselves Managed Security Service Providers endeavor to apply examination systems (and in some cases counterfeit consciousness calculations) to locate examples and alarm clients to issues.
Debugs:
It is a charge in DOS, OS/2 and Microsoft Windows (just in 32bit) which runs the system debug.exe (or Debug.com in more seasoned adaptations of Dos). Debug can go about as a constructing agent, disassembler, or hex dump project permitting clients to intuitively inspect memory substance (in low level computing construct, hexadecimal or ASCII), roll out improvements, and specifically execute COM, EXE and other record sorts. It additionally has a few subcommands which are utilized to get to particular circle segments, I/O ports and memory addresses. Traditionally, all machines and working frameworks have incorporated and upkeep capacity, used to figure out if a project is working correctly. Debug was composed by Tim Paterson to fill this need in QDOS. At the point when Paterson started working for Microsoft in the early 1980s he brought the project with him. Debug was some piece of DOS 1.00 and has been incorporated in MS-DOS and Microsoft Windows.
Conditional Debugs:
This is how the conditional debug is configured;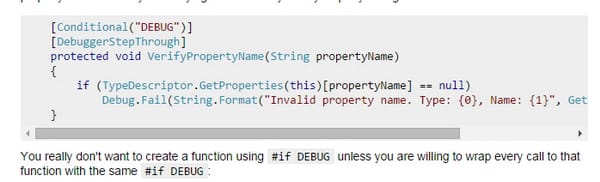
Timestamps
A timestamp is a succession of characters or encoded data distinguishing when a certain occasion happened, generally giving date and time of day, once in a while exact to a little division of a second. The term determines from elastic stamps utilized within business locales to stamp the current date, and off and on again time, in ink on paper archives, to record when the archive was received. Common cases of this sort of timestamp are a stamp on a letter or the "in" and "out" times on a period card. Nonetheless, in present day times utilization of the term has stretched to allude to computerized date and time data connected to advanced information. For instance, machine records contain timestamps that tell when the document was last altered, and advanced cams add timestamps to the pictures they take, recording the date and time the picture was taken. A timestamp is the time at which an occasion is recorded by a machine, not the time of the occasion itself. By and large, the distinction may be irrelevant: the time at which an occasion is recorded by a timestamp (e.g., entered into a log document) ought to be near the time of the event. This information is typically exhibited in a predictable arrangement, considering simple examination of two separate records and following advancement about whether; the act of recording timestamps in a steady way alongside the genuine information is called time stamping. The consecutive numbering of occasions is now and then called time stamping. The timestamps are regularly utilized for logging occasions or as a part of an arrangement of occasions (SOE), in which case every occasion in the log or SOE is stamped with a timestamp. In file systems, timestamp may mean the put away date/time of creation or alteration of a document.
Debugging, Time stamps and the loggings are the common terms in the networking so those who want to opt for a future in the field of networking, should make sure that they learn about them, so that they can make good progress in the field.
Site Search:






