- Home
- Popular IT Certifications
- Troubleshooting for IPv4 (NAT) Issues
Describe troubleshoot for IPv4 Network Address Translation (NAT)
IPv4 is the fourth form in the advancement of the Internet Protocol (IP) Internet, and courses most movement on the Internet. However, a successor protocol, IPv6, has been characterized and is in different phases of generation arrangement.
IPv4 is a connectionless protocol for utilization on parcel exchanged systems. It works on a best exertion conveyance model, in that it doesn't promise conveyance, nor does it guarantee fitting sequencing or shirking of copy conveyance. These perspectives, including information trustworthiness, are tended to by an upper layer transport protocol, for example, the TCP.
Originally, an IP location was partitioned into two sections: the system identifier was the most critical (most elevated request) octet of the location, and the host identifier was whatever remains of the location. The last was thusly additionally called the rest field. This empowered the formation of a most extreme of 256 systems. This was rapidly discovered to be lacking. To beat this breaking point, the high request octet of the locations was reclassified to make a set of classes of systems, in a framework which later got to be known as systems administration. The framework characterized five classes, Class A, B, C, D, and E. The Classes A, B, and C had distinctive bit lengths for the new system recognizable proof. Whatever remains of a location was utilized as long ago to distinguish a host inside a system, which implied that each one system class had an alternate ability to address has. Class D was allotted for multicast tending to and Class E was held for future applications. Beginning around 1985, systems were contrived to subdivide IP systems. One technique that has demonstrated adaptable is the utilization of the VLSM.
Taking into account the IETF standard RFC 1517 distributed in 1993, this arrangement of classes was formally supplanted with Classless Inter-Domain Routing (CIDR), which communicated the quantity of bits (from the most noteworthy) as, case in point, /24, and the class-based plan was named, by complexity. CIDR was intended to allow repartitioning of any location space so that more modest or bigger pieces of locations could be assigned to clients. The progressive structure made by CIDR is overseen by the Internet Assigned Numbers Authority (IANA) and the territorial Internet registries (RIRS). Every RIR keeps up a freely searchable WHOIS database that gives data about IP address assignments. Packets with a private end location are disregarded by all open switches. Two private systems (e.g., two extension business locales) can't convey through people in general web, unless they utilize an IP passage or a virtual private system (VPN). At the point when one private system needs to send a bundle to an alternate private system, the first private system typifies the parcel in a protocol layer so that the parcel can go through the general population system. At that point the bundle goes through general society system. At the point when the parcel achieves the other private system, its protocol layer is uprooted, and the bundle ventures out to its goal. Alternatively, epitomized bundles may be scrambled to secure the information while it goes over general society system.
In computer systems administration, system address interpretation (NAT) gives a method of changing system address data in Internet Protocol (IP) datagram parcel headers while they are in travel over a movement routing gadget with the end goal of remapping one IP location space into an alternate. The term NAT44 is once in a while used to all the more particularly show mapping between two IPv4 addresses; this is the ordinary case while IPv4 conveys the greater part of activity on the Internet. NAT64 alludes to the mapping of an IPv4 location to an IPv6 location, or the other way around. System executives initially utilized system address interpretation to guide each location of one location space to a relating address in an alternate space, for example, when an association changed Internet administration suppliers without having an office to report an open course to the network. Starting 2014 NAT works most usually in conjunction with IP disguising, which is a system that conceals a whole IP location space - generally comprising of private system IP addresses (RFC 1918) - behind a solitary IP address in an alternate, normally open location space. Merchants execute this component in a routing gadget that uses static interpretation tables to guide the "shrouded" addresses into a solitary IP location and that readdresses the friendly Internet Protocol bundles on passageway so they seem to start from the routing gadget. In the converse interchanges way, the switch maps reactions over to the starting IP locations utilizing the tenets ("state") put away in the interpretation tables. The interpretation table principles made in this manner are flushed after a brief time unless new movement revives their state.
The strategy empowers correspondence through the switch just when the discussion begins in the disguised system, since this makes the interpretation tables. Case in point, a web program in the disguised system can peruse a site outside, however a web program outside cannot search a site facilitated inside the disguised network. Be that as it may, most NAT gadgets today permit the system director to arrange interpretation table entrances for lasting utilization. This gimmick is regularly alluded to as "static NAT" or port sending - it permits movement starting in the "outside" system to achieve assigned has in the disguised system. In view of the prevalence of this procedure to moderate IPv4 location space, the term NAT has gotten to be practically synonymous with the technique for IP disguising. As system location interpretation alters the IP address data in bundles, it has genuine outcomes on the Nature of Internet integration and requires cautious regard for the subtle elements of its usage. NAT executions shift generally in their particular conduct in different tending to cases and in their impact on system activity. Merchants of supplies containing executions don't ordinarily report the specifics of NAT behavior. The most straightforward kind of NAT gives a balanced interpretation of IP locations. RFC 2663 alludes to this sort of NAT as essential NAT; it is regularly likewise called a balanced NAT. In this kind of NAT, just the IP addresses, IP header checksum and any larger amount checksums that incorporate the IP location are changed. Essential NATs could be utilized to interconnect two IP arranges that have inconsistent tending to.
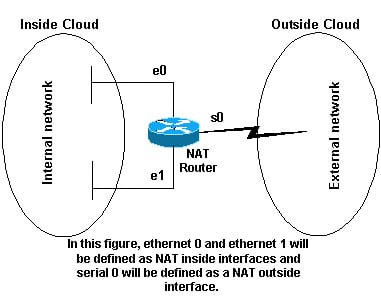
It is regular to shroud a whole IP location space, typically comprising of private IP addresses, behind a solitary IP address in an alternate, normally open, location space. To stay away from uncertainty in the treatment of returned parcels, a one-to-numerous NAT must change extra data, for example, TCP/UDP port numbers in friendly interchanges and must keep up an interpretation table so that return bundles might be accurately tended to the starting host. RFC 2663 uses the term system address and port interpretation (NAPT) for this sort of NAT. Different names incorporate port location interpretation (PAT), IP disguising, NAT over-burden and a lot of people to-one NAT. This is the most widely recognized sort of NAT, and has gotten to be synonymous with the term NAT in as something to be shared use. As depicted, the system empowers correspondence through the switch just when the discussion begins in the disguised system, since this makes the interpretation tables. For instance, a web program in the disguised system can search a site outside, however a web program outside couldn't scan a site facilitated inside the disguised system. On the other hand, most NAT gadgets today permit the system head to design interpretation table sections for perpetual utilization. This peculiarity is regularly alluded to as "static NAT" or port sending and permits movement beginning in the "outside" system to achieve assigned has in the disguised system.
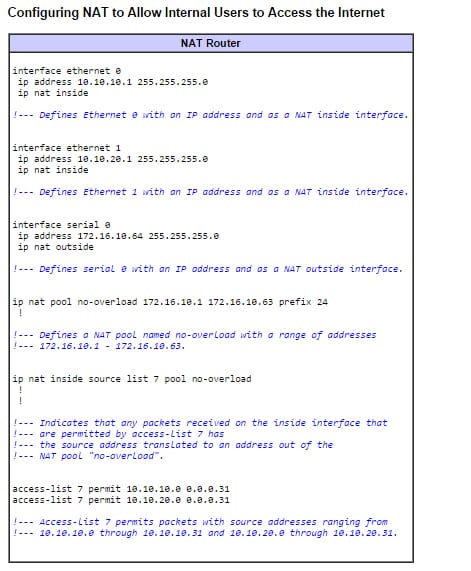
Configuring NAT:
This is how it's done;
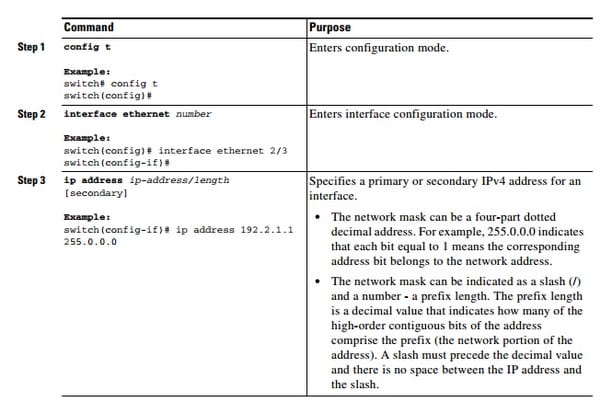
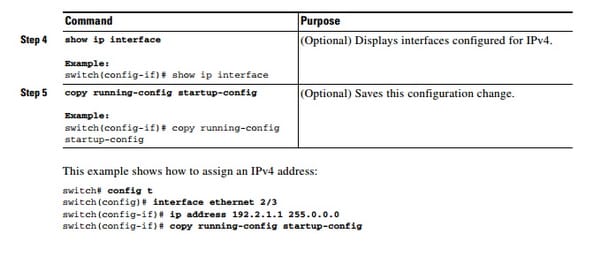
Configuring IPv4:
This is how it's done;
Static NAT, Dynamic NAT, PAT:
Here is the information about them;
Static NAT:
It is sort of NAT in which a private IP location is mapped to an open IP address, where general society location is dependably the same IP address (i.e., it has a static location). This permits an inside host, for example, a Web server, to have an unregistered (private) IP address and still be reachable over the Internet. Static NAT makes an altered interpretation of genuine address to mapped address with dynamic NAT and PAT; each one host utilizes an alternate address or port for every ensuing interpretation. Since the mapped location is the same for every back to back association with static NAT, and a relentless interpretation guideline exists, static NAT permits has on the objective system to launch movement to an interpreted host (if a right to gain entrance rundown exists that permits it). The fundamental distinction between dynamic NAT and a scope of locations for static NAT is that static NAT permits a remote host to start an association with an interpreted host (if a right to gain entrance rundown exists that permits it), while dynamic NAT does not. You likewise require an equivalent number of mapped addresses as genuine locations with static NAT.
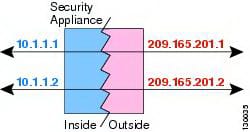
Dynamic NAT:
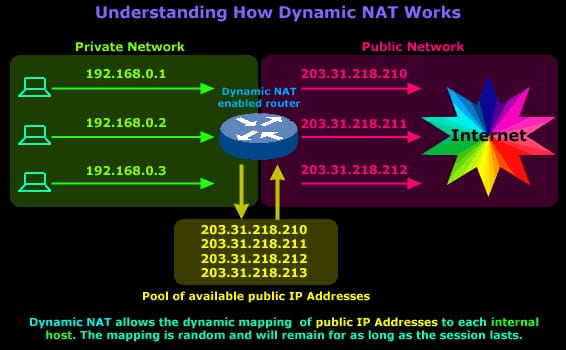
It is sort of NAT in which a private IP location is mapped to an open IP location drawing from a pool of enrolled (open) IP addresses. Normally, the NAT switch in a system will keep a table of enlisted IP addresses, and when a private IP location solicitations access to the Internet, the switch picks an IP address from the table that is not at the time being utilized by an alternate private IP address. Dynamic NAT serves to secure a system as it covers the inward design of a private system and makes it troublesome for somebody outside the system to screen singular utilization designs. An alternate playing point of element NAT is that it permits a private system to utilize private IP addresses that are invalid on the Internet however helpful as inward addresses. Dynamic NAT is the second NAT mode we're going to discuss. Dynamic NAT, in the same way as Static NAT, is not that normal in more modest systems however you'll think that it utilized inside bigger enterprises with complex systems. The way Dynamic NAT separates from Static NAT is that where Static NAT gives a coordinated inside to open static IP mapping, Dynamic NAT does likewise yet without making the mapping to people in general IP static and normally utilizes a gathering of accessible open IPs. While taking a gander at Static NAT, we comprehended that for each private IP Address that needs get to the Internet we would oblige one static open IP Address. This open IP Address is mapped to our inward host's IP Address and it is then ready to speak with whatever remains of the world. With Dynamic NAT, we additionally outline inner IP Addresses to genuine open IP Addresses, however the mapping is not static, implying that for every session our interior hosts speak with the Internet, their open IP Addresses continue as before, yet are liable to change. This IPs is taken from a pool of open IP Addresses that have been saved by our ISP for our open system. With Dynamic NAT, interpretations don't exist in the NAT table until the switch gets activity that obliges interpretation. Dynamic interpretations have a timeout period after which they are cleansed from the interpretation table, subsequently making them accessible for other inside hosts. The outline underneath represents the way Dynamic NAT lives up to expectations:
PAT:
It is an expansion to system address interpretation (NAT) that allows different gadgets on a neighborhood (LAN) to be mapped to a solitary open IP address. The objective of PAT is to moderate IP addresses. Home clients exploit PAT to keep their short of what secure machines from being totally assumed control once a day. At the point when an association endeavor from the outside hits the outer interface of a PAT gadget, it can't be sent unless state exists. State setup must be carried out from within, when a departure endeavor is made. In the event that this form of NAT didn't exist on such a wide scale, the Internet would be a totally better place. No one would ever effectively introduce and patch a Windows machine before a bargain without some the negligible insurance gave by PAT.
NAT, PAT and IPv4 are the very important parts of networking. So, one who is seeking a good future in networking must know about them so that he can implement the usage to the work.
Site Search:






