- Home
- Popular IT Certifications
- SLA Architecture; Configure & Verify IP SLA
Describe SLA architecture and how to configure and verify IP SLA
The SLA is a feature of a Cisco IOS that allows the IT professionals to collect information about the performance of network in the real time. The Cisco IOS IP SLA will continuously collect the data about the things like latency, packet loss, jitter and response time. It is not only offers a network administrator with the baseline information on the performance of the network, it helps the administrators to verify the quality of service levels as well as quickly identify the root of the problem, if the performance level drop. When integrated with the network management system, the visual alerts of the threshold violations can also be captured in the real time. In the coming section, let us see SLA architecture and how to configure and verify the IP SLA. The providers and customers can use the top level SLA to monitor their real service delivery complies with an agreed SLA terms.
6.8 Describe SLA architecture
The SLA stands for service level agreement. It is the part of the service contract where the service is formally defined. The service level management is defined at different levels, such as service based SLA, customer based SLA, and multilevel SLA. The SLA again split into various levels, such as service level SLA, customer level SLA and corporate level SLA.
The IOS IP service level agreement enables the customer to assure the new business critical application and IP service that utilize the video, voice and data in the IP network. The service level agreement is output based and the result of the service is also received by the customer who is subjected to agreement. The SLA commonly includes the segment to address such as performance measurement, customer duties, termination of agreement, warranties, definition of services, disaster recovery, and customer duties. To assure that the LSA are meeting these agreements are proposed with the certain lines of the demarcation and the parties involved are needed to meet regularly open form of communication. The IP SLA sends the data across a network to measure the performance between the multiple network locations or else across multiple network paths. Then it also stimulates the network data as well as IP services and also collects the information about the network performance in the actual time. The IP SLA generates as well as analyze the traffic either between the devices or from a device to the remote IP device including network application server. The measurement offered by various IP SLA operations can also be used for problem analysis, for designing network topologies and for troubleshooting. Based on the certain IP SLA operation, different network performance statistics are monitored within the device and also stored in both CLI- command line interface as well as SNMp MIB. As IP SLA is the layer 2 transport independent, you can also configure the end to end operations over the disparate network to reflect the metric which an end user is wanting to experience.
The IP SLA provides different variety of features which are related to different operations and several additional functions, including VRF support and multiple operation scheduling. The IP SLA is the embedded feature in a network element, hence it competes with the other process for the system resources like memory, CPU, ACL. Packet forwarding, queuing, and much more.
The service level agreement is the formal negotiated agreement between the 2 parties specifying the service characteristics. It records the most common understanding about the priorities, guarantee, responsibilities, service and much more to the purpose to agree on the service levels.
Given below is the SLA architecture:
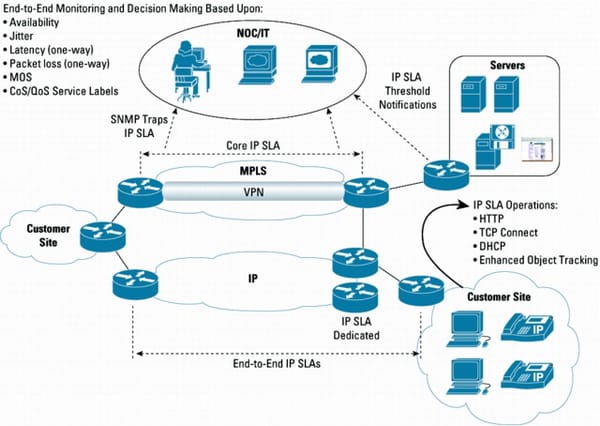
The IP SLA has evolved with the advanced measurement features such as multiprotocol label switching awareness, enhanced voice measurements and application performance. It can also be used throughout the life cycle of SLA as the tool to quantify a network performance in the different stages to get both proactive and reactive approach in meeting the requirements of the SLA. The operations of the IP SLA are sometimes referred as a probes, but not to be confused with the software or hardware packet capture application such as hardware based sniffers, or ethereal or tcpdump which is also referred as probes. The packet capture will work in the promiscuous mode and the packet capture application actively listens as well as capture packets in a wire. The netwflow is the technology which allows the devices to send packet passes to the netflow collector applications. Both the netflow collectors and packet capture are the passive probes. It captures the real network traffic passes to the base analysis. The IP SLA operation is based on the active probes and synthetic networks are generated for the purpose of mainly measure the network performance characteristics of the defined operations. Using the mechanism of active probe with the synthetic network traffic, the IP SLA has greater flexibility.
The IP SLA design based on the deployment primary goal. The possible goal can be to monitor the network health, an increase uptime, or to monitor and deploy the application. Few aspects will influence the design such as IP SLA operations, software choices and hardware, network management applications and performance metrics.
The IP SLA collects the below performance metrics as follows:
- Jitter
- Path
- Delay
- Packet sequencing
- Voice quality scores such as ICPIF, MOS
- Connectivity (mostly one way)
- Packet corruption detection
- Packet loss
- HTTP website download time or FTP server
Because of the distinct areas of architecture and operation, the netflow technologies and IP SLA complement each other and the IP SLAs are more suited for the performance measurement, but the netflow is geared more toward accounting. Advantages of IP SLA are as follows:
1. Historical data storage
2. Near millisecond precision
3. Comprehensive support of hardware makes it as the very cost scalable solution, since it will never need probes.
4. Proactive notification by using the SNMP traps based on the trigger or threshold of the other IP SLA operation.
5.
The IP SLA can be implemented in the any CISCO IOS device- software which supports the operation. A deployment can also be done in 3 different ways, such as composite SLA partial mesh and full mesh. Implementing some of the design and features of the IP SLA will improve the accuracy of the IP SLA measurements.
IP SLA responder:
The IP SLA responder is the IOS software which responds to the SLA request packet. An IP SLA source can send the control packets before an operation starts to accomplish the responder connection. When the control packets are acknowledged, then the test packet is sent to a responder. A responder inserts the time stamp while it receives the packets and factors out a destination processing time and also adds the time stamps to a sent packet. That feature allows a calculation of the unidirectional latency, jitter and packet loss measurements with a kind of accuracy which is not possible with the ping or the other dedicated probe testing. The responder is supported in the UDP echo, TCP connect operations and UDP jitter. The operations of MPLS VRF aware are supported in the ICMP echo, UDP echo, ICMP path jitter operation, ICMP path echo and ICMP echo.
Time synchronization:
A system clock accuracy affects an accuracy of a resulting metric. It is important for the IP SLA operation such as one way latency delay to have the precise time synchronization. In that, some operations also interarrival time and round trip, are very less sensitive to the clock variation.
Shadow router:
The dedicated router is used as the IP SLA measurement source also called as shadow router. This shadow router includes many advantages of implementing the IP SLA.
Granting the SNMP access of read and write to a device cannot be like a big security risk when compared to enabling the SNMP read and write on the production router that carries the customer traffic. The dedicated router may offset a resource load on the production router from an implemented SLA operation of network management. The dedicated router can be the central device which may be managed independently without any impact on the network traffic.
6.9 Configure and verify IP SLA
The IP SLAis especially used for the wide area networks that connects the multiple geographies as well as required to be monitored from the one central location.
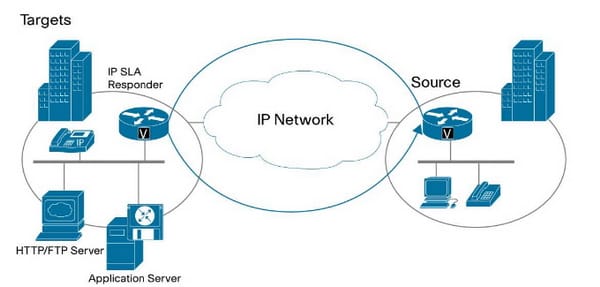
The IP SLA consist of 2 components such as source and target router. The source is where the IP SLA operation is defined. Depends on the parameter of configuration, a source generator packets particular to a defined IP SLA operation and analyze the record and the results so that it may be accessed via SNMP or CLI. The source router may be any router which can support an IP SLA being configured. An IP SLA target based on the IP SLA type operation. For the HTTP/FTP operation, a target can be HTTP or FTP server. For the routing table and UDP jitter, a target should be a device with a responder feature enabled, however, both the target and source participate in the measurement performance. An IP SLA responder can also be added benefit of accuracy, since it inserts out/in time stamps in a payload of packets and hence measures the CPU time which is sent. An IP SLA responder may be enabled with a configuration command as follows: ip sla responder.
Example configuration of IP SLA:
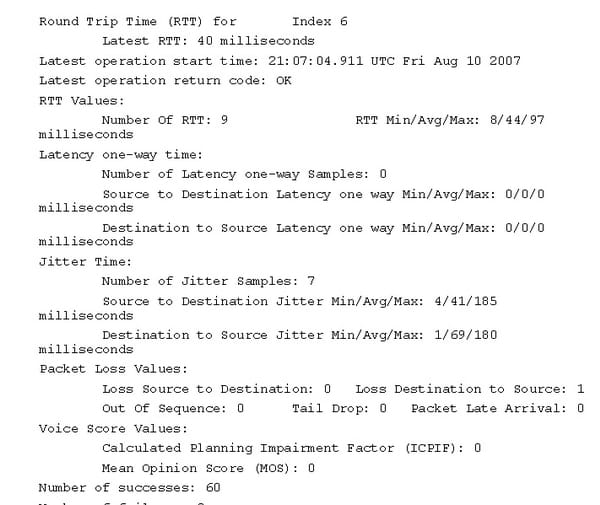
Step 1: UDP jitter operation
Source router as follows:
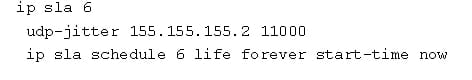
Destinator router as follows:
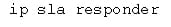

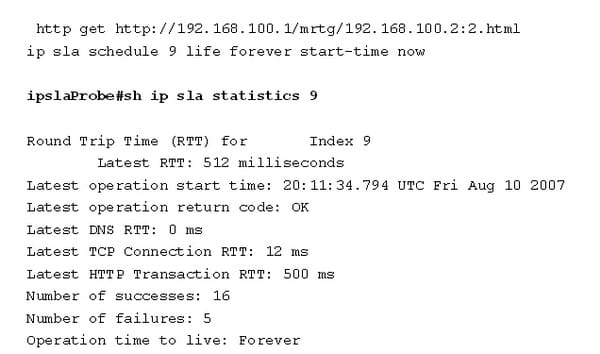
TCP operation:
Source router as follows:
Ip sla 9
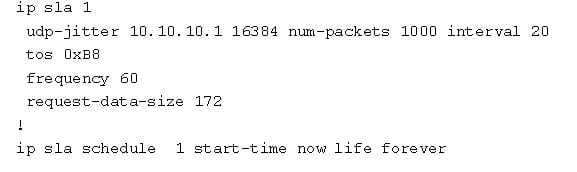
Voice monitoring:
The IP SLA VoIP UDP jitter operation may simulate the voice traffic using the common UDP traffic and codecs which are similar to the real VoIP traffic. A VoIP UDP jitter operations may return 2 additional numeric value which will rate a voice quality.
Source router:
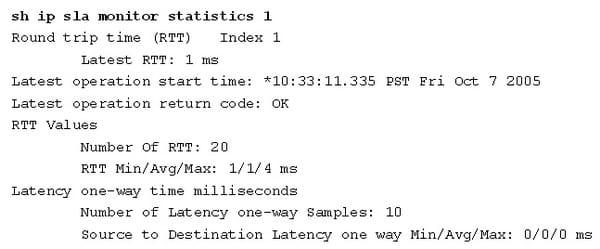
Destination router:
Ip sla responder
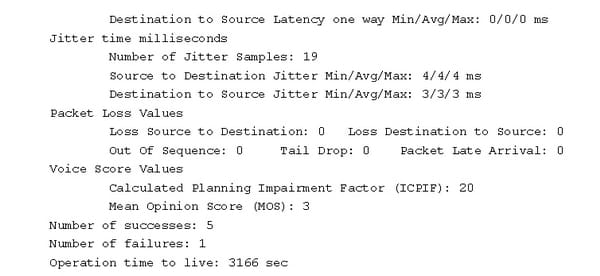
Video monitoring with the UDP jitter:
The IP SLA cannot have any operation proposed designed to monitor the video traffic. The UDP jitter can also be used to simulate the video traffic.
Source router:
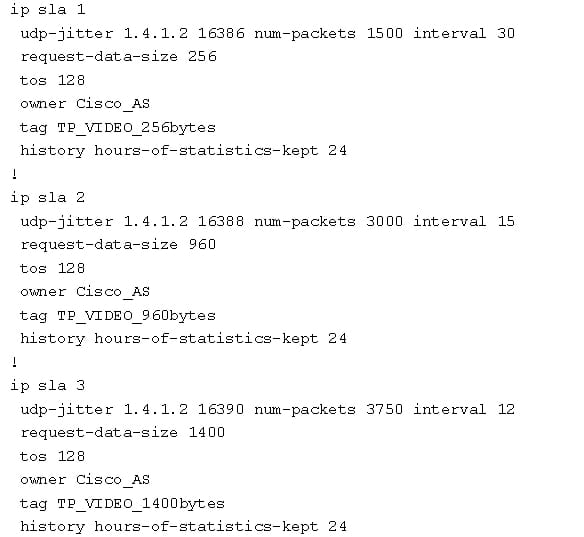
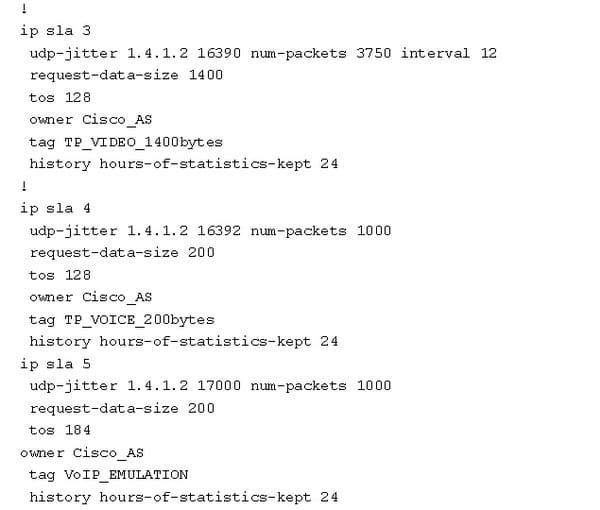

Destination router as follows:
ip sla responder
QoS SLA monitoring:
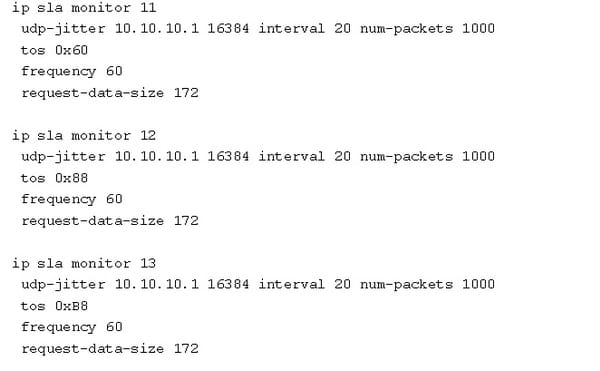
The IP SLA operations may be marked for the type of service to match a target class. The IP SLA configurations support only ToS setting and diffserv will not support.
6.9.a ICMP
The ICMP is one among the main protocols of an IP suite. It is mainly used by the network devices such as router to send error messages. The ICMP is the message control and the error reporting protocol between the host server and the gateway to an internet. The ICMP uses the IP datagram, but the messages are mostly processed by an IP software and it is not directly apparent to the application user. Let us take the IP SLA ICMP in detail.
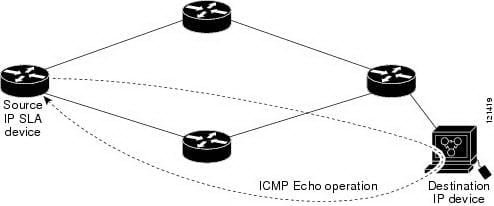
The IP SLA ICMP echo operation is to monitor the end to end response time in between the router and devices by using IPv4 and IPv6. The ICMP echo is most useful for troubleshooting the network connectivity issue.
Step 1:
Command: enable
This step enables the privileged EXEC mode. It enters the password.
Ex: device>enable
Step 2:
Command: configure terminal
It enters the global configuration mode.
Ex: device#configure terminal
Step 3:
Command: ip sla operation-number
This step begins the configuration for the IP SLA operation and also enters the IP SLA configuration mode
Ex: device(config)# ip sla 6
Step 4:
This step defines the ICMP echo operation and also enters the IP SLA ICMP configuration mode.
Command:
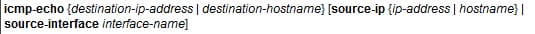
Ex:
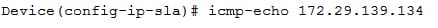
Step 5:
This step sets a rate at which the specified IP SLA operation repeats. It is the optional step.
Command: frequency second
Ex:

Step 6:
This step helps to exit from the privileged EXEC mode
Command: end
Ex:
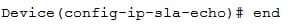
Example configuration as follows:
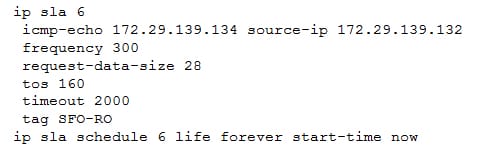
The service level agreement is the common approach to indicate the exact conditions under which service has to be delivered. The typical SLA architecture and its fundamental concepts will give an idea about the SLA technique and concepts in detail. The ICMP echo operation is to measure the time of response between the destination IP device and source IP SLA device. This will help to perform the tasks in a better way.
Site Search:






