- Home
- Popular IT Certifications
- Configuring IPv6 Addressing and Subnetting
How to identify, configure, verify the appropriate IPv6 addressing and subnetting?
The IPv6 serves as the replacement protocol for the IP version 4. As IPv6 uses 128 bits in length, it seems it is far better than the IPv4. So the change IPv4 to IPv4 is unavoidable in today's growing technology. The below content will walk through more about the IPv6 addressing and subnetting. Certainly many things will differ from IPv4 to IPv6. However, most of the core concepts about the IP addressing, routing, routing protocols, and subnetting are somewhat same with that. This chapter will build the foundational concepts such as unicast, EUI-64, ND, RS/ RA, autoconfig(SLAAC), DHCP relay and server and the DHCP protocol operations in detail.
3.2.a Unicast
In the computer networking, the addressing mode refers to a mechanism how the addresses host on the network. The IPv6 provides several types of modes that the single host can also be addressed, and more than one host can be addressed at one time or a host at the closest distance can also be addressed.
In the unicast addressing, the IPv6 interface is identified uniquely in the network segment. An IPv6 packet comprises both destination and source IP addresses. The host interfaces are equipped with the IP addresses that is unique in the network segment. The network router or switch when gets the unicast IP packet, the destined to a single host, sends to one of the outgoing interface which connects the particular host.
The unicast IPv6 addresses are again classified as;
- Link local addresses
- Special addresses
- NSAP addresses
- Aggregatable global unicast addresses
- NSAP addresses
- Site local addresses
3.2.b EUI-64
The most important IPv6 key benefits over internet protocol version 4 is its capacity for the automatic interface addressing. The EUI stands for the extended unique identifier as per RFC2373. It allows the host to assign the unique 64 bit IPv6 interface identifier automatically. This feature is the real key element over the IP version 4 as it eliminates the requirement of the manual configuration or the DHCP in the IPv4 world. This is established on the Ethernet interfaces by just referring the unique 48 bit MAC address as well as reformatting that the value to match the extended unique identifier 64 specification.
The RFC2373 dictates the conversion process, that can be explained in 2 steps. The foremost first step is to convert a 48 bit of the MAC address to the 64 bit value. To perform this, the MAC address is separated first into the two 24 bits, with one as Organizationally unique identifier -OUI and as NIC specific.
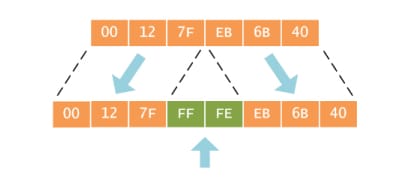
The 16 bits of the hex  value are inserted between those 2 halves to make the 64 bit address. The
value are inserted between those 2 halves to make the 64 bit address. The  is the reserved value in the IEEE guidelines for the EUI, the equipment manufacturers cannot ass in the "real" assignment of the EUI 64 address. On the other side, any EUI address with
is the reserved value in the IEEE guidelines for the EUI, the equipment manufacturers cannot ass in the "real" assignment of the EUI 64 address. On the other side, any EUI address with  value immediately after the OUI portion is recognized as it was generated from the MAC or EUI address.
value immediately after the OUI portion is recognized as it was generated from the MAC or EUI address.
Then the second step is to invert the U/L flag in the Organizationally Unique Identifier address of the portion. The globally unique address allotted by IEE have the bit which is set to 0 originally, indicating the global uniqueness. In the same way, the locally created address, including those used for the virtual interfaces or the MAC address configured manually by the administrator, it will have the bits set to 1. Then again invert the Universal/local bit when using the EUI 64 address as the IPv6 interface ID.
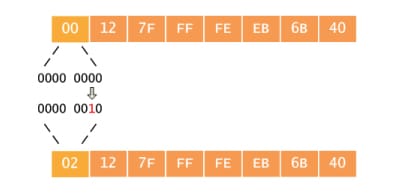
The motivation for inverting a U bit while forming the identifier of the interface is to make it simple for the system administrators to handle the configure local scope identifiers while the hardware tokens are not seen available. It is expected to be the case for a serial links, tunnel end points and much more. The alternative for those in the form of 0200:0:0:1, 0200:0:0:2 and etc., instead of simpler ::1, ::2....
Here the most important part is that the scope address will never change and the global address is global still as well as local address are still local. Instead, the bit is inverted for the convenience, so that the value of a bit has to be inverted as well.
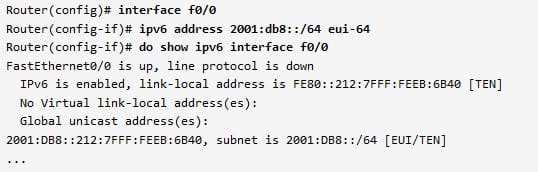
The conversion in the action when assigns the IPv6 address to the router interface.
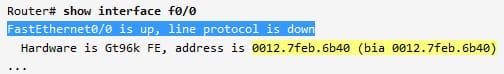
After allotting the EUI 64 designated internet protocol version 6 address to a interface. Verify that the ID interface has been drawn from a MAC address in the described process for both assigned and link local addresses.
3.2.c ND, RS/RA
The neighbor discovery (ND) protocol is the protocol in an IP suite, which is used with the IPv6. It operates on the link layer of an Internet model and responsible for the address autoconfiguration of the nodes. In the IPv6, there are 5 ND messages such as:
- Router solicitation (RS) message
- Router advertisement (RA) message
- Neighbor solicitation (NS) message
- Neighbor advertisement (NA) message
- Redirect message
In the Router solicitation- type 133, any node may send the RS message at any time to request the entire routers on a local link to send RA messages immediately. The routers send the RA messages very periodically, however, when the node powers at first, it casually sends the RS message to obtain the RA information very soon, instead of waiting for a next periodic transmission. It is the only RS message function, so that it has the very easy syntax.
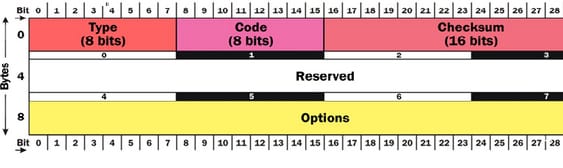
The type field comprises of 133 for RS, the code field has to be 0, the checksum field comprises of the standard IP checksum, the reserved field is unused and has to be 0 and the options field can contain the source link layer address option. It indicates that the link layer address of a sender. If an IP source address is unspecified, then this option must not to be used.
In the RA- type 134, the message communicates with the different subnet wide information to whole nodes in the subnet. Each IPv6 router must send the RA messages in the periodic manner. It must also send the RA messages in the response to the RS message from any of the internal nodes. The RA message syntax is basically complex as shown in the below figure.
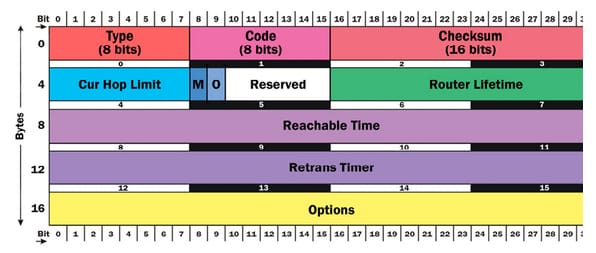
The type field comprises of 134 for the RA. The code field has to be 0, the checksum field comprises of the standard IP checksum, then the reserved field is mostly unused and has to be 0. Then, the cur hop limit field indicates the subnet default values for the hop limit that is placed in a hop limit field of the entire outgoing IPv6 packets. The value of the 0 means that this default value is not at all specified by a sending router. Then the M flag is also known as managed address configuration flag and 'O' flag also known as other address configuration flag. Here, the reserved field is unused and has to be zero, then the router lifetime specified lifetime of a sending router in seconds. The lifetime field of the zero router implies that the router is not interested to act as the subnet gateway, so need not add to a default gateway table by the nodes getting the RA messages. The reachable time is used in a NUD mechanism. The node can be a neighbor is reachable for that number of the milliseconds after getting the reachability confirmation from the neighbor unreachability detection - NUD. The value of the zero indicates that the setting is not indicated by a sending router. Then the retrains is used in an AR and NU mechanisms. The time is in milliseconds in between the transmitted NS messages. The value of the zero implies that the setting is not indicated by a sending router. Then the final one is options field, which has the options like prefix information options, MTU option and source link layer address option.
3.2.d Autoconfig (SLAAC)
The IPv6 has the 2 primary mechanisms for the network autoconfiguration. They are SLAAC- stateless address autoconfiguration and DHCPv6 0- dynamic host configuration protocol for the IPv6. The SLAAC is one among the 9 ND mechanisms, however its very essential as well as complex to have it. It is the important aspects of the IPv6 and will be the key to the deployments of huge numbers of the IP phones, smart TV's, individual computers, connected MP3 players and sensors and many more in the list. The SLAAC is the inherently the decentralized mechanism. The subnet routers will send the RA messages and an internal nodes will autonomously create the global addresses based on the information. Here, no central nodes are involved in the generation other than supplying the valid prefixes in a subnet. There, the routers have no idea of which addresses of every node are generated. So that it is stateless, which means no "state" is maintained by routers.
The SLAAC permits any of the IPv6 compliant nodes to the autonomously generated 1 or more IPv6 unicast addresses. The SLAACbased on having the node in every subnet acting as the source of the neighbor discovery RA messages. Any of the IPv6 complaint firewall or router should have that capacity, but it requires to be well configured and also that has to be enabled. Then, without the RA message's source, all the IPv6 addresses of the every node have to be configured manually.
3.2.e DHCP relay and server
The DHCP version6 relay and server functions are mutually very exclusive on the interface. The DHCPv6 server will offer the configuration parameters which do not need the server to maintain the dynamic state for the individual clients including domain search list option and DNS server addresses. The server function can enable on the enabled interfaces of the individual IPv6. The DHCP server can be configured to do the prefix delegation. Then all configuration parameters for the client is independently configured with the DHCP version 6 configuration pool that is saved in the NVRAM. The configuration pool may be associated with the specific DHCP server on the interface while it gets started. The DHCP server also maintains the automatic binding tables in the memory for track assignment of the configuration parameters like prefixes in between a server and also its client. Then the automatic bindings may be saved permanently on the database agent that can be local NVRAM system or remote TFTP server. The DHCP relay is the one which resides on a client link. It is merely used to relay messages in between the server and client. The relay operation is very transparent to a client. The client locates the DHCP server using the reserved, the link scoped multicast addresses.
3.2.f DHCP protocol operations
The DHCP was proposed to assign the IP address as well as networking information to the computers so that it can communicate through the network automatically with the IPv6 network. The DHCP for the IP version 6 will offer the stateless configuration settings to the IPv6 hosts. The IPv6 hosts will use several methods to configure the addresses such as stateful address autoconfiguration and stateless address autoconfoguration(SLAAC). The SLLAAC are explained well in the above topics.
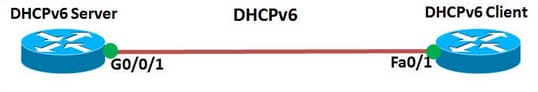
Configuration:
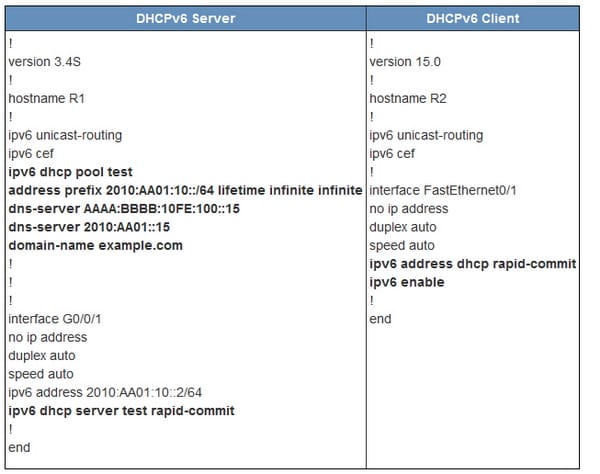
In this configuration, the R1 router is configured as the DHCP server and the R2 router is configured as the DHCPv6 client. To display the DHPv6 information about the pool in the DHCPv6 server will use " show ipv6 dhcp pool" command. Then the output shows the active number of the clients is one and displays other parameter of configuration information like lifetime information and server addresses.
Frankly, today, most of the organizations do not use the public IP version 4 addresses throughout the enterprise internetwork and they like to use the IPv6. So that it is more important learn the about the IPv6 addressing and subnetting concepts to perform the tasks in a better way. The internet protocol version 6 is the new addressing protocol proposed to incorporate the whole sort of the need of the future internet known to all as internet version 2. This protocol as its predecessor IP version 4 works on the layer 3. It offers enormous amount of the logical address space and also has ample features.
Site Search:






