- Home
- Popular IT Certifications
- Policy-Based and Suboptimal Routing
How to Configure policy-based routing and identify suboptimal routing
The main issue that the many network engineers find with the typical routing protocols and systems is that it was based on a routing traffic based on the destination traffic, but when traffic on the network needs the more hands on solution, then the policy based routing takes over it. By using the policy based routing, the network engineer will get the ability to dictate a routing behavior based on the various criteria other than the destination network such as destination network or source, destination address or source, protocol, destination port or source, packet classification and packet size. The configuration of PBR and suboptimal routing are identified.
3.12 configure and verify policy based routing
The PBR stands for the policy based routing. It has the capability to implement the QoS by marking a traffic and classifying at a network edge and using the PBR throughout the network to a route marked traffic along the specific path. The PBR provides a mean to route a particular packet to its destination via the particular next hop. With the help of the PBR, can control which packet follow which path via the network. The particular path that these packets will take will be based on the configuration parameters like address, protocol, VLAN membership, or priority.
This PBR will provide more control over the routing by complementing and extending the existing mechanism offered by the routing protocols. The PBR allows to specify the paths for the certain traffics such as priority traffic over the high cost link. Set up the PBR as the method to route packets depends on the configured policies.
The PBR allows to perform the tasks such as:
- Route packet to the particular traffic engineered paths.
- Classify the traffic based on the extended access list criteria. Access the lists and then accomplish a match criteria.
- Set the IP precedence bits, providing a network the capability to enable the differentiated classes of the service.
The policies are based on the IP address, protocols or port numbers. For the simple policy, use any 1 of the descriptor. For the complicated policy use all of them.
You may ask, why to use this PBR. Let us take the company has 2 links in between the locations, one a low delay expensive with high bandwidth and other high delay lower expensive link with low bandwidth. Now with the help of traditional or old routing protocols, higher bandwidth link will get the most suppose not the entire traffic sent over it depends on the metric savings gained by a delay and/or bandwidth link characteristic. In that way, traffic which needs high bandwidth or low delay link characteristic will be enough possible without giving the entire traffic across the link. Then the implementation of the PBR is very simple and it configured by using the set/match process. The traffic that is to be managed by the PBR can be matched by an ACL and have its parameters or path changed by the set command.
All the packets received on the interface with the PBR enabled are flowed via enhanced packet filters are known as the route maps. This route maps are used by the PBR to find out where the packet is forwarded. The PBR is implemented by simply applying the route map on the incoming interface. The provided interface may have only the 1 route map configured. The route map is configured at a global configuration parser mode. The route map consists of 1 or more route map statements. In that, every statement has the sequence number and a deny clause or permit.
Enable the PBR to change a routing path of specific packets from a default path which is chosen by the IP routing. It offers a wide range of functionality such as protocol sensitive routing, equal access, routing based on the dedicated links, routing based on the interactive versus batch traffic and source sensitive routing. Some traffic or application may benefit from the source specific routing.
To enable the PBR, create the route and apply that on the specific interface
Step 1:
For the PBR configuration, the first thing is the configuration of the route map that defines the policy. It can be done by the route map command as given below:
router(config)#route-map map-tag {permit | deny} {sequence-number}
Here the map tag is just the name that is simply used to indicate the particular route map as well sequence number used to set an order in which the route map statement is evaluated suppose the multiple statements are exist.
Step 2:
The configuration of the match command is used to match a specific type of traffics which can be routed with the help of configured policy. The traffic which is not matched with any of those commands can be handled off to a destination based routing mechanism. Then the common command for that is:
router(config-route-map)#match length minimum-length
The above command is mostly used to match the certain layer three packet sizes and it will be used to send the packets of different sizes down various paths.
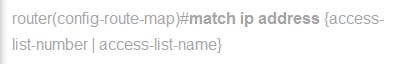
The above command is a workhorse of certain PBR configuration and it is used to match any combination of numbers depends on the configured access list.
Step 3:
It is mainly to configure the specific set of command and also used to control the matched traffic behavior. The typical following command will be used:
router(config-router-map)#set ip next-hop ip-address
The above command is mainly used to indicate an IP address of the next hop of matched traffic. Then make sure that an IP address that is specified in that command is nearby to a configured router.
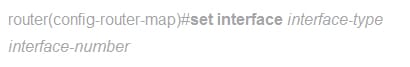
The command used to indicate the matched traffic output interface.

The command used to indicate an IP of a next hop of the matched traffic, such as a set ip next-hop. Even though the command is varied from a set ip next-hop command by just having the various routing orders. While using a set command ip next-hop the traffic is a policy routed and then passed onto the routing method based on destination. While using the command set ip default next-hop, the routing method based on the destination is used and then it allow to pass the policy routing.
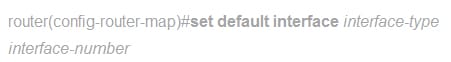
The command used to indicate the default output interfaces to send the traffic where no explicit route exists.
While using any of those combinations of command within the policy, the commands will evaluate in a below order such as:
Set ip next-hop
Set interface
Set ip default next-hop
Set default interface
The PBR is the most powerful tool that can used to control the certain routes of the network traffic, although make sure that the only PBR is used when it is required as a routing method based on the destination which work well by themselves. It helps to maintain the efficiency and proposed for a particular set of circumstances.
3.13 Identify suboptimal routing
Most of the issue with the redistributed routes are fallen into 2 major categories such as suboptimal routing and routing loops. The suboptimal routing is normally happening because of the miscalculation in coming up with the correct seed metric value. Then the packets will get where it's supposed to go eventually, but not in the optimal manner. The suboptimal routing is the problem occasionally created by the redistribution. Suppose, the administrative distance chose the suboptimal route when the directly connected network is proposed as the backup link. However, it is the AD problem as opposed to the redistribution, then it is essential to assure that a suboptimal route is not propagated into a new routing protocol. While designing the network follow the below steps to avoid suboptimal routing while redistributing the routing protocols.
Have the knowledge as well as clear documentation about the network topology, traffic flow, and routing protocols.
Find out which protocol is core protocol and edge protocol.
Find out the redistribution direction, and into the routing protocol that the routers have to be distributed.
Do not overlap the routing protocols. It is very easy if a different protocols are clearly delineated into the separate domains with the routers acting in the function very similar to the area border routers.
Identify a boundary router on which the redistribution has to be configured.
Suppose the 2 way redistribution are not avoided, then use the manual configuring a metric, using distribution access lists, manually configuring the AD mechanism.
The suboptimal problem will occur while 2 or more routers connected between the 2 routing domain, mainly RIP and OSPF. The suboptimal problem behavior is router can use the suboptimal path to forward the packets.
Take OSPF as shown in the below figure:
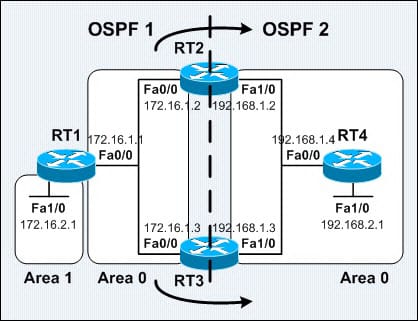
While redistributing in between the different OSPF processes at the multiple points on the network, then it is possible to get into the situations of the suboptimal routing. The above figure shows the OSPF redistribution network. In that, both the RT3 and RT3 are operating OSPF 2 processes as well as redistributing from the OSPF 1 into the OSPF 2 process. The RT1 is the ABR which advertise 172.16.2.0/24 as an inter area OSPF route to the RT3 and RT2. The RT3 and RT2 are redistributing the route from OSPF1 into the OSPF 2 process. Hence, both the RT3 and RT2 can lear more about the 172.16.0./24 as the IA route through the OSPF 1 and as an E2 route through OSPF 2 process. However the IA route is always preferred over the E1/E2 routes, routing tables of the RT2 and the RT3 will show the 172.16.2.0/24 as the IA route with the RT1 as a next hop. Since, there is a chance that the route can be installed into a routing table as the E2 route.
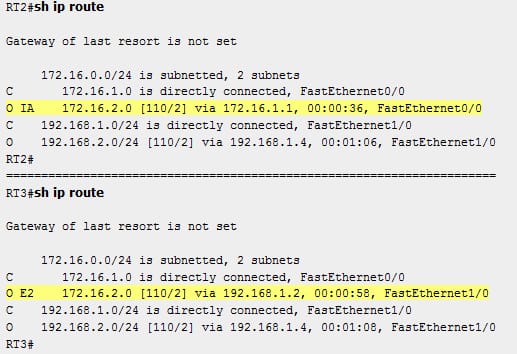
When enabling the multiple OSPF process on the router, the process is independent from a software perspective. While the OSPF operates as in the single process of OSPF. It will always prefer the internal route over the external routes. The OSPF will not perform the route selection between the processes. The OSPF route types and metrics are not considered while deciding a route from what process it has to install in the routing table. Then, there is no interaction in between the various OSPF processes as well as the tie breaker is the AD. Since, both the OSPF process has the default of 110 as the AD value, then the first process which installs a route in the routing table can succeed against the other process.
Here, the first solution is mainly to define the administrative distance value for a route from the different processes of OSPF, hence the routes of specific OSPF process are preferred over a route of another process by the human intention and also not matter of the luck or chance. By implementing a distance OSPF external 115, the OSPF router sub commands under an OSPF 2 process on the both routers, that will increase the administrative distance of an external route in the OSPF 2 process, the internal routes learnt through the OSPF 1 process will prefer over the external route redistributed from the OSPF 1 into the OSPF 2. In case, the main purpose of implementing the various OSPF process is mainly to filter specific routes, then the OSPF ABR type 3 LSA filtering kind feature has to be taken into consideration to achieve the same result. Rather than implementing the OSPF 2 process, the links and routers reside in the OSPF 2 process as in a sample network, can be configured as in the other area of OSPF 1 process followed by simply implementing the type 3 LSA filtering on the RT3 and RT2, the ABR.
The PBR provides you the flexible way routing the packets by permitting you to define the policies for the traffic flows, lessening reliance on the routes which are derived from the routing protocols. The PBR offers a much finger grained level of control across where the packets are routed to. In the other session, the suboptimal routings are discussed. In this, you can learn the how to identify and avoid and why this suboptimal routing problem occurs.
Site Search:






