- Home
- Popular IT Certifications
- Loop Prevention Mechanisms Configuration
How to Configure and verify loop prevention mechanisms
The routing loop is the common issue with the various types of networks. They are formed when the error occurs in the routing algorithm operation and as a result, in the group of nodes, the route to the specific destination forms the loop. In the link state routing type protocols such as IS-IS or OSPF, the routing loop will disappear when the new network topology was flooded to the entire routers within a routing area. The newer distance vector protocols such as Babel, DSDV, EIGRp and BGP have built-in the loop prevention. It uses the algorithm which assures that the routing loop will never occur, not even transiently. In the older routing protocols like RIP don't implement a new form of loop prevention. It implements the mitigations such as route poisoning, split horizon and route filtering and tagging.
3.15 .a Route tagging and filtering
Unless the remedy is offered inherently by a protocol, the routing loop may easily occur in the mesh network. The routing loop disallows few packets from properly routes mainly due to incorrect the routing information circulating in a network. Then the symptom of such routing loops is counting to infinity. While configuring the multipoint redistribution, it is the best idea to use the route tagging to prevent advertising from the routing protocol.
The routing loops will normally occur when redistribution between the protocol with the higher administrative distance to the protocol with lower administrative distance. Therefore, to prevent the routing loop, it is required to filter and tag the routes being learned from its neighbors. The route map is the very powerful tools which are used to accomplish in preventing routes redistribute back to an original domain.
You can filter the routes in the number of ways, filtering the outgoing and incoming routes from the neighbors by using the route maps, distribute lists, filter lists, by BGP community, by BGP attribute and prefix lists. The basic filtering of the BGP route filtering is similar to a route filtering configuration used by the IGP protocols. The list of network prefixes is created by using the prefix list or access list and the information is applied either to the specific neighbor or the neighbors, a blanket application to BGP peers or a peer group. The major difference between the BGP and the IGP route filtering is the number of options which BGP offers for the filter selection criteria. Even the BGP can filter in 3 ways, such as distribute list filtering, filter- list filtering and route map filtering. Instead of solely relying on the addresses and ip access list, the route filtering can be performed by the route tagging. To control the transmission of the routes between the different levels, you can tag the routes with certain attributes also. The routes will carry the attributes which a routing policy can use to import and export the routes between the levels. The sub TLV to the IP prefix TLV are used to carry the attribute or tag on the routes when it comes to the IS-IS. The route tagging will not work when the IS-IS traffic engineering is disabled. You can also verify the tagging and filtering route by correctly applying the command. After verifying the routes are tagged, you can apply the route leaking policy to match the presence of AD instead of the list of the route filters.
The route filtering is a process by which certain route is not considered for the inclusion in a local route database. This route filtering and tagging is very particularly essential for the BGP on a global internet which is used for the variety of reasons.
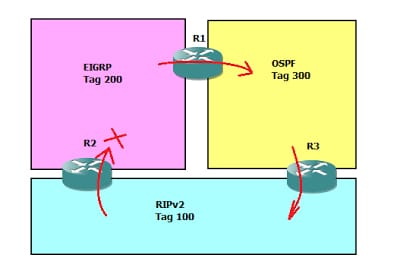
In order to prevent the route redistribution fully back that can cause the loop, for that requires to configure the route map for all the routing domain and also all directions.
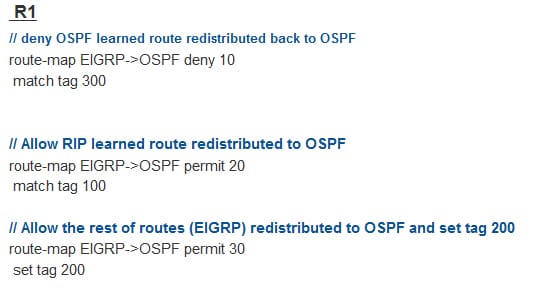
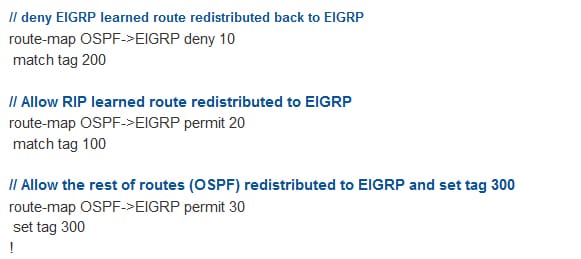
Take the above example, here filter the route from redistributes back to an original domain. Preventing the EIGRP route from getting redistribute back to the EIGRP domain from the RIP and OSPF. In certain condition, make use of the route map to perform this.
3.15.b Split - horizon
The distance vector protocols are very susceptible to the routing loops. The split horizon is the one among the features of the distance vector routing protocols which prevents them. It prevents the router from advertising the path back onto an interface from that it was learned.
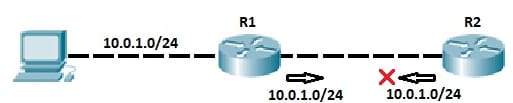
Consider the above network topology. The R2 router has the route to a 10.0.1.0/24 subnet which is advertised to R1 router with the help of the RIP. The R1 router gets the updates as well as stores a route in the routing table. R1 router knows that a routing update for the route has come from the router R2, so it never advertises a route back to an R2 router. Or else, suppose the 10.0.1.0/24 network goes down, then the R2 router will get the route to a 10.0.1.0/24 subnet from router R2. The router R1 thinks that the R2 has a route to reach a subnet and also uses that path. The Router R2 gets the packet from a R1 and send it back to R2 router, because router R2 thinks that the R1 router has the route to reach a subnet, so that creates the routing loop.
The split horizon is the base technique which is used to deduce the chance of the routing loops. The split horizon states that it will never send useful information about the route back in a direction from which an information came and hence the routing information will not be sent again back to a source from when that came. The fact is that only interfaces are mostly considered for a direction and not the neighbors. This rule will work not only for the routers learned through the distance vector routing protocol and also for the routes installed in the routing tables as directly connected into networks. As it resides on a same network, then the neighbors cannot need any of the advertisements on the path to that of the shared networks.
The spilt horizon rules also help to prevent the 2 node routing loops and improves the performance by eliminating the unnecessary updates. The spilt horizon with the poison reverse permits the routing protocol to advertise the entire routes out the interface and also learned from the earlier interface are marked with the infinite distance metrics.
The spilt horizon method is very effective as well as simple to implement and used by most of the distance vector protocols such as VPLS, Babel, EIGRP, IGRP and RIP. The spilt horizon can also be achieved by the technique called as poison reverse. It is equivalent to the route poisoning in all the possible reverse routes which is informing all the routers that the route back to an originating node for a specific packet. The spilt horizon with the poison reverse technique is very effective than the simple split horizon in the networks with the multiple routing paths, however, it affords no remarkable improvement over the simple split horizon in the networks with only 1 routing path.
The spilt horizon with the poison reverse is the variant of the split horizon, route advertising, in which the router actively advertises the routes as the unreachable over an interface through which they were learned. This effect such kind of announcement is mainly to remove most of the looping routes before it propagate via the network. The major disadvantage of the poison reverse is which it will significantly improve the size of the routing announcements in specific common network topologies. This poison reverse technique is used to optimize the routing information transmission and increases the time to reach the network convergence.
3.15.c Route poisoning
The route poisoning is one of the methods to prevent the router from sending packets via route which has become the invalid within the computer network. The distance vector routing protocols in the networks which use route poisoning to indicate to the other routers that the routes are no longer reachable and it will not be considered from the routing tables.
In the route poisoning, it sets the hop count to the unreachable state when the failed network is identified. The route remains poisoned as long as the hold down timer expire. This hold timer is based on the routing protocol and each protocol has a various hold down timer. It is the only one direction traffic flow. Suppose the route is not back at the time of the hold down period expire. Then the route is removed from a routing table and added in a garbage table.
The formation will typically occur when the network goes down. While the router finds the network is down, then it wait to expire for the periodic update. Here, the router may poison a route by simply assigning the infinite metric. It implies that the other routers may not reach the dead network. Since 16 hop is moreover invalid. Then the router will advertise a dead route which is called as route poisoning. When the neighbor gets the poisoned route, then it will break the rule of the split horizon and also send back to the source a same poisoned Route. This is called as the poison reverse. It is important to ensure that the each router gets the original poison route and its updates.
Now the router requires the good time to propagate the poisoned route to entire router, hence the routing loop will be avoided. Especially for this purpose, the hold down timer mechanism is used. The hold down timer is the period of time. In that particular period of time, the poisoned route will freeze in a routing table. So the route becomes unreachable, but it is available in the routing table as possible down. When a hold down period expires, then the route will turn into action again / removed from a routing table. Then the route becomes active only if the router gets the better or same metric value for a poisoned Route. Suppose the worse metric value is achieved for a poisoned route and also the hold down timer expired, then the route can be flushed well out after 240 seconds.
For the RIP, the maximum hop count is 15 and so to do route poisoning on the route, it's hop count is changed into 16, deeming it unreachable and so the routing update is sent. The route poisoning is the best way to avoid the inconsistent updates, when it is used in the conjunction with the triggered updates can actually assist to speed up the network convergence because the routers are no longer have to wait before it advertise that the specific route is poisoned. The below figure gives the solution for the route poisoning.
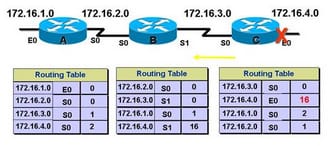
The new version of the IGRP replaces the hold-own with the route poisoning. It observes the increasing cost to the destination and also assume the loop has formed. Only after the reconfirmation of the metric is route assumed to be usable.
However, unlike split horizon with the poison reverse, the route poisoning offers for sending the updates with the unreachable hop counts to all nodes in a network. Some of the distance vector routing protocols like RIP will use the maximum hop counts to find out the number of routers the traffic must travel to reach a destination. Every route has the hop count number that is incremented as a routing information is passed from the router to router. The router is considered as unreachable suppose a hop count exceed the maximum limit allowed.
When the inconsistent routing table is not updated due to the slow convergence in the network where the changes occur. It is very essential to prevent the routing loops with the help of mitigation process such as route poisoning, route tagging and filtering and split horizon. In that, the split horizon prevents the loops between the adjacent routers and route poisoning prevents the larger loops whereas route tagging and filtering will tag as well as filter the unwanted entry and prevents the loops very well. These mechanisms and techniques help to prevent the layer 3 routing loop.
Site Search:






