- Home
- Popular IT Certifications
- ACL & Layer 1 Issues: Troubleshooting Tips
How to troubleshoot and resolve ACL & Layer 1 issues?
ACL is basically is a rundown of authorizations connected to an item. An ACL defines which clients or framework courses of action are allowed access to protests, and also what operations are permitted on given objects. Each section in a common ACL indicates a subject and an operation. For example, if a record has an ACL that contains (Alice: read, write; Bob: read), this would give Alice authorization to peruse and compose the document and Bob to just read it.
When a subject demands an operation on an article in an ACL-based security show, the working framework first checks the ACL for a relevant passage to choose whether the asked for operation is approved. A key issue in the meaning of any ACL-based security model is deciding how get to control records are altered; specifically which clients and courses of action are allowed ACL-alteration access.in the 1990s the ACL and RBAC models were widely tried and used to administrate document consents. A file system ACL is an information structure (generally a table) containing passages that indicate singular client or gathering rights to particular framework questions, for example, projects, courses of action, or documents. These entrances are known as access control sections (Aces) in the Microsoft Windows NT, Openvms, Unix-like, and Mac OS X working frameworks. Every open item contains an identifier to its ACL. The benefits or consents focus particular access rights, for example, whether a client can read from, keep in touch with, or execute an item. In a few executions, an ACE can control whether a client, or gathering of clients, may change the ACL on an item. The vast majority of the UNIX and Unix-like working frameworks (e.g. Linux, BSD, or Solaris) help Posix.1e ACLS, taking into account an early POSIX draft that was deserted. A hefty portion of them, for instance AIX, Freebsd, Mac OS X starting with adaptation 10.4 or Solaris with ZFS file system, help Nfsv4 ACLs, which are some piece of the Nfsv4 standard. In spite of the fact that it is furthermore conceivable to arrange Access Control Lists focused around system space names, this is by and large a faulty thought on the grounds that individual TCP, UDP, and ICMP bundles don't contain area names. Thus, the gadget authorizing the Access Control List should independently purpose names to numeric locations. This displays an extra assault surface for an aggressor who is looking to trade off security of the framework which the Access Control List is ensuring. Both individual servers and switches can have system ACLs. Access control records can by and large be designed to control both inbound and outbound activity, and in this setting they are like firewalls. Like Firewalls, ACLs are liable to security regulations and norms, for example, PCI DSS. The principle option to the ACL model is the Role-based access control (RBAC) model. A "negligible RBAC Model", RBACM, might be contrasted and an ACL component, ACLG, where just gatherings are allowed as passages in the ACL. Barkley (1997) demonstrated that RBACM and ACLG are comparable. In advanced SQL usage, ACL likewise oversee gatherings and legacy in a pecking order of gatherings. So "current ACLs" can express all that RBAC express, and are prominently capable (contrasted with "old ACLs") in their capacity to express get to control approach regarding the path in which chairmen view associations.
Here is the list which ACL uses;
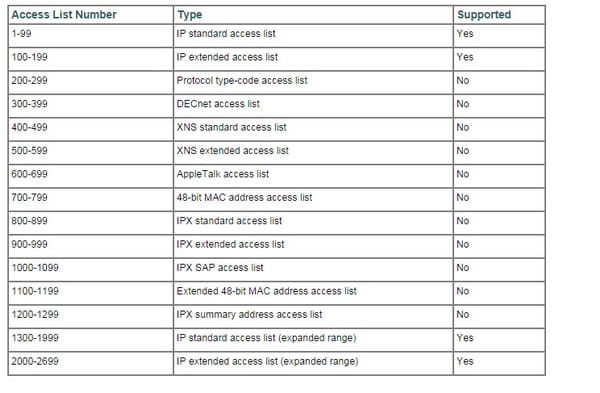
The Physical layer has two obligations: it sends bits and gets bits. Bits come just in estimations of 1 or 0. The Physical layer corresponds specifically with the different sorts of genuine correspondence media. Various types of media speak to these bit values in distinctive ways. Particular protocols are required for each one kind of media to portray the best possible bit examples to be utilized, how information is encoded into media signals and the different characteristics of the physical media's connection interface.
The Physical layer particulars point out the electrical, mechanical and useful necessities for initiating, keeping up and deactivating a physical connection between end frameworks. At the physical layer, the interface between the Data Terminal Equipment (DTE) and the Data Circuit-Terminating Equipment (DCE) is distinguished. The Physical layer's connectors (RJ-45, BNC e.c.t) and diverse physical topologies (Bus, Star, and Hybrid systems) are characterized by the OSI as measures, permitting distinctive frameworks to convey.
Here is a way through which you can resolve an error which takes place through ACL;
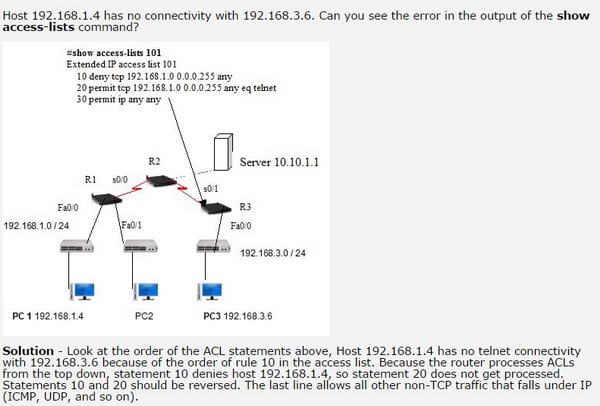
Verify statistics
Verifying statistics is very important thing to do. It can enable the user to understand that how is the performance of the router and whether the data is being transmitted or not.
Verify permitted networks
Traffic streaming over an interface in the FWSM might be controlled in two ways. Movement that enters the FWSM might be controlled by appending an inbound access rundown to the source interface. Movement that passageways the FWSM could be controlled by joining an outbound access rundown to the objective interface. To permit any activity to enter the FWSM, you must join an inbound access rundown to an interface; generally, the FWSM consequently drops all movement that enters that interface. As a matter of course, activity can retreat the FWSM on any interface unless you limit it utilizing an outbound access list, which adds confinements to those officially arranged in the inbound access list. "Inbound" and "outbound" allude to the application of a right to gain entrance list on an interface, either to movement entering the FWSM on an interface or activity leaving the FWSM on an interface. These terms don't allude to the development of activity from a lower security interface to a higher security interface, normally known as inbound, or from a higher to lower interface, usually known as outbound. You may need to utilize an outbound access rundown to rearrange your right to gain entrance list design. For instance, in the event that you need to permit three inside systems on three separate interfaces to get to one another, you can make a basic inbound access list that permits all movement on each inside interface
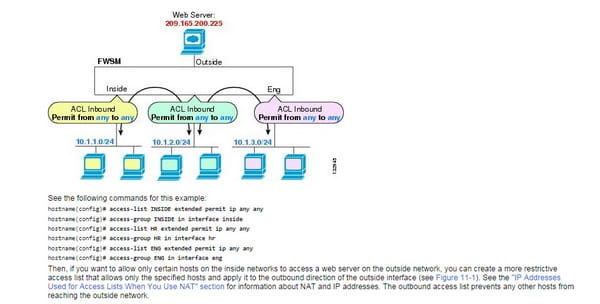
Verify direction
The following commands are used for knowing where the ACL is applied;
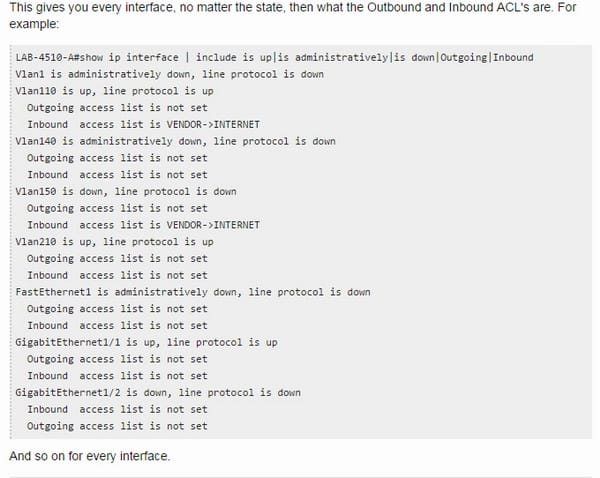
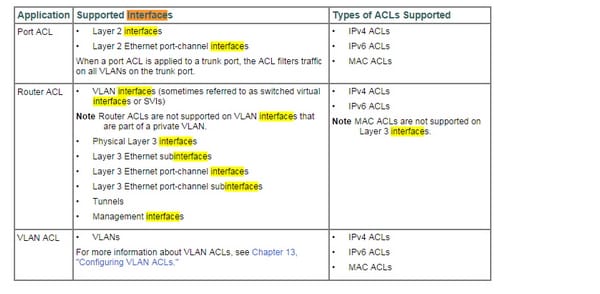
I. Interface
Here is the information regarding the interface;
Framing
In computers networking and telecom, and frame is a computerized information transmission unit that incorporates outline synchronization, i.e. an arrangement of bits or images making it feasible for the collector to recognize the starting and end of the parcel in the stream of images or bits? On the off chance that a recipient is associated with the framework amidst a frame transmission, it disregards the information until it recognizes another casing synchronization arrangement. A frame is an information parcel on the Layer 2 of the OSI model. A casing is "the unit of transmission in a connection layer protocol, and comprises of a connection layer header took after by a packet." Examples are Ethernet outlines (greatest 1500 byte in addition to overhead), PPP outlines and V.42 modem outlines.
In information transfers, particularly time-division multiplex (TDM) and time-division numerous access (TDMA), a frame is cyclically rehashed information obstruct that comprises of an altered number of time openings, one for every consistent TDM channel or TDMA transmitter. In this setting, a frame is normally an element at the physical layer. TDM application illustrations are SONET/SDH and the ISDN circuit exchanged B-channel. TDMA samples are the 2g and 3g circuit exchanged cell voice administrations. The casing is additionally a substance for time-division duplex, where the versatile terminal may transmit amid a few timeslots and get amid others.
CRC
It is a mistake recognizing code regularly utilized within advanced systems and capacity gadgets to locate unintentional progressions to crude information. Pieces of information entering these frameworks get a short check worth appended, in light of the rest of a polynomial division of their substance; on recovery the computation is rehashed, and remedial move might be made against assumed information defilement if the check qualities don't match. CRCS are purported on the grounds that the check (information confirmation) quality is an excess (it stretches the message without including data) and the calculation is focused around cyclic codes. CRCS are famous in light of the fact that they are easy to execute in double fittings, simple to examine scientifically, and especially great at recognizing normal lapses brought on by commotion in transmission channels. Since the check esteem has a settled length, the capacity that creates it is sometimes utilized as a hash function. The CRC was designed by W. Wesley Peterson in 1961; the 32-bit CRC capacity of Ethernet and numerous different principles is the work of a few analysts and was distributed in 1975.crcs are focused around the hypothesis of cyclic lapse adjusting codes. The utilization of efficient cyclic codes, which encode messages by including altered length check esteem, with the end goal of blunder identification in correspondence systems, was initially proposed by W. Wesley Peterson in 1961. Cyclic codes are easy to execute as well as have the profit of being especially appropriate for the recognition of blast lapses, adjoining arrangements of wrong information images in messages. This is vital on the grounds that blast lapses are regular transmission blunders in numerous correspondence channels, including attractive and optical stockpiling gadgets. Ordinarily a n-bit CRC connected to an information piece of self-assertive length will catch any single mistake blast not more than n bits and will locate a small amount of 1 - 2-n of all more lapse blasts. Detail of a CRC code obliges meaning of a purported generator polynomial. The imperative proviso is that the polynomial coefficients are ascertained as per the math of a limited field, so the expansion operation can just be performed bitwise-parallel (there is no convey between digits). The length of the rest of constantly short of what the length of the generator polynomial, which in this way decides to what extent the result might
Runts
We should say that we are on a PDA call, and we consent to use no less than 15 words at once. (More is alright, however no less than 15). On the off chance that I have to say "alright" and simply that, in view of the standard, I would say something like, "alright, filler word, filler word, filler word", and so forth until I surpass the base of 15. This would be called cushioning. On the off chance that you were tuning in, and you heard just 5 words in a sentence or gathering, you could accept that something happened with the sender or the transmission on the grounds that the base length tenet wasn't emulated.
In the days of old school, when we imparted data transmission through center points, if one gadget was sending on the system, and an alternate gadget sent edges on the same system (unintentionally or on the grounds that the two gadgets both thought the system was clear before they sent their casings), this would ravage generally OK edges, and just a section of a casing (under the base length) may be perused by a host, and because of the size could be viewed as a runt and be disposed of (as not being a substantial edge).
Giants
A "GIANT" is simply any frame which got over your MTU size. As has been noted, it could be anything as straightforward as a dot1q endeavor, or MPLS edge, or simply something errant.
Dropped packets
This is how to troubleshoot the dropped packets;
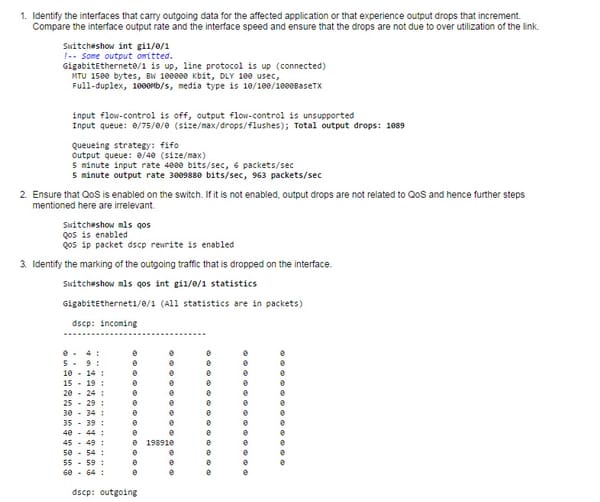
These drops can be changed through two methods, which is buffer change and second is the change of scheduler.
Late collisions
99% of the time you ought to have no crashes with a switch. The exemption is the point at which you are associated with an imparted fragment (center), or a NIC that is just doing half duplex. With full duplex, disc is handicapped and accordingly the interface would not see an impact, yet a blunder. A long link would be the regular answer (past 328 feet or 100 meters). Notwithstanding, there could be a crudely actualized repeater organize that it is joined with, or the repeater or center point class not proper for the separation. We used to have a few decides that we needed to stick to that could result in this also. There are fundamentally limits on the width. At the point when the measurement is excessively vast (or the repeaters excessively moderate), an edge may not be seen by the crash discovery component before it times out and supposes it can send an alternate casing. That is a late impact. Some of this guideline is likewise influenced by the class of repeaters joined. Case in point a class 1 center ought not to be joined with an alternate center.
Input/output errors
There are some input and outputs errors which occur when we use the show ATM command. The picture below shows details;
1. There are the input commands;
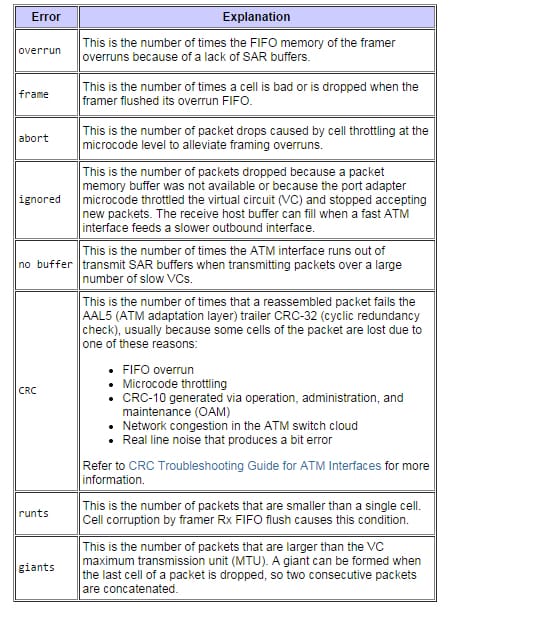
1. This is for output errors;

One must know about what is ACL, as we can see that ACL holds up some great importance in the field of networking. So by going through this article, it is for sure that you can know what ACL is and how it works.
Site Search:






