- Home
- Popular IT Certifications
- How to Configure, Verify and Route VLANs
The process of configuring and verifying VLANS and describe how VLANS create logically separate networks and the need for routing between them
A VLAN is a gathering of gadgets on one or more LANS that are designed to convey as though they were joined to the same wire, when actually they are placed on various diverse LAN fragments. Since VLANS are focused around legitimate rather than physical associations, they are to a great degree adaptable. Here are the important components of VLAN:
Network segmentation
Network Segmentation is the procedure of dividing systems containing touchy data from those that do not.by portioning systems; the security center might be put on the regions that matter most. This decreases the expenses of consistence with numerous regulations. Moreover, work concentrated or immoderate solidifying may be restricted to those systems that are required the most. This additionally ensures that just sanction workers have admittance to touchy data, which lessens the negative impacts if a break ought to occur.by sectioning systems, the security center could be set on the zones that matter most. This decreases the expenses of consistence with numerous regulations. Moreover, work escalated or expensive solidifying may be constrained to those systems that are required the most. This likewise ensures that just endorsed workers have admittance to delicate data, which decreases the negative impacts if a rupture ought to occur. The proceeded with, high recurrence of effective cyber-attacks against today's undertakings has made it richly clear that customary, edge driven security procedures are no more viable. There is insufficient deceivability, control and security of client and application movement traveling high-hazard system limits, and an antiquated supposition that everything within an association's system ought to be trusted.
The Zero Trust structural planning methodology, initially proposed by Forrester Research, is planned to address this by pushing "never trust, dependably check" as its controlling guideline. With Zero Trust there is no default trust for any element including clients, gadgets, applications, and parcels paying little heed to what it is and its area on or in respect to the corporate system. By making Zero Trust limits that viably compartmentalize diverse fragments of the system, you can secure discriminating protected innovation from unapproved applications or clients, diminish the presentation of defenseless frameworks, and keep the parallel development of malware all through your network. Some associations use virtual neighborhood (VLANS) to section their system, yet VLANS essentially confine system activity - they are not able to implement the control of advantaged data. Furthermore, independent from anyone else, a VLAN can't assess your activity for dangers. Genuine Zero Trust system division requires an endeavor security stage that comprehends your applications and the clients.
In our illustration, the trust limits are placed either on or outside to the server farm border. A DMZ and SSL VPN apparatus give assurance from unapproved access; however they do little once a risk operator enters the server farm system. Generally associated gadgets have full get to the server farm organize once the client confirms. The presumption here is that edge controls anticipate unapproved access to framework assault surfaces, an awful supposition. At long last, the level server farm system is one substantial telecast space. Any gadget sending an ARP show searching for an IP address in the server farm will get an answer if the location is allocated to a dynamic server or other gadget. At the end of the day, an assailant can see all servers in the server farm. This gives potential access to each framework assault surface. With enough time and the right abilities, it is just a matter of time before a focused on assault surface breaks. System division with virtual neighborhood (VLANS) makes a gathering of separated systems inside the server farm. Each one system is a different telecast area. At the point when appropriately designed, VLAN division extremely frustrates access to framework assault surfaces. It decreases parcel sniffing abilities and builds risk operator exertion. At last, approved clients just "see" the servers and different gadgets important to perform their day by day assignments.
An alternate playing point of division is convention partition. System designers can restrict certain conventions to specific portions of the endeavor. For instance, if IPX or AppleTalk frameworks exist on your wire, they can each one have their VLAN in which to work.
At last, utilization of VLANS empowers secure, adaptable client versatility. For instance, a client allotted to a particular VLAN will dependably interface with that VLAN paying little mind to area. This is especially useful when outlining remote obligations. This obliges, be that as it may, that you have something like 802.1x running for port authentication. With802.1 xs, you can utilize a RADIUS server and your client aggregates in LDAP or Windows Active Directory to dole out the fitting VLAN rapidly to the client or gadget. Generally, a client discovering a statically designed port allotted to an alternate VLAN can get access get to just by connecting to. Most remote frameworks allocate a VLAN by coupling it with a particular SSID.
Basic traffic management concepts
In machine systems administration, system movement control is the procedure of overseeing, prioritizing, controlling or lessening the system activity, especially Internet data transmission, e.g. by the system scheduler. It is utilized by system directors, to diminish clogging, inactivity and parcel misfortune. This is a piece of transfer speed administration. To utilize these instruments successfully, it is important to measure the system activity to focus the reason for system clogging and assault those issues particularly.Various programming instruments are accessible to measure system activity. A few devices measure movement by sniffing and others utilize SNMP, WMI or other nearby executors to measure data transfer capacity use on individual machines and switches. Be that as it may, the last for the most part don't identify the kind of movement, nor do they work for machines which are not running the essential operator programming, for example, rebel machines on the system, or machines for which no perfect executor is accessible. In the recent case, inline machines are favored. These would by and large "sit" between the LAN and the LAN's passageway point, for the most part the WAN or Internet switch, and all parcels leaving and entering the system would experience them. As a rule the apparatus would work as an extension on the system with the goal that it is imperceptible by clients. Estimation instruments for the most part have these capacities:
- Client interface (web, graphical, comfort)
- Ongoing movement diagrams
- System action is regularly reported against preconfigured movement matching guidelines to show:
- Nearby IP address
- Remote IP address
- Port number or convention
- Logged in client name
- Data transfer capacity quantities
- Help for activity forming or rate restricting (covering with the system movement control page)
- Help site blocking and substance sifting
- Cautions to inform the manager of intemperate use (by IP address or altogether)
Configure and verify VLANS:
Virtual LANS inside an exchanged neighborhood give division and compelling system administration and security. System Engineers have the adaptability of portioning their system into independent VLANS as indicated by work bunches, office separation or even application use without stressing over the physical area of the hosts. Also, because of the way that each one host is connected to a solitary VLAN on the switch, included security is attained.
Every VLAN comprises of a differentiated show area. Which implies that just ports fitting in with a particular VLAN offer shows disposing of unnecessary movement from flooding the whole system; subsequently enhancing the general execution of the system.
At this point, you're most likely feeling that your VLANS can spread through a few building bases. Well get this ... VLANS can likewise develop their presence crosswise over Wide Area Networks (Wans) utilizing a layer 2 passage. This is the reason VLANS might be planned without respect of the physical area of the hosts. This is additionally why VLANS are for all intents and purpose the coolest LANS out there. Cisco impetus switches help Dynamic VLANS by utilizing a VLAN Management Policy Server with a specific end goal to allocate particular VLAN Ids to relating MAC addresses. Generally, Static task of VLANS to switch ports is designed. To have the capacity to do thus, initially, all diverse VLAN subnets need to be characterized. Subsequently, VLAN Ids could be doled out to switch ports and a have that appends on a given port consequently accept the VLAN participation of that port. When a VLAN enrollment is without a doubt, a host can convey to different has inside the same VLAN. In the event that steering between diverse VLANS is obliged then a switch needs to be joined in the system. A host connection can have admittance to one and only VLAN. A connection that can convey more than one VLAN labeled edge is known as a trunk and the technique for distinguishing a few diverse VLANS on a trunk is called labeling. Cisco used to backing its own particular exclusive trunking convention for VLAN labeling - ISL, or Inters witch Link Protocol. Nonetheless, ISL is not backed any longer and Cisco recommends utilizing IEEE 802.1q convention.
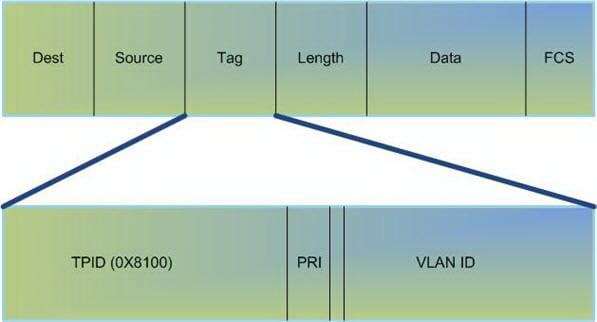
The IEEE 802.1q header contains a 4-byte label header containing a 2-byte convention identifier (TPID) and 2-byte control data (TCI). The TPID has a settled estimation of 0x8100 that shows that the casing conveys the 802.1q/802.1p label data.
The TCI contains the accompanying components:
- Three-bit client necessity
- One-bit authoritative organization marker (CFI)
- Twelve-bit VLAN identifier (VID) which remarkably distinguishes the VLAN to which the edge has a place
Configuring a LAN:
Designing VLANS is entirely simple. The trouble is to choose which clients ought to fit in with which VLAN. When you've chosen this and pictured the VLAN empowered system, then you are prepared to make your VLANS on the Cisco impetus switch. The switch port mode order might be designed utilizing 4 separate choices:
- Trunk: The interface is designed into changeless trunking mode and arranges with the accomplice site interface to set up the into trunk mode.
- Access: Disables port trunk mode; no trunking transaction happens.
- Dynamic attractive: Enables interfaces persistent endeavor to change over the connection to a trunking connection. The interface turns into a trunk interface if the neighboring interface is situated to trunk, attractive, or auto mode. This is the default mode for all Ethernet interfaces.
- Dynamic auto: Makes the interface to turn into a trunk just if the associated port is situated to trunk or alluring.
Verifying the VLAN:
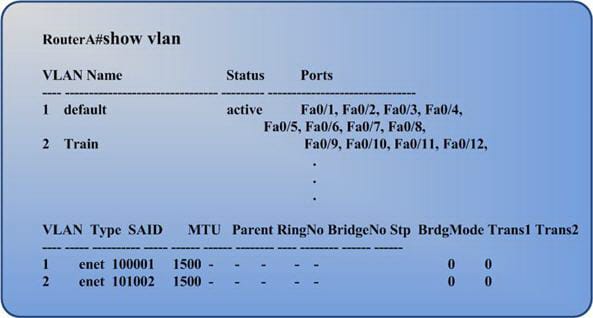
Utilize the show VLAN charge to check your VLAN setup. This command shows all switch ports and their related VLAN and the VLAN status and some additional parameters that identify with Token Ring and FDDI trunks.
You can utilize the show VLAN id [vlan#] charge to see data around a specific VLAN. Beneath you can see an example yield of the show vlan command.
Troubleshooting VLAN:
Three primary steps need to be emulated when troubleshooting VLAN issues:
The primary thing you have to do is to verify that your link and switch port are great. Continuously begin your troubleshooting strategy by exploring your physical network. Test your link and verify its working. Check the switch ports connection LED to verify that layer 1 is working legitimately.
Next, check your switches' interface design. Utilize the order show interface [interface name-number] to check whether there are CRC lapses or late crashes saw on the interface.
These lapses are generally the consequence of physical issues, for example, terrible link or NIC however can likewise show duplex jumble with the connected gadget. If you perceive that crashes are expanding consistently, then search for a duplex befuddle issue or for a blockage on the connection.
If it happens that two hosts can't convey then weigh whether they are in the same VLAN. In the event that they are situated into diverse VLANS then you unquestionably require a switch to have the capacity to empower correspondence between the two hosts. On the off chance that a host is not equipped to interface with the switch, verify the host has a place with the same subnet as the switches VLAN.
So VLAN is the one of the most important parts in networking. It contains many types as well and they should be understood by one in order to make sure that the one learning about them has mastered the field of networking.
Site Search:






