- Home
- Popular IT Certifications
- How to Configure and Verify Switch Port Security
How to configure and verify Switch Port Security
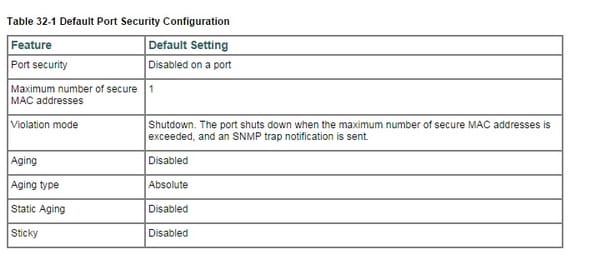
You can utilize the port security peculiarity to limit information to an interface by restricting and distinguishing MAC locations of the workstations that are permitted to get to the port. When you dole out secure MAC locations to a protected port, the port does not forward parcels with source addresses outside the gathering of characterized locations.
On the off chance that you restrict the quantity of secure MAC locations to one and allot a solitary secure MAC address, the workstation connected to that port is guaranteed the full data transfer capacity of the port. On the off chance that a port is designed as a protected port and the most extreme number of secure MAC locations is arrived at, when the MAC location of a workstation endeavoring to get to the port is not quite the same as any of the recognized secure MAC addresses, a security infringement happens.
After you have set the most extreme number of secure MAC addresses on a port, the safe locations are incorporated in a location table in one of these ways:
- You can arrange all protected MAC addresses by utilizing the switch port port-security MAC address MAC_address interface arrangement command.
- You can permit the port to alterably arrange secure MAC addresses with the MAC locations of associated gadgets.
- You can arrange various addresses and permit the rest to be alterably designed.
You can arrange an interface to change over the dynamicMAC locations to sticky secure MAC addresses and to add them to the running setup by empowering sticky learning. To empower sticky learning, enter the switch port port-security MAC address sticky order. When you enter this charge, the interface changes over all the dynamic secure MAC locations, including those that were progressively adapted before sticky learning was empowered, to sticky secure MAC addresses. The sticky secure MAC locations don't consequently get to be some piece of the design record, which is the startup arrangement, utilized each one time the switch restarts. In the event that you spare the sticky secure MAC addresses in the design record, when the switch restarts, the interface does not have to relearn these locations. In the event that you don't spare the design, they are lost. If the sticky learning is crippled, the sticky secure MAC locations are changed over to dynamic secure locations and are expelled from the running setup.
After the most extreme number of secure MAC locations is designed, they are put away in a location table. To guarantee that a connected gadget has the full data transmission of the port, arrange the MAC location of the appended gadget and set the most extreme number of locations to one, which is the default. A security infringement happens if the greatest number of secure MAC addresses has been added to the location table and a workstation whose MAC location is not in the location table endeavors to get to the interface. You can design the interface for one of these infringement modes, in light of the move to be made if an infringement happens:
- Restrict-port security infringement confines information, causes the Security violation counter to addition, and reasons a SNMP Notification to be produced. The rate at which SNMP traps are created might be controlled by the SNMP-server empower traps port-security trap-rate charge.
- shutdown-A port security infringement causes the interface to close down promptly. At the point when a safe port is in the mistake debilitated state, you can bring it out of this state by entering the errdisable recuperation cause psecure-infringement worldwide arrangement charge or you can physically reenable it by entering the shutdown and no close down interface design charges. This is the default mode.
You can likewise modify the time to recoup from the pointed out mistake impair reason (default is 300 seconds) by entering the err disable recuperation.
Sticky MAC
PersistentMAC adapting, otherwise called sticky MAC, is a port security offer that permits maintenance of progressively learned MAC addresses on an interface crosswise over restarts of the switch (or if the interface goes down). PersistentMAC location learning is handicapped as a matter of course. You can empower relentless MAC location adapting in conjunction with MAC constraining to confine the quantity of determined MAC addresses. You empower this peculiarity on interfaces.
To arrange tenacious MAC adapting on an interface first, anticipate movement misfortunes for trusted workstations and servers in light of the fact that the interface does not need to relearn the locations from entrance activity after a restart. Use tenacious MAC adapting in consolidation with MAC restricting to secure against assaults, for example, Layer 2 refusal of administration (Dos) assaults, flood assaults on the Ethernet switching table, and DHCP starvation assaults by constraining the MAC locations permitted while even now permitting the interface to progressively take in a detailed number of MAC locations. The interface is secured in light of the fact that after the farthest point has been arrived at; extra gadgets can't join with the port. By empowering tireless MAC adapting alongside MAC restricting, you can permit interfaces to learn MAC locations of trusted workstations and servers amid the period from when you associate the interface to your system until the utmost for MAC locations is arrived at, and guarantee that after this starting period with the cutoff arrived at, new gadgets won't be permitted regardless of the fact that the switch restarts. The plan B to utilizing diligent MAC learning with MAClimiting are to statically arrange every MAC address on each one port or to permit the port to ceaselessly learn new MAC addresses after restarts or interface-down occasions. Permitting the port to consistently learn MAC locations speaks to a security hazard.
MAC address limitation
MAC constraining for port security ensures against flooding of the Ethernet switching table (otherwise called the MAC sending table or Layer 2 sending table). You empower this peculiarity on interfaces (ports). MAC move constraining locates MAC development and MAC satirizing on access interfaces. You empower this peculiarity on VLANs.one technique to improve port security is to situate the greatest number of MAC addresses that could be learned (added to the Ethernet switching table) on any of the accompanying:
- A particular access interface (port)
- All right to gain entrance interfaces
A particular access interface on the premise of its participation inside a particular virtual LAN (VLAN enrollment MAC limit)another strategy to upgrade port security is to design particular MAC addresses as permitted MAC addresses for particular access interfaces. Any MAC address that is not in the rundown of the designed locations is not learned and the switch logs a message. Permitted MAC ties MAC locations to a VLAN so the location does not get enrolled outside the VLAN. In the event that a permitted MAC setting clashes with an dynamicMAC setting, the permitted MAC setting takes precedence.MAC move constraining causes the switch to breaking point and track the recurrence with which a MAC location can move to another interface (port). It can help avert MAC satirizing, and it can likewise locate and avoid loops. If a MAC location moves more than the arranged number of times inside one second, the switch performs the designed activity. You can arrange MAC move restricting to apply to all VLANs or to a particular VLAN.
Static/dynamic
AdynamicMAC location is one that has been scholarly by means of an ARP demand. In the event that a switch takes in the MAC address from an alternate gadget then it has rapidly sourced the MACaddress. StaticMAC is a MAC you arranged on the switch vs dynamic which is one learnt from the SRCMAC include field in the Ethernet casing crossing the switch.
However there are likewise exceptional MAC locations utilized by the switch for interior purposes which are additionally static like the one utilized for making up extension id utilized within STP (while doing a show MAC they show up with a CPU alongside them).a Static MAC location is one that has been manually include (wrote through an order) into the CAM or MAC location table. AdynamicMAC location is one that has been educated by means of an ARP demand.
Violation modes
A security infringement happens in both of these circumstances:- When the most extreme number of secure MAC locations is arrived at on a safe port and the source MAC location of the entrance movement is not quite the same as any of the distinguished secure MAC locations, port security applies the designed infringement mode.
- if activity with a protected MAC address that is designed or adapted on one safe port endeavors to get to an alternate secure port in the same VLAN, applies the arranged infringement m
I. err disable
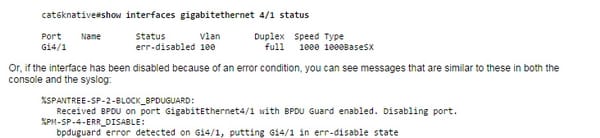
On the off chance that the design demonstrates a port to be empowered, however programming on the switch identifies a mistake circumstance on the port, the product close down that port. At the end of the day, the port is naturally incapacitated by the switch working framework programming as a result of a mistake condition that is experienced on the port. At the point when a port is slip impaired, it is successfully closed down and no activity is sent or got on that port. The port LED is situated to the shade orange and, when you issue the show interfaces charge, the port status shows blunder incapacitated. Here is an illustration of what a mistake incapacitated port looks like from the command line interface (CLI) of the switch:
II. shutdown
Cisco routers like junipers, and hence they don't have any command for shut down. So they can be turned off by simply unplugging them.
III. protect restrict
Port-security is a peculiarity in Cisco switches to confine get to on a specific port. MAC locations are utilized to channel and keep up access. I accept that the primary two goals accomplished with this system are:
- Alertly control the quantity of associated nods which is imperative to stop MAC-location table harming assaults. This assault happens when the MAC location table is full, this will drive the switch to go about as a center in the sense it will begin flooding movement to all associated ports. Consequently, an aggressor associated with a solitary port will then have the capacity to sniff movement from all different ports as well. To secure the switch against this assault, port-security is utilized to situate a most extreme number of acknowledged MAC-addresses. In the event that the number is agreed, the port could be modified to either closed down or dismiss new MAC-addresses.
- Acknowledge predefined gadgets. This will limit port access to a predefined number of nods focused around their MAC-addresses.
Shutdown unused ports
This will help shutting down all the ports which isn't being used;
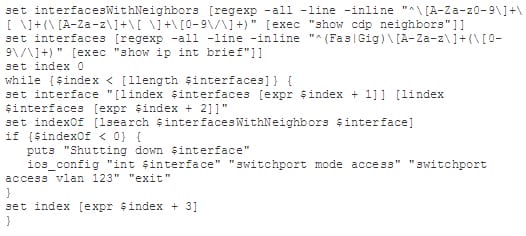
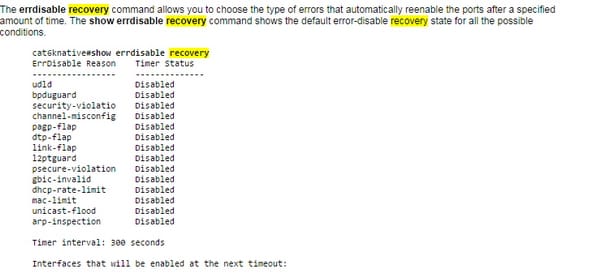
Err disable recovery
This s how disabled ports are enabled;
Assign unused ports in unused VLANs
Use following command for this purpose;
Putting Native VLAN to other than VLAN 1
NativeVLAN is really to a greater extent a security concern than a security profit. It is a decent thought not to utilize a nativeVLAN whatsoever. One approach to achieve this is to situate it to something that isn't generally utilized. It is additionally a decent practice to transform it from the default nativeVLAN of 1. Taking into account what you have expressed, I think you really have a decently clear understanding. I think the nativeVLAN was kind of for retrogressive similarity. Envision this- -
IEEE is really kind of regressive similarity and center points used to be more regular than switches.
Hence it is clear that switch port security is very important element in networking. The reason behind this is explained in this article. So those looking to have future in field of networking should get their hands on this technology. By this, he will have the skills and knowledge which are the basic requirement of any job which concerns the networking and ports security.
Site Search:






