- Home
- Popular IT Certifications
- NAT: Basic Operation and Concepts
The concepts of basic operation of NAT
In computer administration, system address interpretation (NAT) gives a method of altering system address data in Internet Protocol (IP) datagram bundle headers while they are in travel over an activity routing gadget with the end goal of remapping one IP address space into an alternate.
Starting 2014 NAT works most usually in conjunction with IP disguising, which is a method that conceals a whole IP address space - normally comprising of private system IP addresses (RFC 1918) - behind a solitary IP address in an alternate, typically open address space. Merchants execute this system in a routing gadget that uses interpretation tables to guide the "concealed" addresses into a solitary IP address and that readdresses the cordial Internet Protocol parcels on passageway so they seem to start from the routing gadget. In the opposite correspondences way, the switch maps reactions once again to the beginning IP address utilizing the principles ("state") put away in the interpretation tables. The interpretation table principles made in this manner are flushed after a brief time unless new movement revives their state. The strategy empowers correspondence through the switch just when the discussion begins in the disguised system, since this builds the interpretation tables. Case in point, a web program in the disguised system can scan a site outside, yet a web program outside cannot search a site facilitated inside the disguised network. On the other hand, most NAT gadgets today permit the system chairman to design interpretation table entrances for changeless utilization. This peculiarity is regularly alluded to as "static NAT" or port sending - it permits movement beginning in the "outside" system to achieve assigned has in the disguised system. As a result of the notoriety of this procedure to ration Ipv4 address space, the term NAT has ended up practically synonymous with the strategy for IP disguising. As system address interpretation alters the IP address data in bundles, it has genuine results on the Nature of Internet network and requires cautious regard for the subtle elements of its execution. NATusage fluctuates broadly in their particular conduct in different tending to cases and in their impact on system activity. Merchants of supplies containing usage don't normally report the specifics of NAT behavior. The least difficult sort of NAT gives a balanced interpretation of IP address. RFC 2663 alludes to this kind of NAT as essential NAT, which is frequently likewise called a coordinatedNAT. In this kind of NAT, just the IP addresses, IP header checksum and any more elevated amount checksums that incorporate the IP address are changed. Fundamental NATs could be utilized to interconnect two IP organizes that have contradictory tending to.
It is regular to shroud a whole IP address space, normally comprising of private IP addresses, behind a solitary IP address in an alternate, typically open, address space. To maintain a strategic distance from uncertainty in the treatment of returned bundles, a one-to-numerous NAT must modify extra data, for example, TCP/UDP port numbers in friendly interchanges and must keep up an interpretation table so that return parcels could be accurately tended to the starting host. RFC 2663 uses the term system address and port interpretation (NAPT) for this kind of NAT. Different names incorporate port address interpretation (PAT), IP disguising, NAT over-burden and a lot of people to-one NAT. This is the most widely recognized sort of NAT, and has gotten to be synonymous with the term NAT in as something to be shared utilization. As portrayed, the technique empowers correspondence through the switch just when the discussion begins in the disguised system, since this builds the interpretation tables. Case in point, a web program in the disguised system can skim a site outside, yet a web program outside couldn't search a site facilitated inside the disguised system. In any case, most NAT gadgets today permit the system head to arrange interpretation table sections for changeless utilization. This peculiarity is regularly alluded to as "static NAT" or port sending and permits activity beginning in the "outside" system to achieve assigned has in the disguised system.
The greater part of NATs guides various private hosts to one openly uncovered IP address. In a normal setup, a neighborhood system utilizes one of the assigned "private" IP address subnets (RFC 1918). A switch on that system has a private address in that address space. The switch is likewise joined with the Internet with an "open" address doled out by an Internet administration supplier. As movement passes from the neighborhood system to the Internet, the source address in every parcel is interpreted on the fly from a private address to people in general address. The switch tracks fundamental information about every dynamic association (especially the end address and port). At the point when an answer comes back to the switch, it utilizes the association following information it put away amid the outbound stage to focus the private address on the inner system to which to forward the answer. All datagram parcels on IP systems have a source IP address and a terminus IP address. Ordinarily bundles passing from the private system to the general population system will have their source address adjusted while parcels passing from people in general system over to the private system will have their objective address altered. More intricate setups are additionally conceivable.
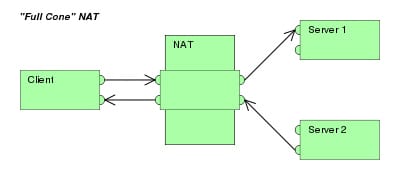
To evade equivocalness in how to interpret returned parcels, further alterations to the bundles are needed. The immeasurable majority of Internet movement is TCP and UDP bundles, and for these protocols the port numbers are changed so that the synthesis of IP and port data on the returned parcel could be unambiguously mapped to the comparing private address and port data. Protocols not focused around TCP or UDP oblige other interpretation systems. ICMP parcels ordinarily identify with a current association and need to be mapped utilizing the same IP and port mappings as that connection. There are a few methods for executing system address and port interpretation. In some application protocols that utilization IP address data, the application running on a hub in the disguised system needs to focus the outside address of the NAT, i.e., the address that its correspondence companions distinguish, and, moreover, regularly needs to look at and arrange the sort of mapping being used. Generally this is carried out on the grounds that it is craved to situate up an immediate interchanges way (either to spare the expense of taking the information by means of a server or to enhance execution) between two customers both of which are behind divided NATs. For this reason, the Simple traversal of UDP over NATs (STUN) protocol was created (RFC 3489, March 2003). It arranged NAT execution as full-cone NAT, (address) limited cone NAT, port-confined cone NAT or symmetric NAT and proposed a strategy for testing a gadget appropriately. Notwithstanding, these strategies have following been expostulated from models status, as the routines have demonstrated defective and insufficient to effectively survey numerous gadgets. New strategies have been institutionalized in RFC 5389 (October 2008) and the STUN acronym now speaks to the new title of the determination: Session Traversal Utilities for NAT.NAT traversal issue emerges when two companions behind unique NAT attempt to convey. One approach to tackle this issue is to utilize port sending, an alternate path is to utilize different NAT traversal systems. The most well-known strategy for TCP NAT traversal is TCP gap punching, which requires the NAT to take after the port safeguarding configuration for TCP, as clarified beneath.
Numerous NAT executions take after the port protection plan for TCP: for a given friendly TCP correspondence, they utilize the same values as inside and outside port numbers. NAT port conservation for friendly TCP associations is critical for TCP NAT traversal, on the grounds that as TCP obliges that one port must be utilized for one correspondence at once, projects tie different TCP attachments to transient ports for every TCP correspondence, rendering NAT port expectation inconceivable for TCP. Then again, for UDP, NATs don't have to have port protection. Surely various UDP correspondences (each with a different endpoint) can happen on the same source port, and applications normally reuse the same UDP attachment to send bundles to unique hosts. This makes port expectation direct, as it is the same source port for every bundle. Moreover, port protection in NAT for TCP permits P2p protocols to offer less many-sided quality and less idleness in light of the fact that there is no compelling reason to utilize an outsider (like STUN) to find the NAT port since the application itself knows the NAT port.
Purpose
The term NAT44 is off and on again used to all the more particularly show mapping between two Ipv4 addresses; this is the run of the mill case while Ipv4 conveys the larger part of activity on the Internet. NAT64 alludes to the mapping of an Ipv4 address to an Ipv6 address, or the other way around. System chairmen initially utilized system address interpretation to guide each address of one address space to a comparing address in an alternate space, for example, when an association changed Internet administration suppliers without having an office to report an open course to the network.
Pool
A Network Address Translation Pool in straightforward terms is a pool that has been cut out of a dispensed addresshinders that doles out inside worldwide addresses on a first start things out serve premise to inside nearby have focused around a match found in a determined access control list. The profit of this kind of setup is that your inside system can utilize Rfc1918 private tending to, for example, the 10.0.0.0/8 territory yet at the same time acquire IP network to the outside world utilizing a solitary open IP address for every host. A few colleges utilize this strategy however the lion's share of colleges in the USA are moving more towards a NAC (Network Admissions Control) base of its private understudies to get to the web because of NAC being able to implement infection security and obliged working framework upgrades. However NAT pooling still has its place in today's systems, for example, the DMZ (Demilitarized Zone) or organizations that possess a piece of open IP addresses and requires each inside host to have its own particular interpreted outside IP address.
At the point when designing a NAT pool you must define a address pool range with a begin and end IP address took after by the system prefix of the designated IP address obstruct the IP address reach is cut out of . After the pool has been made you should then make the NATexplanation that uses a particular access control list that interprets ACL matched inside host machines to the outside worldwide IP addresses in the pool on a first start things out serve premise.
Static
A sort of NAT in which a private IP address is mapped to an open IP address, where the general population address is dependably the same IP address (i.e., it has a static address). This permits an inside host, for example, a Web server, to have an unregistered (private) IP address and still be reachable over the Internet.
1 to 1
Utilizing static NAT, you can forward one or all ports to a server behind your firewall. WatchGuard strays a bit from general security industry wording by utilizing the expression "static NAT" just to allude to sending one port to a solitary server, and utilizing the expression "1:1 NAT" to allude to sending one location to a solitary server. It is also known as the full cones NAT.
Overloading
NAT Overload is the most widely recognized NAT strategy utilized all through all systems that associate with the Internet. This is a direct result of the way it works and the restrictions it can succeed, and we'll investigate these in the following two pages. Whether you utilize a switch, firewall apparatus, Microsoft's Internet imparting capacity or any third gathering program that empowers all your home machines to join with the Internet through one association, you're utilizing NAT Overload.
Source addressing
Utilizing NAT to make an interpretation of private IP locations to open, and the other way around, is frequently called "disguising". At the point when designed thusly, the firewall changes the source IP location of every bundle sent by inward machines to the Internet, supplanting the private IP address with the location of its outside interface.
One way NAT
One way NAT is, when the NAT is set for only one single direction.
NAT is the very important part of the networking. So, those people who are willing to have future in the networking should know about NAT so they can increase their knowledge base.
Site Search:






