- Home
- Popular IT Certifications
- An Overview of Cryptography Basic Concepts
An Overview of Cryptography: Basic concepts

Cryptography basically means keeping information in secret or hidden. There are a number of features associated with cryptography. One is confidentiality which basically means that we need to be sure that nobody will see our information as it travels across a network. Authentication and access control is also another capability provided by cryptography. Some other capabilities provided by cryptography are non-repudiation and integrity which are explained below.
Symmetric vs. asymmetric
Symmetric and asymmetric encryptions are data encryption methods are being used in today's networks and computers. Symmetric encryption is a kind of encryption where one uses the same key to encrypt and decrypt the same information. This means that the same information is required or used during the encryption and decryption process. Being the same encryption key for both ends, it must be kept secret. This therefore means that if a person gets the key, he or she can read all the information that we had encrypted. In case they key gets lost, it is important that one replace it immediately. The security is a symmetric key is normally quite a challenge owing to the fact that one is not sure whether to t to many people or a single individual.
Symmetric encryption is currently being heavily used due to the fact that it is very fast to use. This is because of the fact that very few resources are required. With respect to this aspect, many people tend to combine both symmetric and asymmetric not only for security but also for a quick and efficient working.
Asymmetric encryption is another kind of encryption that one will come across. It is commonly referred to as public key cryptography since there are two keys that are needed. One of the keys will be a private key that one will have to keep it to one's self and not share it with others. There is also a public key which one can give to everyone. One can put it on a public server for instance. This is a key that everyone should have access to. The private key should only be available to one. This is due to the fact that the private key is the one that enables people to send one data in encrypted forms while the private key enables one to decrypt the information encrypted with a public key. This therefore means that no one can decrypt data using a public key.
With the combination of symmetric and asymmetric encryption, there is a lot of flexibility in terms of encrypting the data, sending it to other people and decrypting it.
Session keys
Session keys are special types of cryptographic keys that can only be used once. This means that if a session key encrypts some information at a particular time, it cannot be used again to encrypt any other information.
Fundamental differences and encryption methods
Block vs. streamBlock cipher encryption entails taking one full block of information and encrypting it as a full block all at the same time. In most cases, the blocks are normally of 64-bits or 128-bits. This means that their size is predetermined and remains the same during encryption and decryption. When using the block cipher method, one needs to ensure that to have some confusion so that the encrypted data seems far much different. When using the block ciphers one can also implement the diffusion concept where the output becomes totally different from the input.
Stream cipher is another kind of encryption that is used with symmetric encryption. Contrary to block where all the encryption is done all at once, encryption in stream ciphers is done one bit at a time. This is a type of encryption that can run at a very high speed and requires low hardware complexity. An important aspect to know when using stream ciphers is that the initialization vector should never be the same when one are starting to do some of the streams because someone may easily figure out the initialization vector and encryption key one are using and use it every time one send data across the network. Make sure that one's initialization vector is always changing when one are using it to encrypt information.
Transport encryption
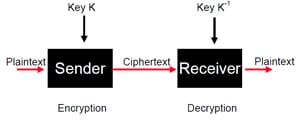
Transport encryption is an aspect of cryptography that involves encrypting data that is in motion. In this case, one has to ensure that data being sent across a network cannot be seen by other people. In addition, the encryption keys should not be visible to others. Transport encryption can be implemented with the use of a VPN concentrator. If one is outside one's office, one will use some software to send data to the VPN concentrator where it will be decrypted and then sent to one's local network in a manner that it can be understood.
With this kind of encryption, it becomes very difficult for an individual to tap into one's network and look into a conversation between two workstations since the information is already scrambled up.
Non-repudiation
Non-repudiation means that information that we have received cannot be attributed to someone else and there is no way they can take it back. In terms of cryptography, we add a different perspective to that where we can add a proof of integrity so that we know that the information we received is intact and we can be sure that the information we received came from the source.
With this, one can also have a proof of origin where one has high assurance that the origin of the information is authenticated from the source.
Hashing
A cryptographic hash is a way of taking existing data, a file, picture, email or text that one have created and create a string of message digest from it. If one wants to verify a cryptographic hash, one can send the message to another person and ask him to hash it and if the hashes match, then the file is the same on both sides.
An important characteristic of hashing is a one-way trip. This means that one cannot look at the hash and figure out what the original text was. This is a method that is used to store passwords since if someone gets the hash, he or she cannot figure out the original password.
A hash can also act as a digital signature in that it can offer some authentication of one's files and data. It also ensures that the data one receives has integrity. This therefore means that one does not have to encrypt all one's information.
One should also make sure that the hashes have no collision. This basically means that two different messages containing different information cannot have the same hash.
Key escrow
Basically, when we are talking about escrow we are talking about a third party that is holding something for us. In the context of cryptography, this refers to the encryption keys. In this case, it requires that a third party stores the encryption key so that we can decrypt information in case the original key gets lost. In this case, the encryption key should be kept in a very safe place so that it is not accessed by others. Key escrow also helps when it comes to the recovery of data.
Symmetric encryption in the context of key escrow means that one are keeping one's key somewhere making sure that it is put in a safe so that no one can get access to it.
Asymmetrical encryption in this case means that one need to have an additional private key that one can use to decrypt information. The process of getting to the key escrow is as important as the key since so have to be aware of what circumstances can prompt one to get the key and who can access the key. Having the right process in place and one have the right ideas behind what one are doing with the key escrow, it then becomes a valuable part of maintaining the integrity and security of one's data.
Steganography
Steganography is a way of encrypting or hiding information but one still has the information in plain sight all the time. This is a way to secure things by making them obscured which in reality is not security. Messages appear invisible but it is right there before one. In other cases, it may be embedded within pictures, sounds and documents. This means that in such a case, all that we see is the cover text of that is above the hidden information.
One way of implementing steganography is by hiding the information in network packets. It is obvious that packets move really fast and therefore it is possible to send a lot of information that is embedded in the packets.
One can also use an image in steganography. This means that one can embed one's information in the image itself.
Digital signatures
In cryptography, digital signatures are used to check for non-repudiation. This basically means that we are digitally signing a message or file. In this case, no type of encryption on the message is required since with the digital signature, an individual is in a position to verify that the message came from one and was not changes in the course. One can sigh it with one's private key and people to whom one have sent the message will use one's public key so as to verify that the message was from one. This is the important bit of having public keys in that one are in a position to verify the senders of the various messages one receives.
If one verify a digital signature with its source, then one are assured that the file or piece of information has not undergone any changes in between the sender and the receiver.
Use of proven technologies
There are many different ways through which people can implement cryptography. In most case, people might not be familiar with the most cryptographic technologies and in this case, they are advised to use proven technologies to encrypt their data. In this case, people reduce their over reliance on the most common data encryption types. In addition, with the use of proven encryption technologies, one is able to have a wide range from which one can choose from.
Elliptic curve and quantum cryptography
The Elliptic curve cryptography is an emerging technology in cryptography. This is a technology that was created so as to deal with the numerous constraints associated with asymmetric encryption such as numerous mathematical numbers. This cryptography method uses curves instead of numbers where each curve has a mathematical formula associated with it.
Quantum cryptography is also another emerging technology in cryptography. Just as the name suggest, this is a technology that employs the use of quantum physics and applying that into the calculations and methods of encryption we are doing inside of our cryptography.
Ephemeral key
Ephemeral keys are special types of cryptographic keys that are generated so as to execute each key establishment process. There are cases where an ephemeral key is used more than once in a single session especially in cases where only one ephemeral key pair is generated for each message.
Perfect forward secrecy
Perfect forward secrecy is also another kind of cryptographic technology whose main aim is to ensure that information or rather data packets being sent across a network are sent with top level secrecy so as to avoid detection. In this case, such packets are normally sent when there is a lot of traffic travelling through a network since it is very difficult to identify a specific packet if the transmission is fully loaded.
Generally, cryptography is a technology whose use and implementation is rapidly increasing. This is because it is a very good method of ensuring information safety. Through cryptography, any piece of information can be encrypted or written in such a manner that it can be very difficult for another person to read if he or she is not able to decrypt it.
Site Search:






