- Home
- Popular IT Certifications
- How to Configure/ Verify Switch Security Features
How to configure and Verify Switch Security features
The Cisco security features help to develop a secure network infrastructure. The IOS software by Cisco performs critical functions to provide layers of security. Following are the features of Cisco IOS security:
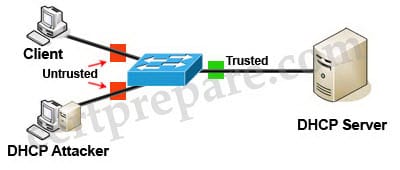
1. DHCP Snooping
DHCP Snooping serves like firewall between trusted and mistrusted servers only related to DHCP. It actually acts like an element of security. It has the following activities:
- It helps in filtering mistrusted messages which are received from the servers.
- It provides with a rate-limit from trusted and mistrusted servers, only related to DHCP.
- It constructs the snooping binding database of DHCP, which actually consists of data related to the mistrusted hosts with hidden IP addresses.
- It uses the snooping binding method of the DHCP database to check for the mistrusted hosts that have tried to venture in.
- Dynamic ARP is another security feature which utilizes the information kept in the DHCP snooping binding database.
- The DHCP snooping characteristic is applied in the software on the MSFC. So that all the messages of DHCP are sent in the PFC and headed to the MSFC's for processing purposes.
Binding database:
DHCP snooping trait is such a dynamic feature that it constructs and maintains the database by utilizing the data taken out from the intercepted DHCP messages. The database consists of an entry of each of the mistrusted hosts with a leashed IP address, only on the condition if it is associated with a VLAN that has DHCP snooping working on it. The database does not consist of entries of trusted hosts which are linked through trusted interfaces. The DHCP snooping trait updates the database whenever specific DHCP messages are delivered to the switch. For example, when a DHCPACK message is delivered to the switch this feature adds an entry in the database. On the other hand, it also removes the entry in the database as soon as the IP address lease is expired or when the host delivers a DHCPRELEASE message.
Packet validation:
Once the DHCP snooping is enabled the switch validates the DHCP packets which are received on the mistrusted interfaces of VLAN's. Unless any of the conditions listed below occur, the witch forwards the DHCP packet. If any of these conditions take place, the packet is dropped.
- A DHCP server outside the network or firewall delivers a packet to the switch such as DHCPOFFER, DHCPACK, DHCPLEASEQUERY or DHCPNAK.
- And if a mistrusted interface receives a packet and the MAC address and the DHCP address do not match. If the MAC address verification option is turned on this check will happen only then.
Database Agent:
The DHCP snooping agent should be used to keep hold of the bindings over reloads. If this option is not enabled the bindings developed by DHCP snooping would be lost upon reload and the connectivity will also be lost. The bindings are stored in a file at a configured location by the database. When it is reloaded the switch goes through the file to build the database for the bindings. As the database changes the switch keeps updating the file.
Restrictions:
The following restrictions should be noted down while configuring the DHCP snooping:- DHCP snooping is not supported by PFC2.
- Only Releases before 12.2(18)SXF5 store maximum of 512 bindings, if the bindings exceed than that the bindings are removed from the database.
- At least 8000 bindings can be stored on DHCP snooping database with Releases after 12.2(18)SXF5.
IP Source Guard
IP Source Guard protects a legitimate host being taken over by any malicious host by providing source IP address filtering on Layer 2 port. This trait uses amazing DHCP snooping and IP source binding to counterpart the IP addresses to hosts on mistrusted Layer 2 access ports. Except for the DHCP packets, all the IP traffic is blocked in the beginning. The traffic with that IP source address is only given permission from the client after the client gets an IP address from the DHCP server.
Channel ports:
The port members do not support the IP source guard; it is only supported on the main Layer 2 channel interface. Once the IP source guard is implemented on the main Layer 2 channel interface, it automatically applies to the rest of the members of the ports.
Trunk Ports:
Trunk ports do not support IP source Guard.
Layer 3 and Layer 3 Port conversion:
Once the layer 3 port is applied instead of the layer 2 ports, the IP source guard policy does not function but still is present in the configuration. Once the port is changed to Layer 2 port, it starts working again.
Voice VLAN and IP source guard:
A layer 2 port supports an IP source guard that belongs to the voice VLAN. A switch voice vlan command is used to validate the voice VLAN for the layer 2 port. DHCP snooping should be enabled for the IP Source guard to work on the VLAN command. To merge the IP source guard feature with the VACL and Cisco IOS ACL the merge mode is used.
IP Source Guard Restrictions:
In case incomplete hardware resources are provided the IP source Guard feature cannot be applied since it is only supported in hardware. Other ACL features used these hardware resources. The restrictions listed below apply to IP source guard:
- Supported by ingress Layer 2 ports.
- Supported with sufficient hardware.
- Any traffic that is processed in software cannot utilize it.
- Traffic filtering cannot be done on MAC address.
- Private VLAN'S do not support it either.
Dynamic ARP Inspection:
Invalid ARP packets are immediately rejected by dynamic ARP inspection. This feature protects the traffic from getting stuck due to any malicious attack in the middle of the traffic blocking the ARP caches. The troublemaker delivers ARP requests by mapping another stations IP address to its own MAC address.
Once the DAI is enabled, and if the sender MAC address and senders IP address are not the same, the switch immediately drops ARP packet in the DHCP snooping binding database. Other switches in the network do not process dynamic ARP inspection if static mappings are not used to figure out the static IP address. With the help of static mapping an IP address can be linked to a MAC address on VLAN.
ARP Packets:
To prevent the denial of service attack, the number of ARP packets is limited, and it also lets the switch CPU perform ARP inspection rechecks. Rate for mistrusted packets is 15 packets per second. Trusted interfaces do not need rate limitations. If you want to change this setting you can do that by using the ip arp inspection limit interface command.
The switch is replaced in the port in the error disabled state if the rate of the incoming ARP packets exceeds. Until you do something about it, the port will remain in that condition. To recover from the error disabled state you can use errdisable recovery.
Port security:
This feature can be used to bind the input to an interface by limiting and identifying MAC addresses of the workstations which can enter the port. To not let the port forward packets with source addresses outside the group of defined addresses, you need to assign a secure MAC address to a secure port. The full bandwidth of a port is assured if you limit the number of secure MAC addresses and assign a single MAC address. A security violation will occur if the limit is exceeded and the MAC address to the workstation differs. Once the maximum number of MAC addresses is secured they are added in an address table in one of the following ways:
- All secure MAC addresses can be configured by utilizing the switch-port security mac-addresses.
- With the MAC addresses of connected devices you can let the port discover secure MAC addresses.
- You can let the rest of the addresses to be dynamically configured, while you configure a number of addresses yourself.
Port security through sticky MAC addresses
This feature of port security provides similar benefits to that of static MAC addresses. However, sticky MAC addresses can be dynamically learned. Through stick Mac addresses; the port security retains the MAC addresses learned dynamically during the condition of link down.
After you enter a copy running config startup config or write memory command, the port security using stick MAC address will dynamically save the MAC addresses in startup configuration file. Then, the port would not need to learn addresses from the ingress after restart or bootup.
With Iphone
As the device is not connected to the switch directly, the switch is not able to physically detect the port link loss when the device is disconnected. However, the Cisco IP phones will send CDP host a TLV to warn the switch about the changes. With the help of Cisco IOS release, the switch can detect the presence of host TLV. After receiving the notification of TLV of the link down on the data port of IP phones, the post security eliminates from tables of address all the sticky and static learned MAC addresses
Post security guidelines and restrictions:
When you are going to configure a port security, go by the following guidelines:
- A secure port cannot be a trunk port.
- For a Switch port analyzer, a secure port can never be a destination port.
- An Ether channel port can never be a part of a secure port.
- Static MAC address configuration and secure port are collectively exclusive.
Default Port Security Configuration |
|
Feature |
Default Setting |
Port security |
Disabled on a port |
Maximum number of secure MAC addresses |
1 |
Aging |
Disabled |
Violation mode |
Shutdown. |
Aging type |
Absolute |
Sticky |
Disabled |
Static Aging |
Disabled |
Private VLAN:
The Private VLAN feature has two problems that service providers face when they use VLAN's.
Scalability: in this the switch supports up to 1005 active VALN'S. The number of customers that the service provider can support is limited when a server provides one VLAN per customer. Once IP routing is enabled it causes IP address management problems since VLAN is allotted a subnet address space. The usage of private VLAN's enhances the scalability problem and gives IP addresses management benefits for service providers and Layer 2 security for the clients.
Regular VLAN domains are partitioned into sub domains by private VLAN's, and they can have multiple VLAN pairs. Primary and secondary VLAN represent a sub domain. In a Private VLAN, all VLAN's pairs share the same primary VLAN. One sub domain is differentiated by a secondary CLAN ID.
Storm Control:
When a packet interferes the LAN a traffic storm is created because of which excessive traffic occurs and degrades the network performance. It prevents the LAN ports from being disturbed by a broadcast, uni-cast or multicast traffic storm on physical interfaces. The traffic suppression is checked continuously by monitoring the level of traffic over a 1 second interval and comparing it with the traffic level which you would have checked. The percentage of the total provided bandwidth of the port is the traffic storm control level. Every port has a single traffic control level which is used for them all.
Traffic storm control verifies the level of each traffic type and it helps you enable traffic storm control in 1 second traffic storm control intervals. The traffic storm level drops when the excess traffic for which the traffic storm control is enabled reaches the traffic
Storm control level
On the Catlalyst 6500 series the traffic storm control is applied in hardware. The packets passed from a LAN to a switching bus are monitored by the traffic storm control circuitry monitors. The packet is distinguished if it is unicast or broadcast, by using the group bit in the packet destination address. It keeps track of the packets counts between the one second interval and extracts the exceeded count of packets. Since hardware traffic storm control utilizes a bandwidth based method to measure traffic, the most important applied factor is setting the percentage of the total bandwidth that can be utilized by controlled traffic. Since, packets do not reach at uniform intervals; the one second interval in which the control traffic is calculated can affect the behavior of traffic storm control.
Site Search:






