- Home
- Popular IT Certifications
- Routing Troubleshooting Process Made Easy
Describe troubleshoot process for Policy-based routing,Suboptimal routing, Loop prevention mechanisms
As the technology is expanding day by day, we expect efficiently working networks. For this, the traditional routing protocol is a major concern. When a packet is received by a router, based on the destination address in the packet, router makes a decision where to forward it. Freedom to implement the forwarding and routing of the packet in a more flexible way is then required by various organizations. In today's eminently performing computer networking, based on guidelines set by the network administrator policy-based routing (PBR) is a technique used to make routing decisions. It provides an easy-going mechanism to customize the operation of the routing table that is to look up an entry and the traffic flow within their networks for the network administrators. Customers can put on some criteria that selectively cause the packets to take different paths with the help of policy-based routing. As in some situations, there comes need to forward the packet based on other requirements.
Troubleshooting policy based routing
An input to a system is expected to generate specific output. For example, selecting the 'play' option from any media player will result in starting of an audio/video file in any specific device. But any unexpected or undesirable behavior during this process is a symptom. And the process of isolating the specific root or causes of the symptom is known as troubleshooting. Often considerable effort and emphasis in troubleshooting is employed on reproducibility. Hence, one of the principles of troubleshooting is that reproducible obstacles can be reliably isolated and then resolved. With policy-based routing, based on the application of originating the traffic, policies to select the network that will be used for outbound traffic can be easily defined. The two common approaches used by troubleshooters are to check for frequently encountered difficulties and easily tested conditions. For example, checking to ensure that a sound button/display screen is on to play audio/video file is said to be of this type.
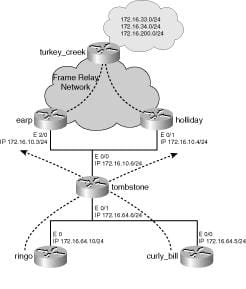
Policy Based Routing is a very commanding tool to control the specific paths of network traffic during packet forwarding. However, use only PBR when it is needed as it avoids destination based routing methods. This feature is designed for a specific set of circumstances and should be used for those purposes to maintain efficiency unlike other features. Other than just the destination IP address/ subnet, the TCP/IP stack in policy basic routing make the routing decisions that take into account the criteria including job name, source port, destination port, protocol type (TCP or UPD), Net Access security zone, MLS security label, and security address. Instead of the existing mechanism provided by routing protocols provides a more flexible mechanism for routing packets through routers. It uses some additional routing criteria both for static routes and dynamic routing. There will be situations in which more specific selection of routing paths can be advantageous while dynamic routing protocols provide easy development. By using a PBR-aware L3- switch (router) traffic can be redirected easily to a proxy server. In such development, specific source traffic can be redirected to a cache engine. Thus, policy based routing makes traffic marking a possibility. It offers some progressive features like selection and forwarding of traffic to discreet Virtual Routing Forwarding as well as Enhanced tracking of the accessibility of next-hops.
The destination address in the packet's IP header is matched to an entry in the router's routing table by the router when a packet arrives on an interface. And the router always routes packets addressed to a specific destination to the same next hop. Policy based routing requires a route map to implement the policy which can then be applied to each interface, but multiple entries for each route map can be configured. In short, the route map applies to traffic that arrives on the interface. Some policies to forward some traffic over one link and other traffic over other link can be formed when router connects to a site through more than one link. Usually, to balance the load, using a routing protocol is preferred.
However, one may want different types of traffic to travel over different paths, even when that traffic is heading to the same network to make network function optimally. The policy based routing technique also include some applications to enforce security, reserve a connection for specific traffic. The path that packets take through different router interfaces can be controlled effortlessly by selecting the traffic for PBR.
Each route map consists of a series of sequenced route map entries. And each route map entry is identified by a name and a sequence number. When the route map is applied to an interface, it is applied as an entire set, which includes all the route map entries with the same name and different sequence numbers. One or more match commands is entered in each route map entry which selects the traffic for PBR. Also one or more set commands may be entered, which determines how the selected traffic is routed or modified. The router begins to process the route map associated with the interface when a packet arrives on an interface. Starting with the entry that has the lowest sequence number, the router processes the entries. The processing of the set of route map entries is stopped as soon as router finds a match for the packet. When this match is made, the matched routes are modified by set commands which will alter the packet or the manner in which it will be routed. Hence, the sequence number assigned to a route map entry should be allocated precisely.
Troubleshoot suboptimal routing
Standard techniques for solving multicommodity problems can be established in the mathematical programming literature. However, the direct application of these techniques to the routing problem in computer networks proves to be computationally challenging. For that reason, considerable effort has been spent in developing practical techniques. The practical importance of routing tables follows from the fact that each table contains all the information required by the corresponding node for the routing of the incoming traffic. In real world networks, suboptimal routing is just not as much a problem as it may appear. There are many cases, especially in service providers, where there are good operational reasons for preferring the simplicity of methods that may result in suboptimal routing. Finally, the topology, rather than metrics, often is the thing that determines real world routing. OSPF prefers intra-area to inter-area to external which is also known as loop prevention. It is possible to identify the shortcomings of existing models and algorithms and to discuss the requirements of any superior approach.
The set of routes on which packets have to be transmitted in order to optimize a well-defined objective function is optimal routing policy. And the optimal routing problem in a computer network consists of the determination of the optimal routing policy. Under suitable assumptions, the optimal routing problem can be formulated as a nonlinear multicommodity flow problem. In fact, the algorithms for the determination of the optimal topology and channel capacities in a computer network involve hundreds of optimal routing computations. Therefore, an extremely fast routing technique has to be applied. Quite satisfactory results have been obtained and the computational efficiency has been greatly improved. However, all of these techniques are affected by a number of limitations. Taking advantages of these properties, a decomposition method is applied, in a significantly simplified form, and an algorithm for the exact solution is presented.
A very important instance of routing policy is the shortest route policy, which transmits packets along shortest routes computed according to a well-defined assignment of the length to the arcs. Suboptimal routing, especially in things like OSPF(Open Shortest path First) summarization, may lead to further stable networks and stability is often more operationally important than absolute best routing. When aiding multiple OSPF processes on a router, from the software perspective, the processes are independent. OPSF protocols, inside one OSPF process, always have a preference of internal route over the external route. Conversely, OSPF does not do any OSPF route selection between processes. Present-day internet routing is not optimal; in fact, it is at a considerable distance from being optimal. This is somewhat due to the embedded complexities and other difficulties of the routing problem but also due to the application of inappropriate routing models and the misapplication of algorithms based upon them. For example, OSPF metrics and route types are not taken into account, when determining the route of which process should be installed into routing table.
Troubleshooting loop prevention mechanisms
The three ways that can be used to prevent sub-optimal routing are manually setting administrative distance, routing tags, and using metric and metric types. There is no interaction between different OSPF processes, and the tie-breaker for this is the administrative distance. Thus, since both OSPF processes have a default administrative distance, the first process seeking to install that route makes it into the routing table. Therefore, administrative distance for routes from different OSPF processes must be organized so that routes of certain OSPF processes are preferred over routes of another process.
Route tagging and filtering
The OSPF inbound filtering using route maps with a distibute manual features allows users to define a route map to prevent OSPF routes from being added to the rounding table. In the route map, the user can match on any property of the OSPF route. Users can define a route map to prevent OSPF routes from being added to the routing table. This filtering occurs at the moment when OSPF is installing the route in the routing table. This attribute has no influence on flooding. In the route map, the user can match on any of the attribute of the OSPF route. That is, the route map could be based on the match options like interface, address, next-hop, route source, metric, route type, tag.This feature can be beneficial during redistribution if the user tags prefixes when they get redistributed.
Split Horizon
A router configured with a primary IP address and secondary IP addresses on a given interface behave in a different way when interfaced depending on whether split horizon is enabled or disabled. Because RIP functions by periodically flooding, thus, the entire routing table out to the network generates a lot of traffic. The split horizon and poison reverse techniques can help minimize the amount of network traffic originated by RIP hosts and make the transmission of routing information more efficient. RIP determines that those advertisments do not need to be retransmitted out the same interface if a router recieves a set of route advertisements on a particular interface.
Route poisoning
The technique which is known as split horizon, helps limit the amount of RIP routing traffic by eliminating information that other neighbours on that interface have already learned. When a router advertises a poisoned route to its neighbour, its neighbour break the rule of split horizon and send the same poisoned route back to the originator, called poision reverse. Babel applies split horizon to the wired links simply.
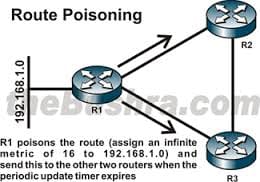
In the same way, the poison reverse technique helps to optimize the transmission of routing information and improve the time to reach network convergence. Split horizon can be attained by means of a technique called poision reverse. The main disavantage of poison reverse is that it can considerably increase the size of routing announcements in certain fairly common network topologies. But it allows for the enhancement of the overall efficiency of the network in case of faults. If router learns about unreachable routes through one of its interface it then directly advertises those routes as unreachable out of the same interface. This is the equivalent of the route poisioning in all possible reverse paths. That is, informing all routers that the path back to the originating node for a particular packet has an unlimited metric. Split horizon with poison reverse is more effective than simple split horizon in networks with multiple routing paths. Although it affords no improvement over simple split horizon in networks with only one routing path. Split horizon states that if a neighbouring router sends a route to a router, then the receiving router will not propogate this route back to the advertising router on the same interface. VPLS uses split horizon technique to avoid loops in the forwarding plane.
Site Search:






