- Home
- Popular IT Certifications
- Troubleshooting IOS AAA Using Local Database
Describe troubleshoot process for IOS AAA using local database
Access control is the way you control who is permitted access to the system server and what administrations they are permitted to utilize once they have admittance. Confirmation, approval, and bookkeeping (AAA) system security administrations give the essential structure through which you set up access control on your switch or access server.
AAA is a structural schema for designing a set of three autonomous security works in a reliable way. AAA gives a particular method for performing the accompanying administrations. Authentication provides the strategy for distinguishing clients, including login and secret key dialog, test and reaction, informing help, and, contingent upon the security convention you choose, encryption.
Other than finishing certificate tests like the Cisco CCNA Security, AAA is a discriminating bit of system foundation. AAA is the thing that keeps your system secure by verifying just the right clients are validated, that those clients have entry just to the right system assets, and that those clients are logged as they go about their business.it is imperative to note that Cisco IOS programming endeavors validation with the following recorded verification technique just when there is no reaction from the past strategy. On the off chance that the security server or client database reacts by denying the client get to, the verification process and the client will get a denied client prompt. When it comes to system security, AAA is a necessity. Here is the thing that each of these is utilized for and why you ought to give a second thought:
- Confirmation: Identifies clients by login and secret key utilizing test and reaction strategy before the client even gets access to the system. Contingent upon your security alternatives, it can likewise help encryption.
- Approval: After beginning verification, approval takes a gander at what that confirmed client has entry to do. Span or TACACS+ security servers perform approval for particular benefits by characterizing quality worth (AV) sets, which would be particular to the individual client rights. In the Cisco IOS, you can characterize AAA approval with a named rundown or approval strategy.
- Bookkeeping: The last "An" is for bookkeeping. It gives a method for gathering security data that you can use for charging, examining, and reporting. You can utilize bookkeeping to see what clients do once they are validated and approved. Case in point, with bookkeeping, you could get a log of when clients logged in and when they logged out.
Verification is the way a client is distinguished preceding being permitted access to the system and system administrations. You arrange AAA verification by characterizing a named rundown of confirmation strategies, and after that applying that rundown to different interfaces. The technique rundown characterizes the sorts of confirmation to be performed and the arrangement in which they will be performed; it must be connected to a particular interface before any of the characterized verification strategies will be performed. The main special case is the default strategy list (which is named "default"). The default system rundown is naturally connected to all interfaces if no other strategy rundown is characterized. A characterized technique rundown overrides the default strategy list. All validation routines, with the exception of neighborhood, line watchword, and empower confirmation, must be characterized through AAA. For data about arranging all validation techniques, including those actualized outside of the AAA security administrations, allude to the section "Designing Authentication." Authorization provides the technique for remote access control, including one-time approval or approval for each one administration, for every client record rundown and profile, client gathering help, and backing of IP, IPX, ARA, and Telnet.
AAA approval works by gathering a set of traits that depict what the client is approved to perform. These ascribes are contrasted with the data contained in a database for a given client and the result is come back to AAA to focus the client's real capacities and limitations. The database might be found generally on the right to gain entrance server or switch or it could be facilitated remotely on a RADIUS or TACACS+ security server. Remote security servers, for example, RADIUS and TACACS+, approve clients for particular rights by partner trait esteem (AV) sets, which characterize those rights with the proper client. All approval strategies must be characterized through AAA. Similarly as with confirmation, you design AAA approval by characterizing a named rundown of approval strategies, and afterward applying that rundown to different interfaces. For data about designing approval utilizing AAA, allude to the section "Arranging Authorization." The accounting Provides the strategy for gathering and sending security server data utilized for charging, reviewing, and reporting, for example, client personalities, begin and stop times, executed charges, (for example, PPP), number of bundles, and number of bytes.
Bookkeeping empowers you to track the administrations clients are getting to and in addition the measure of system assets they are expending. At the point when AAA bookkeeping is initiated, the system access server reports client action to the RADIUS or TACACS+ security server (contingent upon which security strategy you have executed) as bookkeeping records. Each one bookkeeping record is contained bookkeeping AV sets and is put away on the right to gain entrance control server. This information can then be investigated for system administration, customer charging, and/or inspecting. All bookkeeping strategies must be characterized through AAA. Likewise with confirmation and approval, you design AAA bookkeeping by characterizing a named rundown of bookkeeping strategies, and after that applying that rundown to different interfaces. For data about arranging bookkeeping utilizing AAA, allude to the part "Designing Accounting." As a rule, AAA utilizes conventions, for example, RADIUS, TACACS+, or Kerberos to control its security capacities. On the off chance that your switch or access server is going about as a system access server, AAA is the methods through which you build correspondence between your system access server and your RADIUS, TACACS+, or Kerberos security server. Despite the fact that AAA is the essential (and suggested) system for access control, Cisco IOS programming gives extra peculiarities to basic access control that are outside the extent of AAA, for example, nearby username confirmation, line secret word verification, and empower watchword validation. On the other hand, these gimmicks don't give the same level of access control that is conceivable by utilizing AAA. AAA is intended to empower you to progressively arrange the kind of confirmation and approval you need on for every line (for every client) or for every administration (for instance, IP, IPX, or VPDN) premise. You characterize the kind of confirmation and approval you need by making technique records, then applying those strategy records to particular administrations or interfaces. A system rundown is a successive rundown that characterizes the verification strategies used to validate a client. Technique records empower you to assign one or more security conventions to be utilized for confirmation, accordingly guaranteeing a reinforcement framework for verification in the event that the introductory strategy fizzles. Cisco IOS programming uses the first strategy leaned to verify clients; if that system does not react, Cisco IOS programming chooses the following validation technique in the technique list. This procedure proceeds until there is effective correspondence with a recorded validation technique or the verification strategy rundown is depleted, in which case confirmation.
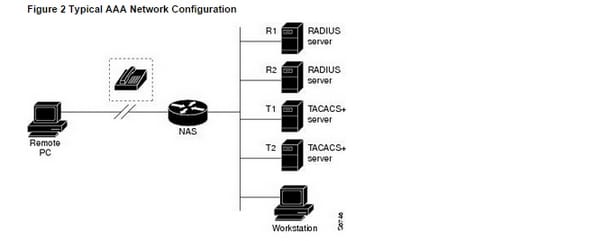
Assume the framework manager has characterized a technique list where R1 will be reached first for confirmation data, then R2, T1, T2, lastly the neighborhood username database on the right to gain entrance server itself. At the point when a remote client endeavors to dial into the system, the system access server first questions R1 for verification data. On the off chance that R1 confirms the client, it issues a PASS reaction to the system access server and the client is permitted to get to the system. On the off chance that R1 gives back a FAIL reaction, the client is denied access and the session is ended. In the event that R1 does not react, then the system access server forms that as an ERROR and questions R2 for validation data. This example proceeds through the staying assigned routines until the client is either confirmed or rejected, or until the session is ended. On the off chance that the majority of the validation strategies return lapses, the system access server will transform the session as a disappointment, and the session will be ended. A FAIL reaction is essentially not quite the same as an ERROR. A FAIL implies that the client has not met the criteria contained in the pertinent validation database to be effectively verified. Validation closes with a FAIL reaction. An ERROR implies that the security server has not reacted to a verification inquiry. Due to this, no verification has been endeavored. Just when an ERROR is recognized will AAA select the following validation system characterized in the confirmation strategy list? You should first choose what sort of security result you need to actualize. You have to evaluate the security chances in your specific system and choose the proper intends to avert unapproved entrance and assault. For more data about surveying your security dangers and conceivable security results, allude to the section "Security Overview." Cisco suggests that you utilize AAA, regardless of how minor your security needs may be.
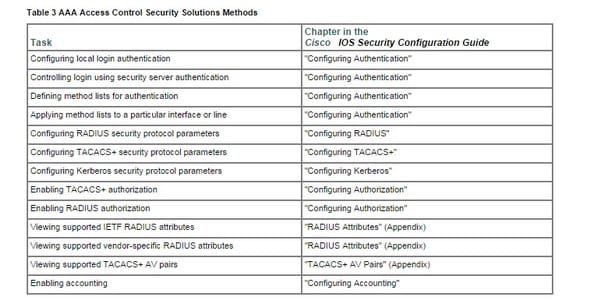
Designing AAA is moderately straightforward after you comprehend the fundamental methodology included. To arrange security on a Cisco switch or access server utilizing AAA, take after this methodology:
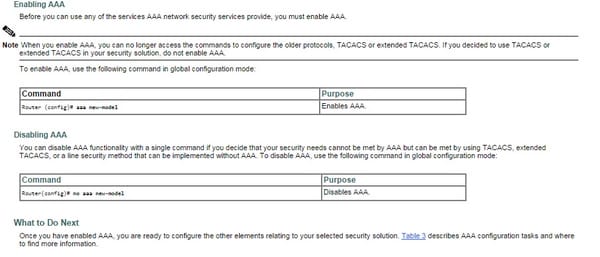
- Empower AAA by utilizing the AAA new-demonstrate worldwide design charge.
- In the event that you choose to utilize a different security server, design security convention parameters, for example, RADIUS, TACACS+, or Kerberos.
- Characterize the system records for verification by utilizing an AAA confirmation summon.
- Apply the system records to a specific interface or line, if needed.
- Configure approval utilizing the AAA approval charge.
- Configure bookkeeping utilizing the AAA bookkeeping charge.
This is how the AAA command is defined;
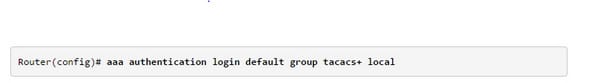
This is a noticeably extensive order, so we should work through it one bit at once. AAA confirmation login tags that the accompanying parameters are to be utilized for client login verification. The statement default is utilized as a part of lieu of a custom name for the rundown (you can just characterize one default list for every AAA capacity). Whatever remains of the line determines validation strategies. Bunch TACACS+ signifies "utilize all arranged TACACS+ servers." If you characterized a named server aggregate in step two, utilize the name of that gathering set up of the statement TACACS+ here. Neighborhood characterizes an optional validation system; it teaches the switch to come up short over to mainly characterized client accounts if none of the verification servers in the first technique are reachable. (Note that this just happens if the servers are inaccessible; a reaction from a server denying verification won't trigger a fizzle over to neighborhood validation.) The above strategy rundown handles just the verification part of AAA. Without anyone else present, this rundown just permits us to confirm as a client with benefit level 1 (client executive mode). To convey an increased benefit level (e.g. benefit level 15, or "empower mode") from the TACACS+ server, we additionally need to characterize an approval technique list for IOS shell creation. To arrange AAA validation, you should first characterize a named rundown of confirmation routines, and afterward apply that rundown to different interfaces. The strategy rundown characterizes the sorts of verification to be performed and the arrangement in which they will be performed; it must be connected to a particular interface before any of the characterized confirmation techniques will be performed. The main special case is the default strategy list (which is named "default"). The default system rundown is naturally connected to all interfaces with the exception of those that have a named technique list expressly characterized. A characterized system rundown overrides the default technique list. A system rundown is a successive rundown portraying the validation routines to be questioned so as to verify a client. Strategy records empower you to assign one or more security conventions to be utilized for verification, accordingly guaranteeing a reinforcement framework for validation in the event that the introductory system fizzles. Cisco IOS programming uses the initially recorded strategy to verify clients. On the off chance that that technique neglects to reacts, the Cisco IOS programming chooses the following validation strategy recorded in the system list. This methodology proceeds until there is fruitful correspondence with a recorded verification system, or all strategies characterized in the strategy rundown are depleted. It is paramount to note that the Cisco IOS programming endeavors verification with the following recorded validation system just when there is no reaction from the past strategy.
AAA security is the demand for the security which is related to networking, so all those who are willing to have future in the field of networking must know about it.
Site Search:






