- Home
- Popular IT Certifications
- Configuring & Verifying Router Security Features
How to configure and verify router security features
The access control list features enable to filter traffic depends on the information in an IP packet header. You can use the access control list on IPv4 as well as IPv6. You can configure the access list on the layer 3 switch or router to offer the basic security for the network. Suppose you did not configure the ACL, all the packets which flowing via the switch can be allowed in all parts of a network. And you can also use the ACL to control that host may access different parts of the network or else to decide what type of the traffic are blocked or forwarded at the router interfaces. Lets us see IPv4 ACL, IPv6 traffic filter and unicast reverse past forwarding in the below section. The unicast RPF helps to mitigate issues that are caused by the forged or malformed IP source addresses in the network by simply discarding the IP packets which lack the verifiable IP source address.
5.4.a IPv4 access control lists (standard, extended, time based)
The ACL stands for access control list which enable to allow or deny the packets based on the destination and source IP address, UDP or TCP protocol information, IP protocol information. You can configure this ACL into 3 types such as standard, extended and time based.
Packet filtering will help limit the network traffic and also restrict the network use of specific devices or users. The ACL filter traffic when it passes via switch or router and denies or permit packets flowing certain VLAN or interfaces. The ACL is the sequential collection of the deny and permit conditions which apply to the packets. When the packets are received on the interface, a switch compares the packet field against any of the applied ACL to verify whether the packet required permission to be forwarded depends on the certain criteria in the access list.
The Cisco MDS 900 family can route the IPv4 traffic between the fibre channel interfaces and Ethernet. An IP static routing features route traffic in between the VSAN. To perform so, every VSAN should be in the different IPv4 subnetwork. The IPv4 ACL offers basic network securities to all the switches in the MDS 9000 family. The IPv4 ACL restricts the IP related traffic depends on a configured IP filter. The filter contains specific rules to match the IP packet. If those packet matches, then the rule will stipulate in case the packet is denied or permitted.
Configuring IPv4 ACL:
Traffic coming into s switch is compared to the IPv4 filters depend on the filter occur in a switch. Then the new filters are also added to the IPv4 ACL end. The switch will keep searching until it has the match. In case no matches are identified when a switch reaches the filter end. The single entry IPv4 ACL with the one deny entry has an effect of denying all the traffic.
Follow the steps to create the IPv4 ACL:
Step 1:
This step configuration mode.
Command: switch# config t
Step 2: this step will configure the IPv4 ACL list 1 and also permits the IP traffic from any of the source address to any of the destination address
Command: switch(config)# ip access-list List1 permit ip any any
Then the below command will remove the called list 1 IPv4 ACL
Command: switch(config)# no ip access-list List1 permit ip any any
Step 3:
This command updates the list1 to deny the TCP traffic from any of the source address to the any destination address.
Command: switch(config)# ip access-list List1 deny tcp any any
Below steps define the IPv4 ACL, which restricts management access:
Step 1:
It enters into the configuration mode.
Command: switch# config t
Step 2:
This step defines the entry in the IPv4 ACL allowing all the addresses in the subnet.
Command:
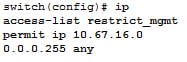
Step 3:
This command adds the entry to the IPv4 ACL to allow any devices to ping the MDS.
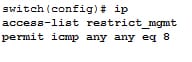
Step 4:
This step explicitly blocks all the other access to the access list named restrict_mgmt.
Command:
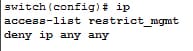
Follow the below steps to use operand and port options:
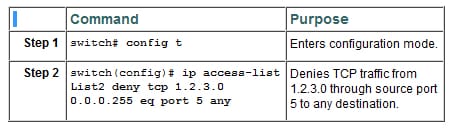
Add IP filters to the existing IPv4 ACL by following the below steps:
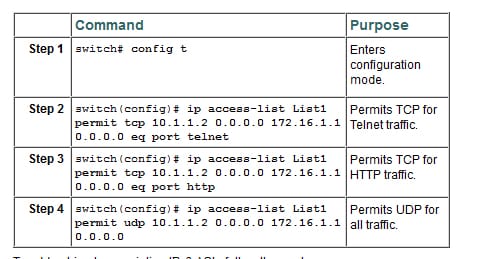
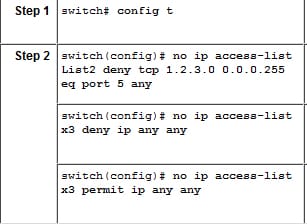
Remove IP filters:
To verify the IPv4 ACL make use of the command show ip access list to see the content of the configured IPv4 ACL.
To create the standard ACL:
Configure terminal
access-list access-list-number {deny | permit} source source-wildcard [log]
end
To create the extended ACL:

IPv4 time based:
You can also selectively apply the extended ACL depends on the time of the day as well as week using the global configuration command of time-range. It first defines the time range name and also sets the date and time in a time range. After that, enter the a time range name while applying the ACLs to set certain restrictions to an access list. You can also use this time range to define while denying or permit statement in the ACL is in effect. The keyword time range and the argument are also referenced in the numbered and named extended ACL tables. The time based access list trigger the CPU activities because a new configuration of an access list should be merged with the other feature and also the combined the configuration loaded into a hardware memory.
5.4.b IPv6 traffic filter
The traffic filtering is the method which is used to enhance the network security by filtering the network traffic based on the types of the criteria. The standard access control list functionality in the IPv6 is same as that of the standard ACL IPv4. This access lists find out what traffic blocked and which traffic is forwarded at the router interface and allow filtering depends on the destination and source addresses, outbound and inbound to the certain interface. Every access list has the implicit deny statement at an end. The IPv6 ACL is defined and its permit and deny conditions are set by using the command ipv6 access list with the permit and deny keywords in the global configuration mode.
The IPv6 extended ACL adds support for the IPv6 options header as well as layer filtering. The ACL is never applied to the self originated traffic.
Syntax for IPv6 traffic filter:
Ipv6 traffic-filter <ipv6_access_list>
IPv6 traffic filter parameter:
This parameter the name of the IPv6 ACL.
<ipv6_access_list>
Mode used:
Port interface mode
Confirmation command used:
Show interface access-group
Description:
Make use of the command to designate the IPv6 ACL to the interface. It is important to create the named IPv6 ACL command before assigning it to the port with command IPv6 traffic filter. Use the command no version, no IPv6 traffic filter to remove the IPv6 ACL from the port.
Example:
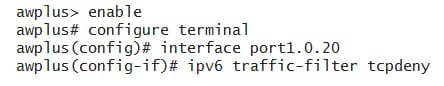
In the below example,adds the IPv6 ACL named as tcpdeny to the port 20:
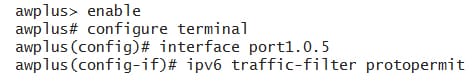
The below example, adds the IPv6 ACL named as protopermit to the port 5:
To verify the configuration, make use of the ping command.
5.4.c Unicast reverse path forwarding
The reverse path forwarding is the technique used in the modern routers for the purpose of ensuring the loop free forwarding of the multicast packets in the multicast routing and also help to prevent the IP address spoofing in the unicast routing. The unicast reverse path forwarding is also known as uRPF. It is one of the security feature. This security feature works by enabling the router to check the reachability of a source address in the packet being forwarded. This ability will limit the spoofed addresses appearance on the network. Suppose the source IP addresses are not valid, a packet is discarded. The unicast RPF will work in one of the 3 different modes such as loose mode, VRF mode or strict mode. Remember that not at all the network device will support all the 3 modes of the operation. When the administrator uses the unicast RPF in the strict mode, a packet can be received on an interface that a router might use to forward a return packet. The unicast RPF configured in the strict mode can drop legitimate traffic, which is received on the interface that was not a router choice for sending the return traffic.
When the unicast reverse path forwarding is enabled on the interface, a router checks all the packets received as an input on that certain interface to assure that the source interface and source address appear in a routing table ad also match an interface on which a packet was received. The look backward capability is only available when the CRF is enabled on a router, because a lookup rely on a presence of the FIB. The CEF generates forwarding information base as the part of the operation. The unicast RPF verifies to view if any of the packet received at the router interface arrive at any one of the return path to the packet source. The uRPF will perform it by doing the reverse lookup in a CEF table. Suppose a packet is received from one reverse path route, a packet is forwarded as normal. Suppose, there is no any reverse path route on a same interface from that the packet is received, it implies a source address is forged or modified. Suppose, the unicast RPF cannot find any reverse path for a packet, then the packet is dropped.
When the packet reaches at an interface where the unicast RPF as well as ACL have been configured, then the below action will occur:
- Input ACL configured on an inbound interface is checked
- The unicast RPF examine to see if a packet is arrived on any one of the best return path to a source, which it perform by doing the reverse lookup in a FIB table.
- The CEF table lookup is carried out for the packet forwarding.
- The output ACL is checked on an outbound interface
- A packet is then forwarded
Strict mode:
Strict mode is the mode that the router can perform 2 checks for all the incoming packets on the certain interface. When the incoming packets flow both checks, then it can be permitted. Or else, it can be dropped. It is fine for the IGP routing since it uses the shortest path to an IP packet's source. An interface which you use to reach a source can be same as the interface what you received in the packets.
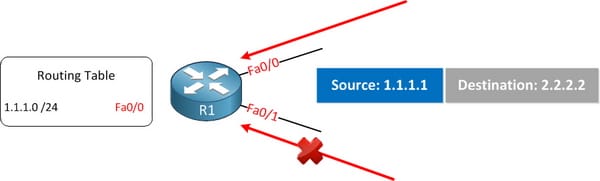
Take the above topology. Here R1 is installed 1.1.1.0/24 network in the routing table, so in order to reach that network it has to use the fastethernet 0/0 interface. But the router will receive the IP packet with the source IP address of 1.1.1.1 on both sides of the interface. The one which it gets on the fastethernet0/0 can be accepted, but a packet on a 0/1 interface can be dropped since it is not an interface that use to reach the source.
Lets see the below picture for how it works:
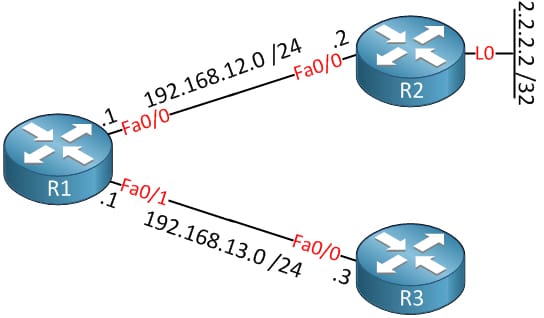
Configure R1 with the static route, hence it can reach a loopback0 R2 interface:

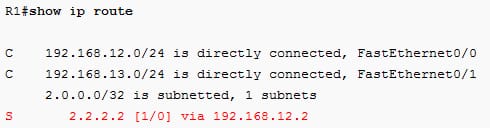
Routing table as follows:
Configure the uRPF strict mode on both the interfaces as follows:
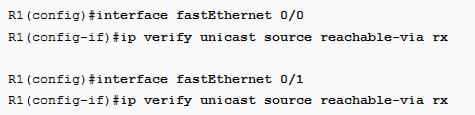
Verify that it is enabled on the interface like below one:
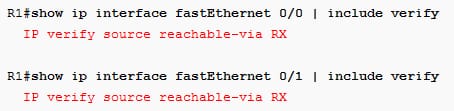
To test the uRPF, send the pings from the R2:
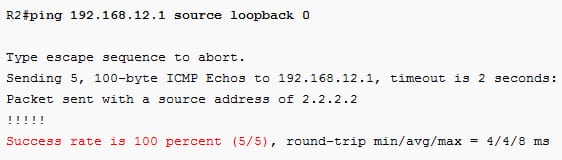
As ping works. Create the new loopback interface on the R3 with the IP address 2.2.2.2 on that to spoof the IP address:
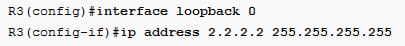
Send few pings from the loopback:
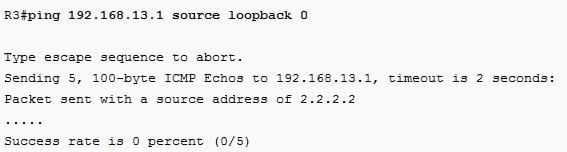
The packet can make that to R1 but it can be dropped there, now verify as follows:
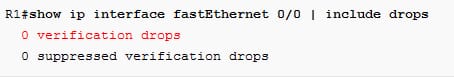
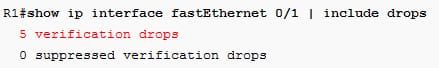
From the above configuration, the spoofed packet on the fastethernet0/1 interface is dropped.
The safe and secure networking is very important for any organization. In that way, network professionals and administrators have to know about this router security access. That the ACL will assist in its own way to provide the necessary things to the network. The Ipv4 ACL is discussed along with the standard, extended and time based. It also includes information about configuring IPv6 traffic filter also. The IPv6 ACL is used to filter that traffic and also restricts access to the router. The uRPF is used as in the ingress filtering mechanism and it is affected by the reverse path forwarding. This uRPF is discussed detail in this section. A Network administrator can use this uRPF to limit the malicious traffic on the enterprise network.
Site Search:






