- Home
- Popular IT Certifications
- Verify Device Management, SNMP and Logging
How To Configure And Verify Device Management, SNMP And Logging
The management IP plane allows to set the management IP address for a security appliance or context in the transparent firewall mode. The below section will helps to learn device management along with the VTY, console, Telnet, HTTP, SSH, SCP, Telnet. The network security mainly relies on the infrastructure and the password. The below section will explain the SNMPv2 and SNMPv3 configuration and verification in detail as well as logging messages along with the timestamps.
6.1 Configure And Verify Device Management
The one and only IP configuration needed for the security appliance is a management IP address. The exception is which you can set an IP address for the management only interface that does not flow through the traffic. In the below section, let us see the about the console, VTY, HTTP, HTTPS, Telnet, SSH and SCP in detail.
6.1.a Console And VTY
The network security mainly relies on the password. In that you can set passwords through console and VTY.
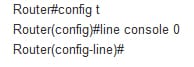
Console: it is the basic connection into each router. Initially set up the router which you required to a console port and at the minimum enable 1 interface and also set the VTY password. Then after enabling one interface, and VTy line is configured, the administrator can telnet into a router and perform the final configuration of the connection. It is essential to protect a console port with the password. Use the line command to configure the console user mode password. There is only 1 console port on all the routers, hence the command is as line console 0.
Ex:
VTY: the virtual teletype line is used to configure the telnet access to the cisco router. The VTy lines have to be configured for the telent to be successful. To configure the VTY line, must see the question mark with a command line 0 to determine the number of lines on the router. Sometimes the number varies with the router type and IOS version. Although, 5 is the most common line as follows:
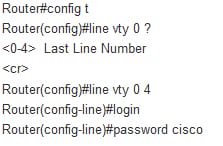
6.1.b Telnet, HTTP, HTTPS, SSH, SCP
Telnet: Telnet is the common way to remotely control web servers. It is the network protocol which is used on the local area networks or internet to offer the bidirectional interactive text oriented communication facility by using the virtual terminal connection. The telnet command allows to communicate with the remote computer, which is using the telnet protocol. You can also run the telnet without parameter in order to enter the context telent denoted by the telnet prompt.
Ex: telnet the.libraryat.whatis.edu
This telnet is likely to be used by the program developers and the professional who has need to use certain data or applications located in the certain host computer.
HTTP: The hypertext transfer protocol is the application protocol for the collaborative, distributed and hypermedia information system. The HTTP functions as the request -response protocol in a client server computing model. The HTTP is proposed to allow intermediate network elements to enable or improve communication between the servers and clients.
HTTPS: The HTTP secure is the communication protocol for secure communication over the computer network with specifically wide deployment on the internet. It offers authentication of the website and also associated web server. It also offers bidirectional encryption of communication in between the server and client, which protects from tampering and eavesdropping with or/and forging the content of the communication.
SSH: The secure shell is the cryptographic network protocol for the secure data communication, remote command execution, remote command line login and also other secure network services between the 2 networked computers. The secure shell is the program to log into the other computer over a network, to execute the command in the remote machine and also to move files from one machine to another. It offers secure communication and strong authentication over the insecure channels. The SSh also protects the network from attacks including, IP source routing, DNS spoofing and IP spoofing. An attacker who managed to take over the network can easily force ssh to disconnect, so that they can play back the hijack or traffic the connection when encryption is enabled. While using the SSH login all the login session, including the password transmission is encrypted, hence it is impossible for the unknown person or outsider to collect the passwords.
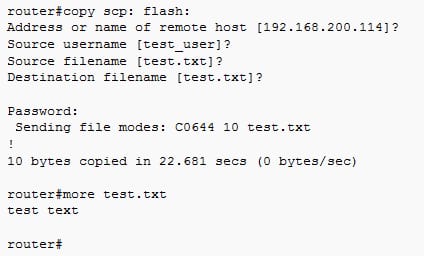
SCP: The SCP stands for secure copy. It is the way of transferring the files between the remote host and local host or between any 2 remote hosts. It is mostly based on the secure shell protocol. It is the subsystem of the SSH and it can also be accessed by the TCP/22. All the TCP traffic is authenticated and encrypted by using a same mechanism as SSH. The below example from the SSC in the EXEC mode:
Download example as follows:
Upload example as follows:
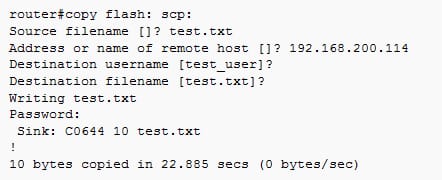
6.1. c (T) FTP
The FTP stands for file transfer protocol. It is the standard network protocol which is used to transfer the files from one host to the other host through the TCP based network like Internet. It builds on the client server architecture and also uses a separate control as well as data connections between the server and the client. It is most commonly used to download the file from a server by using the internet or to upload the file to the server.
6.2 Configure And Verify SNMP
The simple network management protocol is the application layer protocol, which offers the message format for the communication between the SNMP agents and managers. The ANMPv2 and SNMPv3 are discussed below:
6.2.a V2
The SNMPv2 uses the community based form of the security. The community of the SNMP managers which are able to access the MIB agent is defined by the IP address ACL and password. The SNMPv2 security model as follows:
Availability of encryption: NO
Level of security : noauthnopriv
Authentication method: community string
Configuration as follows:
Step 1:
This step enables the privileged EXEC mode.
Command: enable
Ex: device>enable
Step 2:
It enters the global configuration mode.
Command: configure terminal
Ex: device#configure terminal
Step 3:
This step configures the SNMP server group mainly to enable the authentication for the members of the specified name access list. In the below example, an SNMP server group is mainly configured to enable a user authentication for members of an NCL lmnop.
Command:

Ex:

Step 4:
This step configures an SNMP engine ID. The below example, an SNMP engine ID is configured for the remote user.
Command:
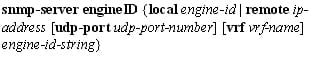
Ex:
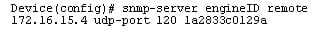
Step 5:
This step adds the new user to the SNMPv2 group and also configure the plain text password for a user.
Command:
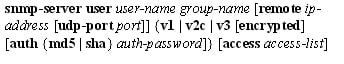
Ex:
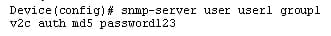
Step 6:
This step helps to exit the global configuration mode.
Command: exit
Ex: device(config)#exit
Verify SNMPv2:
To perform this task, verify the SNMPv2 configuration. The commands of show can also be entered in any order as follows:
Step 1:
Enable
Step 2:
Show snmp group
Step 3:
Show snmp user
Step 4:
Show snmp engine ID
6.2.b V3
The SNMPv3 offers secure access to the devices by the combination of encrypting and authenticating frames over a network. The security features included in the version 3 are such as encryption, authentication and message integrity. It offers for both the security levels and security models. The v3 configuration is a bit different from the v1 and v2. The SNMP offers 3 security levels, such as
Authpriv ? authentication and encryption
Authnopriv? authentication but no encryption
Noauthnopriv ? no authentication and no encryption.
The SNMPv3 is more secure because it will never send the user password in the clear text but uses the SHA1 or MD5 hash based authentication, encryption is done bu using the AES, 3DES and DES.
Example configuration:
Create the new group and also select the security model as follows:
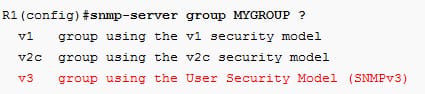
The group is named as mygroup and selected ANMPv3 as a security model. Then select the security level as follows:
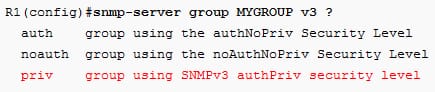
Using a parameter priv, select the authpriv security level. In that, there are different options for the security levels as follows:

Full read access to the all MIB as follows:
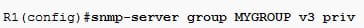
Create the user account as follows:
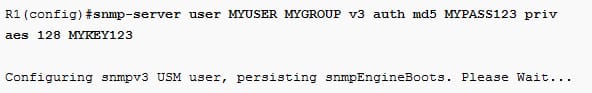
Verification:
If the user account not stored configuration, then the output will be as follows:
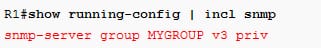
If the user account is found, then the configuration will be:
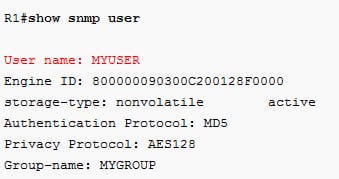
6.3 Configure And Verify Logging
Many network administrators overlook the importance of the router logs. The logging can use for the fault notification, security auditing and network forensics. Administrators and users use different management interfaces of the ACS to do different tasks. By using the administrative access control, you can allow users and administrators to do different tasks. Additionally, you also required an option to track the different actions performed by the users and administrators. The ASC provides several logs which you can track the events and actions.The cisco route log messages can also handle in 5 different ways, such as syslog, local logging, debugs, conditional debugs and timestamps. Let us see in detail.
6.3.a Local Logging, Syslog, Debugs, Conditional Debugs
Local logging: You can specify to send the customer log information to the multiple customers or to log targets and also specify that the log messages are stored locally in the text format or forwarded to the syslog servers. As default, the single predefined local log target is called as local stores that stores data in the text format on the ACS server as well as contains the log messages from a local ACS server only. Additionally, you can see records stored in the CLI local store. Each log is mostly associated with the message code which is bundled with a logging category, according to a log message content.
Syslog: It is the standard for the computer message logging. It allows the separation of the software which generates messages from the systems that stores it and the software that analyze and reports it. It can be used for the security auditing and system management, debugging messages and analysis. The syslog is supported by a wide range of devices, including routers and receivers over the multiple platforms. The syslog is used to integrate the log data from many various types of the systems into the central repository. The format of the syslog packet is HEADER MSG.
Debugs:
The debug is the command in the OS/2, DOS and Microsoft windows. The debugging the methodical process of finding as well as reducing the number of buds or defects.
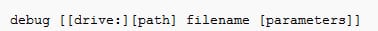
Syntax for debug:
Conditional debugs:
When the condition debugging is enabled, then the router generates debugging the messages for the packets leaving or entering the router on the specified interface and the router cannot generate debugging output packet leaving or entering through the different interfaces. Generally, the router can generate debugging messages for each interface, which results in the large number of messages that consume system resource and also can make it difficult to determine the certain information you need. Given below is the conditional debugging feature which controls the output from the protocol specific debug commands:

6.3.b Timestamps
If the router is configured to receive the time from the network time protocol server, the time in the router log entry can be different from the system clock time if the option is not in a service timestamps log command.
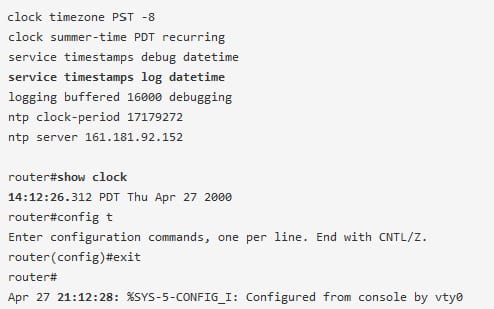
In the above example, a router gets the time from the NTP server and also the service timestamps log datetime is issued. Then the command of show clock will display the time of 14:12:26, when the configuration change is immediately made after the command show clock., a log message shows the time of 21:12:28.
In the resolution, add the localtime option to the command of service timestamps log datetime, issue a global configuration command:
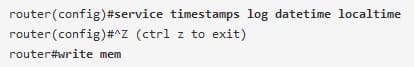
Then the time must be synchronized in between the log message timestamps and the system clock.
The Cisco router will help to simplify the networking setup and offers the most secure and stable link between the LAN and the internet. The Router can perform as a server, such as HTTP, FTP, HTTPS, SSC, SSH. And line such as VTY and console. SNMP provides the standardized framework and the common language used for monitoring and also management of the device in the network. The logging messages, including Local Logging, Syslog, Debugs, Conditional Debugs and timestamps are required to perform the better security for the network or device.
Site Search:






