- Home
- Popular IT Certifications
- Cisco Switch Configuration and Operation
Initial Switch configuration and verifying network status and switch operation using basic utilities such as ping, telnet and SSH
A system switch is a little equipment gadget that joins various machines together inside one neighborhood (LAN). Ethernet switch gadgets were usually utilized on home systems before home switches got to be mainstreamed; broadband switches incorporate Ethernet switches straightforwardly into the unit as one of their numerous capacities. Elite system switches are still broadly utilized as a part of corporate systems and server farms. So, one should know about them all so he can master the field of networking.
Here is the way how the switches are used with the basic utilities;
Hostname
In networking, a hostname is a mark that is allotted to a gadget associated with a machine system and that is utilized to distinguish the gadget in different manifestations of electronic correspondence, for example, the World Wide Web, email or Usenet. Hostnames may be basic names comprising of a solitary word or expression, or they may be structured. On the Internet, hostnames may have attached the name of a Domain Name System (DNS) area, differentiated from the host-particular mark by a period ("dab"). In the recent structure, a hostname is additionally called a space name. On the off chance that the area name is totally pointed out, including a top-level space of the Internet, then the hostname is said to be a completely qualified space name (FQDN). Hostnames that incorporate DNS areas are frequently put away in the Domain Name System together with the IP locations of the host they speak to with the end goal of mapping the hostname to a location, or the converse process. Hostnames are intelligible epithets that relate to the location of a gadget joined with a system. They are utilized by different naming frameworks, e.g., Network Information Service (NIS), Domain Name System (DNS), Server Message Block (SMB), and the significance of hostname will shift as indicated by the naming framework utilized. A hostname serious to a Microsoft NetBIOS workgroup may be an invalid Internet hostname. At the point when displayed with a hostname without any setting, it is generally protected to expect that the system is the Internet and the hostname's naming framework is the DNS.
Host names are ordinarily utilized within a managerial limit and may show up in machine program records, dynamic catalog records, IP location to hostname resolutions, email headers, and so forth.
Mgmt. IP address
Every server in a Cisco UCS space must have an administration IP location doled out to its Cisco Integrated Management Controller (CIMC) or to the administration profile connected with the server. Cisco UCS Manager utilizes this IP address for outer get to that ends in the CIMC. This outer access might be through one of the accompanying:
- KVM reassure
- Serial over LAN
- An IPMI device
The administration IP location used to get to the CIMC on a server could be one of the accompanying:
- A static Ipv4 location allotted specifically to the server.
- A static Ipv4 location doled out to an administration profile. You can't design an administration profile layout with a static IP address.
- An IP address drawn from the administration IP location pool and doled out to an administration profile or administration profile format.
You can relegate an administration IP location to every CIMC on the server and to the administration profile connected with the server. In the event that you do thus, you must use distinctive IP addresses for each of them.
IP default-gateway
A gateway is a hub (a switch) on a TCP/IP arranges that serves as a right to gain entrance point to an alternate system. A default gateway is the hub on the machine organize that the system programming uses when an IP address does not match another courses in the directing table. In home figuring setups, an ISP regularly gives a physical gadget which both unites neighborhood equipment to the Internet and serves as a gateway. Such gadgets incorporate DSL switches and link switches. In hierarchical frameworks a door is a hub that courses the movement from a workstation to an alternate system section. The default gateway ordinarily associate the inside systems and the outside system (Internet). In such a circumstance, the gateway hub could likewise go about as a substitute server and a firewall. The door is additionally connected with both a switch, which utilizes headers and sending tables to figure out where parcels are sent, and a switch, which gives the real way to the parcel lock stock and done with the portal. As it were, a default gateway gives a passage point and a passageway point in a system.
Local user and password:
Local username and password are set so that the data on a computer can stay protected. The method of doing this is pretty simple; one can go to the run and can open CMD. Then get the PS tools and set the password there.
Enable secret password
To give an extra layer of security, especially for passwords that cross the system or are put away on a TFTP server, you can utilize either the enable watchword or enable secret commands. Both summons finish the same thing; that is, they permit you to build a scrambled secret word that clients must enter to get to enable mode (the default), or any benefit level you point out. Cisco prescribe that you utilize the enable mystery summon on the grounds that it utilizes an enhanced encryption calculation. Utilize the enable secret word charge just in the event that you boot a more established picture of the Cisco IOS programming, or in the event that you boot more established boot ROMS that don't perceive the enable secret command.
Console and VTY logins
For the passwords of console and VTY logins, you can go to the global mode and enter the following codes;
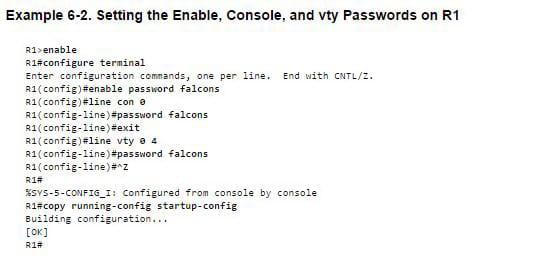
Exec-timeout
The EXEC timeout is a fundamental Cisco IOS setting that you will need to be mindful of when arranging your Cisco gadget to permit client access. By setting the EXEC timeout, you're advising the Cisco gadget to naturally separate clients on a line once they have been unmoving for the length of time of the EXEC timeout esteem. The Cisco IOS programming order line interface (CLI) has two levels of access to orders: client EXEC mode (level 1) and favored EXEC mode (level 15). Nonetheless, you can arrange extra levels of access to orders, called benefit levels, to help your clients while securing the framework from unapproved access. Up to 16 benefit levels might be arranged, from level 0, which is the most limited level, to level 15, which is the minimum confined level. Access to each one benefit level is enabled through divided passwords, which you point out when arranging the benefit level.
For instance, on the off chance that you need a certain set of clients to have the capacity to design just certain interfaces, however not permit them get to other arrangement alternatives, you could make a different benefit level for just particular interface setup orders and appropriate the secret key for that level to those clients.Service password encryption
There is however a decent use for this encryption administration which is to keep topping tom's from looking over your shoulder while you have a design showed on screen from survey clear content passwords. At the point when presenting designs online on offer make sure to uproot the sort 7 encoded passwords as these passwords might be effectively broken. Sort 5 passwords utilize an Md5 hash which is a restricted (non-reversible) 128bit calculation. This secret word can't be "decoded" because of the way of the calculation. When you verify to a Cisco gadget that stores the secret word in Md5 form, the gadget encodes the watchword string you gave and matches it to the string put away in arrangement. On the off chance that it matches then the verification is effective, if not then validation is not and your secret word is declined. Remember sort 7 passwords are viewed as powerless while sort 5 passwords are "uncrack able" per se. Sort 5 secret key hashes can't be decoded with rainbow tables because of the reality the Type 5 watchword hash is partitioned into 3 different areas. Utilizing the Type 5 watchword hash found in the lab direction of this lab, $1 speaks to the Cisco sort 5 secret words, the $id2r which speaks to the "salt" and $2akuk4us6yuqvkggsmklv0 is the real Md5 hash that is ascertained with the "salt". Cisco does not distribute how the "salt" is in fact utilized as a part of the computation of the md5 hash accordingly it is "obscure". Salts are utilized as a part of a way to guarantee additional security for md5 strings making them special and exclusive to the salt capacity composed. Case in point; let's say we utilize the secret word Hello123 and Cisco puts the arbitrarily created salt after the second character in the real passphrase, the prewashed watchword quality would than get to be "He"$salt"llo123 in which case would provide for you a remarkable md5 string. At last the fact I'm trying to make is that the method in which Cisco utilizes the SALT capacity is exclusive. Remember salt is haphazardly produced and put away with the watchword hash which makes it almost difficult to try and make a rainbow for each present estimation of the standard md5 rainbow table in light of the fact that you don't have a clue about the capacity in how the "Salt" is utilized and in addition you can't compose a script to set the secret word on a Cisco gadget to each conceivable secret word found in the rainbow table as the salt is arbitrarily created each time you utilize the "enable mystery XXXX" charge. So when somebody lets you know that the type5 could be broken by a rainbow table is totally inaccurate as a standard rainbow table won't work in light of the fact that a standard rainbow table does not have Md5 hash values.
Copy run start
One must do a copy run start. on a Cisco switch, 2900's or more when you are changing the setup exactly as you would do when designing a switch. In the event that you don't do a copy run start you will lose the arrangement if the switch is rebooted.
Ping
Ping is the name of a standard programming utility (instrument) used to test system associations. It could be utilized to figure out whether a remote gadget, (for example, Web or diversion server) might be arrived at over the system and, assuming this is the case, the association's inertness. Ping instruments are some piece of Windows, Mac OS X and Linux and also a few switches and diversion supports.
Telnet
Telnet is a system convention utilized on the Internet or neighborhood to give a bidirectional intelligent content situated correspondence office utilizing a virtual terminal association. Client information is blended in-band with Telnet control data in a 8-bit byte arranged information association over the Transmission Control Protocol (TCP).telnet was produced in 1968 starting with RFC 15, stretched out in RFC 854, and institutionalized as Internet Engineering Task Force (IETF) Internet Standard STD 8, one of the first Internet standards. Telnet gave access to a charge line interface (for the most part, of a working framework) on a remote host. Most system supplies and working frameworks with a TCP/IP stack help a Telnet administration for remote design (counting frameworks focused around Windows NT).
SSH:
Secure Shell (SSH) is a cryptographic system convention for secure information correspondence, remote charge line login, remote summon execution, and other secure system benefits between two organized machines. It joins, by means of a safe channel over a frail system, a server and a customer running SSH server and SSH customer programs, respectively. The convention particular recognizes two significant forms that are alluded to as SSH-1 and SSH-2. The best-known application of the convention is for access to shell accounts on Unix-like working frameworks, however it can likewise be utilized as a part of a comparative style for records on Windows. It was planned as a trade for Telnet and other unreliable remote shell conventions.
The crust of the topic is that knowing about the utilities and the protocols like SSH, telnet and ping are of immense importance since they are used in the networking a lot. So one must have knowledge about these instruments and how they are configured and how they work.
Site Search:






