- Home
- Popular IT Certifications
- How to Configure and Verify Syslog
How to Configure and verify syslog
Syslog is a standard for computer message logging. It allows partition of the product that creates messages from the framework that stores them and the product that reports and breaks down them. Syslog is a technique to gather messages from gadgets to a server running a syslog daemon. Logging to a focal syslog server helps in total of logs and alarms. Cisco gadgets can send their log messages to a Unix-style SYSLOG administration. A SYSLOG benefit just acknowledges messages, and stores them in records or prints them as indicated by a straightforward design document. This type of logging is the best accessible for Cisco gadgets on the grounds that it can give ensured long haul stockpiling for logs. This is helpful both in standard troubleshooting and in episode taking care of.
Syslog is a route for system gadgets to send occasion messages to a logging server - typically known as a Syslog server. The Syslog protocol is upheld by an extensive variety of gadgets and could be utilized to log diverse sorts of occasions. Case in point, a switch may send messages about clients logging on to reassure sessions, while a web-server may log access-denied occasions. Most system supplies, in the same way as switches and switches, can send Syslog messages. That, as well as can create Syslog information, as do most firewalls, a few printers, and even web-servers like Apache. Windows-based servers don't help Syslog locally, yet a substantial number of outsider devices make it simple to gather Windows Event Log or IIS information and forward it to a Syslog server. Dissimilar to SNMP, Syslog can't be utilized to "survey" gadgets to accumulate data. Case in point, SNMP has a complex progressive structure that permits an administration station to approach a gadget for data on things like temperature information or accessible circle space. That is unrealistic with Syslog - it basically sends messages to a focal area when particular occasions are activated.
Syslog might be utilized for machine framework administration and security inspecting and summed up enlightening, investigation, and debugging messages. It is backed by a wide mixed bag of gadgets (like printers and switches) and recipients crosswise over different stages. On account of this, syslog might be utilized to incorporate log information from numerous distinctive sorts of frameworks into a focal storehouse. Messages are named with an office code (one of: daemon, ftp, kern, mail, news, syslog, client, local0 ... local7) demonstrating the sort of programming that created the messages, and are appointed a seriousness (one of: Emergency, Alert, Critical, Error, Warning, Notice, Info, Debug). Executions are accessible for some working frameworks. Particular design may allow guiding messages to different gadgets (support), records (/var/log/) or remote syslog servers. Most usage likewise gives an order line utility, regularly called lumberjack that can send messages to the syslog. A few usages allow the separating and presentation of syslog messages. Syslog is currently institutionalized by the IETF in RFC 5424.syslog was created in the 1980s by Eric Allman as a major aspect of the Send mail extend, and was at first utilized singularly for Send mail. It demonstrated so profitable that different applications started utilizing it too. Syslog has since turned into the standard logging result on UNIX and Unix-like frameworks; there have additionally been an assortment of syslog usage on other working frameworks and is generally found in system gadgets, for example, switches. Syslog worked as a true standard, without any definitive distributed particular, and numerous executions existed, some of which were contradictory. The Internet Engineering Task Force archived the present state of affairs in RFC 3164. It was made outdated by resulting increases in RFC 5424.
At diverse focuses in time, different organizations have endeavored patent claims on syslog. This had little impact on the utilization and institutionalization of the protocol. Various gatherings are chipping away at draft guidelines itemizing the utilization of syslog for more than simply system and security occasion logging, for example, its proposed application inside the health nature's turf. Regulations, for example, SOX, PCI DSS, HIPAA, and numerous others are obliging associations to execute exhaustive efforts to establish safety, which frequently incorporate gathering and examining logs from numerous distinctive sources. Syslog has turned out to be a compelling organization to merge logs, as there are numerous open source and exclusive devices for reporting and examination. Converters exist from Windows Event Log and also other log configurations to syslog. A rising territory of oversaw security administrations is the gathering and dissection of syslog records for associations. Organizations calling themselves Managed Security Service Providers endeavor to apply examination procedures (and at times computerized reasoning calculations) to discover examples and caution clients to issues.
The PRI part is a number that is encased in plot sections. This speaks to both the Facility and Severity of the message. This number is an eight bit number. The initial 3 slightest noteworthy bits speak to the Severity of the message (with 3 bits you can speak to 8 separate Severities) and the other 5 bits speak to the Facility of the message. You can utilize the Facility and the Severity qualities to apply certain channels on the occasions in the Syslog Daemon. The Priority worth is computed by first reproducing the Facility number by 8 and afterward including the numerical estimation of the Severity. For instance, a bit message (Facility=0) with a Severity of Emergency (Severity=0) would have a Priority estimation of 0. Likewise, a "neighborhood utilize 4" message (Facility=20) with a Severity of Notice (Severity=5) would have a Priority estimation of 165. In the PRI piece of a Syslog message, these qualities would be set between the plot sections as <0> and <165> respectively. The UDP based Syslog protocol is problematic. Not at all like TCP based transmission of messages, does UDP not ensure you the conveyance of the messages. They might either be dropped through system blockage, or they may be malignantly caught and disposed of. The Syslog protocol does not guarantee requested conveyance of parcels. Since each one procedure, application and working framework was composed autonomously, there is little consistency to the substance of syslog messages. Therefore, no suspicion is made upon the organizing or substance of the messages. The protocol is essentially intended to transport these messages. The collector of a Syslog bundle will be unable to validate that the message was in fact sent from the reported sender. A misconfigured machine may send syslog messages to a Syslog daemon speaking to itself as an alternate machine. The regulatory staff may get to be befuddled on the grounds that the status of the assumed sender of the messages may not be precisely reflected in the got messages. An alternate issue connected with validation is that an assailant may begin sending fake messages showing an issue on some machine. This may get the consideration of the framework heads who will invest their time examining the asserted issue. Amid this time, the aggressor may have the capacity to trade off an alternate machine, or an alternate process on the same machine. An assailant may record a set of messages that demonstrate typical action of a machine. At a later time, that assailant may expel that machine from the system and replay the syslog messages to the daemon. Syslog is a customer/server protocol. a logging application transmits an instant message to the syslog collector. The beneficiary is generally called syslog, syslog daemon or syslog server. Syslog messages may be sent by means of the User Datagram Protocol (UDP) or the Transmission Control Protocol (TCP). The information is sent in clear text; in spite of the fact that not a piece of the syslog protocol itself, a SSL wrapper may be utilized to accommodate a layer of encryption through SSL/TLS. Syslog utilizes the port number 514. The first particular in RFC 3164 did not determine numerous protocol perspectives, for example, the greatest message size and the character encoding for the message content. RFC 5424 included numerous subtle elements. Among others, usage must help a most extreme message size of no less than 480 octets, and ought to backing 2048 octets; messages ought to be encoded as UTF-8.
Here is how it can be configured;

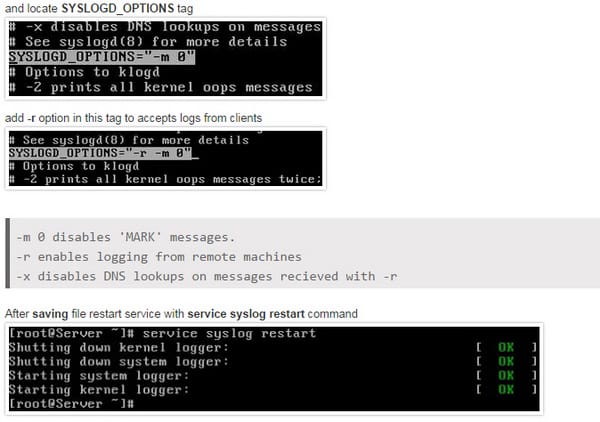
Utilize syslog output
Most Cisco gadgets utilize the syslog protocol to oversee framework logs and alarms. Yet dissimilar to their PC and server partners, Cisco gadgets need huge inward storage room for putting away these logs. To beat this impediment, Cisco gadgets offer the accompanying two choices: Interior cushion. The gadget's working framework designates a little piece of memory cradles to log the latest messages. The cradle size is constrained to few kilobytes. This choice is enabled as a matter of course. In any case, when the gadget reboots, these syslog messages are lost. Syslog- Use an UNIX-style SYSLOG protocol to send messages to an outside gadget for putting away. The capacity size does not rely on upon the switch's assets and is restricted just by the accessible plate space on the outside syslog server. This choice is not enabled as a matter of course.
Before designing a Cisco gadget to send syslog messages, verify that it is designed with the right date, time, and time zone. Syslog information would be pointless for troubleshooting on the off chance that it demonstrates the wrong date and time. You ought to design all system gadgets to utilize NTP. Utilizing NTP guarantees a right and synchronized framework clock on all gadgets inside the system. Setting the gadgets with the exact time is useful for occasion relationship. To enable syslog usefulness in a Cisco system, you must design the inherent syslog customer inside the Cisco gadgets. Cisco gadgets utilize a seriousness level of warnings through crises to produce blunder messages about programming or fittings glitches. The debugging level shows the yield of debug charges. The Notice level showcases interface up or down moves and framework restart messages. The educational level reloads demands and low-process stack message.
Here is the command list for it;

At the point when a level is pointed out in the logging trap level charge, the switch is arranged to send messages with lower seriousness levels too. Case in point, the logging trap cautioning charge arranges the switch to send all messages with the seriousness cautioning, mistake, discriminating, and crisis. Essentially, the logging trap debug order causes the switch to send all messages to the syslog server. Since the debug methodology is relegated a high CPU necessity, utilizing it within an occupied system can result in the switch to crash.
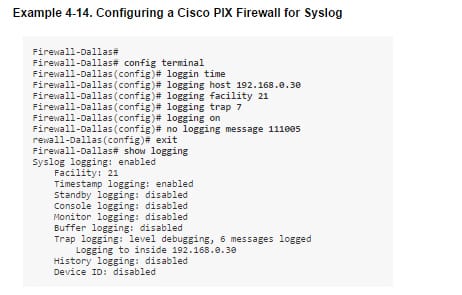
For included dependability, the Cisco PIX Firewall could be arranged to send syslog messages through TCP. If you don't mind note that if the syslog server plate is full, it can close the TCP association. This will result in a foreswearing of administration on the grounds that the Cisco PIX Firewall will stop all movement until the syslog server circle space is liberated. Both The Syslog Server and PFSS offer this gimmick. The Syslog has a caution system to caution the net ADMIN through email or pager when the circle is nearing its ability. The setting might be secured from the Syslog Daemon Setup window. In the event that the PIX stop on account of a plate full condition, you should first free some circle space. At that point impair syslog informing on the PIX by utilizing the no logging host order, took after by enabling syslog informing utilizing the logging host command. The change in office level for a specific message in the past case is for representation purposes just. Changing the office level from its default quality is a progressed net admin work and is determinedly demoralized. A Cisco PIX Firewall confronting the Internet is subjected to a lot of spontaneous activity as ping sweeps, port outputs, and tests. This can result in the log record to wind up substantial inside days. It will be loaded with information, making it hard to scan for helpful data. You ought to tweak your firewall to smother certain basic messages utilizing the no logging message-id-number order. Moreover, utilize the IOS firewall offers on the edge switch to channel undesirable movement before it hits the Cisco PIX Firewall.
Syslog are important part of the networking. So those looking to have some good future in networking should know about it so they can become master at it.
Site Search:






